- What Is Cloud Native?
- What Is Threat Modeling?
- What Is CNAPP?
- CSP-Built Security Vs. Cloud-Agnostic Security
- What Are Microservices?
- What Is Cloud-Native Security?
- What Is Cloud Network Security?
- What Is Microsegmentation?
-
Core Tenets of a Cloud Native Security Platform (CNSP)
- What Is a Cloud Native Security Platform?
- CSPM Tools: How to Evaluate and Select the Best Option
- What is Platform as a Service (PaaS)?
-
What Is Serverless Security?
What Is CSPM?
Cloud security posture management (CSPM) is the practice of controlling public cloud infrastructure risk. CSPM tools automate the detection and remediation of misconfigurations across cloud resources (e.g., Amazon EC2 instances). Organizations use CSPM in public cloud and multicloud environments to reduce the likelihood of breaches and improve regulatory compliance.
Cloud Security Posture Management Explained
Cloud security posture management (CSPM) is a means of mitigating risk and compliance violations by identifying and remediating misconfigurations across public cloud environments. CSPM tools help security and compliance teams by providing automated visibility, continuous monitoring, and remediation workflows for their infrastructure as a service (IaaS), platform as a service (PaaS) and software as a service (SaaS).
Organizations generally adopt CSPM as a standard security practice when they migrate their applications to various cloud providers, such as Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP). As part of the cloud security shared responsibility model, CSPM tools help client organizations in many ways.
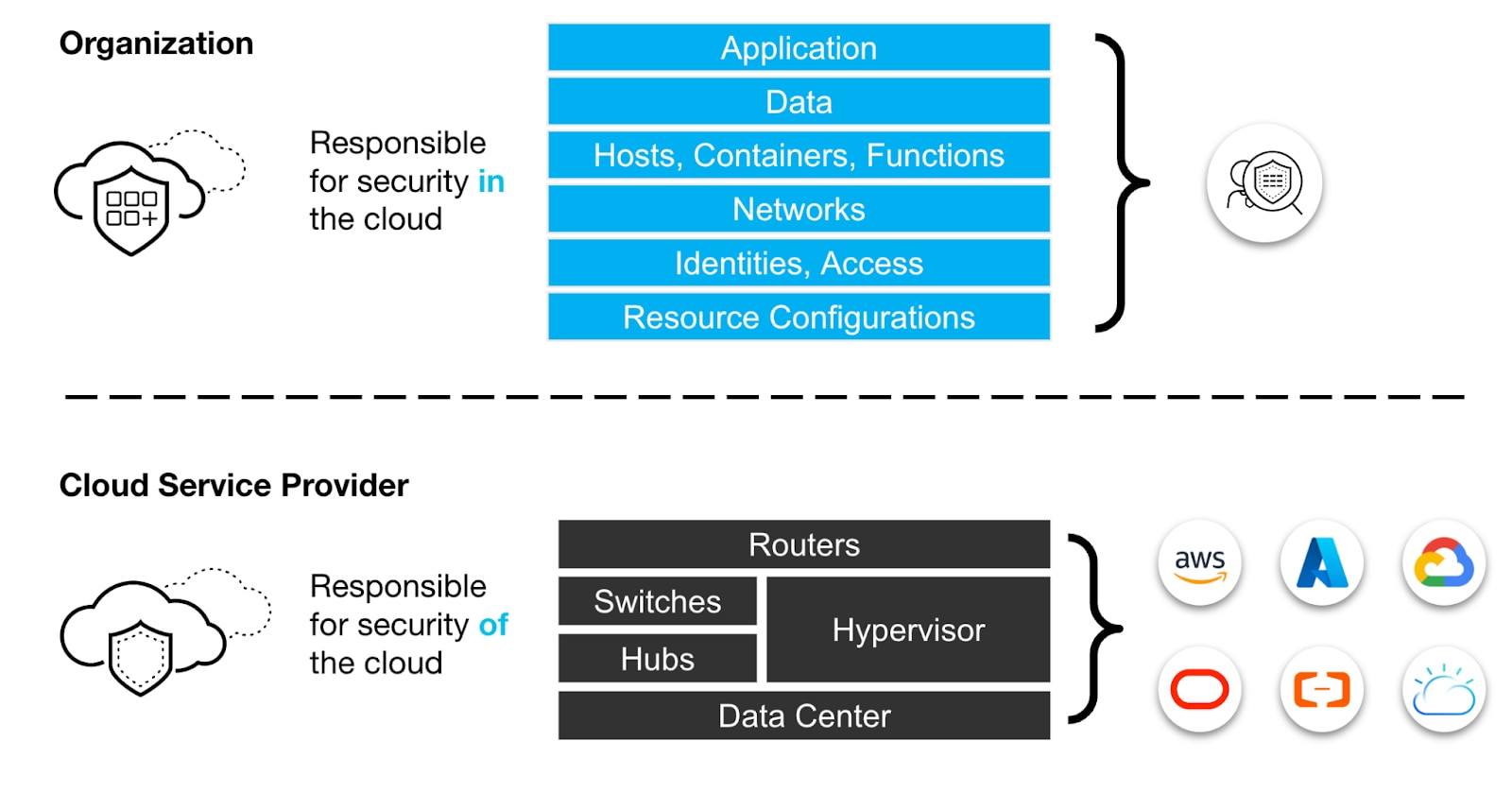
Why Is CSPM Important?
