Disclaimer: The company names and brands referenced in this blog post are mentioned solely as examples of cybercriminals fraudulently impersonating these legitimate organizations. These references do not imply any association, endorsement, or security vulnerabilities with the actual companies mentioned. The legitimate companies had no involvement in these fraudulent activities and all trademarks remain the property of their respective owners.
The Evolution of Email Threats
Cybercriminals are now weaponizing generative AI to create flawless, convincing, and personalized phishing campaigns that can easily bypass traditional security solutions. Traditional Secure Email Gateways (SEGs) and Integrated Cloud Email Security (ICES) solutions analyze emails in isolation, leaving them blind to the subtle, multi-stage attacks that define the modern AI-driven threat landscape.
A new approach is needed—one that sees beyond the inbox. The recently launched Advanced Email Security module in Cortex addresses this by correlating threat data across email, identity, endpoints, cloud, SaaS, and the network to see the full attack picture. The following real-world examples from Palo Alto Networks customers demonstrate how this integrated approach stops sophisticated threats that other tools miss.
Common Attack Tactics and Themes
Theme 1: Brand Impersonation and Trust Exploitation
Modern attackers have perfected the art of impersonating trusted brands to lower user defenses and bypass security filters.
Financial Services Impersonation - Wells Fargo Campaign
In this sophisticated attack, threat actors impersonated Wells Fargo Bank, targeting multiple users within a financial institution. The attack began with a seemingly routine Google Drive notification about a shared item—a tactic designed to leverage users' inherent trust in legitimate cloud services.
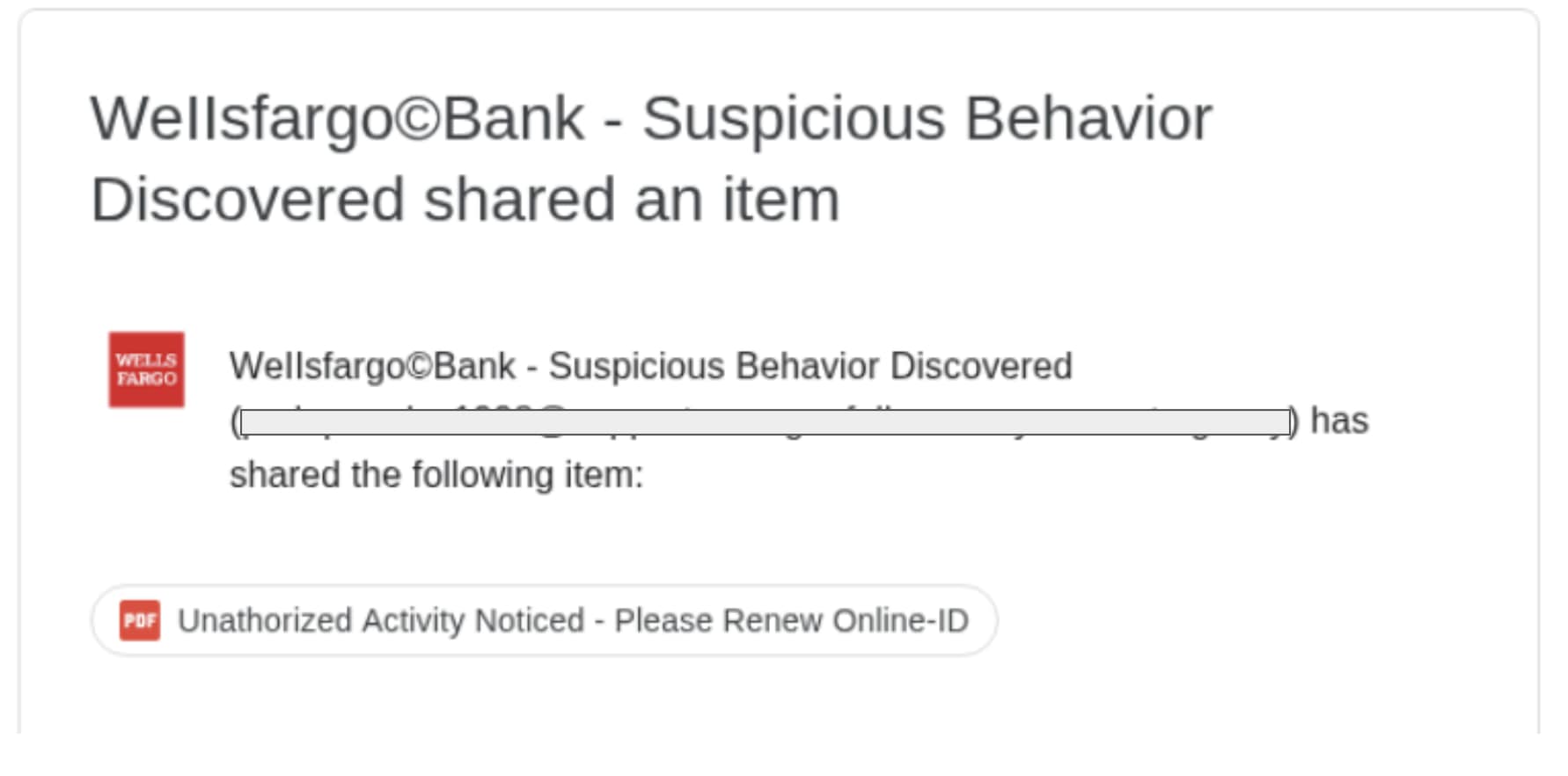

The document link titled "Unauthorized Activity Noticed" created urgency and alarm, leading to a document with a "VERIFY" button that redirected to a malicious website protected by CAPTCHA. This evasion technique gave users confidence in the site's legitimacy while blocking automated URL scanners.
