Executive Summary
Adversaries are actively shifting their focus from traditional email to modern collaboration platforms like Microsoft Teams, transforming them into a primary vector for sophisticated attacks. By leveraging the inherent trust users place in internal communication applications, threat actors can bypass conventional security measures to gain initial access, establish persistence, steal sensitive data, and move laterally within an organization. Established groups like Midnight Blizzard and Black Basta are already weaponizing Microsoft Teams, proving that security operations must extend their visibility into the heart of the collaborative workspace.
To counter this evolving threat, organizations need a security approach that can dissect activity within the SaaS application itself. This blog demonstrates how the Palo Alto Networks Cortex XSIAM platform provides the crucial visibility and analytics required to detect and respond to attacks that originate and operate within Microsoft Teams. By correlating various indicators - from token theft via a phishing message to anomalous data gathering using the Graph API - Cortex XSIAM connects disparate events into a cohesive incident, allowing security teams to see the full attack narrative and eliminate the threat.
The Challenge
As organizations across the globe integrate Microsoft Teams and other instant messaging platforms into the core of their daily operations, sophisticated threat actors are taking notice. These tools are no longer seen merely as channels for communication - they're emerging as powerful attack vectors for initial access, reconnaissance, sensitive data collection, and lateral movement within enterprise environments. It's time for security teams to shift their focus from the traditional email inbox and address the growing threats landscape within the collaboration ecosystems.
Understanding the Risk: The Factor of User Trust
The core of the problem lies in a dangerous trust in instant messaging platforms. Users perceive Teams as a secure, internal "walled garden." A message from a colleague or even a federated partner in Teams doesn't trigger the same level of suspicion as an external email, there is no ingrained cultural habit of inspecting every link. This inherent trust is precisely what makes it such an effective phishing and social engineering platform. Employees are far more likely to click a link, open a file, or approve a request sent via Microsoft Teams, believing it has already been vetted by the corporate environment.
This isn't just speculation; real-world incidents have established the urgency of the topic. State-sponsored groups like Midnight Blizzard have been observed weaponizing Teams, luring users into approving multifactor authentication (MFA) prompts and hijacking accounts. Similarly, distributors of the DarkGate malware have abused the platform to send malicious attachments, successfully bypassing traditional email gateways by targeting users where their guards are lowered. These events prove that the collaborative hub is firmly in the crosshairs of adversaries, demanding our immediate and focused attention.
The Crown Jewels in Plain Sight
The threat extends far beyond phishing. The deep integration of Microsoft Teams into the business workflow has created a powerful and multifaceted attack surface.
Many organizations, in the name of seamless collaboration, have misconfigured overly permissive external access and federation settings. This can create an unlocked side door, allowing an attacker from a compromised external tenant - or one they control - to directly message employees. To the end-user, this message can appear as if it's coming from a trusted partner or contractor, providing the attacker with an instant foothold of credibility.
Beyond being an entry point, Microsoft Teams is a destination. Think about the conversations that happen in private chats and channels that you have access to. They can be a treasure trove of sensitive information: intellectual property, sensitive credentials for other systems, API keys, strategic plans, and confidential financial data. For an attacker, compromising a single Teams account isn't just about reading messages; it's about attempting to gain access to the organization's most valuable secrets, all conveniently indexed and searchable.
Anatomy of a Teams Attack: From Initial Access to Data Exfiltration
Initial Access - The Deceptive First Contact
The primary goal of initial access is to establish a foothold within the target's environment. In Microsoft Teams, this often begins with social engineering, leveraging the inherent trust users have in the platform.
Attackers frequently exploit the configured external access policy, which might be too permissive, to initiate contact. While external users are restricted from sending links or files directly, clever adversaries have developed bypasses:
For example a common technique involves starting a chat with more than one member and then proceeding to remove one of them to avoid restrictions for external users on link sharing.
