Organizations rely on technology to carry out their operations. As the number of users and systems grows, managing access to resources becomes critical. Here’s where identity and access management (IAM) comes in, allowing organizations to control who has access to what resources and when.
Using out-of-the-box (OOTB) IAM policies, though, may not meet an organization's needs. Customizing IAM policies, on the other hand, is key to securing your unique environment.
Customizing IAM policies allows an organization to hone their access control policies to meet their specific requirements. This enables organizations to make sure that users have the appropriate access to resources while ensuring that sensitive information is kept secure.
With OOTB IAM policies, organizations may find themselves in one of two situations — granting unnecessary access to users or restricting access to necessary resources. Customization provides the flexibility to determine the level of access needed for each user or group, making sure that all users can do their jobs effectively.
Custom IAM Policies Help Organizations to Comply with Regulatory Requirements
Industries have different regulations, and each organization's interpretation of those regulations can differ. Customizing IAM policies enables organizations to set access control policies that align with their regulatory requirements, avoiding non-compliance penalties and mitigating security risks.
Customizing IAM Policies Can Reduce the Risk of Insider Threats
Insider threats occur when individuals within an organization misuse their access to resources, intentionally or unintentionally. Customization allows organizations to set up policies that prevent users from having more access than necessary, reducing the risk of insider threats. By limiting access to only what’s required, organizations can reduce the potential damage caused by an insider threat.
Customizing IAM Policies Can Help Organizations Simplify Access Management
Because OOTB policies aren’t always suitable for the organization's unique requirements, relying on them often leads to a more complex access management process. Customization simplifies this process by enabling organizations to set up policies tailored to specific needs. This simplification can save organizations time and resources, allowing them to focus on their core business functions.
Factors to Consider When Creating a Custom Policy
When creating a custom IAM policy, consider several factors to ensure the policy aligns with your organization's unique needs while maintaining security and compliance. Key considerations include:
- Granularity: Determine the appropriate level of granularity for your policy. Avoid creating overly permissive policies that grant broad access, as this increases the risk of unauthorized access and potential data breaches. Instead, follow the principle of least privilege, granting users the minimum necessary permissions to perform their tasks effectively.
- Resource Scope: Identify the specific resources and services to which the policy should apply. Consider whether the policy should apply globally across all resources or be limited to specific regions, accounts or services. Adjusting the resource scope allows for targeted access control and reduces the risk of inadvertently granting access where it's not needed.
- User and Group Considerations: Take into account the different roles and responsibilities within your organization. Create policies that align with these roles, granting appropriate permissions based on job functions and responsibilities. Consider using groups to manage permissions more efficiently, allowing for easier policy maintenance and updates.
- Policy Hierarchy: Understand the hierarchy of IAM policies and how they interact with each other. Policies are evaluated in a specific order, and conflicting permissions can result in unexpected access. Ensure that custom policies are properly prioritized and consider any inherited permissions from higher-level policies to avoid unintended consequences.
- Regular Review and Updates: IAM policies should not be set in stone. As your organization evolves, roles change and new services are adopted. It's crucial to routinely review and update policies. Conduct regular assessments to ensure that policies still align with business requirements and adhere to security best practices.
- Testing and Validation: Before deploying a custom IAM policy, thoroughly test it in a controlled environment to verify it works as intended. Validate the policy against different use cases and scenarios to ensure that it provides the desired level of access control without impeding legitimate user activities.
- Audit and Monitoring: Implement robust auditing and monitoring practices to track policy changes, permissions granted, and user activity. This allows for proactive detection of potential security issues, unauthorized access attempts or policy violations. Regularly review audit logs to identify anomalies or suspicious activities.
- Documentation and Communication: Document the purpose and rationale behind each custom policy. This documentation serves as a reference for policy administrators, auditors and compliance teams. Communicate policy changes to users and provide them with the necessary guidance on how to comply with new policies.
By considering these factors when creating custom IAM policies, you can ensure that your policies are well designed, aligned with your organization's unique needs, and provide the necessary level of access control while maintaining security and compliance.
