What Is Firewall Configuration? | How to Configure a Firewall
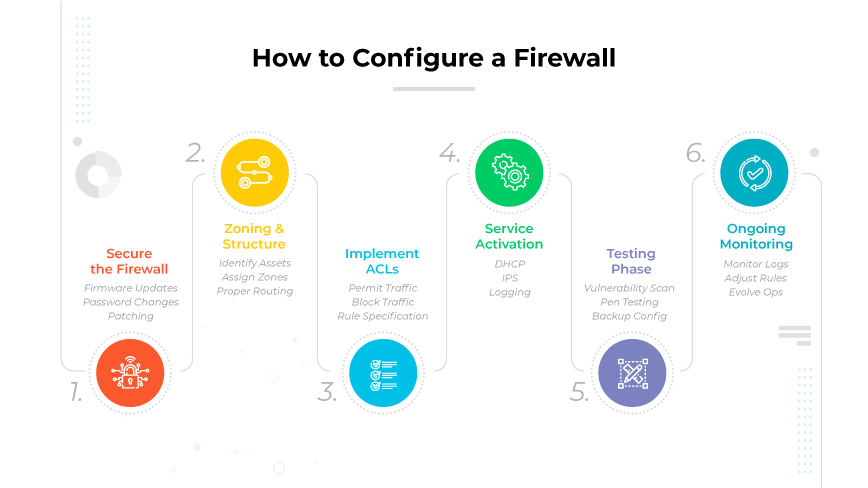
Firewall configuration is the process of setting specific rules and policies that govern how a firewall monitors and controls incoming and outbound traffic. Firewall configuration steps include:
- Secure firewall
- Zoning and structure
- Implement ACLs
- Service activation
- Testing
- Monitoring
This process determines which data packets can pass through, ensuring the firewall blocks unauthorized access and permits legitimate traffic.
Why Is Proper Firewall Configuration Important?
Effective firewall configuration is important because it protects network integrity by specifying detailed criteria based on IP addresses, domain names, protocols, and port numbers. Configuration requires regular updates and adjustments to adapt to evolving security threats and maintain a robust defense.
Proper firewall configuration is fundamental to network security. It establishes the rules and boundaries that determine which traffic can enter and leave the internal network. A correctly configured firewall can efficiently differentiate between safe and potentially harmful traffic. Proper configuration enables the passage of legitimate data while blocking unauthorized attempts to access the system.
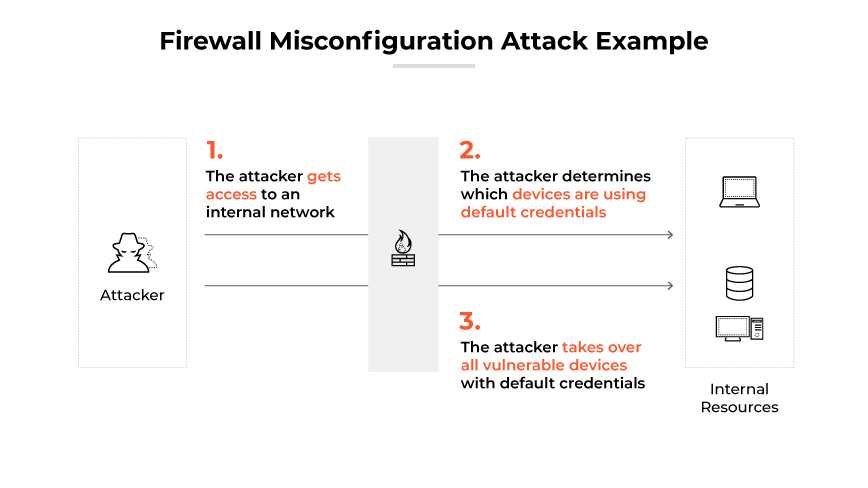
Misconfigured firewalls may inadvertently allow threats to pass through, leaving networks vulnerable to attacks. Many network breaches are due to configuration errors rather than the inherent vulnerability of the firewall itself.
It is crucial to tailor firewall settings to the specific requirements of each network. This involves regularly updating rules, closing unnecessary ports, and applying patches to address security loopholes. An optimal configuration minimizes the risk of breaches and maximizes network performance, ensuring both security and efficiency for users and administrators.
How to Configure a Firewall
Firewall configuration steps will vary based on the type of firewall (hardware firewalls or software firewalls), operating system (OS), and vendor. The general instructions provided here offer a broad framework for the setup process but should not replace the guidance recommended by the vendor. Always refer to manufacturer specific documentation for exact instructions.
Secure the Firewall
Start with foundational security by updating the firewall to the latest firmware to patch known vulnerabilities. Immediately change default credentials to strong, unique passwords, and disable any unnecessary user accounts. Restrict administrative access by IP, and if possible, set up multi factor authentication to add an additional layer of security.
