High Security Vulnerability in OpenSSL: CVE-2022-3602 and CVE-2022-3786
On Tue Oct 25, the OpenSSL project team released an advisory announcing the forthcoming release of OpenSSL version 3.0.7. The advisory was issued to call attention to a critical vulnerability in OpenSSL versions between 3.0.0 and 3.0.6. The OpenSSL 3.0.7 release will be available on Tuesday, November 1, 2022. The Prisma Cloud security research team is actively monitoring the vulnerability and security fix release.
Update: 11/01/2022
On November 1, 2022 the OpenSSL project team released the patch notes for OpenSSL 3.0.7 as anticipated. The full security advisory for what are now known as CVE-2022-3602 and CVE-2022-3786 was also released.
According to the advisory, the vulnerabilities lie in the parsing mechanism of the email address during the name constraint checking. An attacker would need to craft a special malicious email address to trigger the vulnerability. For an attacker to leverage this vulnerability, though, they would need either an installed CA (certificate authority) to have signed their malicious certificate containing their specially crafted email address or for an OpenSSL instance to continue certificate verification despite failure to construct a path to a trusted issuer. These two conditions make exploitation of the vulnerabilities unlikely.
The vulnerabilities, which were initially rated Critical severity, have been downgraded to High severity. Their impact could range from denial of service of the affected instance or, depending on some prerequisites, remote code execution (RCE).
User Action Required
The Prisma Cloud Intelligence Stream is updated regularly to include known information regarding vulnerabilities. At this time, users should upgrade all OpenSSL instances between 3.0.0 and 3.0.6 to version 3.0.7.
This blog post will continue to be updated to describe relevant protections for Prisma Cloud users.
OpenSSL Overview
OpenSSL, first released in 1998, is an open-source cryptography library with a wide variety of applications around the SSL and TLS protocols. OpenSSL allows users to perform various SSL-related tasks, such as private keys generation, CSR (Certificate Signing Request), SSL certificate installation, and more.
Most Linux distributions come with OpenSSL pre-compiled, which makes a vulnerability in this component so dangerous, particularly considering the thousands of companies around the world that use OpenSSL daily. Many readers will remember a vulnerability dubbed Heartbleed that shook the world with its pervasive impact. Although some entertained concerns that this new vulnerability would have a similar widespread impact, that fortunately will not be the case.
Who Is Potentially Affected?
Any OpenSSL versions between 3.0.0 and 3.0.6, as well as any application that uses an impacted OpenSSL library, is vulnerable. OpenSSL v3 only comes standard with the newest Linux distributions, such as Ubuntu 22.04 or RHEL 9, so most Linux machines aren’t running the latest version of OpenSSL and won’t be affected.
Prepare for the Update Using Prisma Cloud
Prisma Cloud users can prepare by inventorying the workloads with OpenSSL packages.
Use Vulnerability Explorer to search for workloads with the vulnerability.
