Introducing Cortex Exposure Management on Cortex XSIAM
Despite technological advancements, legacy vulnerability management (VM) systems leave enterprises grappling with an ever growing amount of vulnerabilities and inefficient, slow remediation processes. Organizations struggle to identify critical risks as they switch between multiple, disparate security tools. Manually sifting through a pile of alerts makes it impossible to prioritize and remediate the most pressing threats. Bring clarity to vulnerability management with a unified solution that connects all data, using AI and automation to help you handle your biggest risks.
The Problem with Legacy Vulnerability Management Approach
Legacy VM vendors, while pioneers in vulnerability assessments, have largely focused only on identifying vulnerabilities, neglecting the essential aspect of management and remediation, thus ultimately, leaving organizations exposed to AI-powered attacks.
Traditional vulnerability management is one of the least sophisticated processes in the security organization today. While there have been big advances in runtime protection on the agent and cloud, VM solutions still scan weekly or monthly, with typical SLAs that usually take days from start to finish. Couple this with having to use disjointed products to then apply that scanning data and actually take action to remediate, this process is just too slow.
This outdated approach has resulted in:
- An overwhelming backlog of vulnerabilities, with enterprises struggling to prioritize and address them effectively.
- A reliance on rudimentary tools like spreadsheets for managing vulnerabilities, leading to inefficient operations.
- Millions of dollars wasted on mitigating risks that, in reality, have little impact on the organization due to flawed prioritization methods.
- Excess effort spent remediating vulnerabilities that have solid compensating security controls, i.e. CVEs that aren’t internet facing, behind a firewall, or have a runtime agent installed.
