Cloud adoption has transformed how businesses operate while expanding the attack surface available to attackers. Threat actors are accelerating the speed, scale and sophistication of their campaigns, increasingly targeting legitimate credentials to quietly access systems and escalate privileges. Once inside, they move fast and across the board – from identity providers to cloud services, SaaS platforms, endpoints and other critical systems.
These identity-driven attacks are hard to detect since the activity looks legitimate - making real-time behavioral detection critical. Cloud security posture management (CSPM) tools focus on identifying configuration risks but do not offer runtime protection to detect and respond to active threats. They also rarely connect the dots between identity systems, infrastructure and application activity.
A recent incident involving a sophisticated threat actor highlights this challenge. The attack began with social engineering, which enabled privilege escalation across systems like Okta, Office 365 and AWS. The attackers mapped high-value data assets and attempted to exfiltrate sensitive files while leveraging native tools to avoid detection.
The blueprint presented in this attack reflects how cloud threats are evolving - distributed across services, identity-driven, and often invisible to traditional security tools. A solution like Cortex Cloud, which correlates signals across diverse data sources, is pivotal for detecting signatureless activity and surfacing context-rich alerts that enable swift effective response.
A Modern Attack in the Wild: The Scattered Spider Example
A recent financially motivated campaign by the threat actor (TA) Muddled Libra (aka “Scattered Spider”, UNC3944) illustrates how attackers exploit identities and trusted native tools to compromise systems stealthily.
Initial Access
The attack began with a phone call to an executive-level employee. Vishing (voice phishing) is often used by TAs to acquire credentials. Credential theft can be performed by directing the target to log in to a fake, attacker-controlled Okta page, or to persuade the user to reset their password to one provided by the attackers. Having captured the executive's credentials, the TA promptly reset the user's password and enrolled a new multifactor authentication (MFA) device, locking the victim out of their account and enabling the TA to gain administrative control over the Okta environment.
Privilege Escalation & Lateral Movement
Having gained these administrator privileges in Okta, the TA gained broad access across the organization, using single sign-on (SSO) not only for pivoting purposes but also to escalate their privileges in other systems, including Office 365, SharePoint and AWS.
The TA’s privilege escalation actions, such as creating new users and assigning admin rights, occurred in Okta, but the impact of those actions played out in AWS. This is the essence of cross-data-source detection – the security event is initiated in one environment, while its real consequences unfold in another. Without a unified data lake capable of correlating identity changes in Okta with subsequent cloud activity in AWS, such an attack could easily go undetected until significant damage occurs.
Discovery & Enumeration
Scattered Spider uses native SaaS interfaces, built-in AWS tools, and APIs to map high-value targets discreetly. In this tactic, dubbed “Living off the Land”, the TA utilizes legitimate binaries, like AWS CLI, instead of known exploits, evading signature-based detection and necessitating advanced behavioral analysis.
For example, Scattered Spider leveraged the AWS Systems Manager (SSM) service to execute arbitrary commands directly on EC2 instances, using APIs such as StartSession or SendCommand. Similar APIs also exist on other CSPs, such as Azure runcommand.
Pinpoint Exfiltration & Impact
Armed with precise insights gained through enumeration, the attackers swiftly identified critical data repositories, such as financial data stored in AWS. Utilizing their privileged access, the TA focused on executive-level data (e.g. financially related documents). Such information can be exfiltrated from services such as S3, EBS snapshots, and Office 365.
Cortex CDR: Purpose-Built for Real-World Threats
Most security tools detect isolated events and lack the ability to identify multistage, stealthy attacks, like those conducted by Scattered Spider. Cortex Cloud Detection and Response (CDR) takes a fundamentally different approach. It ingests telemetry from across your environment and enriches it with cloud posture context, enabling the detection of early attack signals that traditional tools often miss. To illustrate the breadth of data sources and correlations involved in this incident, we’ll walk through a few of the key detectors that contributed to its detection.
