As the cloud continues to dominate the operating landscape, it has also revolutionized identity and access management, giving rise to new challenges — particularly with the proliferation of identities required by users, applications, services, and devices. The vast number of permissions available to grant identities, combined with a significant portion of high-risk, highlights the mounting challenge organizations face in managing access to data across cloud platforms.
“Managing cloud permissions is challenging due to the number of assets and diverse authorization systems, worsened by the explosion of machine identities,” says Gartner®. “Security and risk management leaders must combine traditional IAM and cloud security approaches with CIEM for efficient identity-first security.”
Gartner recently published its 2023 Innovation Insight: Cloud Infrastructure Entitlement Management (CIEM), which offers valuable insights for security and risk management leaders tasked with shaping cloud security strategies. By leveraging this research, professionals can evaluate CIEM capabilities, enabling them to make informed decisions and implement effective solutions to enhance their organization's cloud security posture.
Download your copy of the 2023 Innovation Insights: CIEM.
Fortifying Cloud Security with CIEM
CIEM delivers essential visibility and a simplification of the process of identifying and addressing potential vulnerabilities. Depicted by Gartner, “CIEM capabilities help enterprises manage cloud access risks via administration-time preventive controls for the governance of entitlements in hybrid and multicloud infrastructure as a service (IaaS) and platform as a service (PaaS). They use analytics, machine learning (ML) and other methods to discover anomalies in account entitlements, like accumulation of privileges, and dormant and unnecessary permissions. Leading CIEM capabilities enforce least-privilege policies and remediate violations.”
Gartner lists these four core uses of CIEM:
- Visibility of entitlements
- Removing unused entitlements
- Discovering other types of anomalies
- Compliance automation
CSPM and CIEM: Better Together
While traditional cloud security posture management (CSPM) focuses on identifying misconfigurations in security settings for cloud-native services, CIEM focuses on identity management. When these two tools are integrated, working together, configuration data can be correlated to prioritize actionable insights and analyze attack paths. For example, an overly-permissive identity (identified from CIEM) is riskier when associated with a publicly accessible cloud-native service (determined by CSPM) than an internal resource.
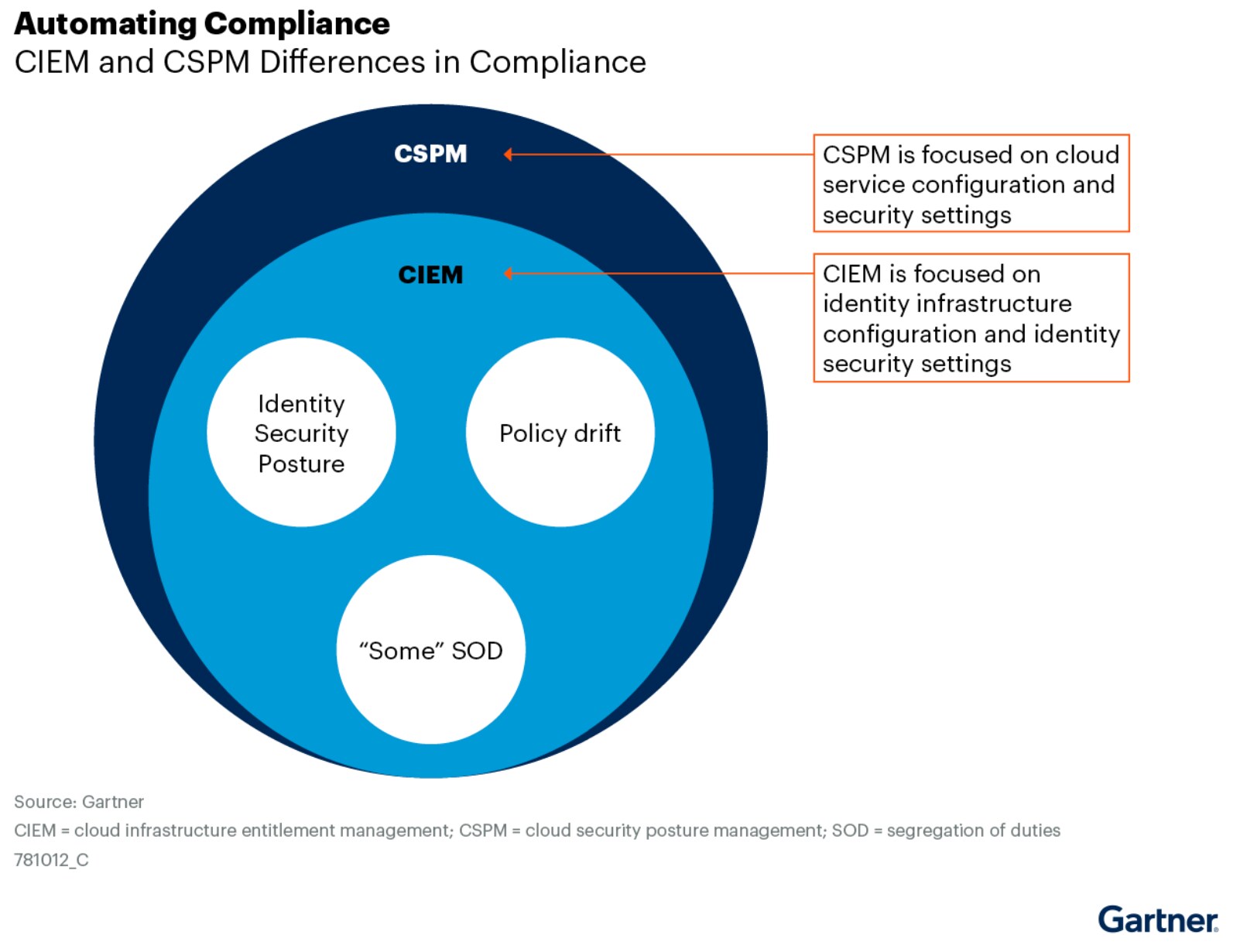
Recommendations for Security Leaders
The Gartner Innovation Insight offers several recommendations for security leaders evaluating CNAPP solutions. Palo Alto Networks has excerpted a few we consider paramount to securing your applications.
