This post is also available in: 日本語 (Japanese)
Executive Summary
March 16 Update: A detailed timeline of protections released across our Cortex XDR products has been added to this blog post.
On March 2, 2021, Volexity reported the in-the-wild exploitation of four Microsoft Exchange Server vulnerabilities: CVE-2021-26855, CVE-2021-26857, CVE-2021-26858 and CVE-2021-27065. As a result of these vulnerabilities being exploited, adversaries can access Microsoft Exchange servers and allow the installation of additional tools to facilitate long-term access into victims' environments. There has also been a report of multiple threat actors leveraging these zero-day vulnerabilities, meaning post-exploitation activity may vary depending on the purpose of the different threat actors.
These vulnerabilities affect the following Microsoft Exchange Server versions:
- Microsoft Exchange 2013.
- Microsoft Exchange 2016.
- Microsoft Exchange 2019.
Microsoft has released an emergency out-of-band security update to patch these vulnerabilities. We strongly advise immediately updating all Microsoft Exchange servers to the latest available patched versions released by Microsoft.
This blog will help you proactively search for related indicators of compromise (IOCs) using Cortex XDR.
Hunting for this Attack in Your Environment
Review existing alerts for signs of compromise
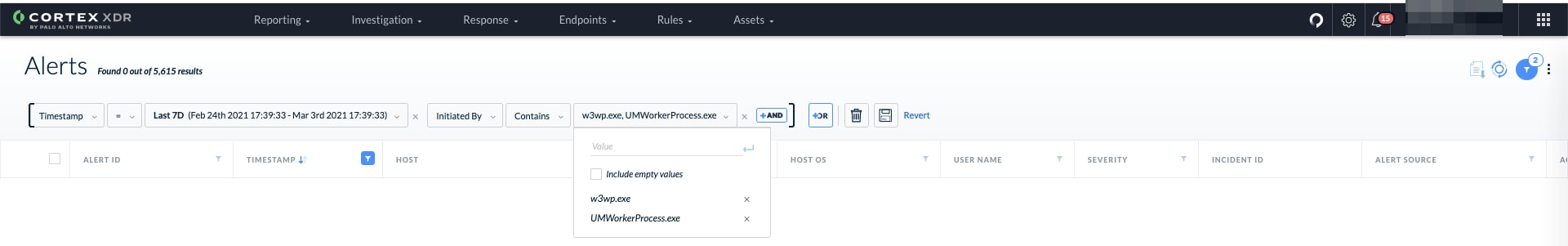
Leveraging the existing alerts in Cortex XDR, we suggest hunting for alerts from the IIS process, w3wp.exe, and the exchange worker process, UMWorkerProcess.exe.
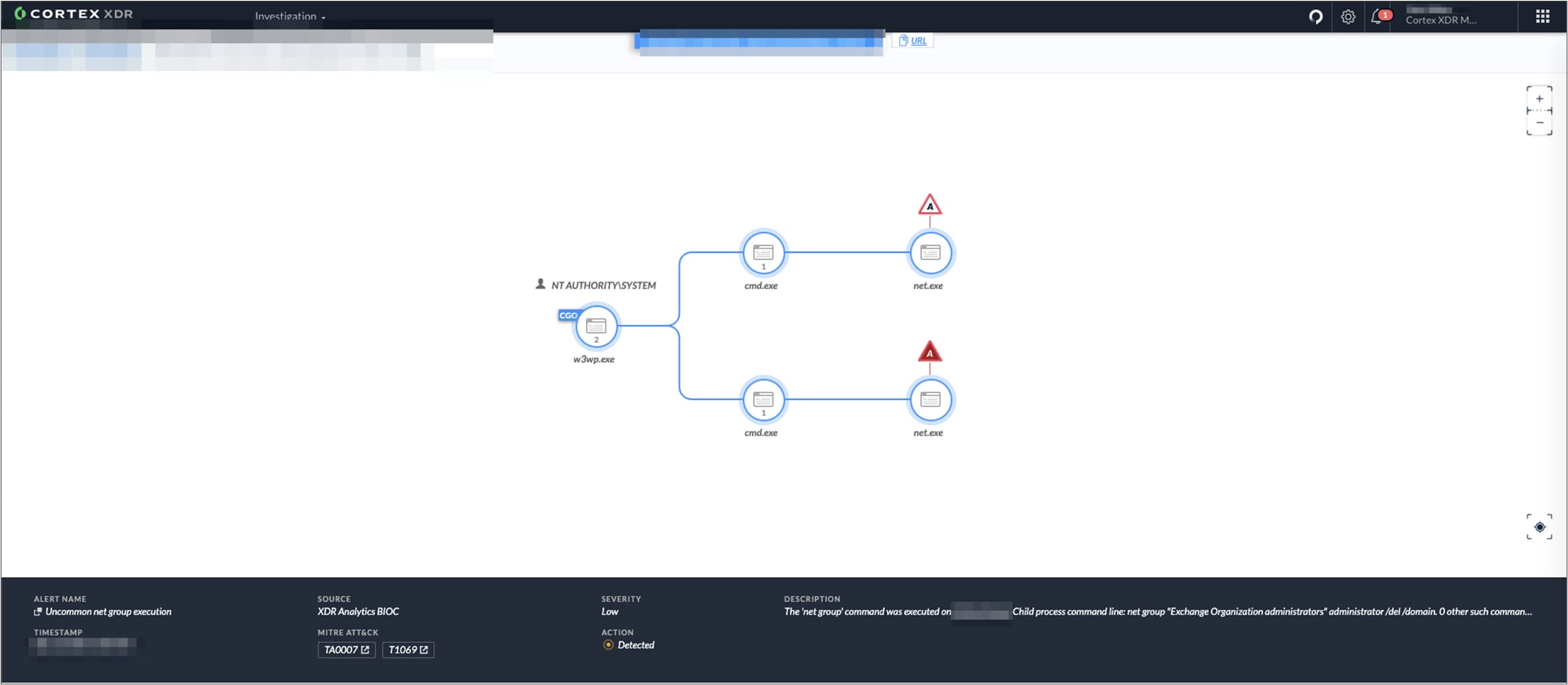
From there, we can pivot to a causality screen to drill deeper:
Hunt for the attack using XQL Search in Cortex XDR:
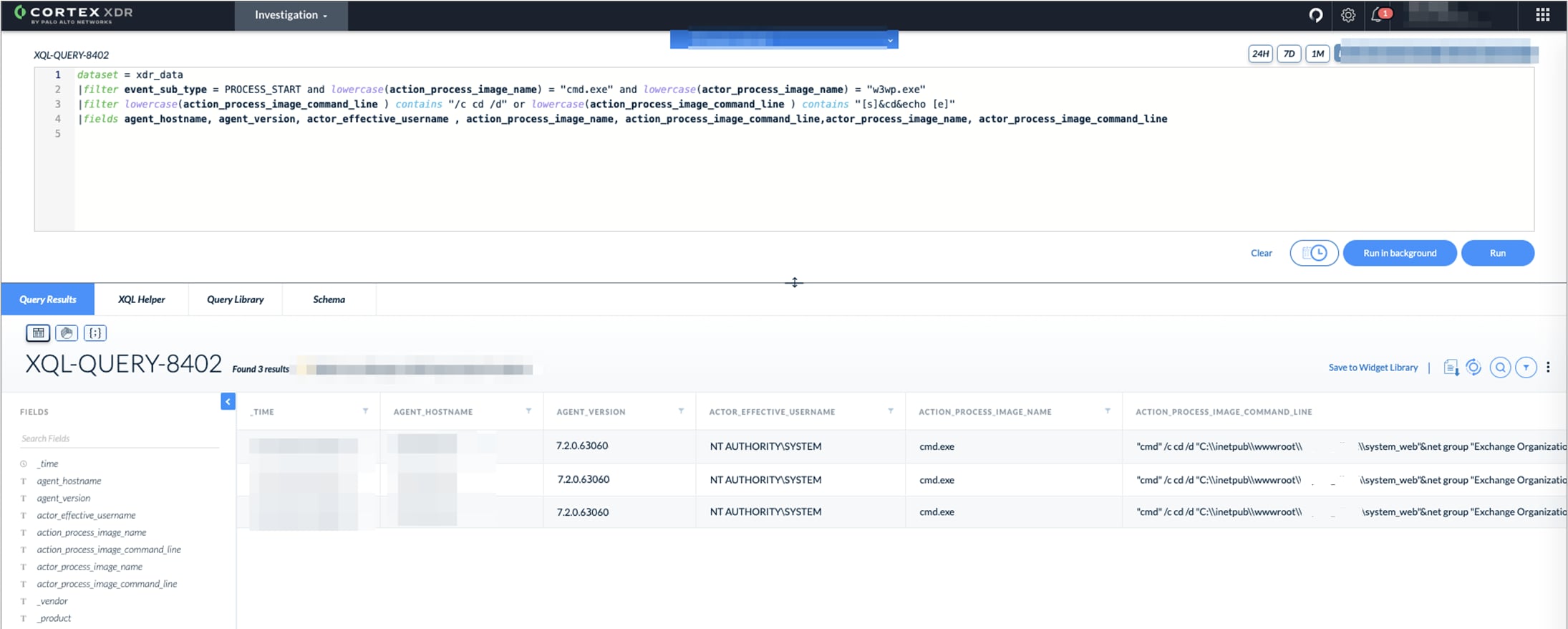
The China Chopper webshell has very distinct command line patterns that use [s]&cd&echo [e].You can look for these patterns with the following query:
|
1 2 3 4 5 6 7 |