Design Firewall Zones and IP Address Structure
Develop a network segmentation strategy by categorizing all network assets. For example(s), email servers, virtual private network (VPN) servers, and web servers. Create distinct zones such as a demilitarized zone (DMZ) for public facing services, and secure areas for sensitive data. Allocate unique IP ranges for each zone and apply them to the firewall interfaces. This step is critical to prevent unauthorized access and contain potential breaches.
Implement Access Control Lists (ACLs)
For each zone, define ACLs that precisely allow or deny traffic based on source and destination IP addresses and ports. Start with the most restrictive rules and ensure the final rule is a default deny for all undefined traffic. Regularly review and update ACLs to reflect changes in the network architecture and threat landscape.
Activate Additional Services and Logging
Enable only necessary services such as virtual private networks (VPNs), DHCP, or IPS. Deactivate any service not in use to minimize the attack surface. Configure comprehensive logging for all traffic and events. Ensure security personnel send logs to a secure and centralized logging server for analysis and compliance purposes.
Test the Configuration
After the initial setup, conduct thorough testing of the firewall configuration using penetration testing tools and vulnerability scanners. This is to verify that all rules apply correctly and that no unauthorized traffic gets through. Keep a verified backup of the working configuration to restore the system if needed.
Ongoing Monitoring and Management
Implement a robust firewall management and monitoring system for continuous observation of the firewall's performance and security logs. Adjust rules in response to new threats and operational requirements. Maintain a clear change management document for every configuration change. Employ predictive analysis tools where available to proactively address potential issues.
Common Firewall Configuration Mistakes
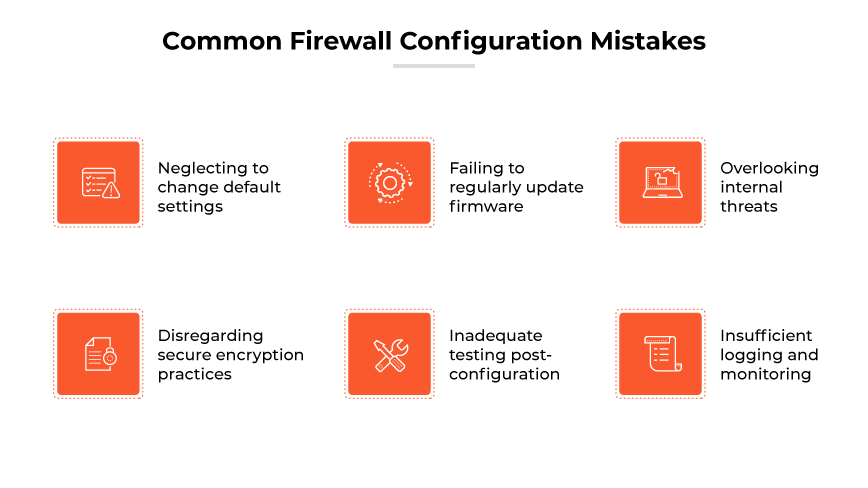
Alt text: FW configuration mistakes: default settings, outdated firmware, internal threats, discounting encryption, inadequate testing & logging
Even with a strong security posture in place, firewall misconfigurations can introduce substantial risks. Firewall misconfigurations can create openings in network defenses, exposing sensitive and critical systems to unauthorized access. Just misconfigured rule can open an inadvertent pathway for malicious actors to infiltrate the network.
Neglecting to Change Default Settings
One common oversight in firewall configuration is not changing the default settings. Firewalls often come with publicly known manufacturer defaults, making them vulnerable. Ensure all defaults, including passwords, usernames, and IP addresses, are custom to prevent unauthorized access.
Failing to Regularly Update Firmware
Failing to update firewall firmware can leave a network exposed to exploits targeting old vulnerabilities. Set a schedule to check for updates regularly and apply them promptly. This maintains the firewall's effectiveness against emerging security threats.
Overlooking Internal Threats
Internal threats are often overlooked. Ensure firewall configurations include measures to monitor and control internal traffic. Security rules should be in place to limit user access to necessary resources only, reducing the risk of internal data breaches.
Disregarding Secure Encryption Practices
Secure encryption is vital in protecting data that passes through a firewall. Weak encryption on VPNs and other channels can be a significant flaw. Use strong, up-to-date encryption standards to protect data integrity and confidentiality.
Inadequate Testing Post-Configuration
A firewall configuration is not complete without thorough testing. Skipping this step can result in undetected vulnerabilities. Perform penetration testing and system checks to validate that each rule functions as intended, and the firewall effectively protects the network.
Insufficient Logging and Monitoring
Another common mistake is not enabling or configuring adequate logging and monitoring. Without logs, detecting breaches or unauthorized access attempts becomes challenging. Set up comprehensive logging and establish monitoring protocols to observe network traffic and flag anomalies.