Once the user clicks a malicious link sent, they are often directed to a phishing page designed to harvest credentials or session tokens. Public tools like EvilGinx are perfectly suited for this, acting as a reverse proxy to steal session cookies, bypassing MFA and granting the attacker direct access to the user's Teams session, and potentially other Microsoft 365 services.
Figure 1 shows an example of how such a phishing page created using EvilGinx might appear to a user after clicking on it, luring them to a credential harvesting site.
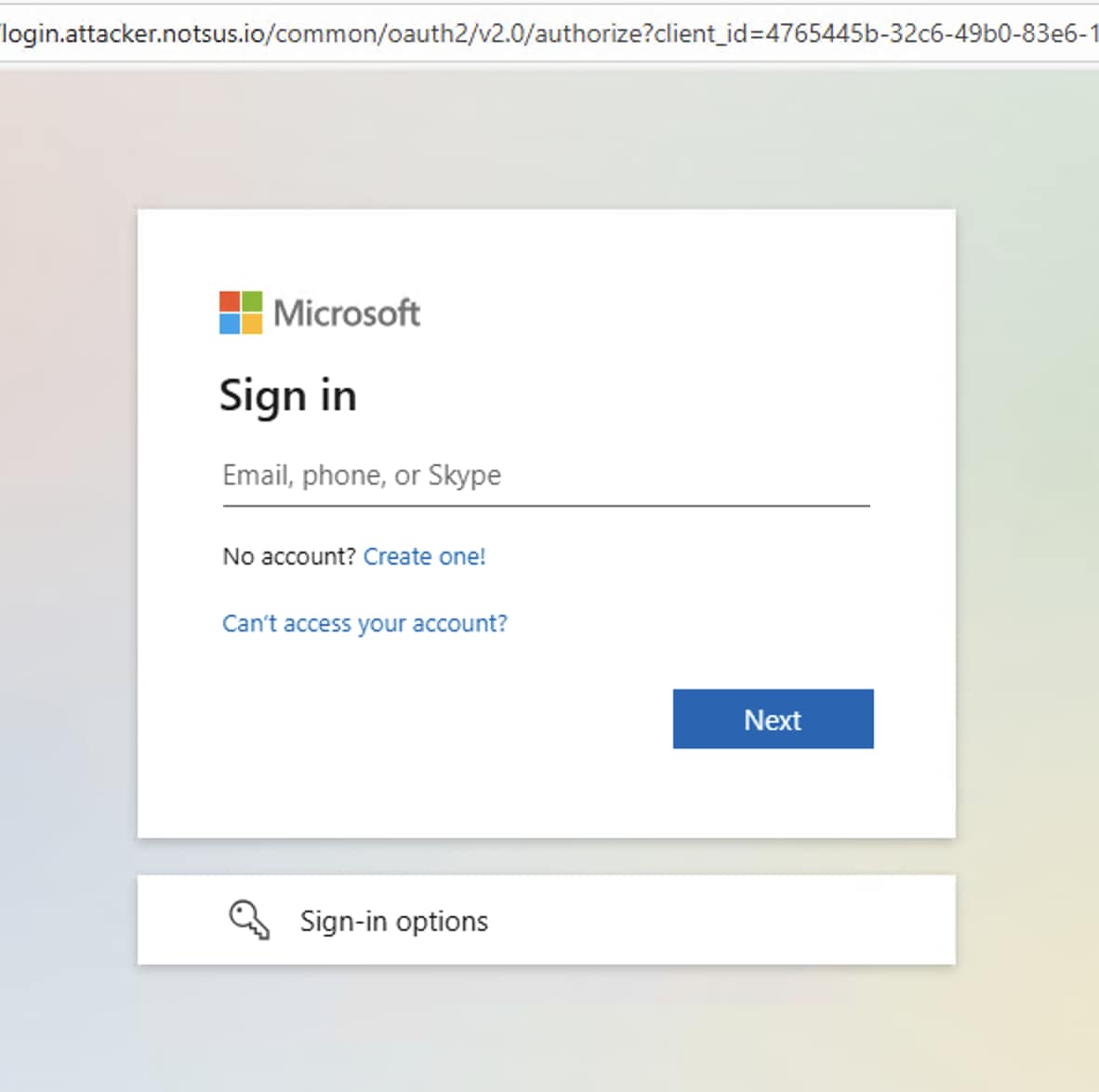
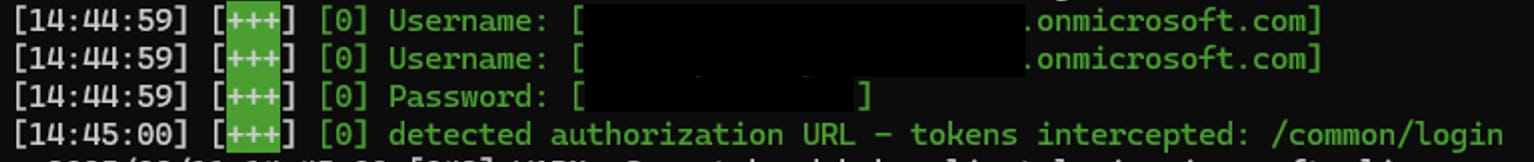
Figure 2 shows how intercepted credentials and tokens will look on EvilGinx’s server after a user clicked and logged in through the phishing link sent.
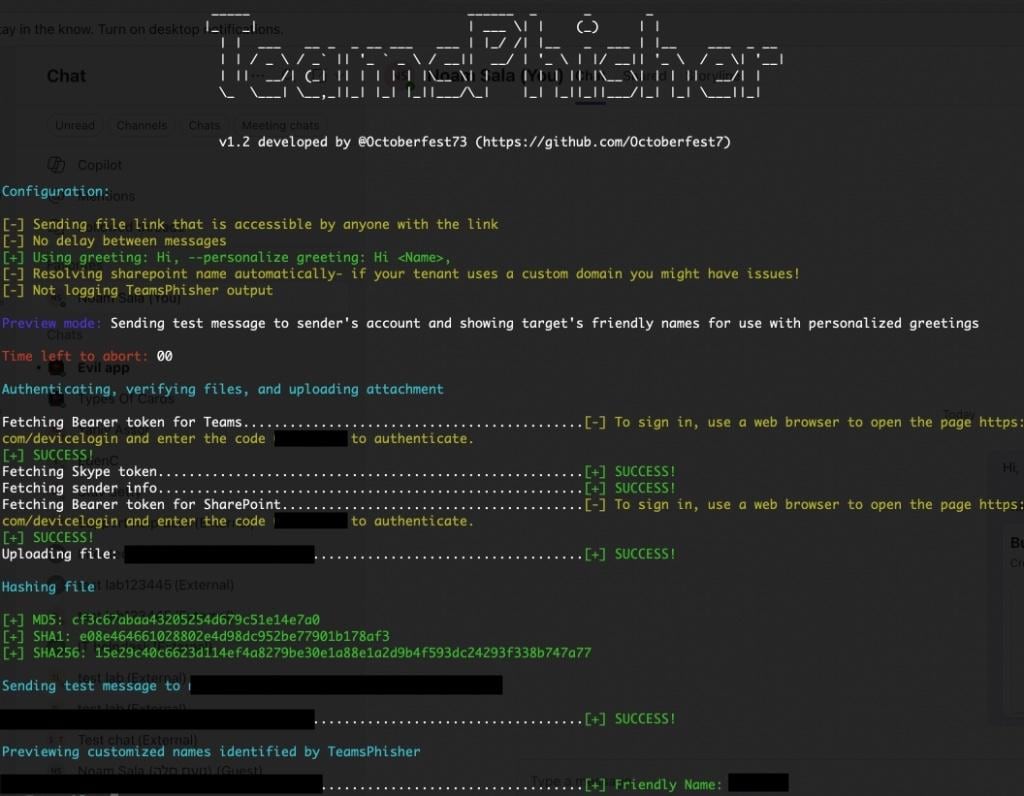
Another example of a publicly available tool that can be used to lure victims into downloading malicious payloads is TeamsPhisher.