CSPM becomes crucial as companies increasingly adopt public cloud infrastructure, such as AWS, Microsoft Azure, and GCP. Public and multicloud infrastructure enables IT and development teams to rapidly configure and deploy services and applications, ultimately accelerating innovation.
This shift, while beneficial, naturally results in risky cloud configurations, also known as cloud misconfigurations. Cloud misconfigurations can lead to unwanted outcomes including data breaches or hefty fines for violating regulatory compliance.
Organizations adopting cloud infrastructure are responsible for practicing CSPM, but wIthout a CSPM tool, security teams face significant challenges:
Multicloud Complexity
Each cloud provider offers different infrastructure architectures and taxonomy for security teams to learn and manage. Amazon VPC and Azure VPN, for example, are virtual networks that have unique nuances. Cloud providers frequently release new services, challenging security teams to keep pace.
CSPM tools can detect, unify and normalize cloud provider services into a single console reducing complexity for security teams.
Security Blind Spots
Organizations often find it challenging to achieve visibility into their cloud environments, which leaves them unable to answer questions such as:
- What cloud services does my organization use?
- Who made changes to cloud resources? What changes did they make? When did the changes happen?
- What cloud misconfigurations exist in my cloud environment?
- Is my organization maintaining compliance requirements?
With a CSPM tool, security teams get visibility into cloud resources, configuration changes, risks, compliance violations and more.
Compliance Obligations
Many businesses adopting cloud infrastructure have regulatory compliance requirements mandating specific security measures — PCI DSS, GDPR, SOC 2, and HIPAA, to name a few. Any lapse in maintaining proper cloud configurations can lead to noncompliance, potentially resulting in hefty fines, legal repercussions, and damage to a brand’s reputation.
CSPM tools can help businesses ensure that their cloud infrastructure meets these compliance requirements. For starters, CSPM tools automatically compare cloud configurations against regulatory controls to detect compliance violations and provide remediation guidance. Some solutions include compliance reporting, allowing security teams to produce audit-ready reports in minutes.
Poor Developer Experience
A benefit of adopting cloud infrastructure in enabling agility, but security teams are seen as an obstacle to development teams. According to Gartner, “Security teams are perceived as slowing down modern DevOps style development.” Modern CSPM practices require security teams to collaborate with developer and DevOps teams to remediate misconfigurations. Traditional security tools weren’t designed with this in mind. As a result, they generate excessive low-risk alerts for developers to address.
Modern CSPM tools can improve security and developer collaboration by prioritizing misconfigurations with context and augmenting remediation steps.
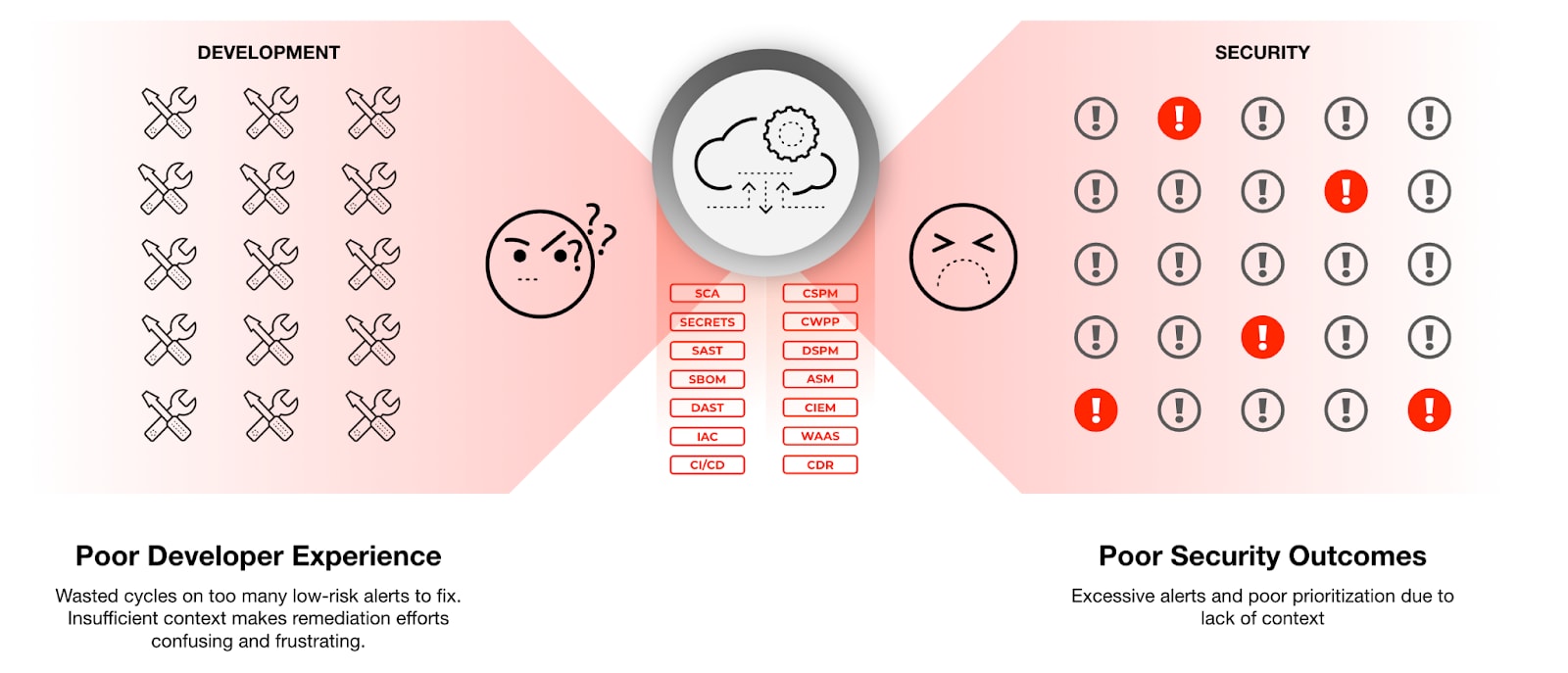
Employing a CSPM solution is a first step to securing cloud infrastructure and keeping private data secure. Cloud-native computing is here to stay, and cloud security posture management tools play a critical role in providing vital visibility and control over cloud infrastructure.
