If you’re like 94% of enterprises, you are using the cloud in one way or another. But if you’re also like 84% of organizations, you are struggling to apply traditional security tools to your cloud based environment. Maybe you’re also among the 93% of companies that lack visibility into their cloud data, or the 24% who are running cloud workloads that are missing critical security patches.
I could go on, but you get the point: companies that have moved to the cloud don’t always do a good job of securing the workloads they run there. For that reason, it’s worth stepping back and assessing how well you’re meeting cloud security threats. Whether you’re just starting out on your cloud journey or were building cloud-native apps before it became the cool thing to do, chances are you’re overlooking potential cloud security vulnerabilities or risks.
With that reality in mind, here’s a cloud security checklist that companies of all types can use to assess the state of their security strategy.
Build Your Cloud Security Checklist from Questions
The first step in building your cloud security checklist is asking various stakeholders who can inform you of what’s working and what’s not. Groups to query include:
- Your developers: They’ll be able to tell you about shortcuts they may be taking in building and deploying code to the cloud that could compromise security. They will also be aware of any pain-points that make it hard to follow best practices when working with cloud software, such as issues integrating on-premises access-control systems with those that work for cloud workloads.
- Your vendors: Vendors who supply tools and services that support your cloud workloads will know which security practices they recommend for consuming their resources.
- Your users: Users can inform you of security issues or risks that impact them when they use your applications. Although surveying every user directly may not be feasible, consider sending surveys to those with whom you have a strong relationship (like long-time customers). You can also ask support staff about user complaints involving security problems in order to identify relevant trends.
Share Your Responsibility
The concept of shared responsibility – meaning you are responsible for securing some parts of your cloud solution stack while your cloud providers secure others – is part and parcel of cloud security. But it is often misunderstood; indeed, 73% of organizations report being unclear about where their responsibility starts and their cloud providers’ ends.
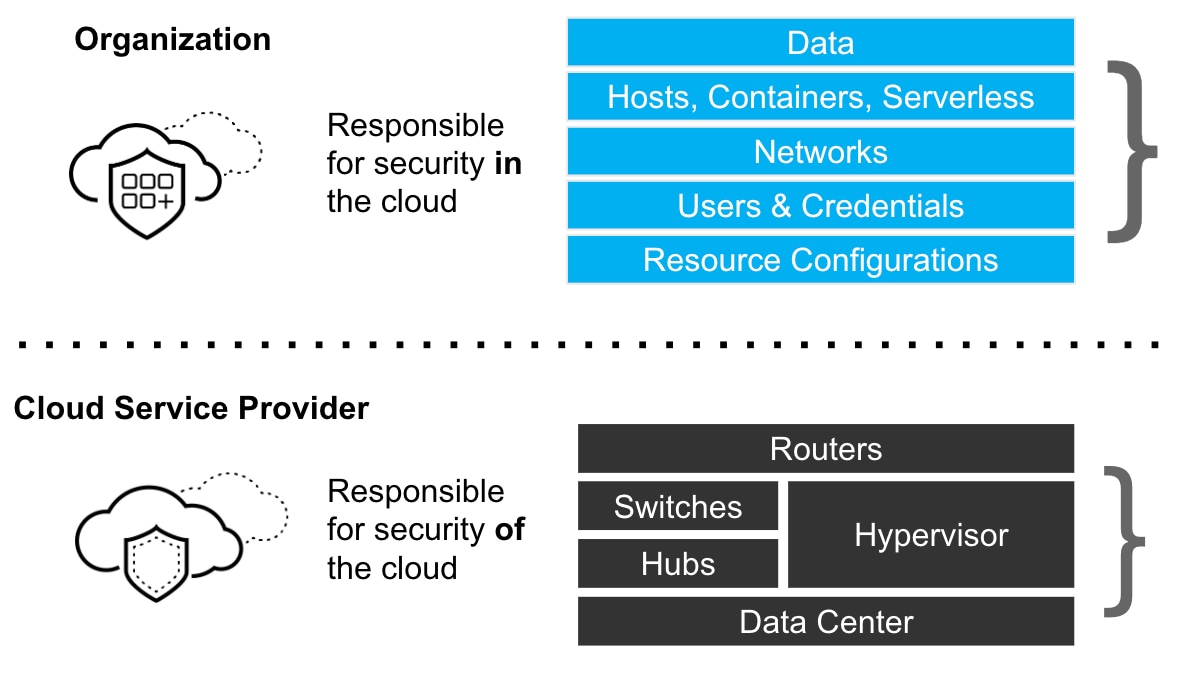
So, as part of your cloud security assessment, evaluate your current strategy for meeting shared responsibility requirements and determine whether it leaves any parts of your workloads or infrastructure unsecured.
