-
What Is MITRE ATT&CK Framework?
- MITRE ATT&CK Framework Explained
- Structuring Adversary Behavior by Tactic
- MITRE ATT&CK Tactics and Their Role in Security Intelligence
- MITRE ATT&CK Techniques
- MITRE ATT&CK Use Cases
- Using the MITRE ATT&CK Framework during a Live Attack
- Comparing MITRE ATT&CK and the Cyber Kill Chain
- Advancing Organizational Maturity with ATT&CK
- Toward a Behavioral Framework for Securing AI
- MITRE ATT&CK Framework FAQs
- How Do I Implement MITRE ATT&CK Techniques?
-
What is the MITRE ATT&CK Matrix?
- MITRE ATT&CK Matrix Explained
- Key Components of MITRE ATT&CK: Tactics, Techniques, and Procedures
- Diverse MITRE ATT&CK Matrices: Adapting to Specific Environments
- How Organizations Operationalize MITRE ATT&CK
- Implementing and Maintaining a MITRE ATT&CK Program
- Benefits of Leveraging the MITRE ATT&CK Framework
- Common Challenges and Solutions
- MITRE ATT&CK and the Cybersecurity Landscape
- MITRE ATT&CK Matrix FAQs
-
What Are MITRE ATT&CK Techniques?
- MITRE ATT&CK Techniques Explained
- The Anatomy of a MITRE ATT&CK Technique
- Understanding Common and Emerging ATT&CK Techniques
- Detecting and Mitigating MITRE ATT&CK Techniques
- Leveraging ATT&CK Techniques for Enhanced Security Operations
- The Future Evolution of ATT&CK Techniques
- MITRE ATT&CK Techniques FAQs
-
How Has MITRE ATT&CK Evolved?
- Evolution of MITRE ATT&CK Explained
- The Historical Trajectory of MITRE ATT&CK
- Why TTPs Matter: Shifting the Cybersecurity Paradigm
- Key Milestones in ATT&CK's Expansion and Refinement
- Core Components and Their Evolving Definition
- Why the Evolution Matters: Benefits for Cybersecurity Professionals
- Addressing the Evolving Threat Landscape with ATT&CK
- Operationalizing the Framework: Practical Applications and Challenges
- The Future of MITRE ATT&CK
- Evolution of MITRE ATT&CK FAQs
- What Are MITRE ATT&CK Use Cases?
- A CISO's Guide to MITRE ATT&CK
- How Does MITRE ATT&CK Apply to Different Technologies?
What is the Difference Between MITRE ATT&CK Sub-Techniques and Procedures?
MITRE ATT&CK, a framework for understanding and categorizing cyberthreats, includes both sub-techniques and procedures, each serving a distinct role. While sub-techniques provide a more detailed classification within the broader techniques of the ATT&CK framework, procedures are the real-world instances or methods of how attackers carry out these techniques and sub-techniques. More specifically:
Sub-techniques:
- Are refinements or more specific manifestations of the main techniques listed in the ATT&CK framework
- Provide a more granular view of how a particular technique can be executed
- Allow for a deeper understanding and more precise categorization of attacker behaviors. For example, if the primary technique is "phishing," sub-techniques might include "spear phishing" or "whaling," which are specific types of phishing attacks
Procedures:
- Provide specific methods or steps an adversary uses to execute a technique or sub-technique
- Represent attackers' actual implementation of the techniques in the real world
- Vary widely, even when the underlying technique or sub-technique is the same, as different threat actors might have other tools, skills, or resources.
Understanding the MITRE ATT&CK Framework
The MITRE ATT&CK framework, developed by MITRE Corporation, stands as a cornerstone in the realm of the landscape of cyber threats and adversary tactics, offering a comprehensive and structured approach to understanding the strategies employed by cyber adversaries.