Related download: Guide to Cloud Security Posture Management Tools
How Does CSPM Work?
Understanding the mechanics of CSPM is essential to appreciate its role in enhancing cloud security. The following section explores how CSPM helps secure cloud infrastructure.
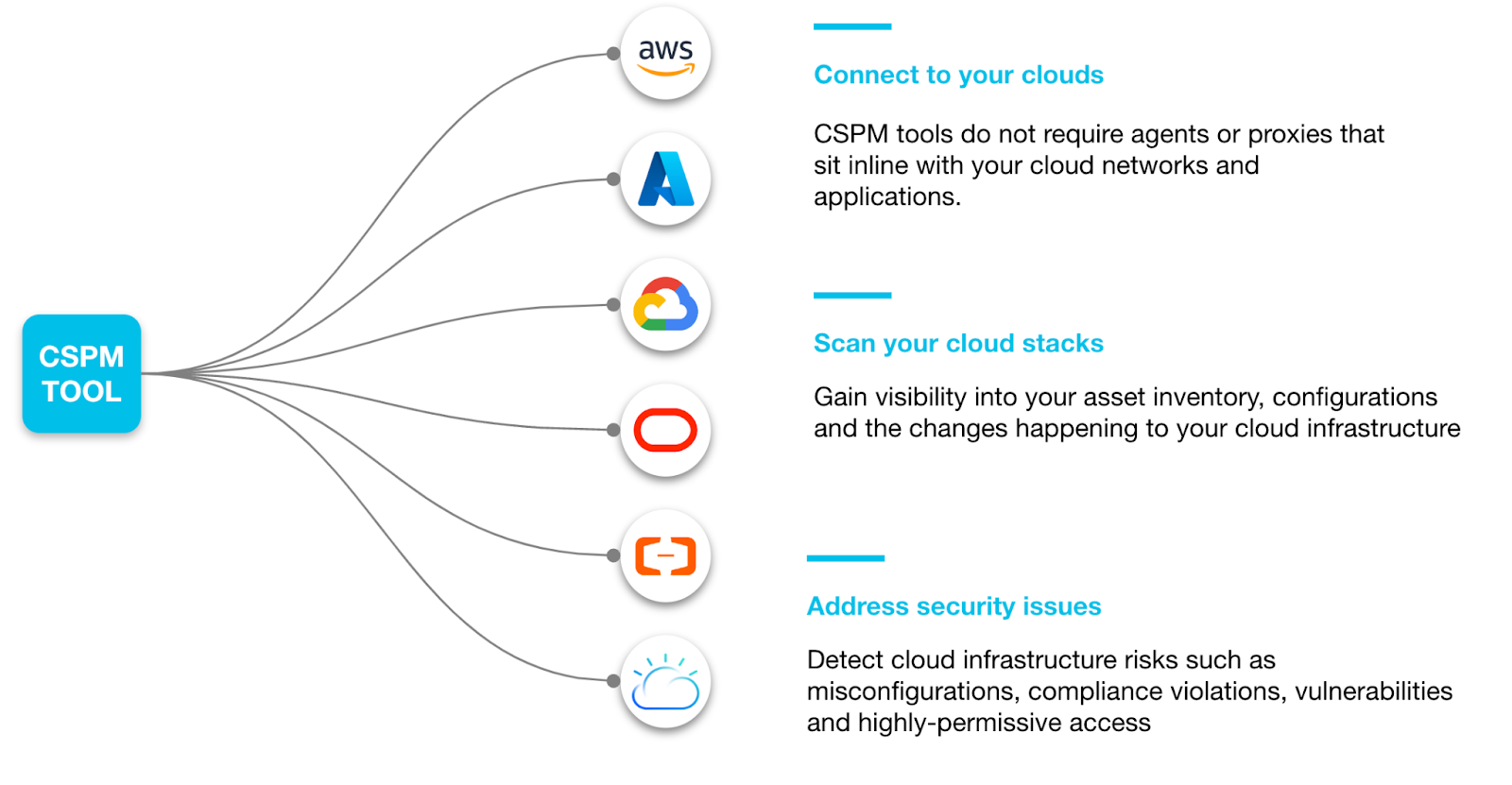
Connect to Your Cloud Environments
Unlike many security approaches that require agents or proxies, CSPM solutions connect to your cloud providers APIs for visibility, also known as agentless security. Organizations must grant access to their CSPM tools within their cloud providers. CSPM tools offer automated workflows, generating the permissions needed for effective posture management. Many CSPM providers give organizations the flexibility to choose between read-only access for just visibility and minimal read-write permissions for visibility and automated remediation.