Automate, Automate, Automate
By now, pretty much everyone knows why automation is so critical and beneficial. (We can thank the DevOps folks for preaching that gospel to us so aggressively over the past decade.) But the challenge arises in putting automation into practice – especially in the cloud, where automation routines that you developed for on-premises workloads don’t always work.
That’s why it’s worth taking a look at the extent to which your current cloud security operations are automated and finding ways to automate more. Vulnerability scanning and alerting are good places to start with cloud security automation. Automated policy-based audits of cloud configurations may help unveil security issues, too.
Build a Response Plan
Having an efficient process in place for finding security problems in the cloud is of little use if you don’t also have a plan for responding to them. As you review your cloud security posture, identify any major security risks for which you don’t yet have an incident management plan or playbook in place. Developing one should be included in your cloud security checklist.
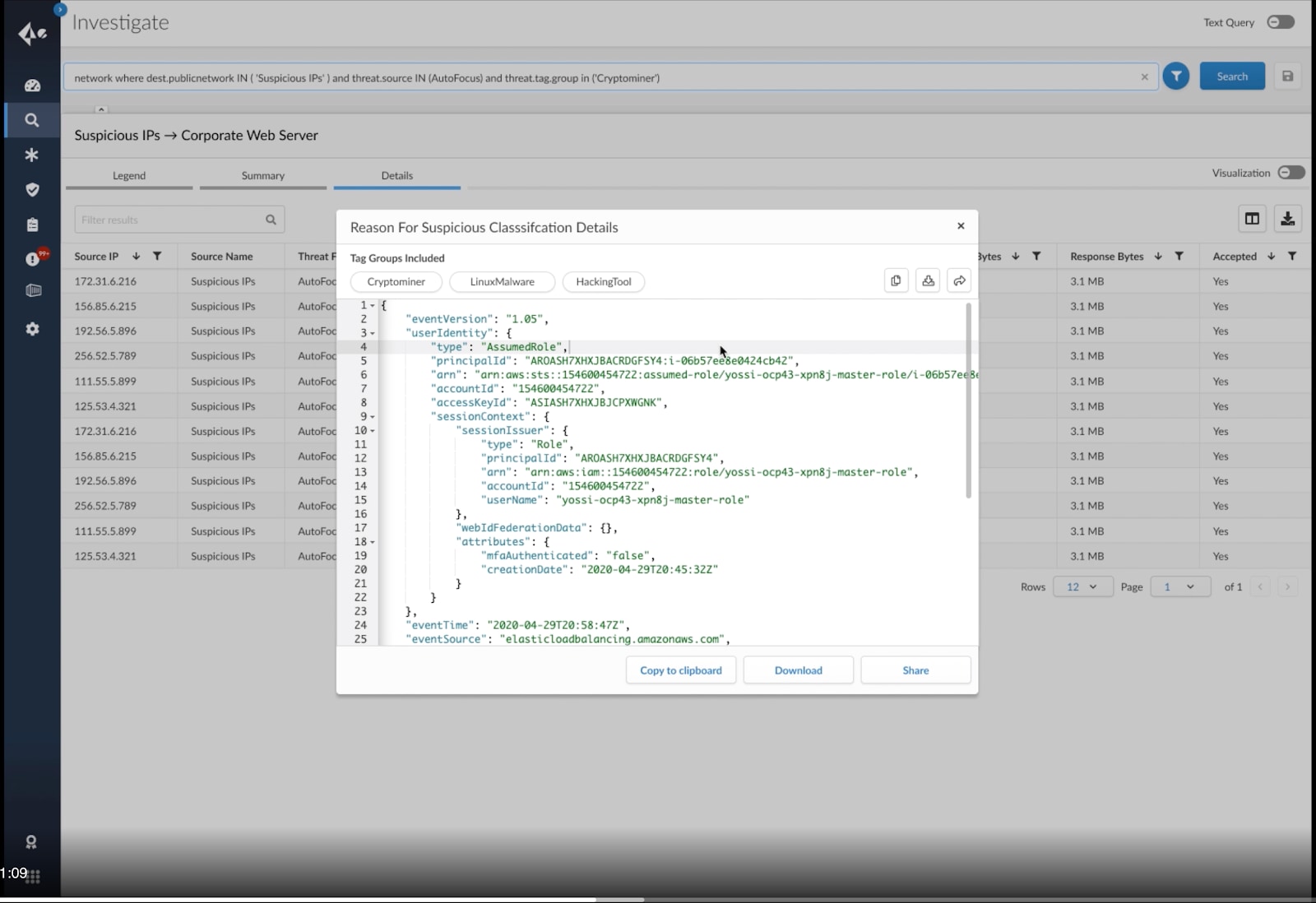
What will you do if you discover an Amazon Simple Storage Service (S3) bucket that you inadvertently exposed publicly? How will you respond if an app gets DDoS’d? What if you need to recover databases in response to a ransomware attack? These are examples of fairly common cloud security incidents to which you should be prepared to respond.
