-
What Is a Cyber Attack?
- Threat Overview: Cyber Attacks
- Cyber Attack Types at a Glance
- Global Cyber Attack Trends
- Cyber Attack Taxonomy
- Threat-Actor Landscape
- Attack Lifecycle and Methodologies
- Technical Deep Dives
- Cyber Attack Case Studies
- Tools, Platforms, and Infrastructure
- The Effect of Cyber Attacks
- Detection, Response, and Intelligence
- Emerging Cyber Attack Trends
- Testing and Validation
- Metrics and Continuous Improvement
- Cyber Attack FAQs
-
What Is a Zero-Day Attack? Risks, Examples, and Prevention
- Zero-Day Attacks Explained
- Zero-Day Vulnerability vs. Zero-Day Attack vs. CVE
- How Zero-Day Exploits Work
- Common Zero-Day Attack Vectors
- Why Zero-Day Attacks Are So Effective and Their Consequences
- How to Prevent and Mitigate Zero-Day Attacks
- The Role of AI in Zero-Day Defense
- Real-World Examples of Zero-Day Attacks
- Zero-Day Attacks FAQs
-
What Is Lateral Movement?
- Why Attackers Use Lateral Movement
- How Do Lateral Movement Attacks Work?
- Stages of a Lateral Movement Attack
- Techniques Used in Lateral Movement
- Detection Strategies for Lateral Movement
- Tools to Prevent Lateral Movement
- Best Practices for Defense
- Recent Trends in Lateral Movement Attacks
- Industry-Specific Challenges
- Compliance and Regulatory Requirements
- Financial Impact and ROI Considerations
- Common Mistakes to Avoid
- Lateral Movement FAQs
-
What is a Botnet?
- How Botnets Work
- Why are Botnets Created?
- What are Botnets Used For?
- Types of Botnets
- Signs Your Device May Be in a Botnet
- How to Protect Against Botnets
- Why Botnets Lead to Long-Term Intrusions
- How To Disable a Botnet
- Tools and Techniques for Botnet Defense
- Real-World Examples of Botnets
- Botnet FAQs
- What is a Payload-Based Signature?
-
Dark Web Leak Sites: Key Insights for Security Decision Makers
- Dark Web Leak Sites Explained
- Evolving Extortion Tactics
- The Role of Leak Sites in Ransomware Double Extortion
- Critical Risks Exposed by Data Leak Sites
- Anatomy of a Dark Web Leak Site
- Proactive Defense: How Organizations Can Mitigate Dark Web Leaks
- Dark Web Leak Site FAQs
- What to Do If Your Organization Appears on a Dark Web Leak Site
-
What is Spyware?
- Cybercrime: The Underground Economy
-
What Is Cross-Site Scripting (XSS)?
- XSS Explained
- Evolution in Attack Complexity
- Anatomy of a Cross-Site Scripting Attack
- Integration in the Attack Lifecycle
- Widespread Exposure in the Wild
- Cross-Site Scripting Detection and Indicators
- Prevention and Mitigation
- Response and Recovery Post XSS Attack
- Strategic Cross-Site Scripting Risk Perspective
- Cross-Site Scripting FAQs
- What Is a Dictionary Attack?
- What Is a Credential-Based Attack?
-
What Is a Denial of Service (DoS) Attack?
- How Denial-of-Service Attacks Work
- Denial-of-Service in Adversary Campaigns
- Real-World Denial-of-Service Attacks
- Detection and Indicators of Denial-of-Service Attacks
- Prevention and Mitigation of Denial-of-Service Attacks
- Response and Recovery from Denial-of-Service Attacks
- Operationalizing Denial-of-Service Defense
- DoS Attack FAQs
- What Is Hacktivism?
- What Is a DDoS Attack?
-
What Is CSRF (Cross-Site Request Forgery)?
- CSRF Explained
- How Cross-Site Request Forgery Works
- Where CSRF Fits in the Broader Attack Lifecycle
- CSRF in Real-World Exploits
- Detecting CSRF Through Behavioral and Telemetry Signals
- Defending Against Cross-Site Request Forgery
- Responding to a CSRF Incident
- CSRF as a Strategic Business Risk
- Key Priorities for CSRF Defense and Resilience
- Cross-Site Request Forgery FAQs
- What Is Spear Phishing?
-
What Is Brute Force?
- How Brute Force Functions as a Threat
- How Brute Force Works in Practice
- Brute Force in Multistage Attack Campaigns
- Real-World Brute Force Campaigns and Outcomes
- Detection Patterns in Brute Force Attacks
- Practical Defense Against Brute Force Attacks
- Response and Recovery After a Brute Force Incident
- Brute Force Attack FAQs
- What Is an Advanced Persistent Threat?
