How is network security managed in your Google Cloud environment? This question has been under frequent consideration for security operations teams as domain responsibilities increasingly intertwine with the added complexity of infrastructure management within public clouds. On one hand, sophisticated hackers and state-sponsored threat actors are constantly scanning internet-exposed instances and exploiting newly found vulnerabilities. While on the other side, security teams increasingly face a multitude of challenges in scaling operations to detect and respond to threats effectively. This is a concerning paradigm, presenting a difficult scenario for understaffed security operations teams.
As presented, there is much more work to be done in the complicated and dynamic nature of cloud security and incident response operations. Unfortunately, enterprises lack many of the needed capabilities to achieve speed, scale and accuracy for effective response and remediation measures.
Thankfully, help is on the way. The recently announced Google Cloud IDS is a next-generation and cloud native intrusion detection service (IDS) that provides threat detection for intrusions, malware, spyware and command-and-control attacks. When this native Google Cloud service – built with Palo Alto Networks threat detection technology – is integrated with Cortex XSOAR, organizations can automate incident response processes and bring improvements to the overall network security posture.
Google Cloud IDS Content Pack
The latest content pack released for Cortex XOSAR features Google Cloud service integrations that allow organizations to automate remediation of intrusion and response activities. Now security teams can leverage scale and improved standardization to enforce security operations and incident response processes for an effective process around alerts.
Benefits:
- Automate intrusion detection, response and remediation actions across Google Cloud
- Standardize SecOps with Cortex XSOAR’s case management functionality
- Unify disjointed functions and bring collaboration across teams
- Enforce service level agreements for incident response processes based on standard operating procedures with the ability to auto-notify stakeholders