dataset = xdr_data |filter event_sub_type = PROCESS_START and lowercase(action_process_image_name) = "cmd.exe" and lowercase(actor_process_image_name) = "w3wp.exe" |filter lowercase(action_process_image_command_line ) contains "[s]&cd&echo [e]" |fields agent_hostname, agent_version, actor_effective_username , action_process_image_name, action_process_image_command_line,actor_process_image_name, actor_process_image_command_line |
Microsoft Internet Information Server (IIS) dropping ASPX files into Exchange and generic IIS loading locations is a good indication of a webshell drop:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 |
config case_sensitive = false | dataset = xdr_data | filter event_type = FILE and event_sub_type in (FILE_WRITE, FILE_CREATE_NEW) and action_file_extension = "aspx" and action_file_path ~= "(\\inetpub\\wwwroot\\aspnet_client\\|\\frontend\\httpproxy\\owa\\auth\\|\\frontend\\httpproxy\\ecp\\auth\\)" and action_file_path != "*\\frontend\\httpproxy\\ecp\\auth\\timeoutlogoff.aspx" and actor_process_image_name in ("UMWorkerProcess.exe", "w3wp.exe", "umservice.exe") |
Running discovery commands from IIS processes is a good indication of an attacker trying to get the lay of the land. Hunt for such activities using this query:
|
1 2 3 4 5 |
dataset = xdr_data |filter lowercase(causality_actor_process_image_name) = "w3wp.exe" and lowercase(actor_process_image_name) in ("cmd.exe", "powershell.exe") and lowercase(action_process_image_name) in ("net.exe", "quser.exe","certutil.exe", "arp.exe","hostname.exe", "whoami.exe", "netstat.exe", "ping.exe", "ipconfig.exe", "wmic.exe", "del.exe") |fields agent_hostname, agent_version, actor_effective_username , causality_actor_process_image_name, causality_actor_process_command_line , actor_process_image_name, actor_process_command_line, action_process_image_name, action_process_image_command_line |
The attackers use compression and memory dumps to stage exfiltration and credential access using C:\programdata as the staging location. Hunt for servers doing this activity using this query:
|
1 2 3 4 5 6 7 |
config case_sensitive = false | dataset = xdr_data |filter event_type = FILE and event_sub_type in (FILE_CREATE_NEW, FILE_WRITE) and agent_os_sub_type contains "server" |filter action_file_path ~= "c:\\programdata\\[a-zA-Z0-9]+\.(rar|zip|zipx|7z)" OR action_file_path ~= "(c:\\root\\[a-zA-Z0-9]+\.dmp$|c:\\windows\\temp\\[a-zA-Z0-9]+\.dmp$)" |
The Exchange worker process does not usually create subprocesses and one of the exploit targets this process. This XQL query in Cortex XDR will help hunt for such cases:
|
1 2 3 4 5 6 7 |
config case_sensitive = false | dataset = xdr_data | filter event_type = PROCESS and event_sub_type = PROCESS_START and os_actor_process_image_name = "UMWorkerProcess.exe" | filter action_process_image_name != "WerFault.exe" and action_process_image_name != "wermgr.exe" |
Hunt and respond with Cortex XSOAR
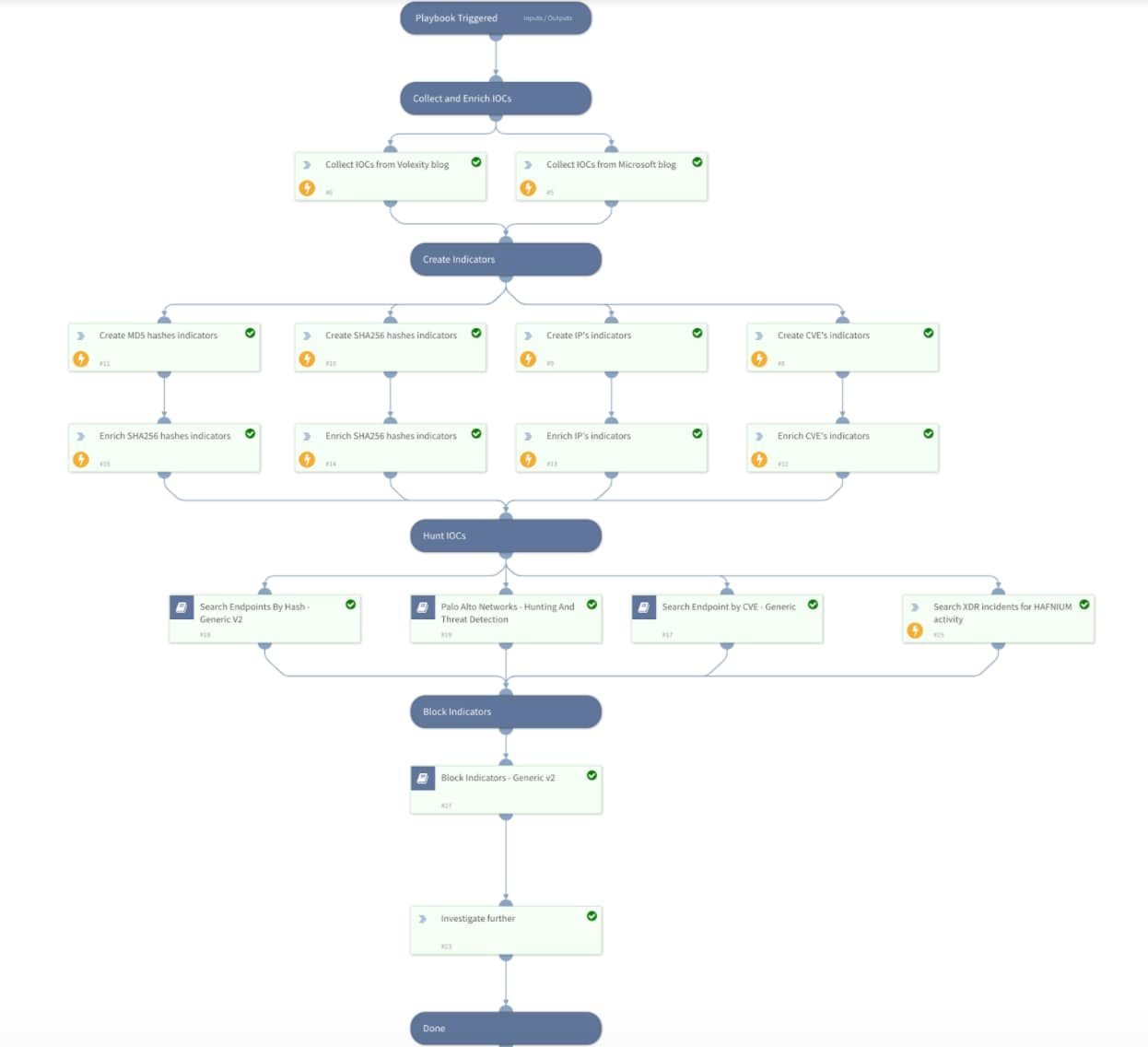
Cortex XSOAR has released a playbook called “HAFNIUM - Exchange 0-day exploits”. You can find it in the Rapid Breach Response content pack on our Cortex XSOAR Marketplace. The fully automated playbook will execute the following:
- Collect indicators to be used in your threat hunting processes
- Query firewall logs to detect malicious network activity
- Search endpoint logs for malicious activity to detect compromised hosts; if Cortex XDR is enabled, the playbook will also search for alerts detailed above
- Block indicators in various third-party tools
![]()
Cortex XDR alerts that detect this attack
| Source | Description |
| Cortex XDR Analytics BIOC | Uncommon net group execution |
| Cortex XDR Analytics | Multiple Discovery Commands |
| Cortex XDR BIOC | Exchange process writing aspx files |
| Cortex XDR Agent | Behavioral Threat Detected |
| Cortex XDR Agent | Suspicious Process Creation |
| Cortex XDR Analytics BIOC | Uncommon remote service start via sc.exe |
| Cortex XDR Analytics BIOC | Rare SSH Session |