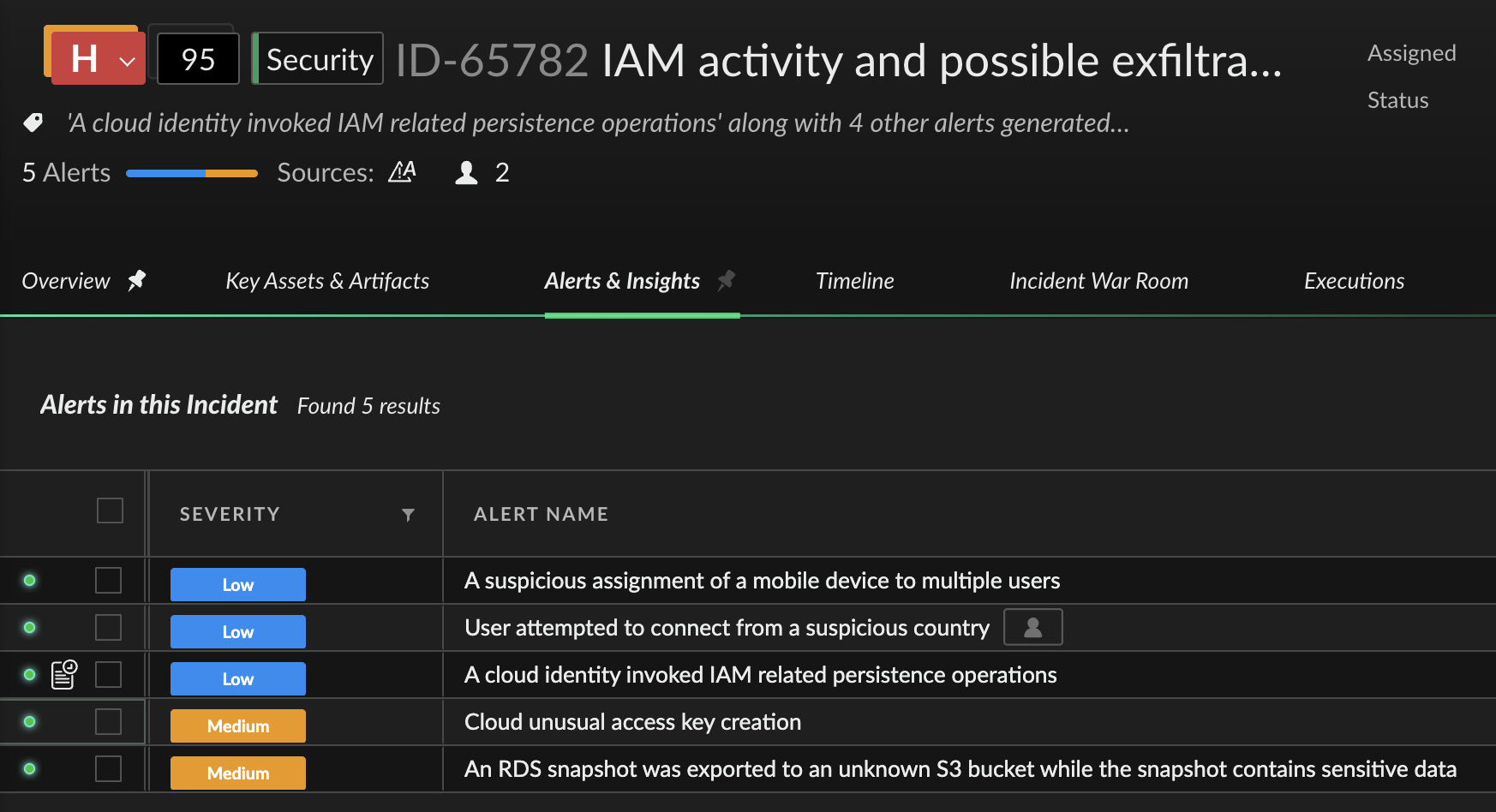
By inspecting and correlating signals from Okta, AWS CloudTrail and Office 365 access provider event logs, Cortex CDR uncovered the full lifecycle of the attack. It detected the password reset, as well as anomalous MFA device enrollment and API tokens originating from unfamiliar networks, immediately flagging potential account takeovers before further lateral movement could be achieved.
- Detectors: Okta account reset password attempt, Okta device assignment, User added a new device to Okta Verify instance
Cortex CDR flagged a number of abnormal behaviors that are indicative of attackers using legitimate cloud credentials to establish a foothold in the cloud for persistence and the next phases of the attack.