ATT&CK, which stands for Adversarial Tactics, Techniques, and Common Knowledge, is not just a static model - it's a living framework that constantly incorporates evolving methods and behaviors of known adversaries. Initially released in 2013, this framework has become an invaluable tool for security professionals, enabling them to detect and trace potential threats and develop effective defense mechanisms.
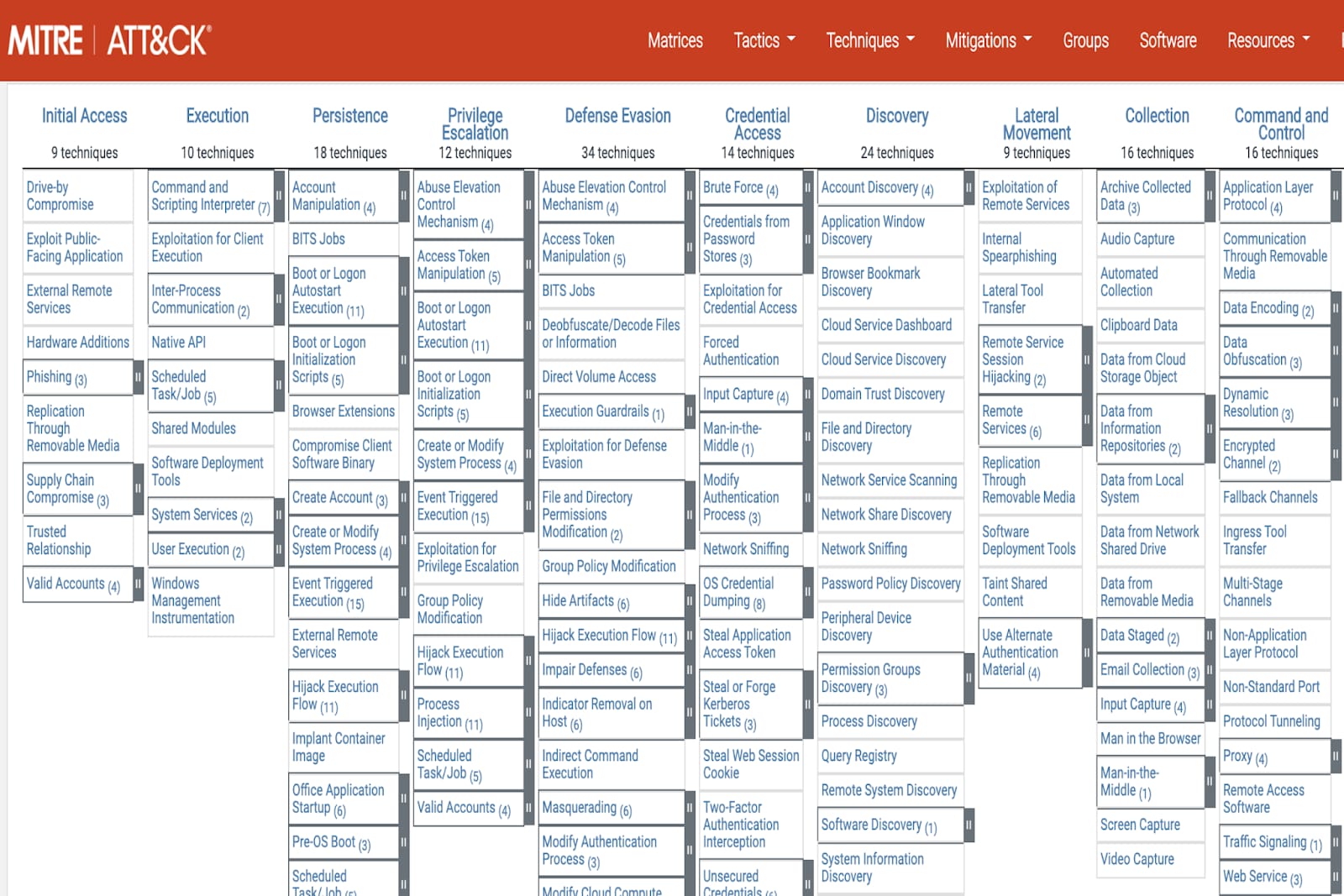
The MITRE ATT&CK framework is a knowledge base of tactics and techniques designed for threat hunters, defenders and red teams to help classify attacks.