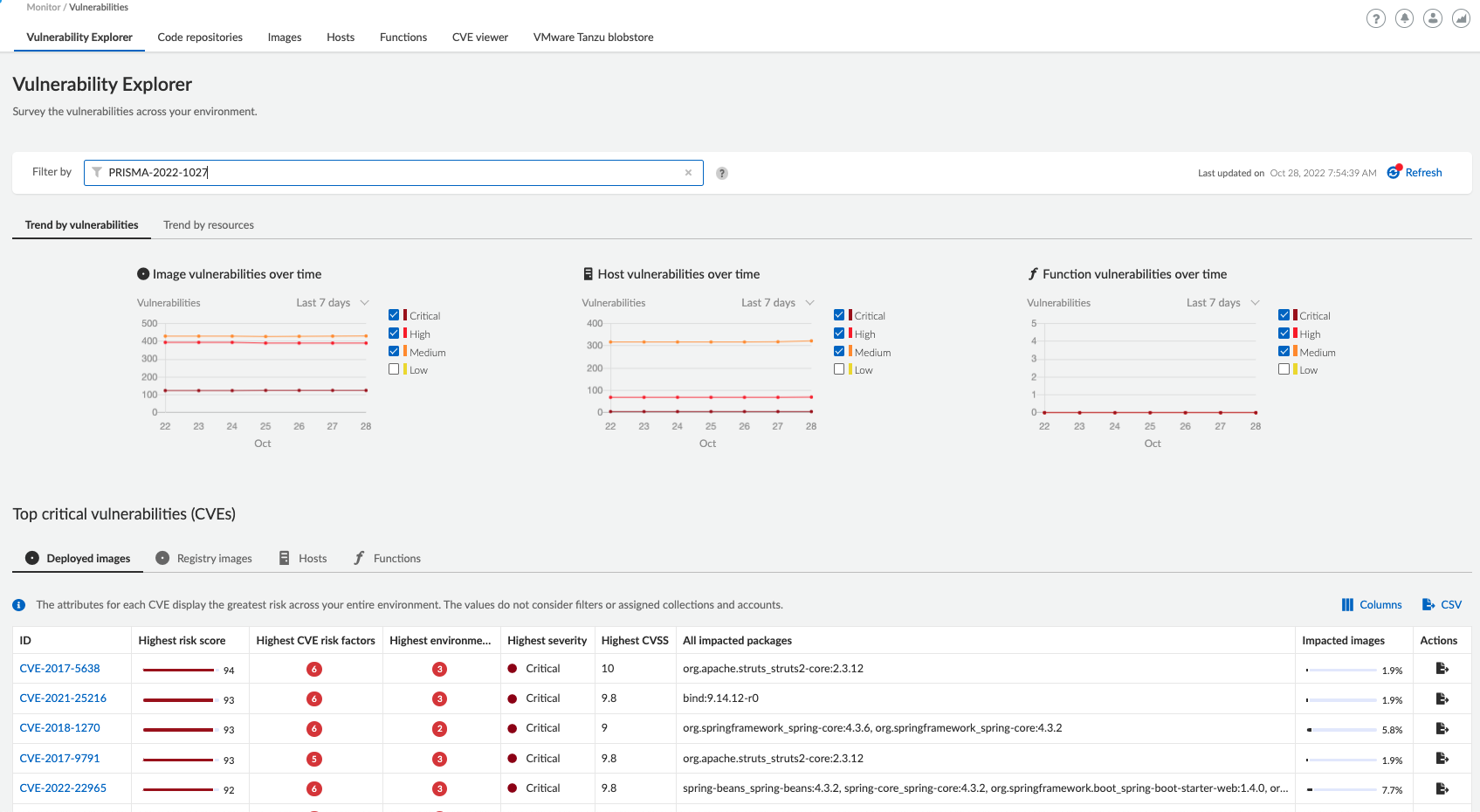
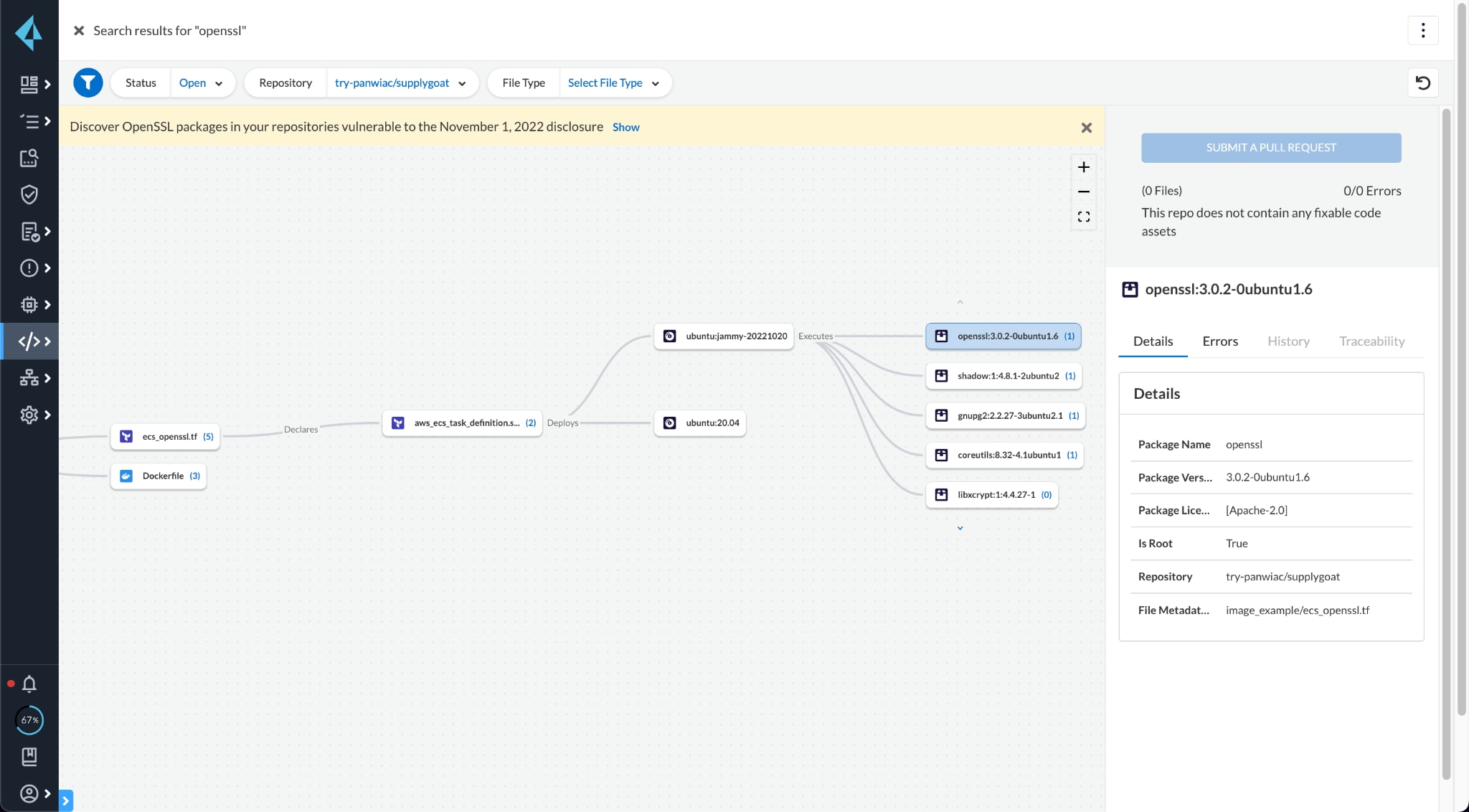
Determine if your images, containers, and hosts have OpenSSL packages by querying the Package Information. Prisma Cloud provides an asset's complete software bill of materials (SBOM).