| Cortex XDR Analytics BIOC | Uncommon ARP cache listing via arp.exe |
| Cortex XDR Analytics BIOC | Uncommon user management via net.exe |
| Cortex XDR Analytics BIOC | WmiPrvSe.exe Rare Child Command Line |
| Cortex XDR Analytics BIOC | Script Connecting to Rare External Host |
| Cortex XDR BIOC | Remote process execution using WMI |
| Cortex XDR BIOC | 64-bit PowerShell spawning a 32-bit PowerShell |
| Cortex XDR BIOC | Suspicious PowerShell Command Line |
| Cortex XDR BIOC | Dumping Registry hives with passwords |
Observed Activities
We have seen attackers create webshell files on these paths:
| C:\Program Files\Microsoft\Exchange Server\V15\FrontEnd\HttpProxy\owa\auth\RedirSuiteServerProxy.aspx
C:\inetpub\wwwroot\aspnet_client\system_web\r1BMaJKT.aspx C:\inetpub\wwwroot\aspnet_client\system_web\[RANDOM].aspx C:\inetpub\wwwroot\aspnet_client\supp0rt.aspx C:\inetpub\wwwroot\aspnet_client\discover.aspx |
We have seen attackers execute the following commands:
| "cmd" /c cd /d "C:\\inetpub\\wwwroot\\aspnet_client\\system_web"&net group "Exchange Organization administrators" administrator /del /domain&echo [S]&cd&echo [E]
wmic /node:$NODE$ /user:$USER$ /password:$PASSWORD$ process call create "powershell -exec bypass -file c:\programdata\payloadDns.ps1" "cmd.exe" /c powershell -exec bypass -file c:\programdata\bot.ps1 net group "Exchange Servers" /DOMAIN cmd /c start c:\windows\temp\xx.bat net group "Exchange Organization Administrators" /domain dsquery server -limit 0 net group [REDUCATED] /domain "cmd" /c cd /d "C:\\inetpub\\wwwroot\\aspnet_client\\system_web"&arp -a&echo [S]&cd&echo [E] net use \\[REDUCATED] [PASSWORD] /user:[USER] powershell.exe -PSconsoleFile "C:\Program Files\Microsoft\Exchange Server\V15\Bin\exshell.psc1" -Command ".'C:\windows\help\help\1.ps1'" nltest /domain_trusts "cmd" /c cd /d "C:\\inetpub\\wwwroot\\aspnet_client\\system_web"&wmic process call create "reg save hklm\sam c:\programdata\$FILE_NAME$.log &echo [S]&cd&echo [E] |
