As the leading infrastructure as code (IaC) framework, HashiCorp Terraform has paved the way for developers to build and maintain cloud resources more easily. Offered as a service, Terraform Cloud provides everything practitioners, teams, and global businesses need to create and collaborate on infrastructure and manage risks for security, compliance, and operational constraints. The latest innovation in the Terraform family, Terraform Cloud Run Tasks, makes adding third party steps to Terraform Cloud’s continuous integration and continuous deployment (CI/CD) a native experience. This new feature highlights the value HashiCorp has placed on their ecosystem partners.
Run Tasks are the simplest way to integrate with third parties directly within Terraform Cloud. As a Run Tasks beta integration, Bridgecrew was one of the first HashiCorp partners to natively integrate as a step between the Terraform plan and Terraform apply steps.
Today, alongside HashiCorp, Prisma Cloud and Bridgecrew are celebrating the GA launch of Run Tasks. Now, any team using Terraform Cloud can seamlessly add policy-as-code checks to their Terraform pipelines for completely automated security guardrails and feedback.
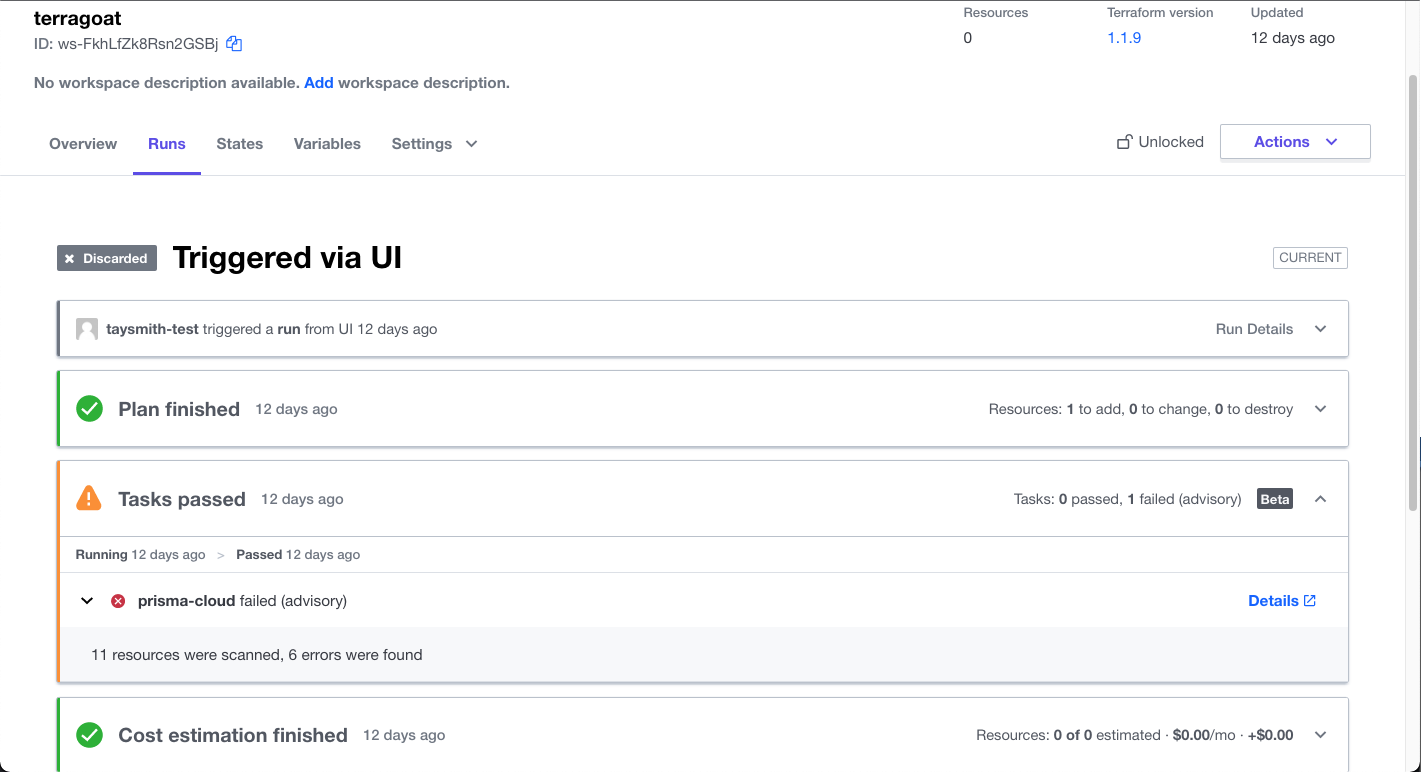
How Prisma Cloud’s Run Task Integration Works
A typical Terraform Cloud workflow includes a run being triggered, either automatically by a developer pushing new code or manually. This is followed by a plan that projects what changes will be made to the running cloud environment. Run Tasks are the next step, running third-party integrations, such as cost estimates or policy-as-code before the final step that applies the code.