Nearly all offerings support AWS, Azure, and GCP and some support additional cloud providers including Oracle, Alibaba, and IBM Cloud.
Get Visibility
Once connected, CSPM solutions use the API-based connectivity to give you visibility into your cloud asset inventory, configurations, audit trail (configuration changes), network communications, and cloud events.
Identify Misconfigurations and Compliance Violations
CSPM tools come with out-of-the-box configuration checks, also known as policies that compare your cloud resources and configurations against security controls. Typically, the policies will map to an industry best practice framework (e.g., CIS, MITRE ATT&CK) or regulatory compliance (e.g., PCI DSS, HIPAA). CSPM tools often come with hundreds of policies mapping to dozens of frameworks.
Anytime a configuration matches a defined policy, a CSPM solution will identify this as a misconfiguration and alert security teams.
Examples of Misconfigured Services
- Amazon EC2 instance has IMDSv2 disabled
- Azure Kubernetes Service endpoint is publicly accessible
- GCP API key not rotating in every 90 days
Detect Threats
Traditional security approaches require proxies and agents to detect threats such as malware, network attacks and data exfiltration. With CSPM, security teams can detect compromises in action just by using the telemetry from your cloud providers such as network traffic (e.g., Amazon VPC flow logs), events (e.g., AWS CloudTrail event logs).
Using policies, and artificial intelligence in some cases, CSPM solutions continuously inspect logs and events to detect anomalies and suspicious activity. Some tools will map incidents to the MITRE ATT&CK tactics for enhanced visibility and prioritization.
An effective CSPM must maintain high-fidelity threat intelligence to identify the latest threats and assess their severity level. The ability to detect anomalies on the network and correlate them with other types of threat data is also important for gaining full context on the potential risk impact of any threat. The same must be done with user and entity behavior analytics (UEBA) data.
Contextualize Risks
While policies help security teams identify misconfigurations and compliance issues, many enterprises will have thousands of misconfigurations, creating a need for risk prioritization. That’s why many CSPM offerings have expanded into identifying additional risk signals, normally found in other tools, such as vulnerabilities, highly permissive access, active threats and more.
Backed by graph database technologies, present-day CSPM tools contextualize misconfigurations with additional findings that together form potential attack paths. Like individual misconfigurations, modern CSPM offerings typically include out of the box policies that identify attack paths. Since combined issues pose a greater threat than individual misconfigurations, security teams use contextualized risk to improve their prioritization efforts.
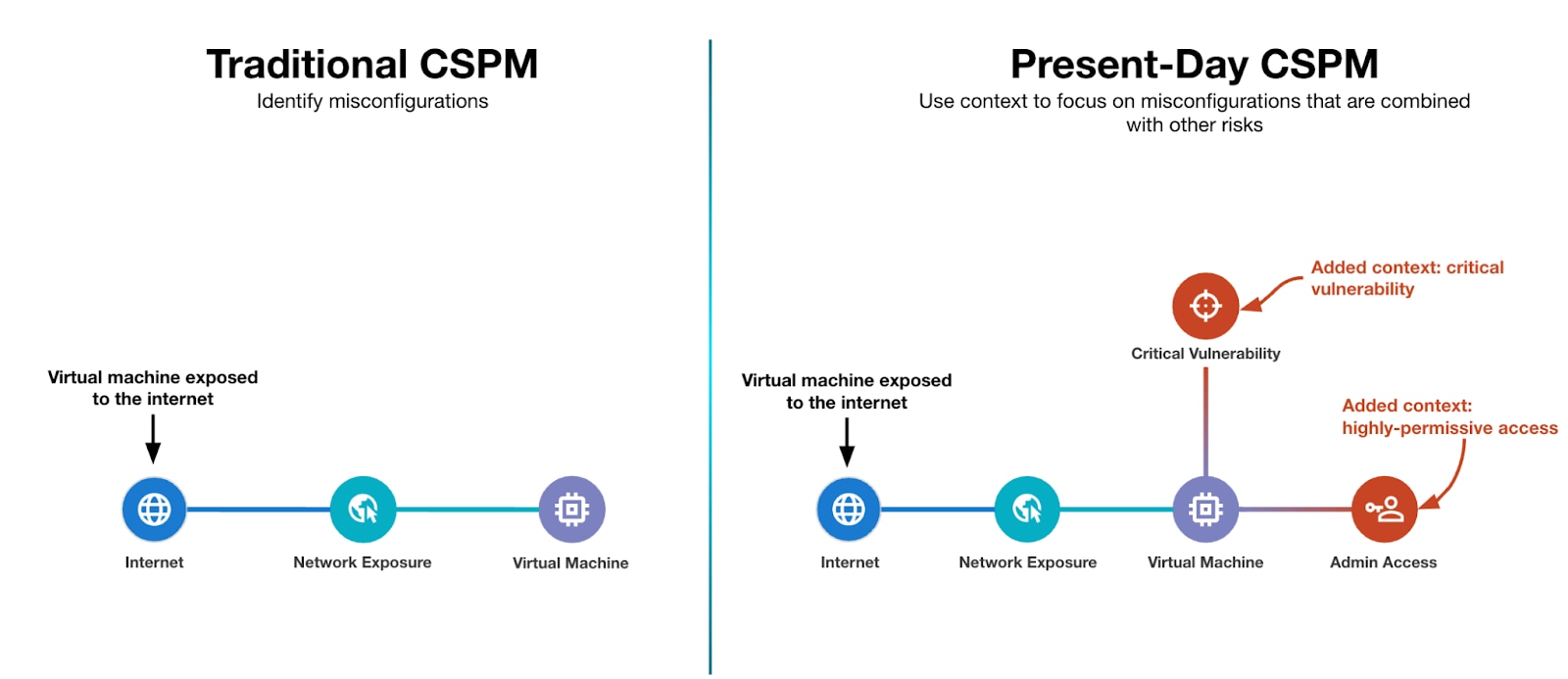
Remediate Issues
At minimum, CSPM solutions provide step-by-step remediation instructions which security teams can forward to the teams responsible for the misconfiguration for improved collaboration.