- Focus on evaluating CIEM capabilities if you have a multicloud ecosystem to mitigate the risks of inconsistently defined and configured cloud permissions.
- Use CIEM as part of a broader IAM and cloud security strategy. It can’t replace full-featured IGA and PAM technologies, especially in organizations with lots of legacy and on-premises resources, nor can it replace traditional CSPM.
- Use CIEM to manage entitlements of machine and human identities.
- Use CIEM’s advanced analytics for simplifying dynamic privilege management with reduced manual input.
- Leverage CIEM in DevSecOps and infrastructure-as-code to provide visibility into unnecessary privileges and refining policies without disrupting developer flows.
Prisma Cloud Delivers Cloud Infrastructure Entitlement Management
Prisma Cloud’s CIEM module delivers simple, consistent IAM across Amazon Web Services (AWS), Microsoft Azure and Google Cloud Platform (GCP). Accurately calculating net-effective permissions, Prisma Cloud helps organizations understand their multicloud identity risk, including identities managed with IdPs and SSO tools, such as Azure AD.
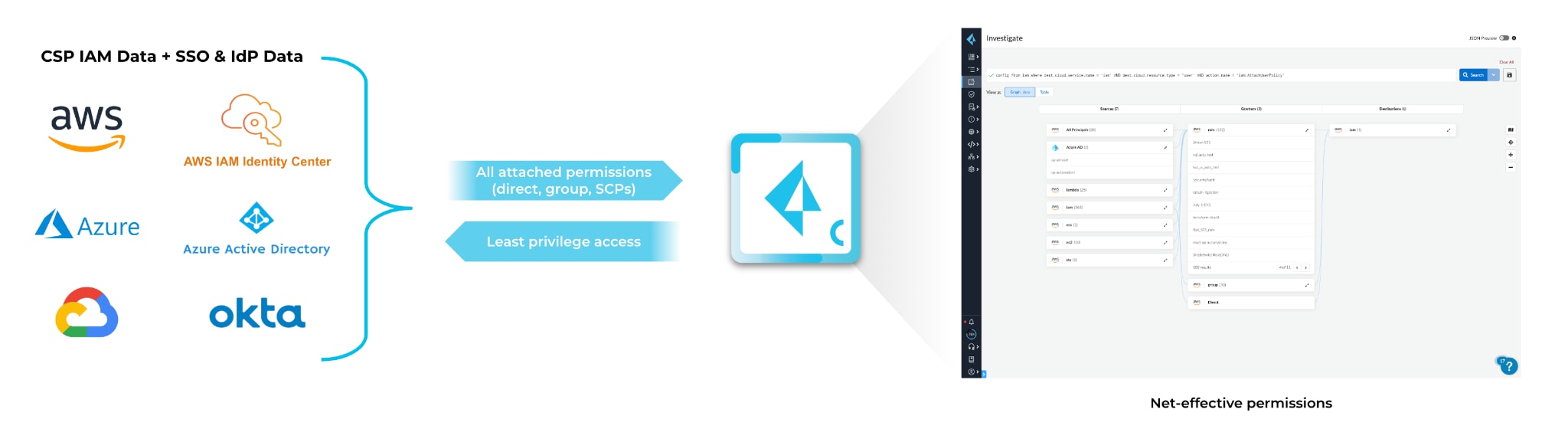
Organizations can rightsize permissions and employ automated remediation to continually adjust permissions, reducing the attack surface. Additionally, Prisma Cloud provides intelligent graph visualizations that enable IAM practitioners to see who has access to what across cloud environments.
By integrating CIEM into its cloud-native application protection platform (CNAPP), Prisma Cloud ensures the security of applications from code to cloud across multicloud environments. The platform provides comprehensive security, continuous visibility, and proactive threat prevention throughout the application lifecycle. As a result, Prisma Cloud facilitates effective collaboration between security and DevOps teams, accelerating secure cloud-native application development and deployment.
In short, Prisma Cloud's code-to-cloud coverage addresses security needs at every stage of the cloud journey, covering code, infrastructure, workloads, data, networks, web applications, and APIs. With over 4 billion cloud assets secured and 1 trillion cloud events processed daily, you can trust Prisma Cloud to protect your cloud environments at any scale.
Palo Alto Networks is proud to be recognized by Gartner as a Representative Provider for CIEM.
Learn More
You won’t want to miss the Gartner research on CIEM. Read Innovation Insight: Cloud Infrastructure Entitlement Management (CIEM) today.
Gartner, Innovation Insight: Cloud Infrastructure Entitlement Management, by Henrique Teixeira, Abhyuday Data, Michael Kelley, 11 May 2023
GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally, and is used herein with permission. All rights reserved.
Gartner does not endorse any vendor, product or service depicted in its research publications and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s Research & Advisory organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.