Structure of the MITRE ATT&CK Framework
The main components of the MITRE ATT&CK framework are tactics, techniques, and procedures (TTPs). A sub technique delves into more specific methods and offers a more granular view of an adversary's approach, breaking the techniques down into more detailed actions. Understanding the components of the ATT&CK framework is essential for effectively leveraging its insights in cybersecurity defense strategies.
The MITRE ATT&CK framework categorizes techniques into specific tactics. However, in real-world scenarios, certain techniques may span across multiple tactics or be applicable in different stages of an attack. Attackers often use a combination of techniques across various tactics in a fluid and adaptive manner.
The framework serves as a guideline for understanding the relationship between tactics and techniques, but it does not restrict techniques to operate solely within the confines of a single tactic.
H4: Tactics - The Why
Tactics in the ATT&CK framework explain the motivation or the why behind actions taken in an attack, such as an attacker trying to gain 'Credential Access' to penetrate a network further or ‘Exfiltration’ to steal data.
H4: Techniques - The How
Techniques describe the specific methods to achieve these goals (e.g., malvertising, spear phishing, and content injection). Techniques are the strategies employed to realize these tactical goals. Referring to our previous example, the technique used to achieve credential access could be a 'Brute Force Attack.'
These techniques can further be broken down into sub-techniques. In the case of a 'Brute Force Attack,' sub-techniques might include 'Password Guessing' or 'Credential Stuffing,' each representing a different approach to the same end.
H4: Procedures - The Implementation
Procedures bring these elements to life by providing concrete examples of how these tactics, techniques, and sub-techniques are executed in the real world. They often reference specific tools, malware, or threat actor methods observed in actual cyber incidents. Procedures are the actual implementation of the techniques or sub-techniques illustrated through real-world examples of specific threat actor behaviors.
Exploring Sub-Techniques in the ATT&CK Framework
The sub-techniques within the MITRE ATT&CK framework go deeper into how an attacker may execute a broader technique, providing a more precise understanding of cyberthreats and making it easier to identify and respond to them.
Sub-Techniques for Tailored Defense Responses
Sub-techniques break down complex attack techniques into more precise and actionable components, each with unique indicators and mitigation strategies. This subdivision allows for a more nuanced understanding of an attacker's approach, enabling red teams, or defenders, to tailor their responses more accurately. The subtle threat intelligence that a sub-technique reveals about different attacker patterns helps security teams in the following ways:
- Aid in threat modeling, risk assessment, and strategic decision-making
- Anticipate potential threats and allocate resources for defense and mitigation
- Enhance the ability to anticipate, detect, and respond to specific adversary behavior
- Facilitate risk assessments to improve security posture
- Fine-tune detection systems, incident response protocols, and strategic cybersecurity planning
- Gain insights into the sophistication and capabilities of potential threat actors
- Optimize security controls
Consider the 'Spear Phishing' technique under the broader tactic of 'Initial Access'. Within this technique, several sub-techniques could be like 'Spear Phishing via Email' or 'Spear Phishing via Social Media.' Each sub-technique represents a different way the broader spear phishing technique is carried out, helping defenders pinpoint the exact nature of the threat.
Exploring Procedures in the ATT&CK Framework
Procedures in the ATT&CK framework are the tangible, real-world applications of techniques and sub-techniques. They represent the specific ways threat actors put these methods into practice, offering concrete examples that can be analyzed and learned from.
Procedures provide specific actions or steps an attacker takes to execute a technique or sub-technique. Each procedure is typically tied to a particular threat actor or threat group and describes how the technique or sub-technique is implemented.