- Slow and manual remediation processes that are spread across different teams with varied priorities, further complicating the security posture.
Attackers are now exploiting faster than ever, especially with the introduction of generative AI (GenAI), making it critical for security teams to have the right tools to automatically mitigate and remediate in real time. This has led to a significant evolution in the vulnerability management landscape to now encompass:
- Enterprise Vulnerability Management
- Cloud Vulnerability Management
- Attack Surface Management
- Cyber Asset Attack Surface Management
- Risk-Based Vulnerability Management
All of these approaches are now converging in a unified approach known as Exposure Management.
This comprehensive strategy goes beyond mere identification of vulnerabilities, it provides an all-encompassing view of the organization’s exposure, enabling more effective and efficient vulnerability management.
The Cortex Approach to Exposure Management
With our robust portfolio of security solutions and innovations, Palo Alto Networks is uniquely equipped to address these challenges. Cortex Exposure Management leverages our deep expertise and cutting-edge technology to transform how vulnerabilities are managed.
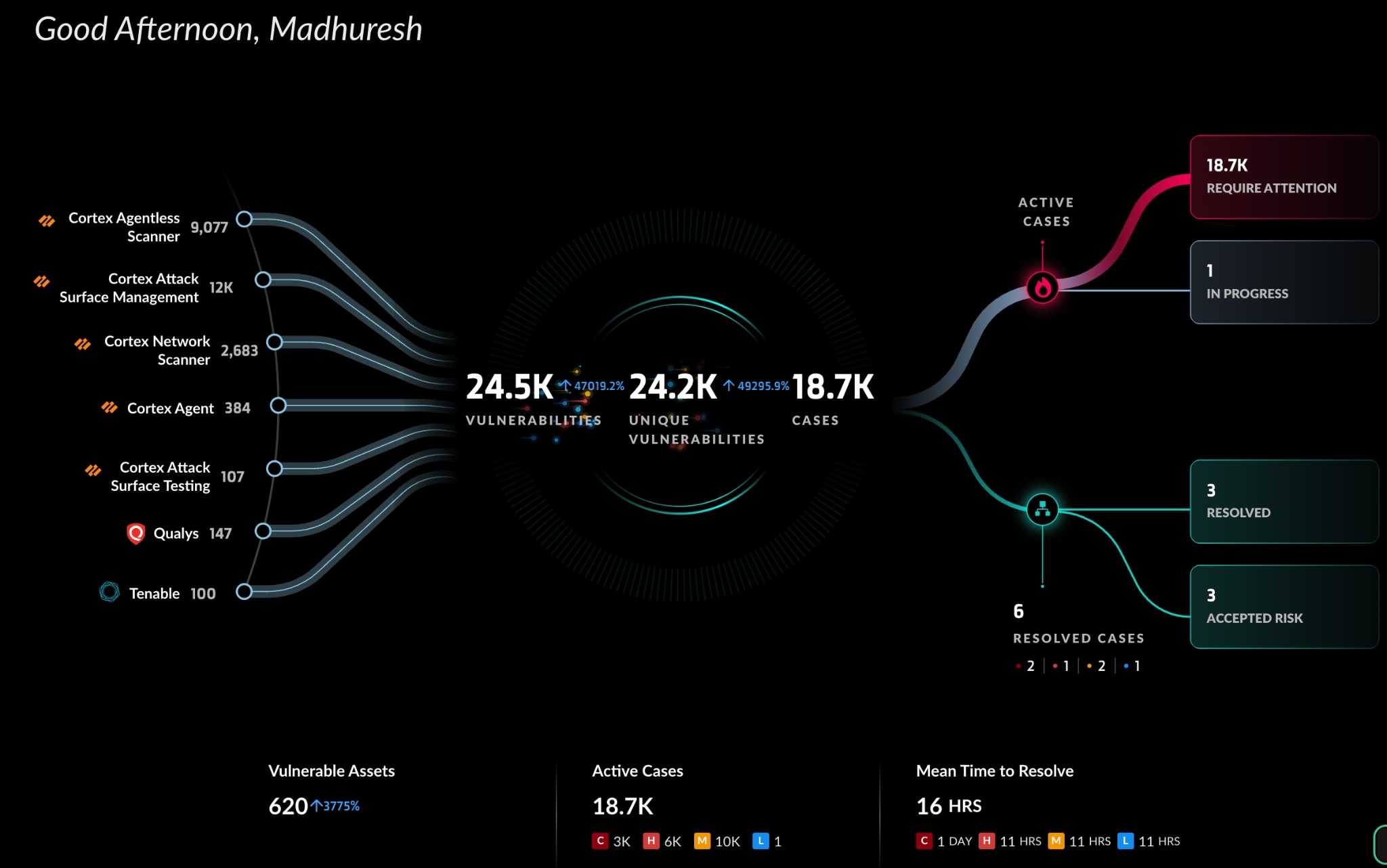
When speaking with customers, two major challenges consistently arise: the increasing workload and the slow pace of remediation. Our solution addresses these issues head-on:
- Vulnerability data source optimization integrates all Common Vulnerabilities and Exposures (CVEs) data sources, both native and third-party scans, to ensure full visibility of the vulnerabilities. This includes network, cloud, endpoint, perimeter, IoT/OT, and third-party scanners, delivering outside-in, inside-out visibility into your vulnerabilities.