Figure 3 shows how TeamsPhisher would be used by an attacker to send a phishing message to a user inside a target company.
Discovery and Internal Pivoting - Blending In
Once an attacker has gained initial access, their next step is typically to understand the environment, identify high-value targets, and expand their reach. This phase focuses on discovery and internal pivoting, often leveraging the compromised user's existing permissions.
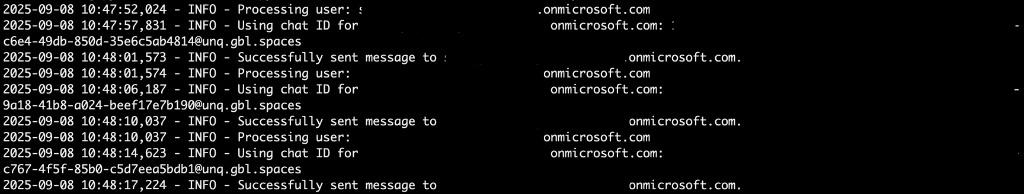
With a compromised internal account, an attacker can now perform highly credible spear phishing attacks from within the organization. Messages sent from a trusted internal identity - even if it's a low-privilege account - are far more effective. The attacker might impersonate IT support, a manager, or a colleague requesting urgent assistance, sharing a seemingly legitimate document, or asking for sensitive information. These internal phishing attempts can lead to further credential theft, malware execution, or tricking other users into granting additional permissions.
Figure 4 shows how an attacker can leverage Microsoft’s Graph API to automate the process of internal spear phishing attack through Teams by sending messages to multiple users via Graph API.
Persistence - Securing a Long-Term Foothold
A sophisticated attacker will also seek to maintain their presence within the tenant.
One method for achieving persistence in Microsoft Teams can be by creating and sideloading a malicious custom application or a bot. If the organization's policies allow users to upload custom applications, an attacker can use a compromised account's privileges to install an application that appears benign but contains malicious functionality.
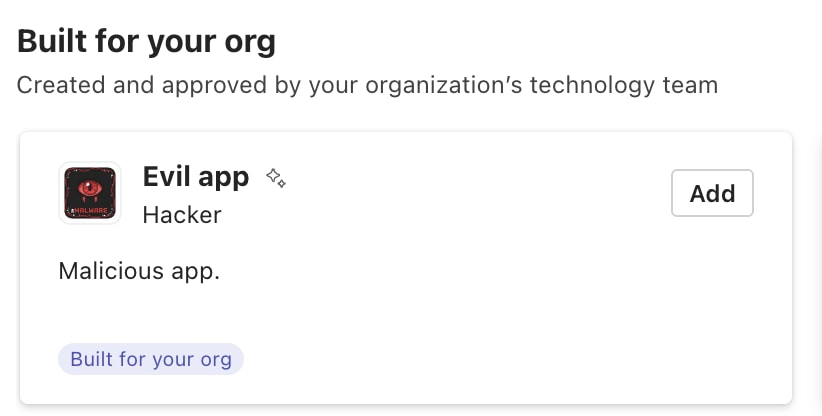
To further enhance the effectiveness of the method, the attacker, with the right permissions, can publish the application to the organization catalog, letting more users download the malicious application, which can be used as another pivoting method.
Figure 5 is an example of a malicious application that is published to the organization catalog in our lab environment, and it appears under the “built for your org” section.
Data Gathering and Exfiltration - The Heist
This is often the ultimate objective of the attack - stealing the sensitive information that resides within Microsoft Teams chats and channels.