Make Friends
DevSecOps may be a buzzword, but the concept behind it is powerful. Make sure DevOps and SecOps teams have shared goals, and try to build a cooperative culture. Eliminate blame and find solutions. Identify metrics that each group can assess to determine how effectively they are achieving security goals. Make sure all stakeholders have visibility into the security state of your cloud, and that there are open communication channels that engineers can use to trigger a response when they notice a potential security problem.
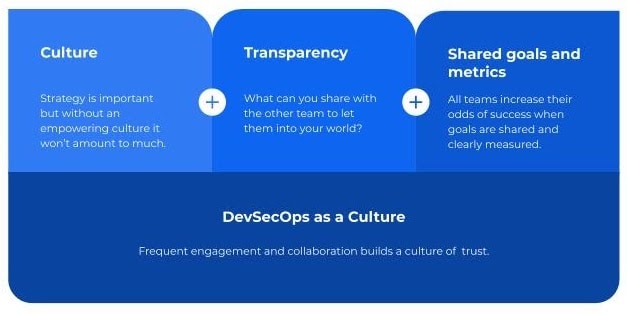
Shift Left
Speaking of buzzwords, “shift left” is another one, but it also has real value. You can shift cloud security (and, indeed, all aspects of security) left by building security checkpoints into your software development lifecycle as early as possible and repeating them frequently throughout the CI/CD pipeline – up to and after deployment.
Along similar lines, strive to ensure that you can roll back to an earlier release quickly if you identify a security issue with a production app. Ideally, that will never happen, but it may, and you should be prepared to fix it with as little disruption to users as possible.
Get the Right Tools
People and processes will go a long way toward helping you secure your cloud workloads, but you also need the right tools. The final item on your cloud security checklist should be to evaluate your current toolset and determine whether it is still meeting your cloud security needs.
