General Data Protection Regulation, or GDPR, has been the center of conversation for European Union (EU) policymakers and technologists since 2018. In short, GDPR bans businesses from collecting or processing customer data without explicit consent.
This may seem simple, however, many of the digital platforms and tools that enterprises love track user data, particularly social media. The release of GDPR has caused a massive shift in how EU businesses can interact with their customers online and has caused a ripple effect of necessary large-scale website overhauls for organizations of all sizes.
For example, the Meta Pixel (formerly Facebook Pixel) is a set of code that allows marketers to measure, optimize, and build audiences for ad campaigns. However, under GDPR, EU companies must receive explicit consent before using these on landing pages and other web forms. Failing to remove it from your site or adequately disclosing it is a violation of GDPR and can result in hefty fines up to 10M euros.
This marketing tracking code is not limited to Meta. It is found across many social media platforms like TikTok, Twitter, and more. Large enterprises have thousands of websites using tracking technologies, some of these known and others largely unknown to the organization leading to potential violation of GDPR.
These problems are compounded for large organizations by:
- Abandoned marketing websites
- Unknown websites of acquired companies
Abandoned websites create an even larger problem, when promotional sites are forgotten, leaving Pixels out in the wild with little hope of finding them. This presents the challenge of not just updating websites but finding them in the first place.
The easiest way to identify these assets is to have a way to manage your web attack surface and be alerted in real time if any live web asset that belongs to your organization is running tracking code.
Xpanse is an Active Attack Surface management solution that helps your organization actively discover, learn about, and respond to unknown risks in all connected systems and exposed services. With the Web Attack Surface Management (Web ASM) feature, your security teams can get complete, current, and accurate visibility into your public-facing web infrastructure without any manual work.
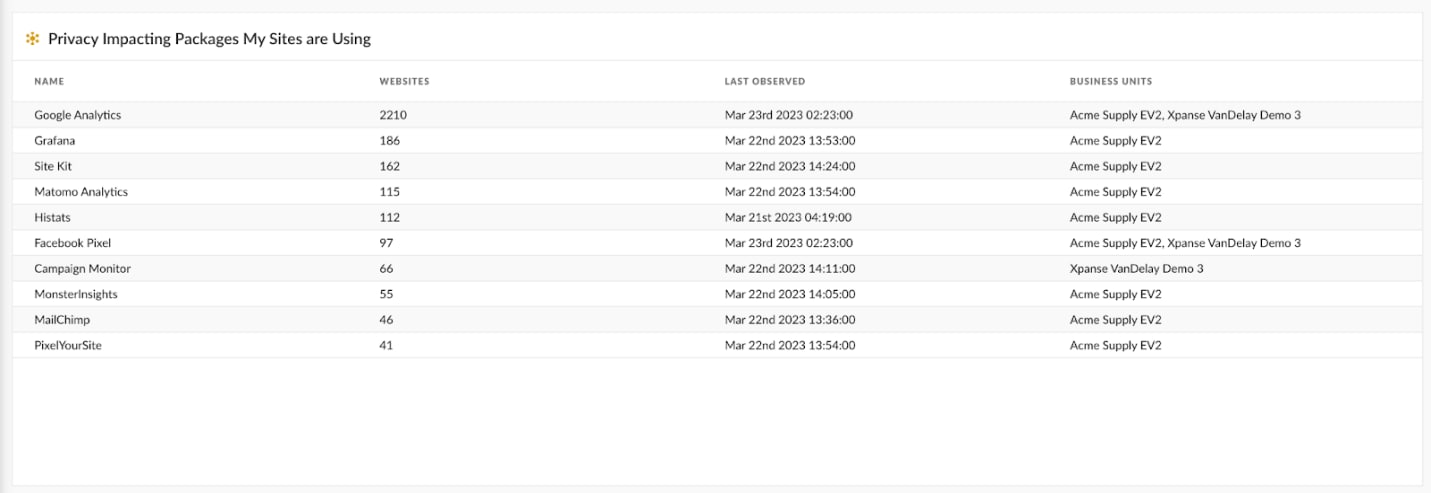
Xpanse scans and crawls the internet daily to find known and unknown websites and pulls down privacy packages that each site uses. Through a mix of web crawling and AI engines working together to discover and classify the different web technologies, we are able to accurately identify your web sprawl and associated risks, including websites in your environment that potentially violate GDPR. Additionally, Web ASM performs a security best practice analysis to identify misconfigurations and potential vulnerabilities.
Organizations can use the high-level dashboard to view all privacy impacting packages that their organization’s websites are using in order to quickly take down and de-risk against GDPR compliance. This helps your organization not only prevent potential violations but also increase operational efficiency of your security teams by automatically inventorying these packages.
Xpanse Web ASM continuously discovers and monitors your website inventory and web technologies:
- Identifies insecure and misconfigured websites
- Identifies websites failing security best practices
- Tracks and measures risk from third-party libraries or dependencies
- And much more…