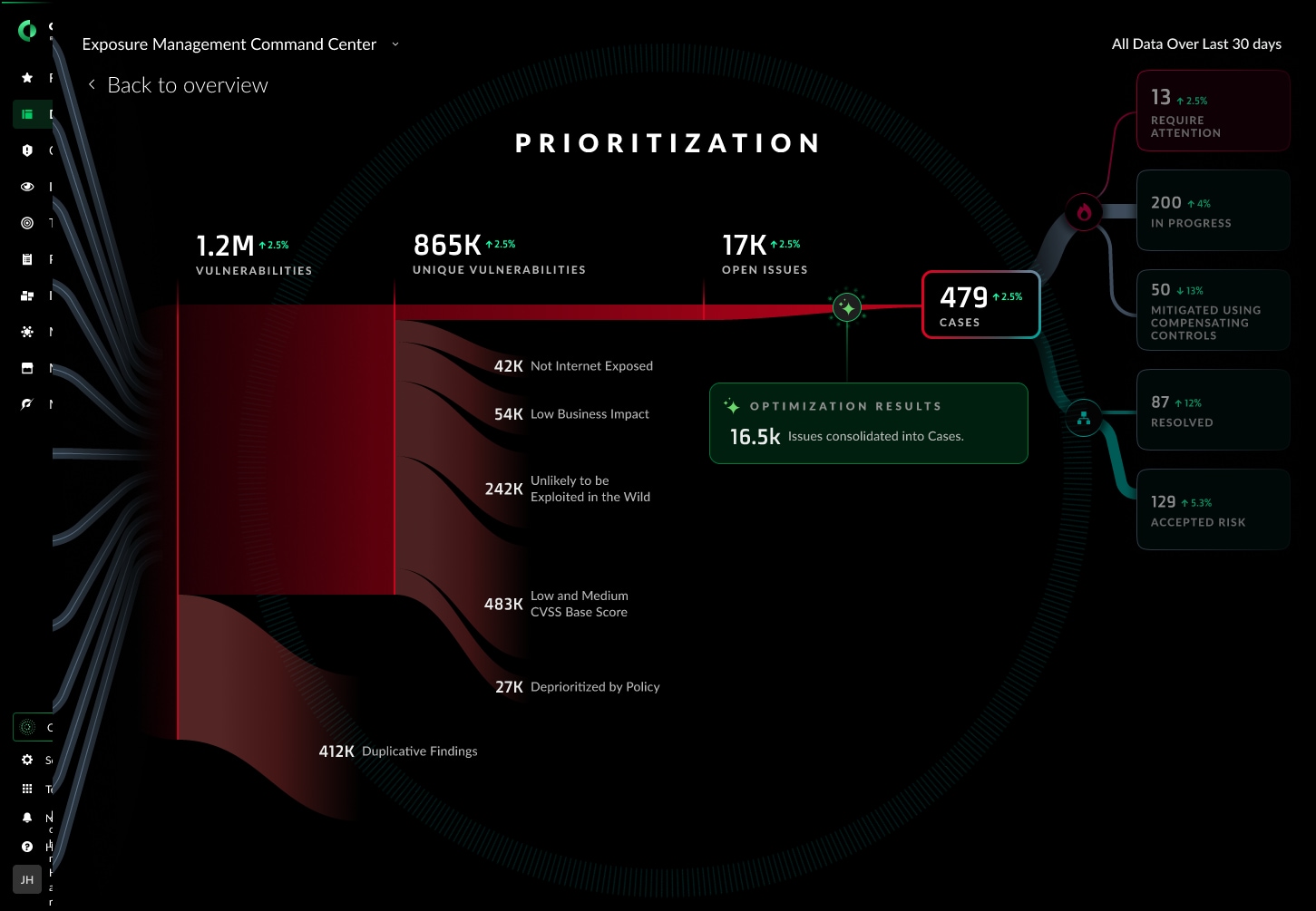
- AI-Based Precision Filtering evaluates the effectiveness of compensating controls and their relevance to new threats, while also gathering critical context like the asset owner, existing mitigations, reachability, and threat intel.
Research shows that only 6% of CVEs are exploitable in the wild and even less when considering existing controls and internet exposure factors. Rather than sorting through a haystack to find the important, exploitable threats, our AI-powered Cortex Exposure Management reduces alert fatigue by cutting vulnerability noise by up to 99%. This allows you to prioritize critical risks and automate remediation across your entire enterprise. By incorporating this intelligence into our prioritization, we ensure that efforts are focused on the vulnerabilities that truly matter.