- Visibility into malicious activities hiding in your network traffic across Google Cloud VPC networks
- Bring speed, scale and accuracy into SecOps
How does the Cloud IDS content pack work?
Google Cloud IDS alerts are automatically ingested into Cortex XSOAR through the Google Cloud Pub/Sub integration. Cortex XSOAR automatically creates incidents for each ingested Cloud IDS alert and triggers the corresponding playbook. The playbook automatically extracts the attacker IPs and adds them to the cloud firewall rule deny list, thereby blocking the attacker from further accessing the VPCs. Google Cloud IDS provides complete visibility into the malicious activities in the VPCs, and Cortex XSOAR automates the incident response processes, and together they bring improvements to the overall network security posture.
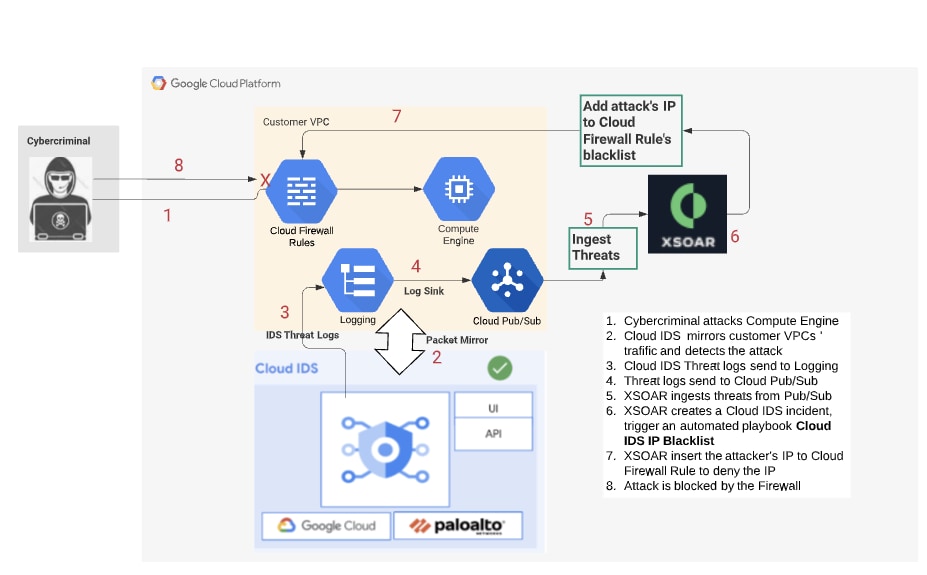
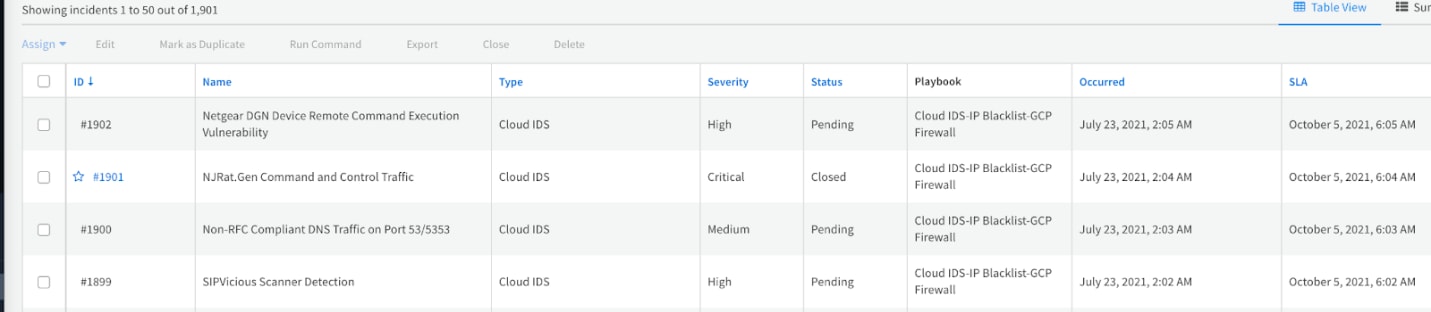
The Cloud IDS - IP Blacklist GCE Firewall playbook automatically extracts the attacker IP address from Cloud IDS alerts and adds the IP address to Google Cloud Compute Engine firewall deny list, thereby automatically blocking the attacker IP address from accessing Google Cloud. Please refer to the Cortex XSOAR documentation for a detailed deployment procedure.
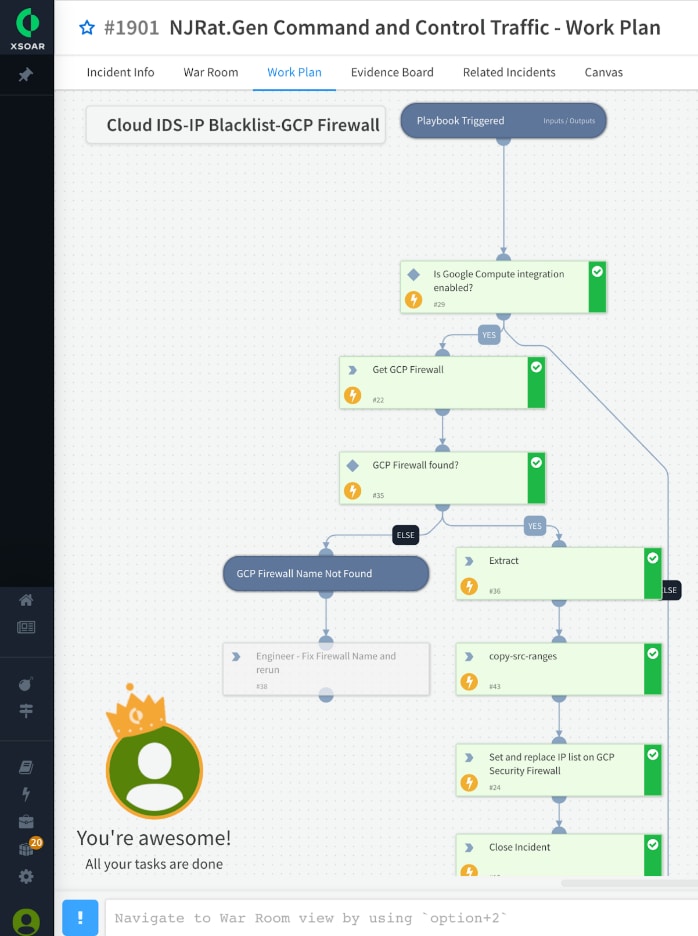
View of the automated Google Cloud IDS response playbook in action
Conclusion
With the help of Cortex XSOAR and Google Cloud IDS core capabilities, security operations, incident response and threat intel teams can work more efficiently by eliminating manual processes surrounding threat detection and response. Cortex XSOAR can automate the process of intrusion investigation, enrichment and threat hunting by orchestrating across Google Cloud and related tools (e.g., SIEM, firewalls, endpoint security and threat intelligence sources). The resulting scenario enables enhanced coordination and orchestration across security teams so that you can minimize risk and exposure to the enterprise.
You can learn more about Google Cloud IDS and sign up for access to the preview or take a deeper look at Cortex XSOAR and try the free Community Edition.