Cloud security is a data analysis problem. Security teams are inundated with signals and alerts. As an industry, we’ve traditionally relied on point tools that focus on specific types of data, each with their unique scanning capabilities. These tools often come with their own visualizations and languages, which result in a fragmented field of data lacking the correlations needed to prioritize security issues.
Security problems in the real world involve multiple dimensions or multiple areas. Effective security requires an effective data processing layer that ensures meaningful data connections are built. Connecting the dots between data points and resources enables security teams to visualize complex, interconnected security incidents more efficiently. Teams can more readily understand the root causes of critical issues and potential attack paths, which allows for faster investigation and remediation.
Introducing the Infinity Graph from Prisma Cloud
The Infinity Graph, introduced in Prisma Cloud’s Darwin release, offers a unified visualization of users' cloud assets and security issues. It's designed not only to present data but to present data in a way that's flexible and intuitive. Users can customize views, search for assets based on specific attributes, blend in security issues, and delve into use cases, such as exploring IAM permissions or investigating network flow logs.
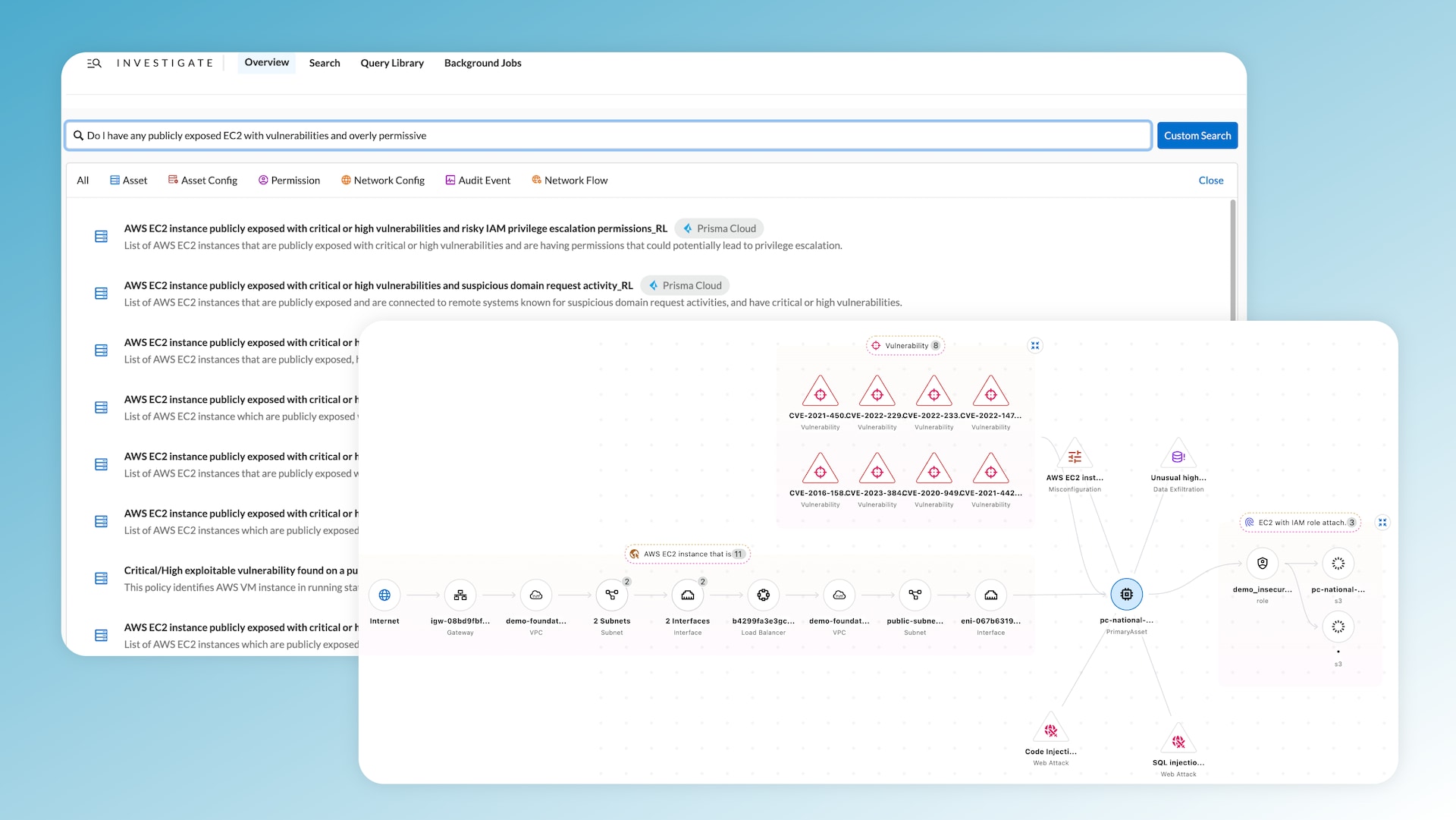
At its core, the Infinity Graph represents assets, security issues, and connections. Users can navigate through the graph with ease, expanding groups of assets or security issues to reveal details and drill into specific security findings for greater context. With aspects like internet exposure, for instance, users can trace the full exposure path from the internet to the VPC, subnet and corresponding EC2.