- Detectors: A user logged in to the AWS console for the first time, Cloud unusual access key creation
Cortex CDR detected cloud identities attempting to discover available infrastructure and services - often a sign that an attacker is mapping out the environment.
- Detectors: Cloud infrastructure enumeration activity, Multi region enumeration activity
The TA was very selective, targeting the exfiltration of a handful of files, a challenging scenario to detect. However, by leveraging the Data Security Posture Management (DSPM) capability, the Cortex Cloud platform identified that the exfiltrated files contained sensitive data, automatically raising the alert’s severity - bringing focus to an otherwise under-the-radar attacker activity.
- Detectors: An identity performed a suspicious download of multiple cloud storage objects, User accessed multiple O365 AIP sensitive files, Cloud snapshot containing sensitive data was shared with unusual AWS account(s)

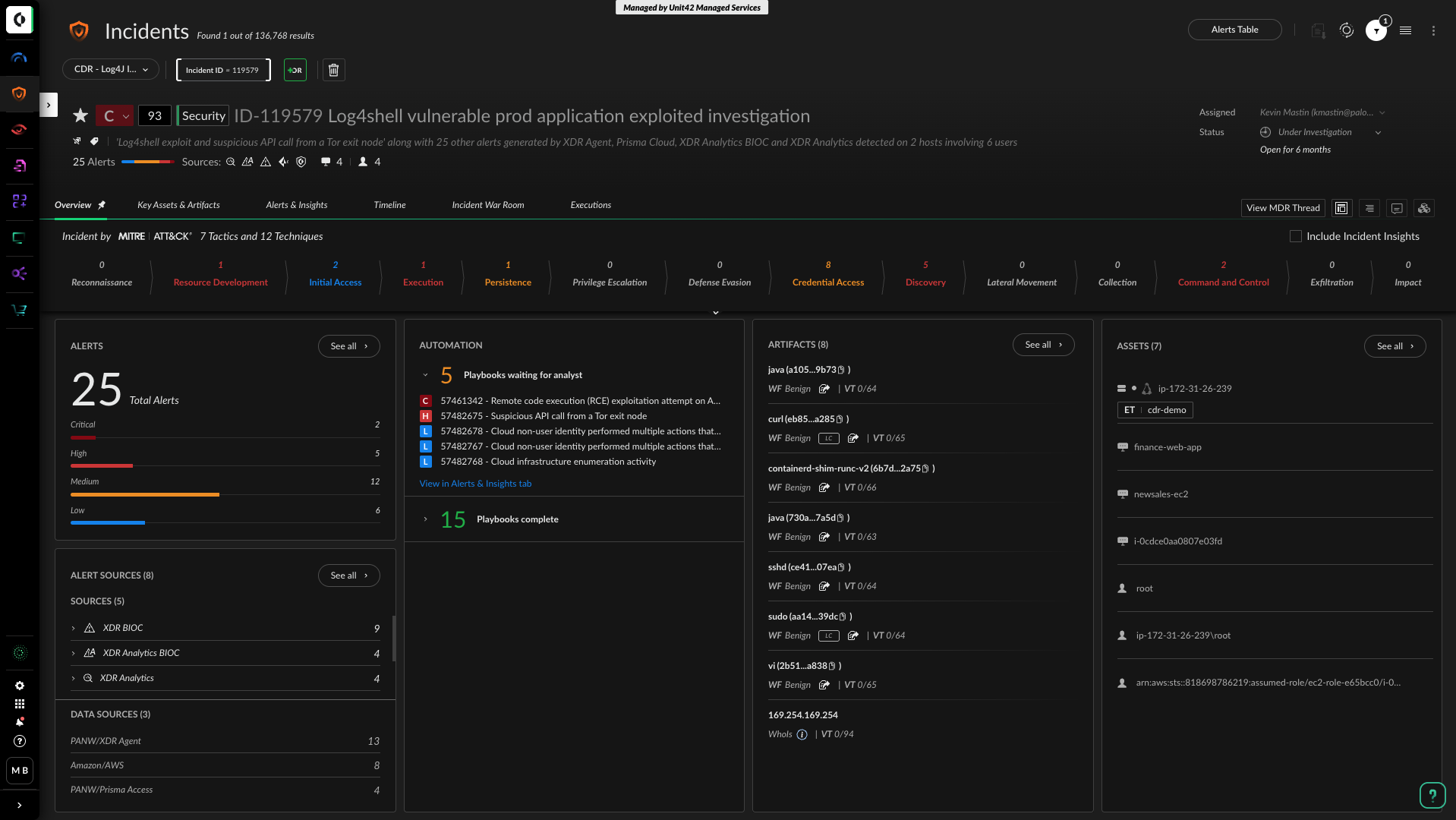
The Architectural Advantage: Unified Detection Across Domains
Out of the Box Cross-Domain Detection
With Cortex Cloud, events from Okta, cloud service providers, Azure AD, SaaS logs, network, endpoint, container runtime data and more are streamed into a unified data lake that uses advanced detectors to uncover the most sophisticated threats.