CSPM solutions should integrate with external platforms like SIEM, SOAR, ticketing systems and collaboration tools (e.g., Slack) allowing security teams to stream alerts and remediation feedback to the right teams.
In some cases, security teams can automatically remediate violations from their CSPM console to facilitate rapid response.
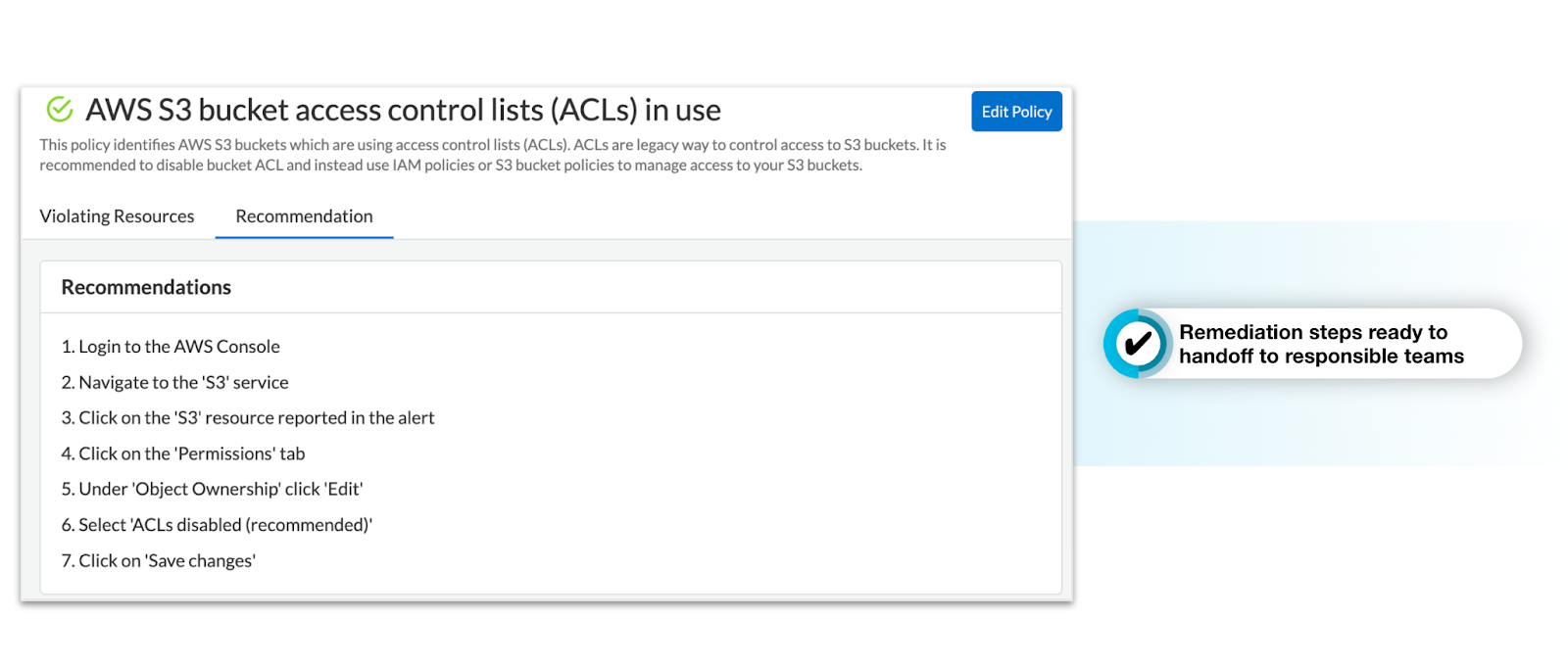
Monitor and Report
As security teams repeatedly identify and remediate cloud infrastructure misconfigurations, they should notice downward risk trends over time.
CSPM tools with built-in reporting capabilities help security teams verify their efforts and communicate with key stakeholders. For organizations running regulated applications on public cloud infrastructure, they can leverage CSPM to answer compliance posture questions like:
- Am I passing or failing my compliance checks?
- What percentage of my environment is compliant?
- Which resources are noncompliant and how can I address it?
CSPM solutions offer the ability to produce easily consumable reports. With a click of a button, security teams can generate a PCI DSS v4.0 report in PDF format, illustrating each PCI control and confirming that their cloud infrastructure complies with each control. From the CSPM tool, teams can hand off the report to a compliance expert for easy auditing or send it to a developer to communicate compliance concerns and prioritize remediation efforts.