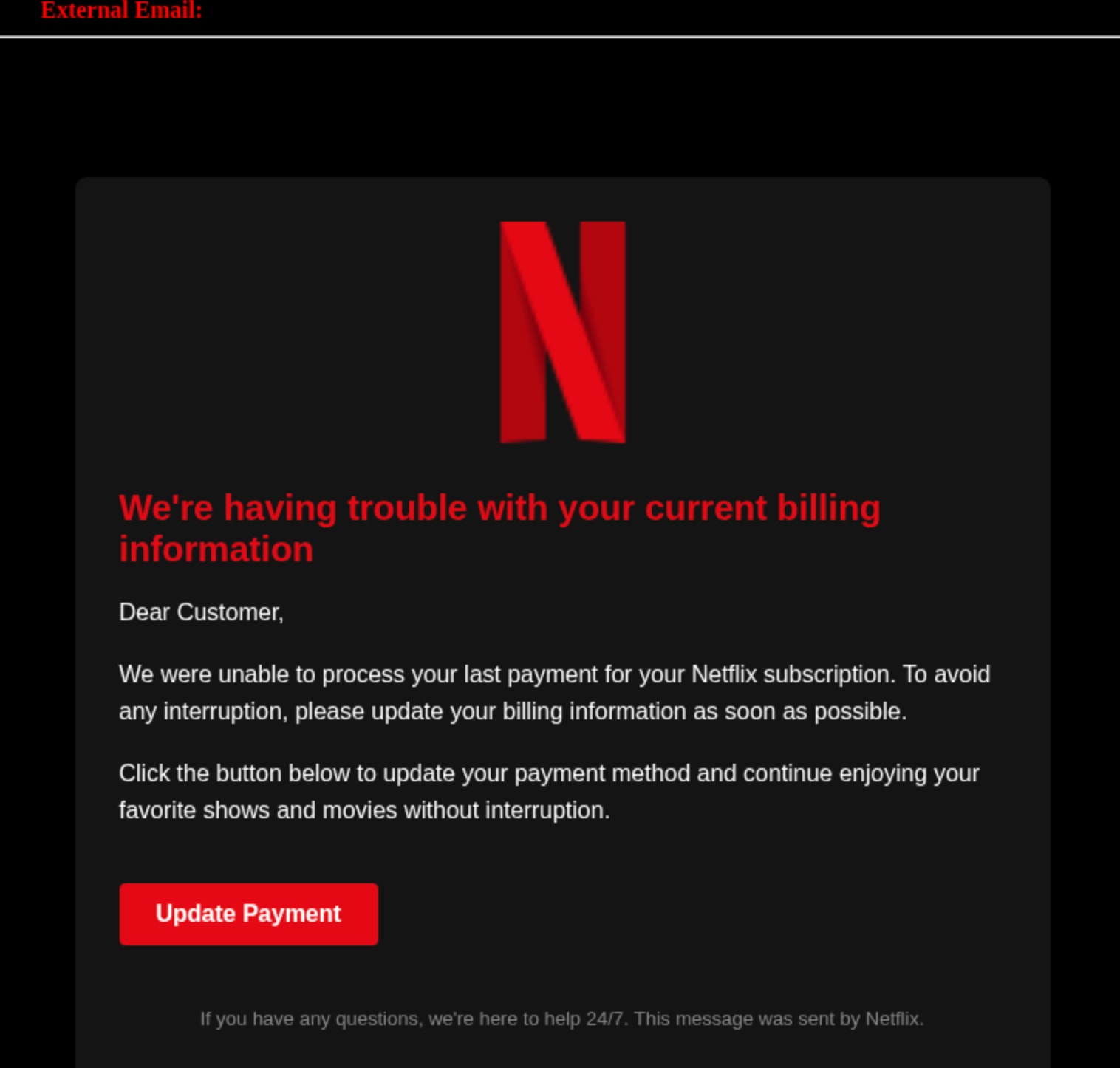
Streaming Services Impersonation - Netflix and Spotify
Two separate campaigns targeted popular streaming services. The Netflix impersonation used the subject line "We're having trouble with your current billing information," while the Spotify attack warned of "a problem with your billing information." Both campaigns created visual replicas of legitimate communications, using official logos and branding to establish authenticity.