How to Create a Custom IAM Policy in Prisma Cloud
Now let’s take a look at how you can create a custom IAM policy in Prisma Cloud. You have two approaches you could take.
Add a New Policy with the “Add Policy” Action on the “Policies” Page
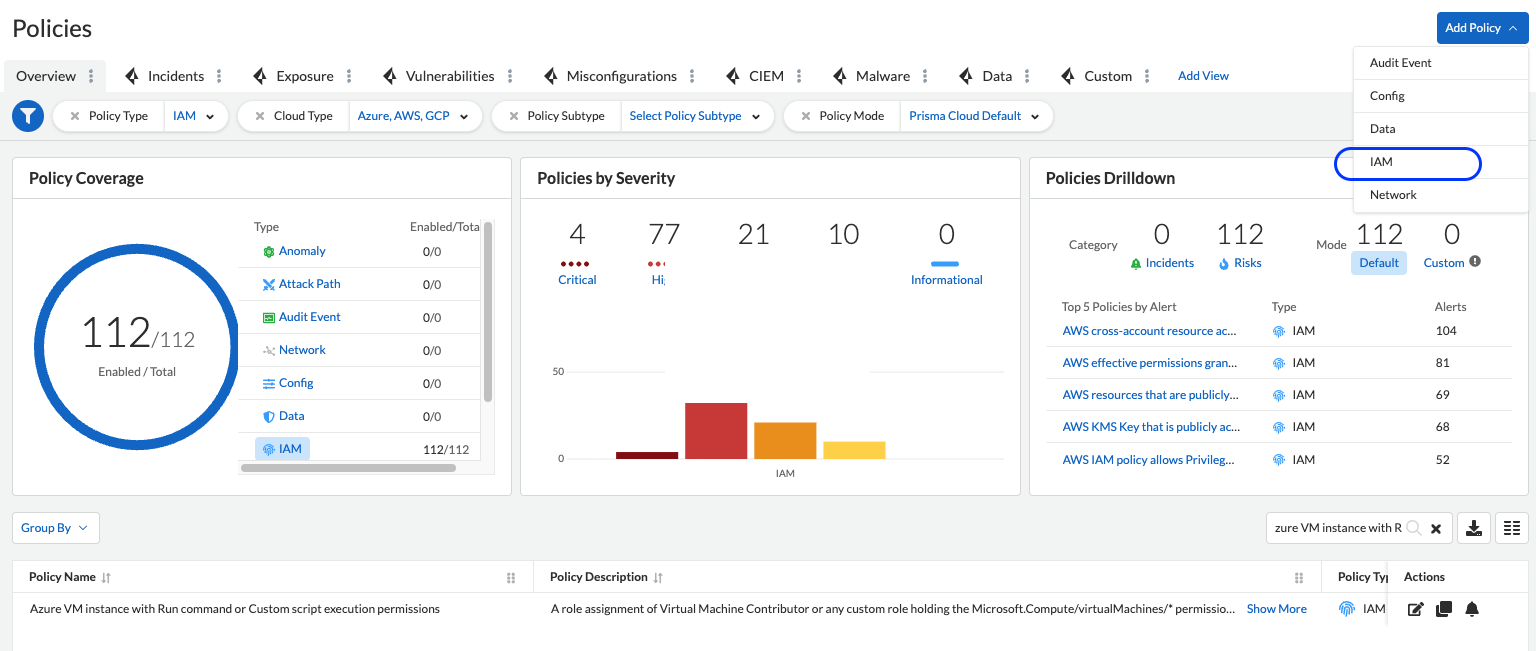
Go to the “Policies” page and click on the “Add Policy” button, then select IAM.
If you have a specific use case you want to address with Prisma Cloud Alert, you can utilize this option to initiate a clean start.