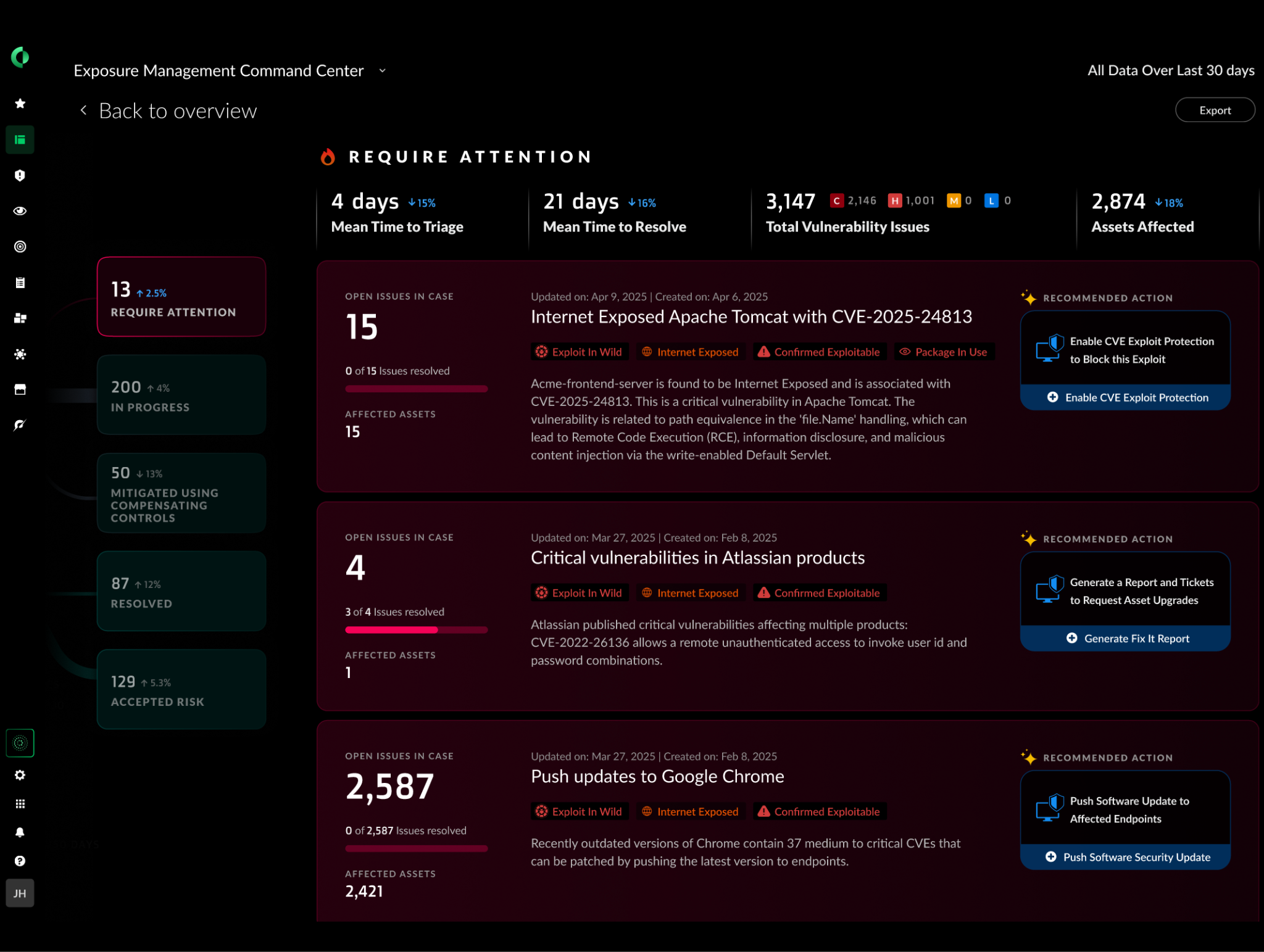
- Shift Right Strategy advocates for the immediate mitigation of critical vulnerabilities using existing security tools, followed by a methodical approach to remediation. This strategy is supported by AI-driven automation that not only recommends actions but also automates remediation workflows, which, when coupled with automated service ownership identification, significantly reduces the time and effort required by security teams.
With the launch of Cortex Exposure Management, Palo Alto Networks is set to redefine the standards of vulnerability management. By addressing the core deficiencies of traditional VM solutions and integrating advanced AI capabilities, we are empowering enterprises to not just manage, but master their security landscapes.
Discover how Exposure Management in Cortex XSIAM can transform your vulnerability management strategy: Visit our website or contact our sales team for a demonstration.