Why Traditional Security Failed:
- Cloud email providers allowed emails to bypass spam filtering due to legitimate service integration
- Secure email gateways found no malware or known malicious signatures
- Well-formatted HTML emails without attachments passed through standard filters
- CAPTCHA protection blocked automated URL analysis tools
How Advanced Email Security Stopped These Attacks: Advanced Email Security analyzed sender authentication records (SPF, DKIM, DMARC) and recognized brand impersonation signs, including high-reputation logos combined with low-reputation sending domains. The AI-powered detection identified urgent calls-to-action related to financial information as high-risk patterns and blocked the threats in real-time.
Theme 2: Hyper-Personalization and Social Engineering
Attackers are leveraging detailed reconnaissance to create highly personalized attacks that appear legitimate and relevant to specific targets.
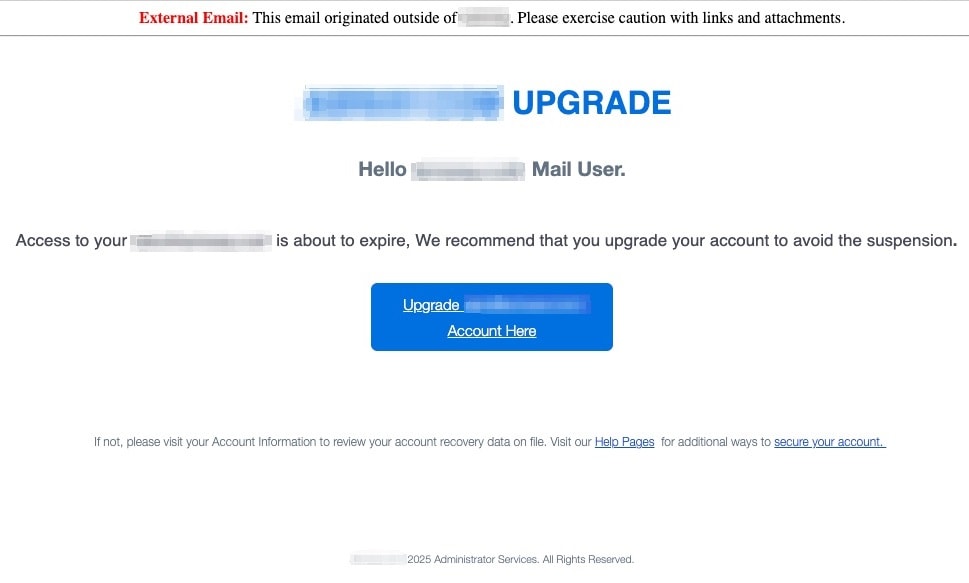
The Administrator Services Deception
A highly targeted phishing email was sent to a generic but important email address, claiming the user's account was about to expire and needed immediate upgrading. The attack featured flawless execution with a fake but official-looking "2025 Administrator Services" signature and no grammatical errors, making it indistinguishable from legitimate corporate communication.
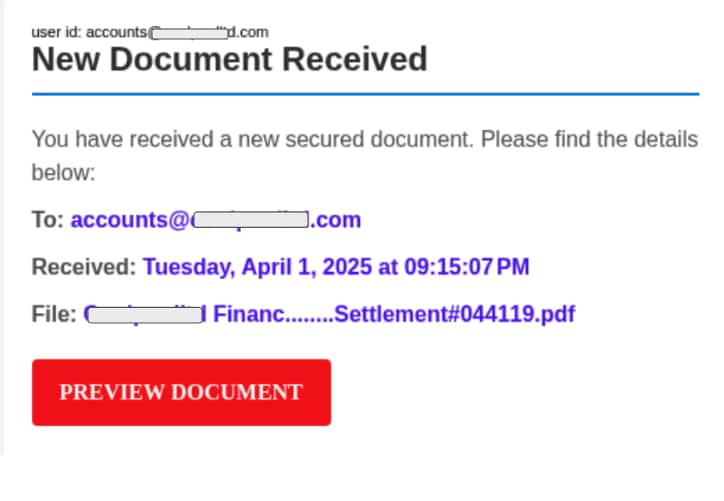
Personalized Document Fraud
This attack impersonated a document sharing service with an email titled "New Document Received." The email specifically addressed the recipient by name and referenced their company, creating strong legitimacy. The link led to a malicious website protected by CAPTCHA to avoid automated detection.