Our Run Tasks integration acts as a guardrail to scan against hundreds of built-in IaC security policies and block insecure deployments. For example, if you add a new S3 bucket to a Terraform file and forget to turn on encryption, Terraform Cloud will build a plan for that code and Prisma Cloud’s Run Task will block that code before the apply stage.
In this way, you can ensure that only secure IaC is deployed as cloud infrastructure.
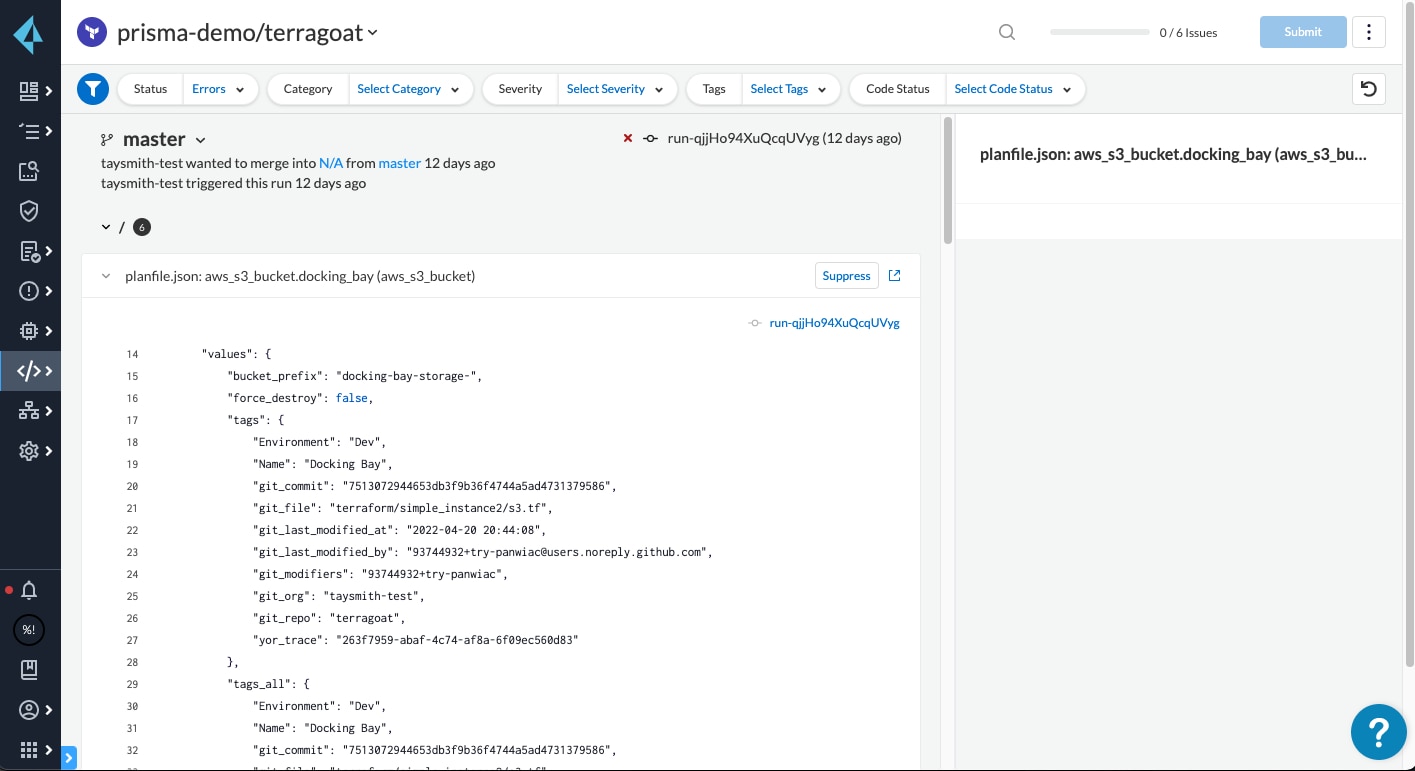
Getting Started with Prisma Cloud’s Run Task
The integration is fully automated and takes only a few steps. First, Prisma Cloud’s Run Task integration uses a webhook to run Terraform plan files against our hundreds of built-in policies and any custom policies you added to the platform and automatically respects suppressions applied in the platform. The results are then sent back to the Prisma Cloud platform to determine if the IaC is secure enough to be applied.
Administrators can choose to set Prisma Cloud in one of two different modes: Mandatory or Advisory. Mandatory mode uses Run Task results to automatically block insecure IaC from being deployed, whereas Advisory mode presents the results as merely informational. The automated workflows create a scalable and repeatable way for security to be embedded in developer workflows.
Note: This integration is available for both Prisma Cloud and Bridgecrew customers. Read more about the Bridgecrew Run Tasks integration here.
Making Security Guardrails More User-Friendly
HashiCorp has greatly simplified integrating new tools into developer workflows with Run Tasks. Prisma Cloud uses our many CI integrations like our Run Tasks integration to bridge the gap between engineering, DevOps, and security and enable engineering teams to deploy more secure cloud infrastructure autonomously.