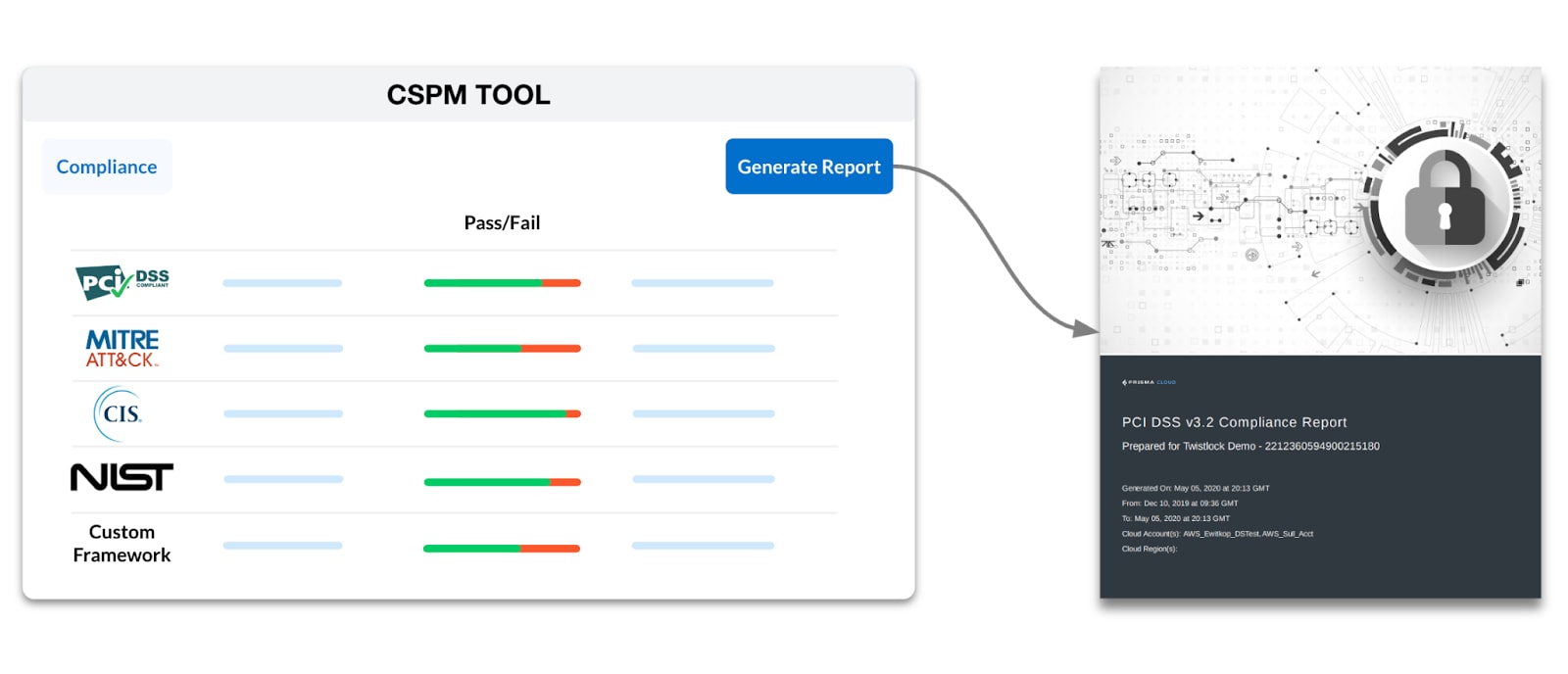
The Evolution of CSPM
CSPM is unsustainable as a standalone product and capabilities have been absorbed into adjacent markets or into a platform. This has forced the CSPM scope to include more than just visibility, compliance, and governance. The table below compares present-day and traditional CSPM.
| Present-day CSPM | Traditional CSPM | |
|---|---|---|
| Asset Inventory |
✓ |
✓ |
| Audit trail of configuration changes |
✓ |
✓ |
| Misconfiguration detection |
✓ |
✓ |
| Compliance violation detection |
✓ |
✓ |
| Automated remediation |
✓ |
✓ |
| Audit-ready reporting |
✓ |
✓ |
| Network flow visibility |
✓ |
✓ |
| API discovery and visibility |
✓ |
|
| Threat detection — suspicious behavior, network anomalies |
✓ |
|
| Effective network exposure |
✓ |
|
| Risk context — correlate misconfigurations with vulnerabilities and other findings |
✓ |
|
| Integrated agentless workload scanning |
✓ |
|
| Integrated with cloud infrastructure entitlement management (CIEM) |
✓ |
|
| Integrated with data security posture management (DSPM) |
✓ |
|
| Integrated infrastructure-as-code scanning |
✓ |
|
| Integrated internet attack surface scanning |
✓ |
|
| Cloud provider coverage | AWS, Azure, Google, Oracle, Alibaba, IBM | AWS, Azure, Google |
| Frequency of visibility updates | Near-real time (within minutes or seconds) | Snapshots (1-2 times a day) |

CSPM Vs. Other Solutions
With numerous product categories available in the market, security professionals should understand the scope of various cloud security solutions. Below are examples of common security controls that have similarities or overlap with CSPM.
What Is the Difference between CASB and CSPM?
Cloud access security broker (CASB) solutions filter network traffic to and from cloud services and SaaS applications to protect data. CSPM focuses on securely configuring cloud infrastructure. Unlike CASB, CSPM tools don’t sit inline with the network, filter traffic, nor do they focus on SaaS applications.
What Is the Difference Between Cloud Security and CSPM?