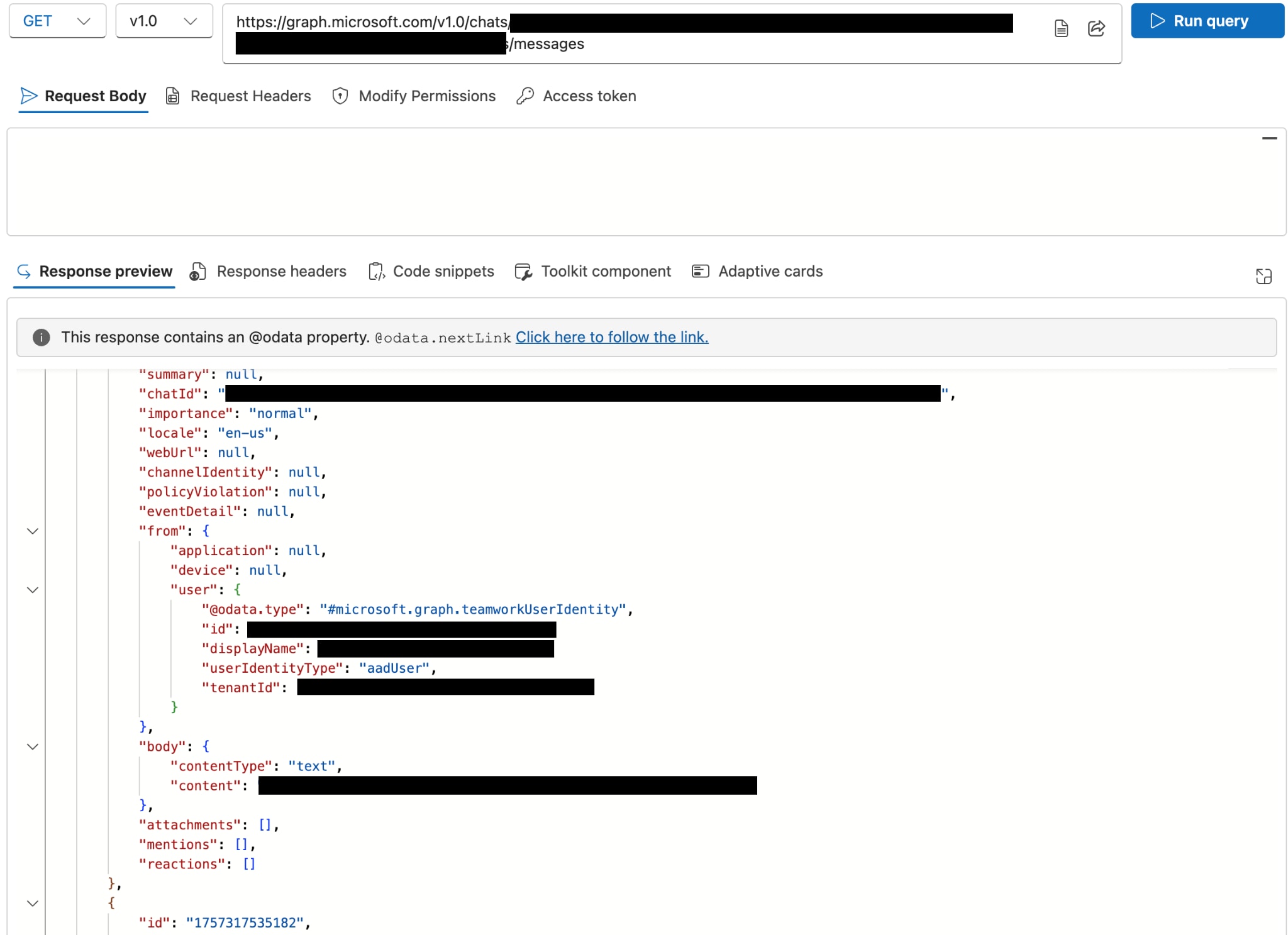
Microsoft Graph API can work with Microsoft Teams across a variety of APIs. . For an attacker, it can be a tool for mass data collection. Using the session tokens stolen during the initial access phase, or the permissions granted to their malicious application, an attacker can make programmatic API calls to access a vast amount of data, including reading the full history of a user's private one-on-one and group chats.