Clone an Existing OOTB IAM Policy
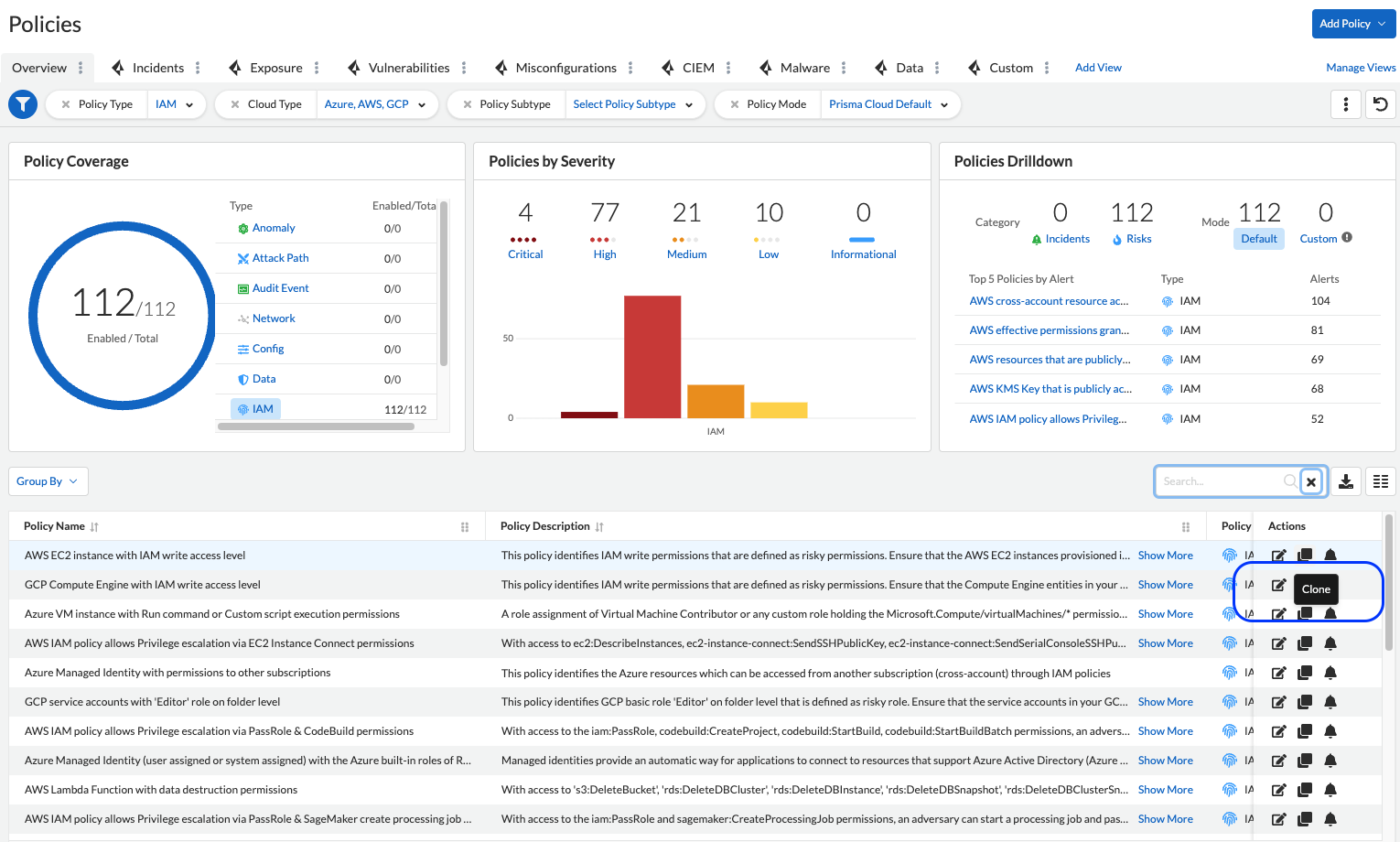
Go to the “Policies” page and find an existing IAM OOTB policy that you want to clone. Then click the “Clone” button. It’s that simple.
If you’d like to exclude specific resources, or if you need to add company-facing conditions to the current IAM OOTB policy, use this option.
Learn More
With customized IAM policies, organizations can ensure that users have appropriate access, comply with regulatory requirements, reduce the risk of insider threats, and simplify the access management process.
If you’d like to learn about the CIEM capabilities of Prisma Cloud, take it for a free 30-day test drive.