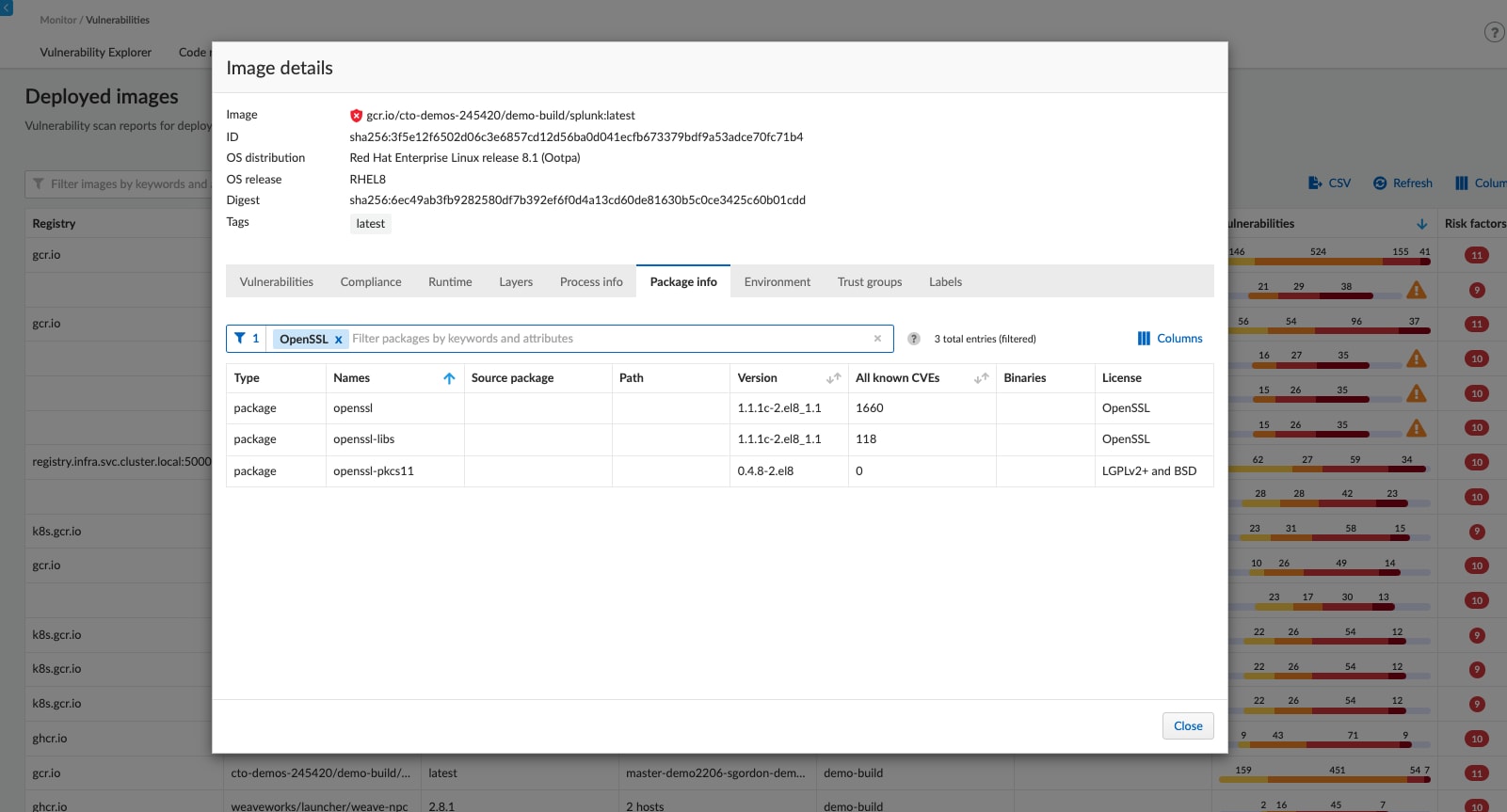
As soon as the vulnerability is disclosed, you can detect, block, and remediate vulnerabilities in the IaC templates, CI/CD pipelines, container registries, and your runtime deployed hosts and containers.
A banner on the top of the Projects and Supply Chain pages will help you filter down to relevant results.