Internal IT Department Spoofing
Attackers impersonated an internal IT department, sending server security upgrade notifications claiming the recipient's mailbox was "out of date." The email used corporate branding and was specifically tailored to the victim's company to appear authentic.
Why Traditional Security Failed:
- Personalization and lack of obvious malicious content bypassed spam filters
- No known malicious signatures were present
- External emails crafted to appear internal confused basic filtering systems
How Advanced Email Security Stopped These Attacks: Cortex Advanced Email Security's Large Language Models (LLMs) analyzed underlying intent rather than just scanning for keywords. The AI-powered detection recognized combinations of urgency, impersonation tactics, and suspicious authentication patterns. The system employed "multi-signal" detection, combining multiple context clues to identify sophisticated phishing attempts.
Theme 3: Localization and Cultural Targeting
Sophisticated attackers are tailoring campaigns to specific regions and languages to increase effectiveness and evade detection.
Brazilian Invoice Fraud Campaign
This attack demonstrated advanced sophistication through localization. An email sent to a Brazilian company contained what appeared to be a standard invoice written in Portuguese. The attached file was named to mimic legitimate Brazilian invoice format (Nota Fiscal Eletrônica). The "invoice" was actually a malicious dropper hosted on trusted services like Dropbox, configured to force automatic downloads.
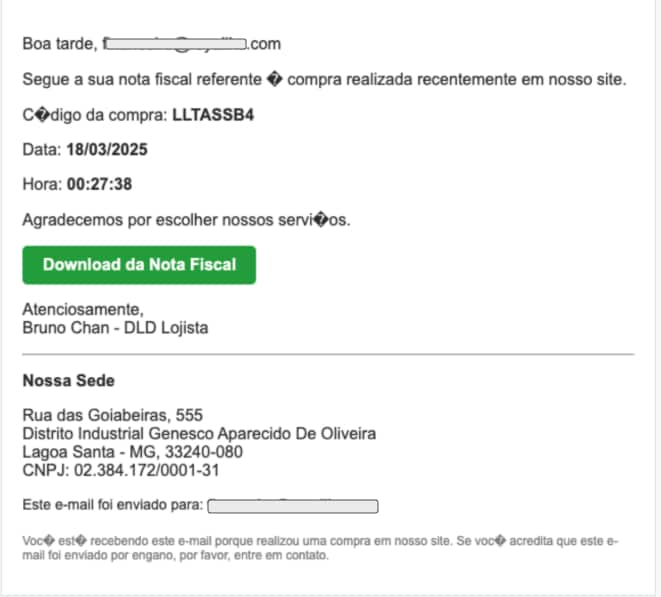
Why Traditional Security Failed:
- URLs pointed to trusted domains like Dropbox
- Scanners couldn't predict forced downloads of malicious executables
- Localized content and formatting appeared legitimate
How Advanced Email Security Stopped This Attack: Advanced Email Security detected financial fraud intent through deep content inspection. The system identified dangerous combinations including authentication failures and mismatches between displayed link text (.pdf) and actual delivered files (.exe). The LLM's foreign language support enabled effective analysis of localized attacks.
The Unified Security Advantage
The attacks targeting organizations today are multifaceted and designed to bypass legacy security controls. These cases demonstrate that traditional email security tools analyzing threats in isolation are frequently evaded. Cortex Advanced Email Security stops modern threats by leveraging a fundamentally different approach:
Cross-Domain Visibility: Integrating email data with endpoint, identity, and network telemetry allows AI-driven engines to understand full context and true intent behind attacks.
AI-Powered Analysis: Large Language Models analyze underlying intent rather than relying solely on signatures or keywords, enabling detection of novel and sophisticated attacks.
Multi-Signal Detection: Combining multiple context clues and behavioral indicators provides comprehensive threat assessment that individual security tools cannot achieve.
Real-Time Correlation: By correlating threat data across the entire security ecosystem, the solution identifies sophisticated campaigns before they can result in breaches.
Conclusion
The modern threat landscape demands a unified security approach. Attackers use diverse tactics—from brand impersonation and localized fraud to internal phishing and social engineering. Security solutions focused only on external threats or known signatures inevitably miss critical indicators.
Cortex Advanced Email Security succeeds where traditional tools fail because it enables unified visibility across all attack vectors. By analyzing internal and external emails and correlating that data with endpoint and identity signals, it detects and responds to the full spectrum of email-based threats, securing organizations from every angle.
To learn more, visit our Cortex Advanced Email Security page.