- What is an Exploit Kit?
- What Is Credential Stuffing?
- What Is Smishing?
-
What is Social Engineering?
- The Role of Human Psychology in Social Engineering
- How Has Social Engineering Evolved?
- How Does Social Engineering Work?
- Phishing vs Social Engineering
- What is BEC (Business Email Compromise)?
- Notable Social Engineering Incidents
- Social Engineering Prevention
- Consequences of Social Engineering
- Social Engineering FAQs
-
What Is a Honeypot?
- Threat Overview: Honeypot
- Honeypot Exploitation and Manipulation Techniques
- Positioning Honeypots in the Adversary Kill Chain
- Honeypots in Practice: Breaches, Deception, and Blowback
- Detecting Honeypot Manipulation and Adversary Tactics
- Safeguards Against Honeypot Abuse and Exposure
- Responding to Honeypot Exploitation or Compromise
- Honeypot FAQs
- What Is Password Spraying?
- How to Break the Cyber Attack Lifecycle
-
What Is Phishing?
- Phishing Explained
- The Evolution of Phishing
- The Anatomy of a Phishing Attack
- Why Phishing Is Difficult to Detect
- Types of Phishing
- Phishing Adversaries and Motives
- The Psychology of Exploitation
- Lessons from Phishing Incidents
- Building a Modern Security Stack Against Phishing
- Building Organizational Immunity
- Phishing FAQ
- What Is a Rootkit?
- Browser Cryptocurrency Mining
- What Is Pretexting?
- What Is Cryptojacking?
What is a Command and Control Attack?
Malicious network attacks have been on the rise in the last decade. One of the most damaging attacks, often executed over DNS, is accomplished through command and control, also called C2 or C&C. Command and control is defined as a technique used by threat actors to communicate with compromised devices over a network.
C2 usually involves one or more covert channels, but depending on the attack, specific mechanisms can vary greatly. Attackers use these communication channels to deliver instructions to the compromised device to download additional malware, create botnets or exfiltrate data.
According to the MITRE ATT&CK framework, there are over 16 different command-and-control tactics used by adversaries, including numerous subtechniques:
- Application Layer Protocol
- Communication Through Removable Media
- Data Encoding
- Data Obfuscation
- Dynamic Resolution
- Encrypted Channel
- Fallback Channels
- Ingress Tool Transfer
- Multi-Stage Channels
- Non-Application Layer Protocol
- Non-Standard Port
- Protocol Tunneling
- Proxy
- Remote Access Software
- Traffic Signaling
- Web Service
How a Command and Control Attack Works
The attacker starts by establishing a foothold to infect the target machine, which may sit behind a Next-Generation Firewall. This can be done in a variety of ways:
- Via a phishing email that:
- Tricks the user into following a link to a malicious website
or - opening an attachment that executes malicious code.
- Tricks the user into following a link to a malicious website
- Through security holes in browser plugins.
- Via other infected software.
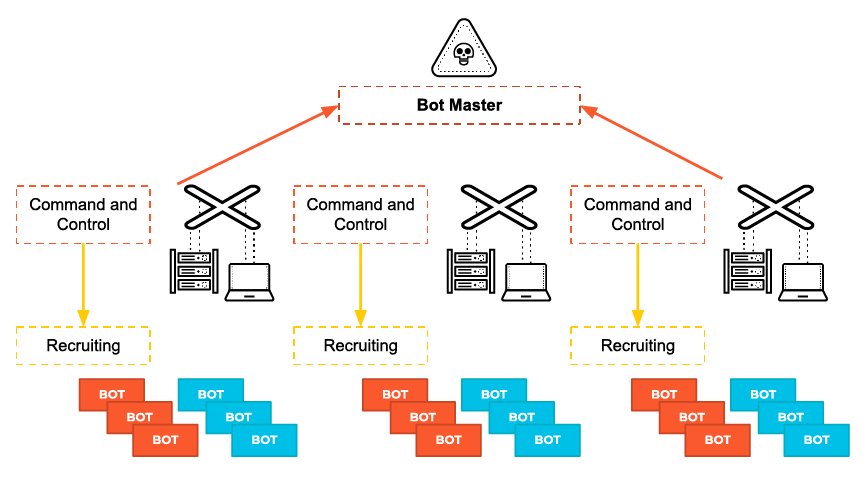
Once communication is established, the infected machine sends a signal to the attacker’s server looking for its next instruction. The compromised host will carry out the commands from the attacker’s C2 server and may install additional software. Many attackers try to blend C2 traffic with other types of legitimate traffic like HTTP/HTTPS or DNS. The goal is to avoid being detected.