Detailed Protection Timeline
| Date | Product | Protection Description |
| Prior to disclosure | Cortex XDR PRO | Cortex XDR Analytics:
Cortex XDR Analytics BIOC:
Cortex XDR BIOC:
|
| Prior to disclosure | Cortex XDR Prevent | Cortex XDR Agent – Behavioral Threat Detected* |
| March 2 | NGFW | Threat Prevention Content Release 8380 containing vulnerability signatures for the four vulnerabilities.
Severity ID CVE-ID critical 90796 CVE-2021-26855 critical 90797 CVE-2021-26858 critical 90798 CVE-2021-27065 critical 90800 CVE-2021-26857 |
| March 3 | Cortex XDR PRO | Content released as part of pack 2021.03.03.1
Cortex XDR BIOC -Exchange process writing aspx files |
| March 4 | Cortex XDR Prevent | Cortex XDR Agent content pack 170
Cortex XDR Agent - Suspicious process creation** |
| March 9 | NGFW | Threat Prevention Content Release 8383 containing additional vulnerability signatures for the “ProxyLogon” vulnerability
Severity ID CVE-ID critical 90815 CVE-2021-26855 |
| March 10 | Cortex XDR Prevent | Cortex XDR Agent content pack 171
Cortex XDR Agent - Behavioral Threat Prevention*** |
| March 15 | XDR Agent 7.3.1 | New Cortex XDR agent version which allows for visibility into CVE-2021-28655 exploitation attempts (agent content pack 171-54296) |
* On post-exploitation activities such as Mimikatz usage prevention.
** Preventing the execution of attacks from the China Chopper webshells.
*** Preventing writing of webshells by exploited IIS Servers.
Conclusion
Due to the alarming activity of threat actors exploiting these zero-day vulnerabilities against vulnerable Microsoft Exchange servers, we strongly advise immediately updating all Microsoft Exchange servers to the latest available patched versions released by Microsoft.
We also advise updating to the latest product and content version, and hunting for threats using the supplied XQL queries and the existing protection mechanisms within the product.
Read the Unit 42 Threat Assessment here.