Figure 6 provides a conceptual view of how an attacker might use Graph API to pull chat data, effectively exfiltrating sensitive conversations.
Detection: How Cortex XSIAM Exposes Malicious Activity in Teams
Cortex XSIAM is capable of detecting attacks targeting Microsoft Teams, by analyzing behavior and correlating events directly from the application itself.
Cortex XSIAM provides rich detection capabilities that can identify the various stages of an attack conducted through Microsoft Teams. By ingesting and analyzing a rich data stream from Teams and other services, the platform applies behavioral analytics to distinguish legitimate user activity from the subtle indicators of a compromise. For example, after establishing a baseline of normal communication patterns, it can detect deviations indicative of an in-progress phishing attempt and raise a corresponding alert.
The platform's Identity Threat Detection and Response (ITDR) capabilities can provide the next layer of security by detecting any subsequent misuse of stolen credentials, such as an anomalous session logon to Microsoft Teams.
Figure 7 and 8 show some examples of alerts investigations that are related to Microsoft Teams.
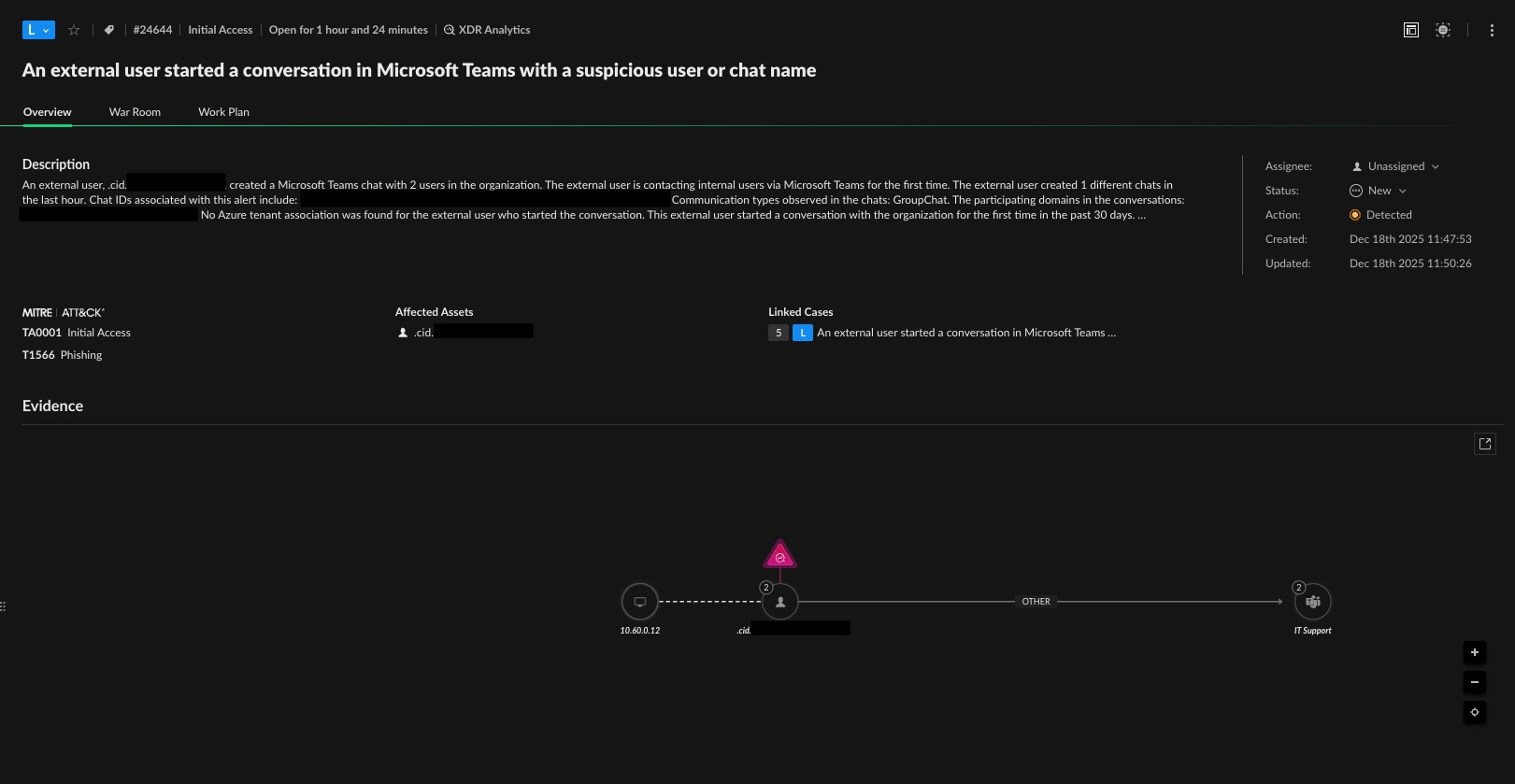
By linking the alerts and events that will trigger upon an attack via Microsoft Teams, security teams are provided with a holistic view of how the entire Microsoft Teams platform can be abused as an attack surface, connecting the dots from initial entry to the final objective.
Conclusion