The scope of cloud security is much broader than CSPM, encompassing the security of applications, data, identities, networks, and infrastructure within cloud environments. CSPM detects and remediates misconfigurations across cloud infrastructure. Many organizations adopt CSPM early in their cloud journey and believe it is an important first step for cloud security.
What Is the Difference Between CNAPP and CSPM?
Cloud-native application protection platform (CNAPP), a term coined by Gartner, is an integrated set of cloud security and compliance capabilities designed to help secure and protect cloud-native applications across development and production. Core capabilities of a CNAPP include:
- Cloud security posture management (CSPM)
- Cloud workload protection platform (CWPP)
- Code security
- Web application and API security (WAAS)
- Cloud infrastructure entitlement management (CIEM)
- Data security posture management (DSPM)
These core functionalities within a CNAPP give security teams comprehensive visibility of public cloud infrastructure across the entire application development lifecycle. When initially adopting a platform at the early stages of their cloud journey, most organizations begin with CSPM.
What Is the Difference Between CWPP and CSPM?
Cloud workload protection platforms (CWPP) protect cloud compute instances such as hosts (e.g., Linux, Windows), containers (e.g., Kubernetes), and serverless functions (e.g., Amazon Lambda) against threats. The scope of CWPP is vulnerability management, compliance, and runtime protection for compute instances while CSPM tools identify and remediate cloud infrastructure misconfigurations.
Market trends show that organizations are increasingly adopting CSPM and CWPP together. According to Gartner, “By 2025, 60% of enterprises will have consolidated cloud workload protection platform (CWPP) and cloud security posture management (CSPM) capabilities to a single vendor, up from 25% in 2022.”
What Is the Difference Between CIEM and CSPM?
While CSPM expands visibility, governance and compliance into cloud resource configurations, it doesn't typically deliver deep identity controls or access governance. This is where cloud infrastructure entitlement management (CIEM) can help.
CIEM tools focus on identifying cloud identity risks and managing entitlements for accessing cloud infrastructure. Together, CSPM and CIEM technologies can help manage the security posture of cloud infrastructure via configuration and entitlement management.
What Is the Difference Between SIEM and CSPM?
Security information and event management (SIEM) aggregates security events from several different IT infrastructure sources (cloud, network, identity, etc.) to detect and mitigate threats. CPSM identifies security risks across cloud infrastructure. Most CSPM solutions can export findings to SIEM tools for further analysis and response.
What Is the Difference Between DSPM and CSPM?
Data security posture management is the practice of protecting sensitive data hosted within cloud environments. Through techniques like data discovery, data classification, and data governance.
Both DSPM and CSPM provide visibility, detect and remediate misconfigurations and aid compliance, but CSPM focuses on the cloud infrastructure configuration. DSPM focuses on the data hosted in the cloud.
What Are Researchers Saying About CSPM?
Gartner on CSPM
Gartner offers several research pieces on CSPM, some standalone CSPM research and others bundled into CNAPP research.
According to the 2023 Gartner Market Guide for Cloud-Native Application Protection Platforms, “By 2025, 75% of new CSPM purchases will be part of an integrated CNAPP offering.” The research piece highlights the growing interest in CSPM, saying “The number of end-user calls on CNAPPs grew 70% from 2021 to 2022 with an emphasis on CSPM due to compliance drivers and ease of deployment via APIs.”
Gartner hasn’t conducted a Magic Quadrant report for CSPM but offers other research to help security professionals make informed decisions with CSPM solutions.
Forrester
Despite Forrester’s lack of standalone research articles on CSPM, the firm recognizes CSPM as a core component of Cloud Workload Security (CWS), a platform-based product category for cloud security. Forrester analyzed and scored CWS vendors, including their CSPM capabilities, in The Forrester Wave: Cloud Workload Security Q1, 2024.
GigaOm
GigaOm is one of few research firms that closely research CSPM independently. Their researchers analyzed and scored vendors who they believe are the top CSPM providers in the 2023 GigaOm Radar: Cloud Security Posture Management report.