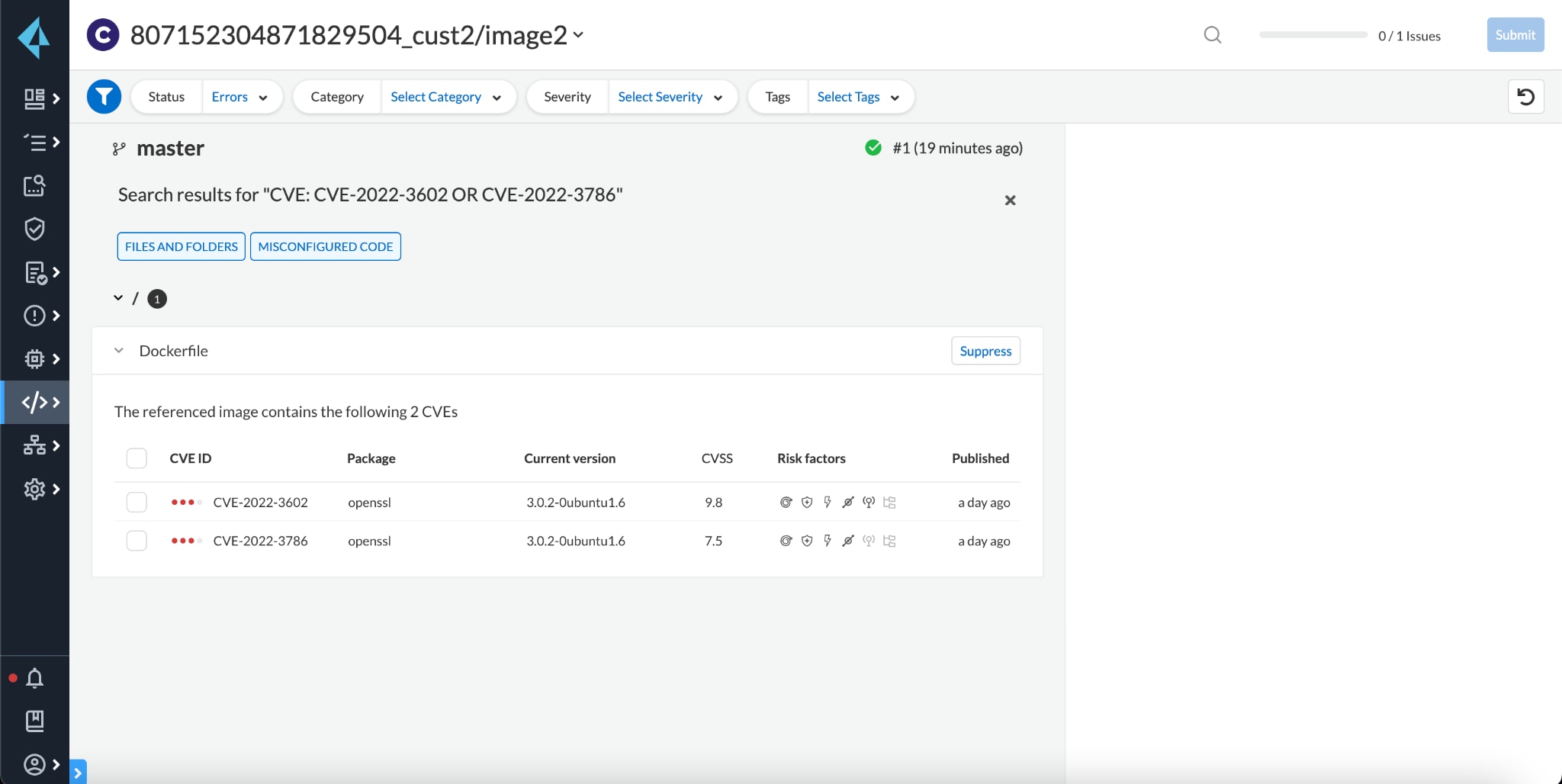
Prisma Cloud, even before deployment, will help identify vulnerabilities in images referenced in infrastructure as code (IaC) and provide early warning to developers about vulnerabilities and a chance to fix the issue in code. In this case, if an IaC template – such as Terraform, Dockerfiles, Kubernetes, or CI/CD pipelines – leverages an image with the OpenSSL vulnerability, developers will be flagged in development environments and blocked in pipelines to prevent merging vulnerable code.