Throughout this post, we deconstructed a realistic attack kill chain - from an initial phishing page that bypasses traditional defenses to internal pivoting, persistence, and finally, data collection using the platform's own APIs. This highlights a critical shift: security risks now extend into the core of trusted collaborative spaces.
Detecting these threats requires moving beyond perimeter controls and gaining deep visibility into application behavior. As we analyzed, the operational footprints of these attacks are subtle. They are found not in obviously malicious files, but in anomalous communication patterns, unusual API calls, and suspicious actions. By correlating these signals into a clear, coherent story, a platform like Cortex XSIAM can expose an attack that would otherwise remain hidden.
Additional Resources
- Real world cases
Canada government - Midnight Blizzard
Cleardata - Midnight Blizzard
TheHackerNews - BlackBasta - Tools
EvilGinx
TeamsPhisher
Graph API
XSIAM Alerts and MITRE Techniques
Table 1 lists the Cortex XSIAM alerts and the associated MITRE ATT&CK techniques these alerts detect.
| Alert Name | Alert Source | ATT&CK Technique |
|---|---|---|
| Microsoft Teams messages were exported from conversation | XDR Analytics, Identity Analytics | Data from Information Repositories: Messaging Applications: Messaging Applications |
| User exported multiple messages in Microsoft Teams via Graph API | XDR Analytics, Identity Analytics | Data from Information Repositories: Messaging Applications |