Procedures provide examples of how theoretical attack vectors are operationalized to help security teams tailor their threat hunting, incident response, and security posture to counteract adversary behavior.
For example, in the context of the 'Credential Dumping' technique, a procedure might detail how a specific piece of malware, such as Mimikatz, is used to extract credentials from a system. This real-world example helps defenders understand the theory behind 'Credential Dumping' and the practical aspects of its execution and, crucially, how it can be detected and mitigated.
The Role of Sub-Techniques in Cybersecurity Strategies
Sub-techniques are subdivisions of broader techniques in the MITRE ATT&CK framework that offer a fine-grained understanding of adversary tactics, crucial for developing targeted defensive measures.
Guiding Defensive Tactics
Breaking down general cyber attack methods into more detailed actions provides a roadmap for cybersecurity teams to anticipate and prepare for more nuanced attack scenarios.
Sub-techniques illuminate the specific paths adversaries might tread within a broader technique. For instance, understanding the sub-techniques under 'Phishing', such as 'Spear Phishing via Email', enables teams to develop specialized defense mechanisms against each variant.
Empowering Cybersecurity Professionals
Cybersecurity experts consider sub-techniques as practical tools and not just theoretical concepts. These sub-techniques allow professionals to accurately predict and prevent attacks by analyzing the attacker's playbook. Sub-techniques are invaluable in building a proactive cybersecurity program by providing deep insight into the adversary's behavior.
Procedures as a Tool for Detailed Threat Analysis
Where sub-techniques offer a detailed breakdown of attack methods and procedures to ground this knowledge in the reality of actual cyber incidents, they are concrete examples that illustrate how theoretical concepts manifest in the real world of cyber warfare.
In-Depth Understanding of Attacker Methods
Procedures are similar to case studies focusing on specific cyberattack instances. They provide a detailed account of how a particular technique or sub-technique was used in a real attack scenario, including the tools, scripts, and sequences employed by attackers. This level of detail is essential for security analysts to analyze and comprehend the complexities of an attack.
Tailoring Cybersecurity Responses
The practical insights derived from procedures enable security teams to tailor their responses with a level of specificity that generic strategies cannot offer.
Whether adjusting detection systems to recognize particular malware signatures or modifying incident response plans to address specific attack sequences, the knowledge from procedures ensures that defensive measures are as targeted and effective as possible.
Practical Application and Analysis
The practical application of sub-techniques and procedures in cybersecurity is vividly illustrated through real-world case studies. These examples highlight how the theoretical elements of the MITRE ATT&CK framework are operationalized in threat detection and response.
Leveraging ATT&CK for Organizational Benefit
Beyond specific threat responses, organizations can integrate the insights from sub-techniques and procedures into broader security strategies. This includes tailoring training programs to address the most relevant threats and adjusting security architectures to preempt the tactics and techniques most likely to be used against them.
Continuous Evolution: Staying Updated with ATT&CK Framework
The MITRE ATT&CK framework constantly evolves to reflect the changing cyberthreat landscape. It's essential to keep up with revisions and additions to maintain an effective cybersecurity strategy.
Keeping Pace with the Dynamic Nature of Cyberthreats
As new techniques and sub-techniques emerge, the ATT&CK framework expands to include these developments. This dynamic nature ensures the framework remains a relevant and valuable resource for cybersecurity professionals.
Best Practices for Staying Informed
To stay abreast of updates to the ATT&CK framework, cybersecurity teams should:
- Regularly visit the MITRE ATT&CK website and subscribe to update notifications.
- Participate in cybersecurity forums and communities that discuss the latest trends and insights related to the ATT&CK framework.
- Attend webinars, workshops, and conferences on the latest developments in cyber threat intelligence and the ATT&CK framework.
Integrating Updates into Practice
When updates are released, teams should assess how these changes might impact their security posture. This could involve updating threat models, revising incident response plans, or reconfiguring security tools to align with the latest insights from the framework.