The attacker now has complete control of the victim’s computer and can execute any code. The malicious code will typically spread to more computers, creating a botnet – a network of infected devices. In this way, an attacker can obtain full control of a company network.
Command and control is one of the last stages of the kill chain (coined by Lockheed Martin). It occurs right before threat actors complete their objectives. This means that the attacker has already bypassed other security tools that may have been in place. Thus, it is critical for security professionals to quickly discover and prevent C2.
Types of Command and Control Techniques
There are three different models C2C attacks use. These models dictate how the infected machine will communicate with the command and control server. Each were designed to evade discovery as effectively as possible.
1. Centralized architecture
This is likely the most common model, much like a client-server transaction architecture. When a new computer is infected by a bot, it will join the botnet by initiating a connection to the C&C server. Once joined to the channel, the bot waits on the C&C server for commands from the botmaster. Attackers often use prevalent hosting services for C2c servers.
This model can be easy to detect and block, as the commands originate from one source. Therefore, the IP can be quickly detected and blocked. However, some cybercriminals have adapted their approach by employing load balances, redirectors, and proxies in their setup. In this case, detection is more challenging.
2. Peer to peer (P2P) architecture
This model is decentralized. Rather than relying on a central server, botnet members transfer commands between nodes. This makes the P2P model much more difficult to detect. Even if detected, it’s usually only possible to take down one node at a time.
The peer-to-peer model is used frequently in tandem with the centralized model for a hybrid configuration. The P2P architecture works as a fallback when the main server is compromised or taken down.
3. Random architecture
The random architecture model is by far the hardest to detect. This is by design. The objective is to prevent security personnel from tracing and shutting down the C&C server or identifying the botnet’s chain of command. This model functions by transmitting communications to the infected host (or botnet) from disparate sources:
- IRC chat rooms
- CDNs
- Social media comments
Cybercriminals improve their odds of success by selecting trusted, commonly used sources.
Devices Targeted by C&C
Command and control attacks can target nearly any computing device, including but not limited to.
- Smart phones
- Tablets
- Desktops
- Laptops
- IoT devices
IoT devices have the potential to be at increased risk of C&C for various reasons:
- They are hard to control as a result of limited user interfaces.
- IoT devices are usually inherently insecure.
- Smart objects rarely get patched, if ever.
- Internet of Things devices share large amounts of data via the Internet.
What Hackers Can Accomplish Through Command and Control
- Malware delivery: With control of a compromised machine within a victim’s network, adversaries can trigger the download of additional malware.
- Data theft: Sensitive data, such as financial documents, can be copied or transferred to an attacker’s server.
- Shutdown: An attacker can shut down one or several machines, or even bring down a company’s network.
- Reboot: Infected computers may suddenly and repeatedly shutdown and reboot, which can disrupt normal business operations.
- Defense evasion: Adversaries commonly attempt to mimic normal, expected traffic to avoid detection. Depending on the victim’s network, attackers establish command and control with varying levels of stealth to circumvent security tools.
- Distributed denial of service: DDoS attacks overwhelm servers or networks by flooding them with internet traffic. Once a botnet is established, an attacker can instruct each bot to send a request to the targeted IP address. This creates a jam of requests for the targeted server.
The result is like traffic clogging a highway – legitimate traffic to the attacked IP address is denied access. This type of attack can be used to take a website down. Learn more about real-world DDoS attacks.
Today’s attackers can customize and replicate malicious C2 code, making it easier to evade detection. This is because of the sophisticated automation tools which are now available, although they are traditionally used by security red teams.
How do you stop attackers from using DNS against you? Read our white paper to learn the steps you can take.
Command and Control FAQs
Attackers use various methods to establish C2 channels, including:
- Embedding malicious code in email attachments or links.
- Exploiting vulnerabilities in software or hardware.
- Using compromised websites to deliver malware.
- Employing social engineering techniques to trick users into executing malicious payloads.
- Leveraging legitimate services and protocols like HTTP/HTTPS, DNS, and social media to evade detection.
Organizations can defend against C2 attacks by implementing robust security measures, including:
- Using advanced threat detection tools to identify and block suspicious activities.
- Employing network segmentation to limit the spread of malware.
- Regularly update and patch systems to close vulnerabilities.
- Conducting continuous monitoring and logging of network traffic.
- Educating employees about phishing and social engineering attacks.
- Utilizing threat intelligence to stay informed about emerging C2 tactics and infrastructure.