| External user started a Microsoft Teams conversation | XDR Analytics, Identity Analytics | Phishing |
| External user created a Microsoft Teams conversation with suspicious operations | XDR Analytics, Identity Analytics | Phishing |
| External user added a link to a Microsoft Teams chat | XDR Analytics, Identity Analytics | Phishing |
| User installed an application in Microsoft Teams via Graph API | XDR Analytics, Identity Analytics | Cloud Application Integration |
| A Microsoft Teams application was installed | XDR Analytics, Identity Analytics | Cloud Application Integration |
| User sent messages in Microsoft Teams to multiple users via Graph API | XDR Analytics, Identity Analytics | Internal Spearphishing |
| Microsoft Teams application setup policy was modified | XDR Analytics, Identity Analytics | Cloud Application Integration Impair Defenses |
| Microsoft Teams external communication policy was modified | XDR Analytics, Identity Analytics | Impair Defenses |
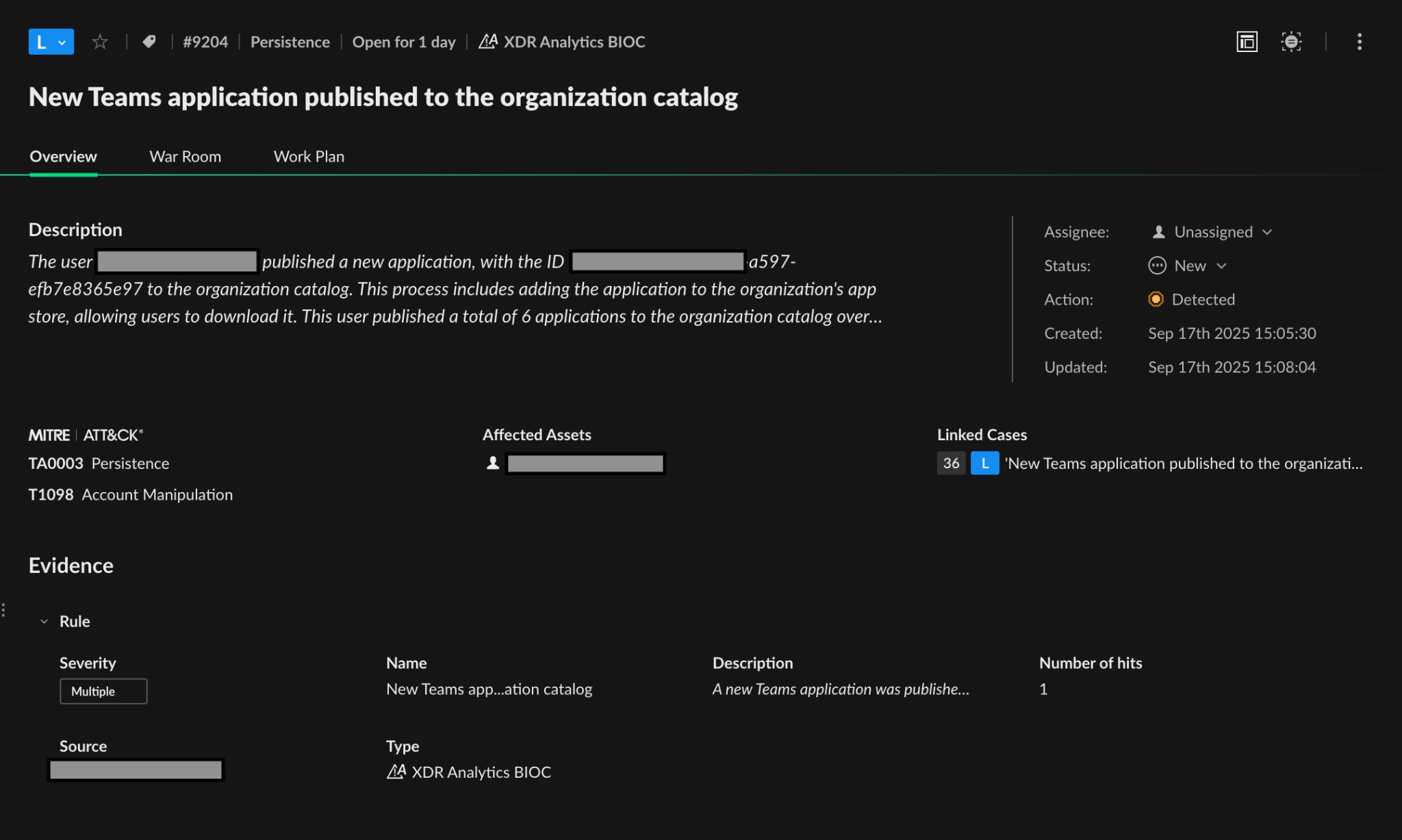
| New Teams application published to the organization catalog | XDR Analytics, Identity Analytics | Account Manipulation |
| A user uploaded malware to SharePoint or OneDrive | XDR Analytics, Identity Analytics | User Execution: Malicious File |
| A Microsoft Teams bot was added to a team | XDR Analytics, Identity Analytics | Cloud Application Integration |
| Microsoft Teams enumeration activity | XDR Analytics, Identity Analytics | Cloud Service Discovery |
Table 1. Relevant alerts and MITRE techniques.