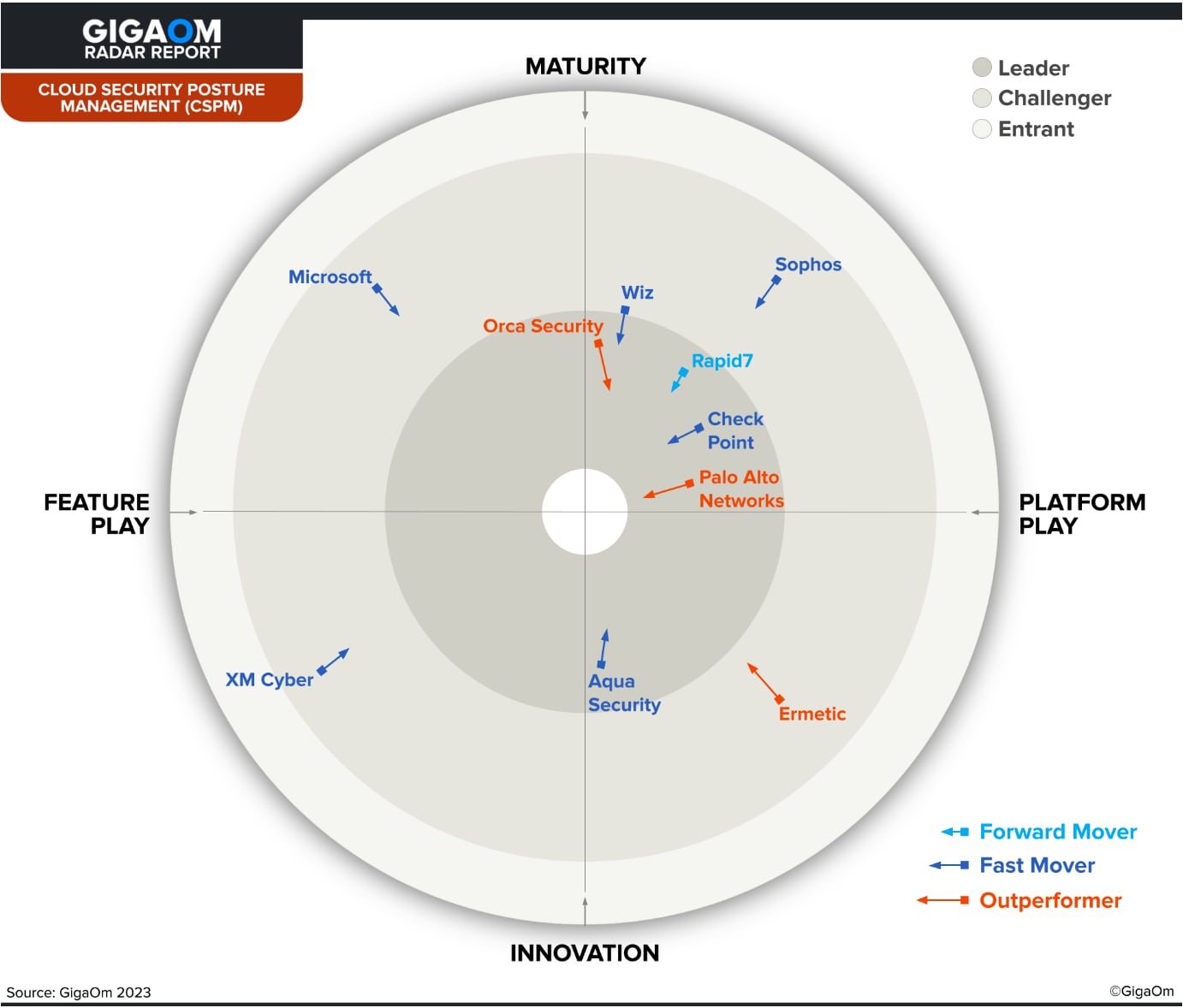
What Are the Benefits of CSPM?
Greater Visibility
Gaining visibility into all cloud services distributed across cloud providers is both essential and challenging. CSPM solutions provide centralized visibility across cloud and multicloud environments by analyzing and normalizing data sources as well as creating a detailed inventory of cloud resources and assets.
Some CSPM solutions provide continuous real-time visibility, while others collect periodic snapshots of cloud asset inventories. A CSPM solution that offers single-dashboard visibility across several clouds is more than convenient. This CSPM platform is immensely valuable to security teams, given that schematics for each cloud provider environment differ.
Reduced Cloud Security Risk
Many CSPM tools contextualize misconfigurations with other cloud security findings such as vulnerabilities, highly permissive access, data risks and more. By correlating these findings, security teams can prioritize cloud risks with the greatest impact to their business. Remediation guidance and automation built into CSPM tools help security teams address critical risks quicker.
Improved Regulatory Compliance
Governance and compliance teams using the cloud and dealing with stringent compliance regulations — PCI DSS, GDPR, SOC 2, and HIPAA, to name a few — often struggle to demonstrate compliance to auditors. A CSPM solution can help with compliance monitoring and reporting:
- Continuous monitoring of your compliance posture and automatic mapping against common compliance frameworks
- Quick-generation audit-ready reports, reducing the time to create, share, and consume compliance reports
- Ability for SOC teams to investigate audit data for unusual user behavior or potential account compromise
Cloud Security Posture Management (CSPM) FAQs
Cloud security posture management (CSPM) is one module in the cloud-native application protection platform (CNAPP).
CNAPP, providing a comprehensive and fully integrated approach to cloud security in a single platform, comprises CSPM, cloud workload protection platform (CWPP), application security, and cloud infrastructure entitlement management (CIEM).
When used together, CSPM, DSMP, and DDR solutions provide a comprehensive data security strategy that addresses different aspects of data security. CSPM can ensure the security and compliance of cloud infrastructure, while DSPM can secure sensitive data within the cloud, and DDR can detect and alert in real time when changes occur that increase the risk of data exposure.
CSPM, DSPM, and DDR work together to provide a comprehensive data security solution that addresses cloud infrastructure security, data protection, and real-time response. For example, CSPM can integrate with DSPM to ensure that sensitive data is properly secured. Then DDR focuses on data events happening in real-time, allowing teams to respond when changes occur.
Commonly known as HIPAA, the Health Insurance Portability and Accountability Act of 1996 is a federal law that installed national standards to protect individuals' medical records and other individually identifiable health information — defined as protected health information (PHI). It applies to health plans, healthcare clearinghouses, and healthcare providers electronically conducting certain healthcare transactions.
Penalties for HIPAA violations are issued by the HHS Office for Civil Rights (OCR) and state attorneys general. The OCR can impose a maximum fine of $1.5 million per violation, per year. Depending on the type of violation, covered entities can also be subject to criminal or civil lawsuits.
