What Is DNS?
Learn what DNS is, why it’s essential to internet functionality, and how it impacts your online experience, from browsing websites to network security.
Each device connected to the internet has an IP address. The domain name system, or DNS, is a protocol that translates a user-friendly domain name, such as www.paloaltonetworks.com, to an IP address – in this case, 199.167.52.137. DNS is ubiquitous across the internet. Without it, we’d have to memorize random strings of numbers, which our brains aren’t equipped to do very well.
Related Video
How Attackers Use DNS to Steal Your Data
How DNS Works
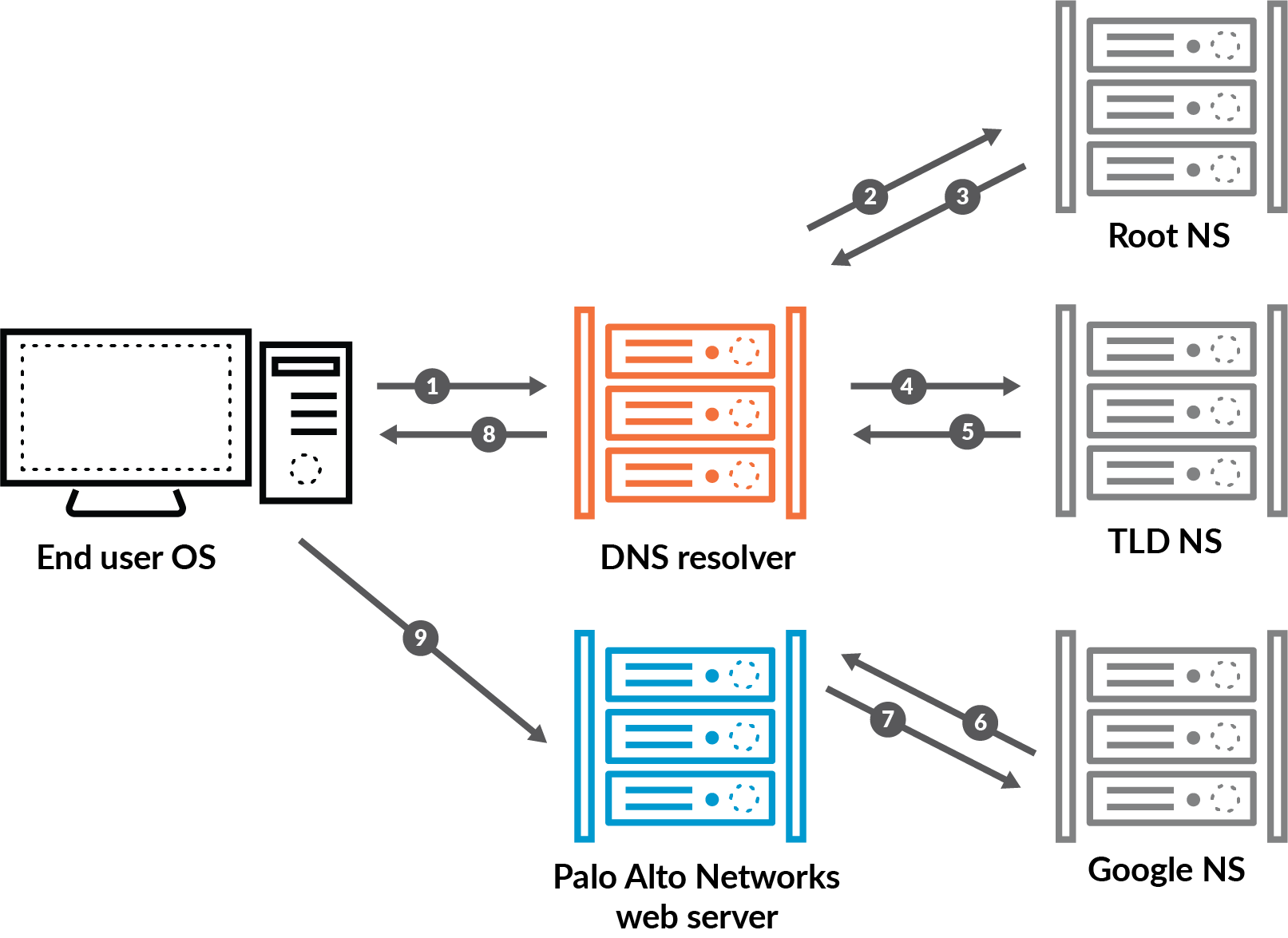
To explain this, let’s look at five steps in a DNS lookup.
- You, the user, initiate a query by typing www.paloaltonetworks.com into your browser. The query is sent to a DNS resolver, a computer usually provided by an IP provider. It is the DNS resolver’s job is to track down the IP address.
- The resolver queries one of the root servers. Root servers are distributed around the world and hold the locations of all top-level domains – TLDs – such as .com, .edu, and .net. The root server sends a response back to the resolver.
- The resolver can now notify the TLD server. The TLD server doesn’t hold the IP address you’re looking for, but it knows the locations of the name servers for Palo Alto Networks.
- The DNS resolver queries one of the name servers. This time, the server knows the IP address and responds with an address record.
- In the last step, the DNS resolver sends the IP address – 199.167.52.137 – back to your computer, and the website loads in your browser.
All this happens in the background in mere milliseconds. Sites like google.com or paloaltonetworks.com may have multiple IP addresses, which can speed up DNS lookup times. There may be millions of people looking for the same information at the same time, even from different countries around the world, and these queries will likely go to different servers, distributed worldwide.
DNS information is also cached on your computer and on the servers used by your internet service provider. Once the IP address for paloaltonetworks.com is saved, your computer no longer needs to access a DNS resolver to resolve the name with its IP address.
Why You Need to Know About DNS
- DNS is the backbone of the internet. It helps us reach the correct sites.
- DNS mechanisms are used to identify who is allowed to send email on behalf of a domain so email from impostors doesn’t reach you.
- DNS resolvers are attacked regularly.
Take this example from Palo Alto Networks Unit 42®. On January 22, 2019, the U.S. Department of Homeland Security published an emergency directive requiring federal agencies to comply with a number of steps as a response to a series of recent DNS hijacking attacks from a foreign country. The purpose of these attacks was to redirect traffic meant for companies’ and agencies’ email servers toward malicious clones operated by the hackers.
How do you stop attackers from using DNS against you? Read this white paper to learn the steps you can take to stop DNS attacks.