Efficient Correlation of Data
Data is only as valuable as the insights they provide. In cloud security, this often means correlating vast amounts of data across different tools to identify potential threats. The Infinity Graph now does this for you, alleviating the time-consuming and error-prone process. All data is interconnected and visualized in one place in the Infinity Graph, allowing for immediate prioritization and action.
With attack path analysis, for instance, users can surface assets based on a combination of multiple attack vectors or security signals. This comprehensive context ensures that users always focus on the most pressing issues, ensuring a more secure cloud environment.
Key Infinity Graph Features
- Preview Cards: Preview cards offer a quick glance at assets and security issues, providing essential metadata and severity details.
To access the full details of a specific asset or security issue, users can click into the sidecar to explore different dimensions of additional metadata.
- Path Highlights: This feature emphasizes a specific path, showing users how a security issue is related from its source to its potential impact.
When navigating through a large graph with numerous assets and connections, path highlighting becomes a crucial feature to use. By highlighting a specific path, it helps maintain focus and shows users how a particular security issue relates from its source to the destination blast radius impact.
- Alert Sidecar: Alert sidecars provide representations of alert context, ensuring users are always informed.
Attack Path Analysis
In a landscape where threats can emerge from multiple vectors, attack path analysis delivering an understanding of potential pathways of attack is key to getting out ahead of threats.
With Prisma Cloud’s Infinity Graph and unified environment, users can search for assets and attach attack path vectors to them. In a single query, you can identify an internet-exposed EC2 instance, having overly permissive access, and possessing critical vulnerabilities.
The Infinity Graph allows users to pivot their queries, adding layers of security context. If a common issue emerges, users can set it as a policy, ensuring they receive alerts and can conduct regular scans. This approach ensures that security teams can identify and mitigate threats before they escalate.
Real security problems involve multiple dimensions or multiple areas.
Trace Security Issues
The intricate web of cloud infrastructure makes tracing security issues from their origins to their potential impacts an arduous task. The Infinity Graph, however, simplifies this complexity with its capacity to trace issues from code to cloud.
Consider vulnerability tracing as an example. With the Infinity Graph, a vulnerability can be tracked from its inception in code packages, through its journey in deployed images and onto runtime assets like serverless functions or virtual machines. This end-to-end visibility ensures that security professionals can pinpoint the source of vulnerabilities and initiate remediation processes directly from the platform.
Network Traffic Flow Logs Investigation
Network traffic is the lifeblood of any digital infrastructure. It's also a potential source of vulnerabilities. In the Infinity Graph, Prisma Cloud introduces the Swimlane view — a tool designed for investigating network flow logs.
The Swimlane view offers a hierarchical representation of network traffic. Users can see, at a glance, the relationships between specific workloads, subnets, and VPCs. This rich context proves invaluable when identifying potential threats. For instance, users can quickly discern between internal workloads and external IPs, even identifying potentially suspicious IPs communicating with their environment. By offering both a granular and holistic view of network traffic, the Swimlane view equips users to respond to threats with precision and speed.
The Power of a Unified Platform
The Infinity Graph opens up a new world for security teams. Standing out for its unified approach, it optimizes data intel as it brings everything together under one roof. The Infinity Graph emphasizes infinite possibilities, catering to a variety of use cases and ensuring that security professionals can tackle the most pressing issues with clarity and efficiency. More than just a tool, it's a platform — a unified, infinite platform.
Video: Prisma Cloud’s Darwin release makes it easier than ever to secure your cloud infrastructure.
Learn More
Tune in to our on-demand virtual event, CNAPP Supercharged: A Radically New Approach to Cloud Security, and learn about Prisma Cloud's latest innovations. In the webinar, we show you how to streamline app lifecycle protection, so be sure to watch on demand today. And don’t miss an opportunity to test drive best-in-class security with a free 30-day Prisma Cloud trial.