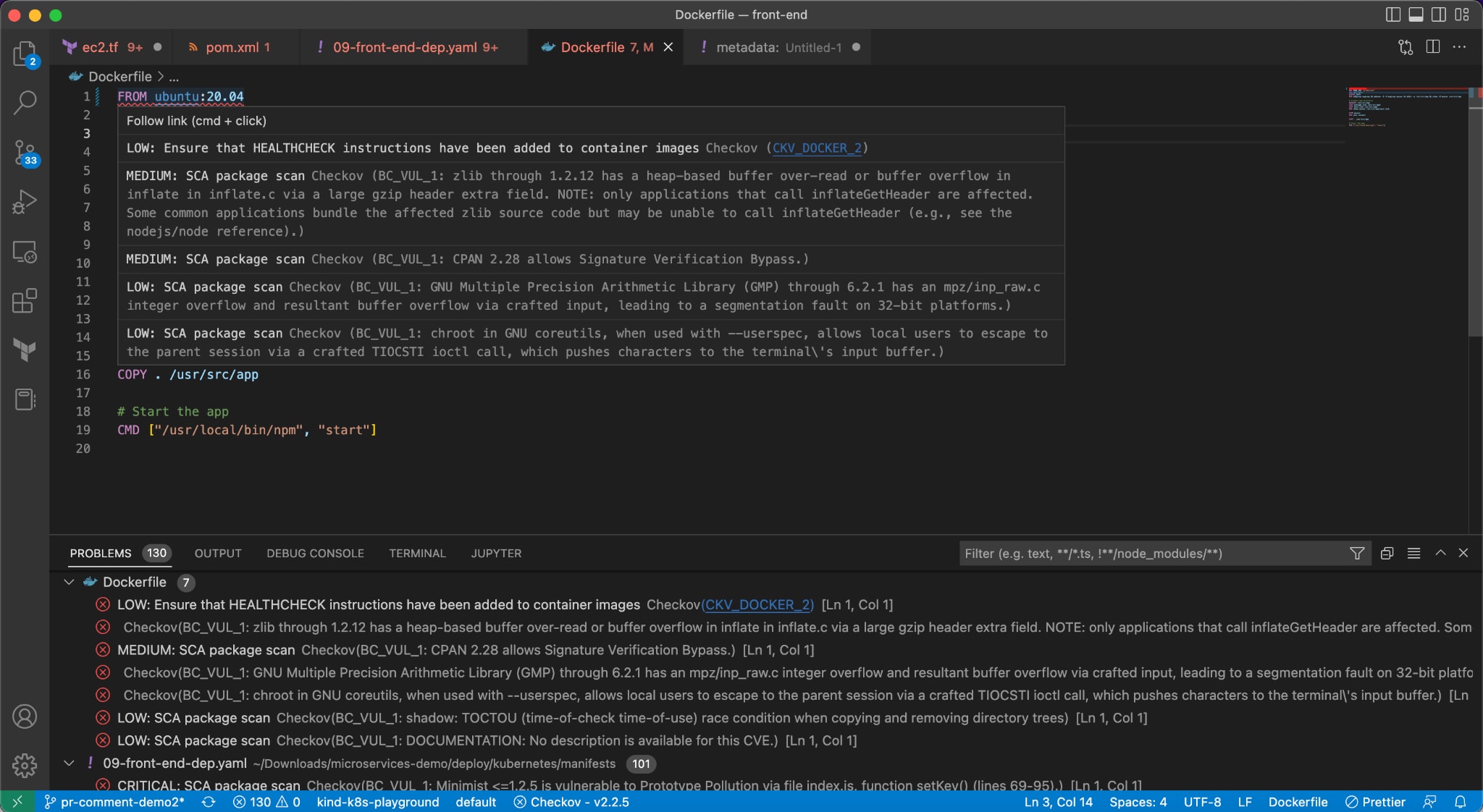
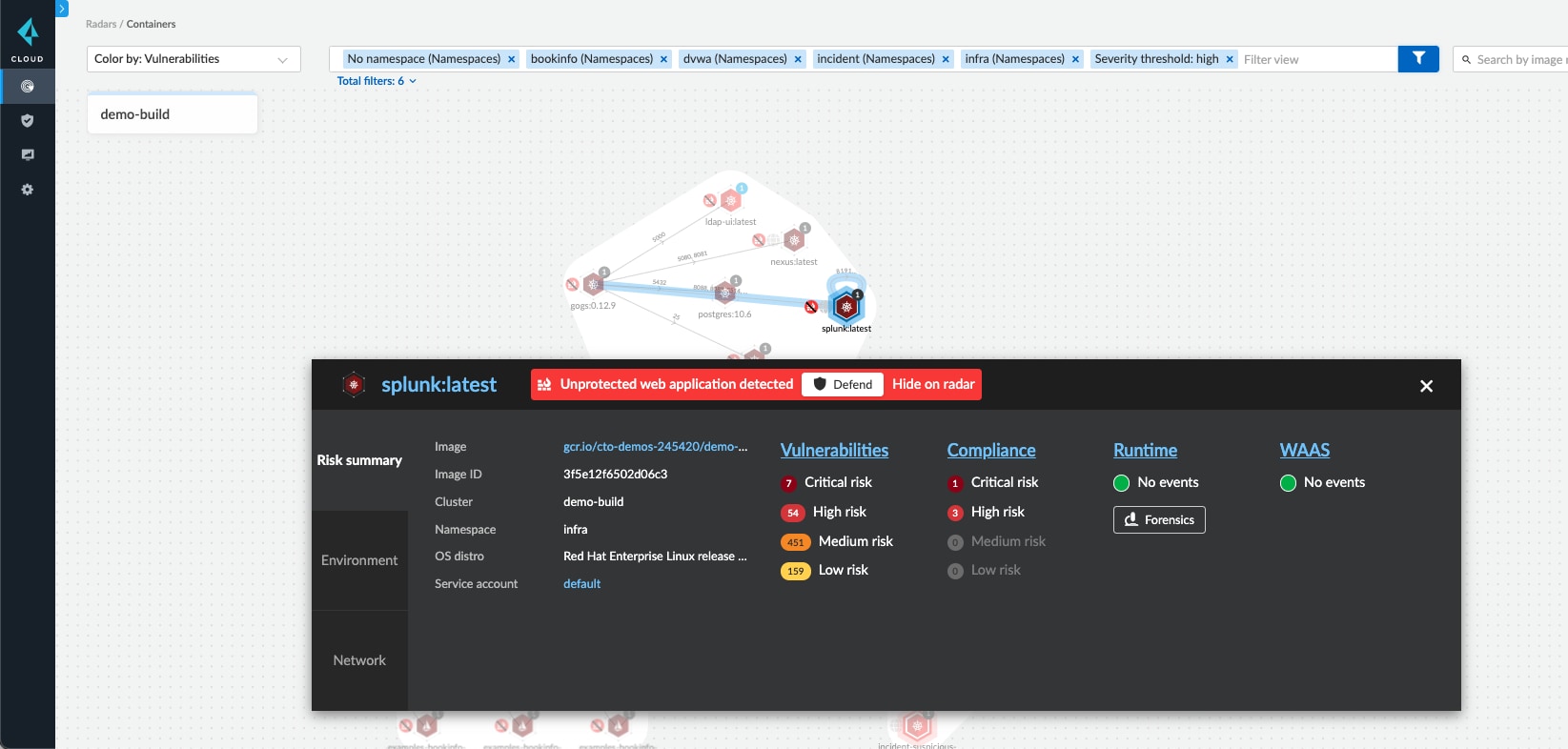
Compute Radar provides a graphical view of the workload deployments where users can review the environments affected by vulnerability severity. For workloads with applications and APIs receiving external traffic, defend by applying a web application firewall and a virtual patch with a single click.
Summary
OpenSSL is a core component of many workloads and the backbone of applications leveraging networks. Although some details pertaining to the latest vulnerabilities are forthcoming, security teams should patch vulnerable systems to version 3.0.7.
Prisma Cloud customers can apply controls to address this vulnerability across multiple stages in the application lifecycle, from the code to the cloud.
We will update this post as details are released. We recommend you check back in the coming days to remain aware of key information.