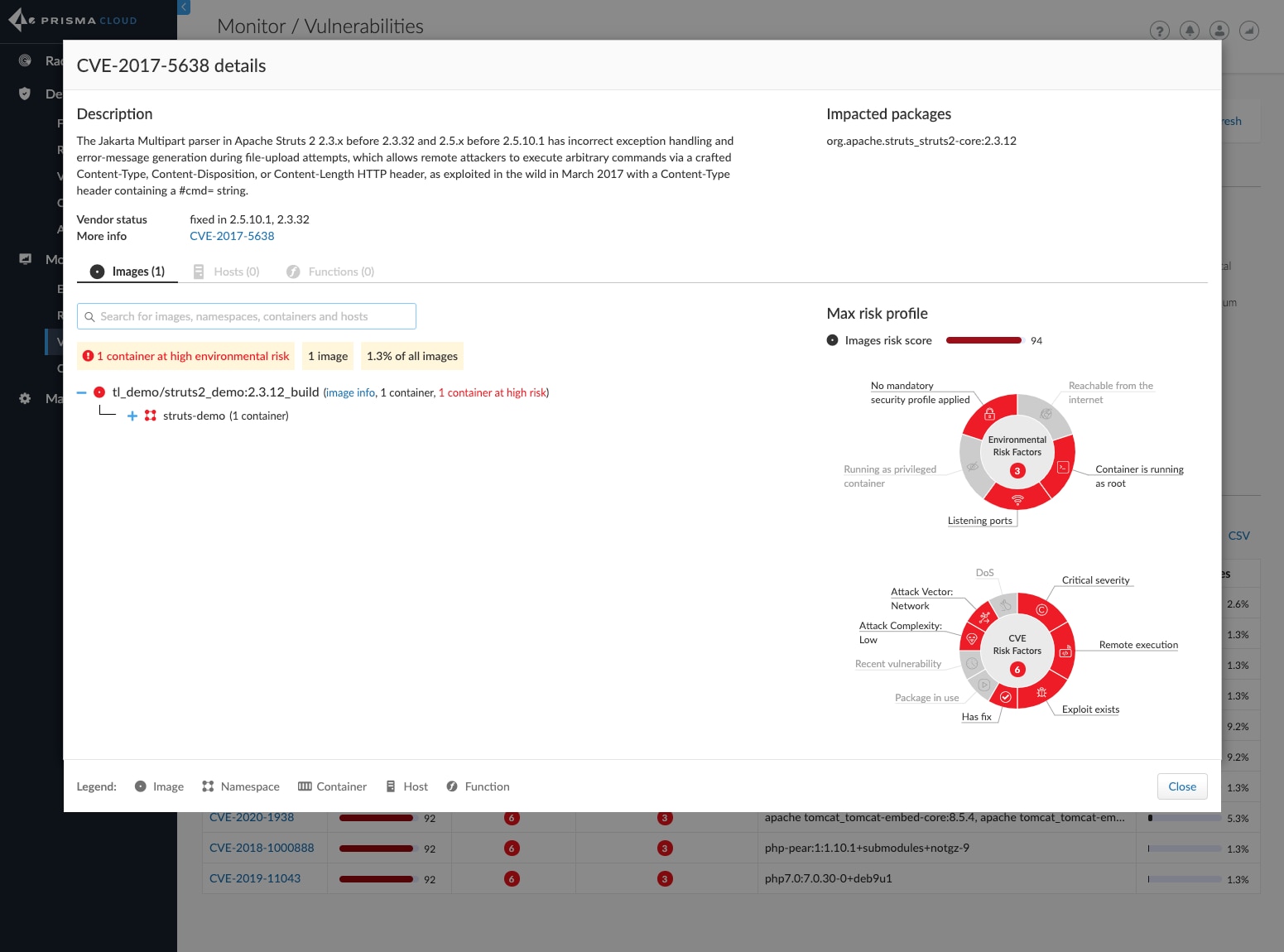
The best cloud native security platforms envelop the entire CI/CD lifecycle and integrate with all stages of the DevOps workflow. They offer visibility and protection across the entire stack, anywhere it exists. Automated detection and response, CI/CD scanning, and policy and compliance governance should be baked into your cloud security toolset.
Improving Your Cloud Security Checklist
Your cloud security checklist should be tailored to your needs, of course. There’s no one-size-fits-all checklist that is exhaustive, and the considerations you assess will vary depending on factors such as whether you use one cloud or multiple clouds, and whether you have a hybrid strategy or have migrated everything to the cloud. Nonetheless, the checklist points above are a good starting point for evaluating how secure your cloud workloads are at present, and how you can improve them continuously over time.
Most importantly, do your best to avoid the more persistent myths about cloud security. Check out our webinar 3 Myths of Cloud Native Security to learn a few that come up frequently.