Context-Aware Severities
In addition to runtime events, the Cortex Cloud data lake also ingests posture findings from various modules (Cloud, Data, AI, Identity, Kubernetes and more. Cortex Cloud automatically leverages these findings for context-enhanced detections. For example, If a suspicious action targets a production asset that contains PII, Cortex Cloud factors that into the alert, ensuring alerts reflect not just the security issue but also the sensitivity and exposure of the affected asset.
Precision AI-Driven Investigation
SmartGrouping connects related tactics such as initial access, persistence, and exfiltration into a single incident with a clear timeline and causal context. Analysts no longer need to jump between tools or guess what’s related. They get the full picture quickly, reducing triage time from hours to minutes.
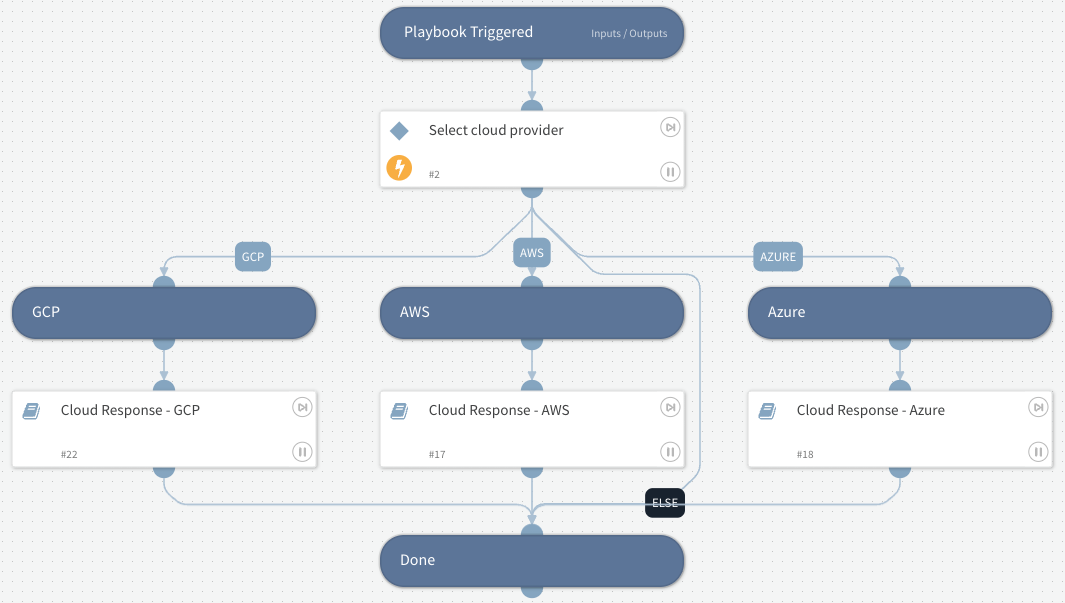
Automated Response
Cortex Cloud features hundreds of out-of-the-box playbooks for SOAR. Security teams can act fast, using workflows that can be triggered manually or configured to run automatically based on predefined rules. This gives teams the ability to respond in minutes, not hours or days.
See it in Action
Interested in learning more about Cortex Cloud? Check out the product tour or sign up for a personalized demo.