Infrastructure as code scanning
Infrastructure as code presents an opportunity to secure cloud infrastructure in code before it’s ever deployed to production. Prisma Cloud streamlines security throughout the software development lifecycle using automation and by embedding security into workflows in DevOps tooling for Terraform, CloudFormation, Kubernetes, Dockerfile, Serverless and ARM templates.
Automate cloud security scanning in code
Add automated checks for misconfigurations and exposed secrets at every step of the software development lifecycle.
Leverage the power of open source and the community
Checkov, the leading open source policy-as-code tool powering Prisma Cloud Infrastructure as Code Security, is backed by an active community and has been downloaded millions of times.
Embed code security feedback directly in developer tools
Prisma Cloud comes with native integrations for IDEs, VCS, and CI/CD tooling to help developers ship secure code in their existing workflows.
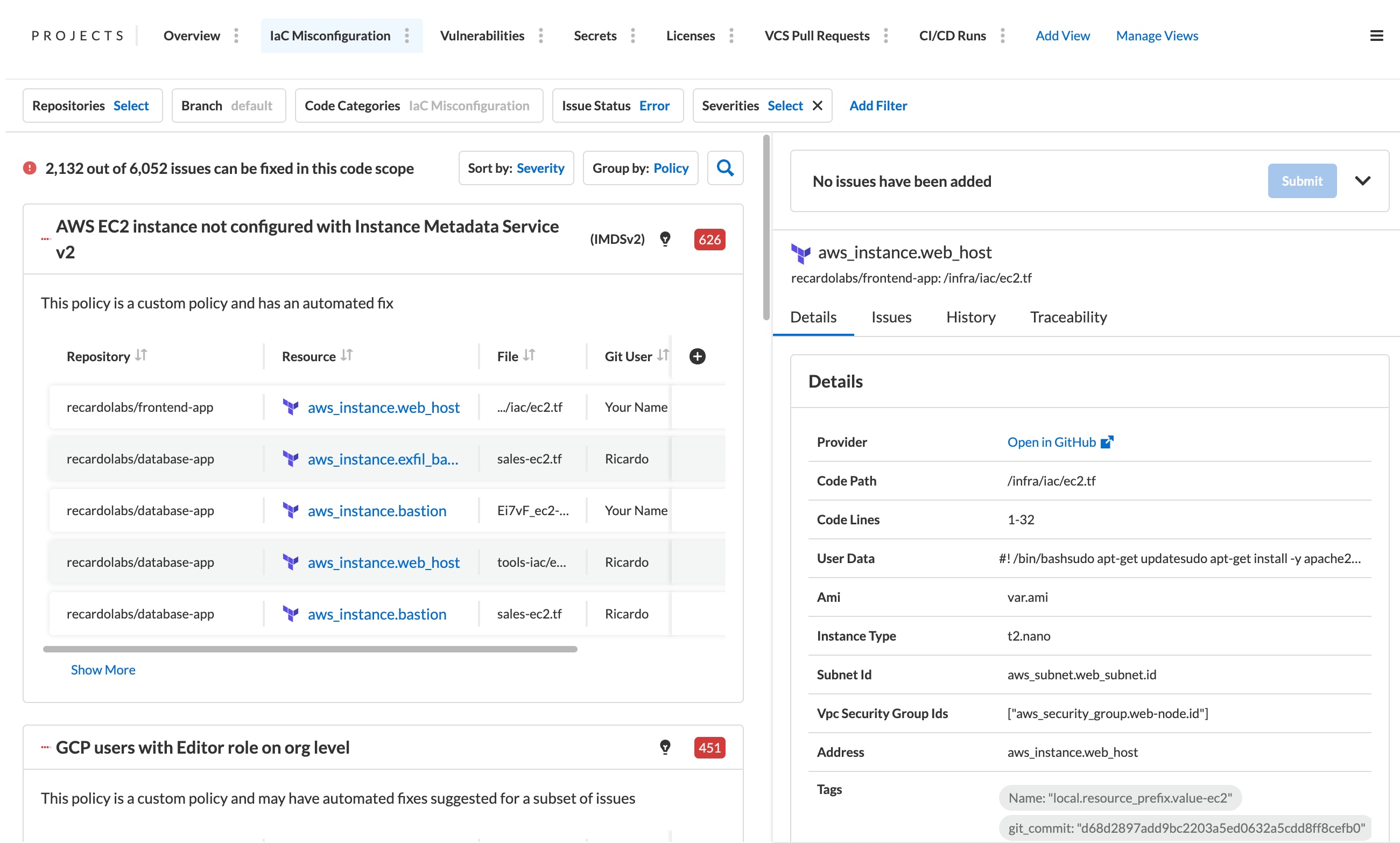
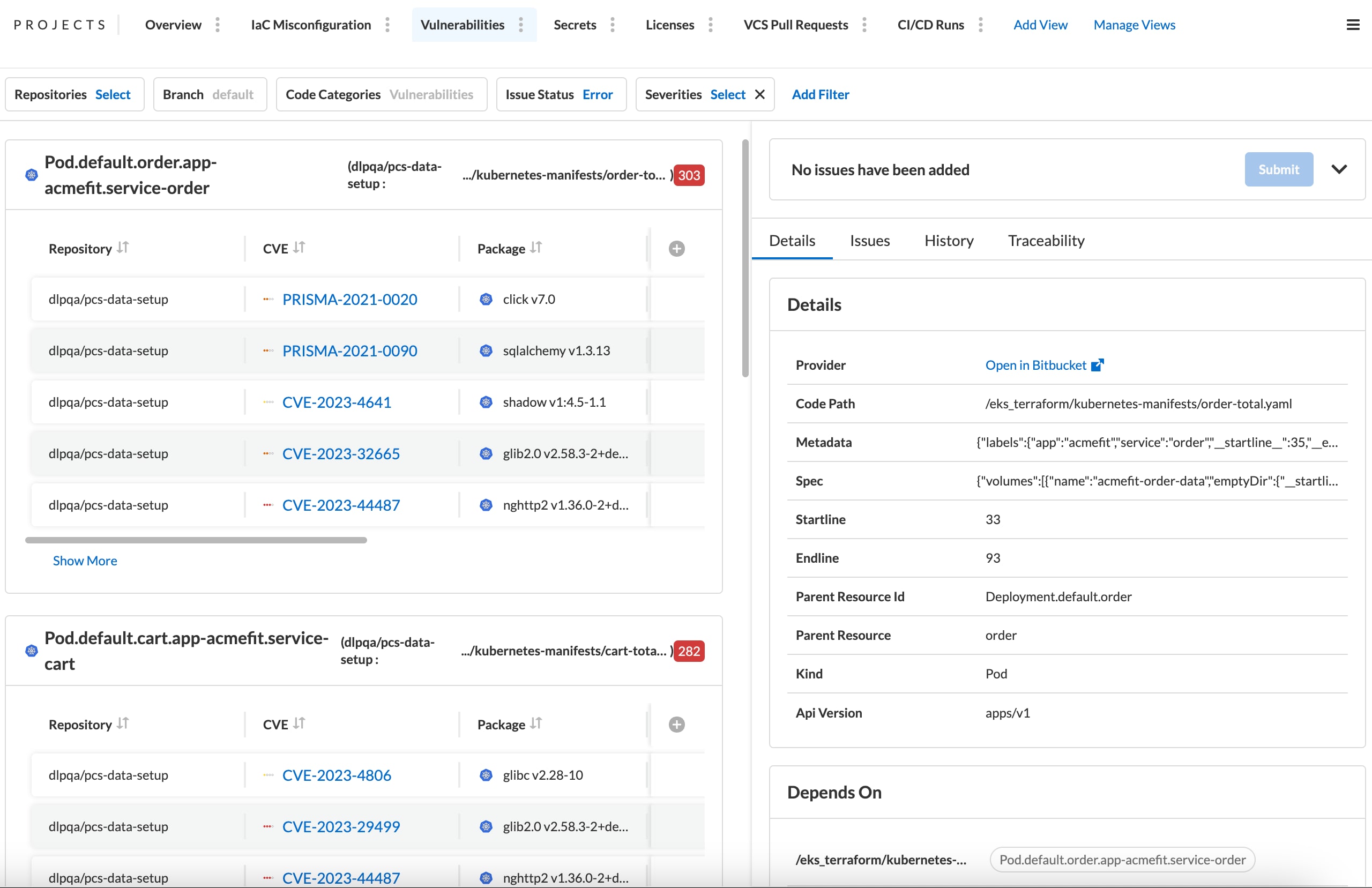
Include deep context for misconfigurations
Prisma Cloud automatically tracks dependencies for IaC resources as well as the most recent developer modifiers to improve collaboration in large teams.
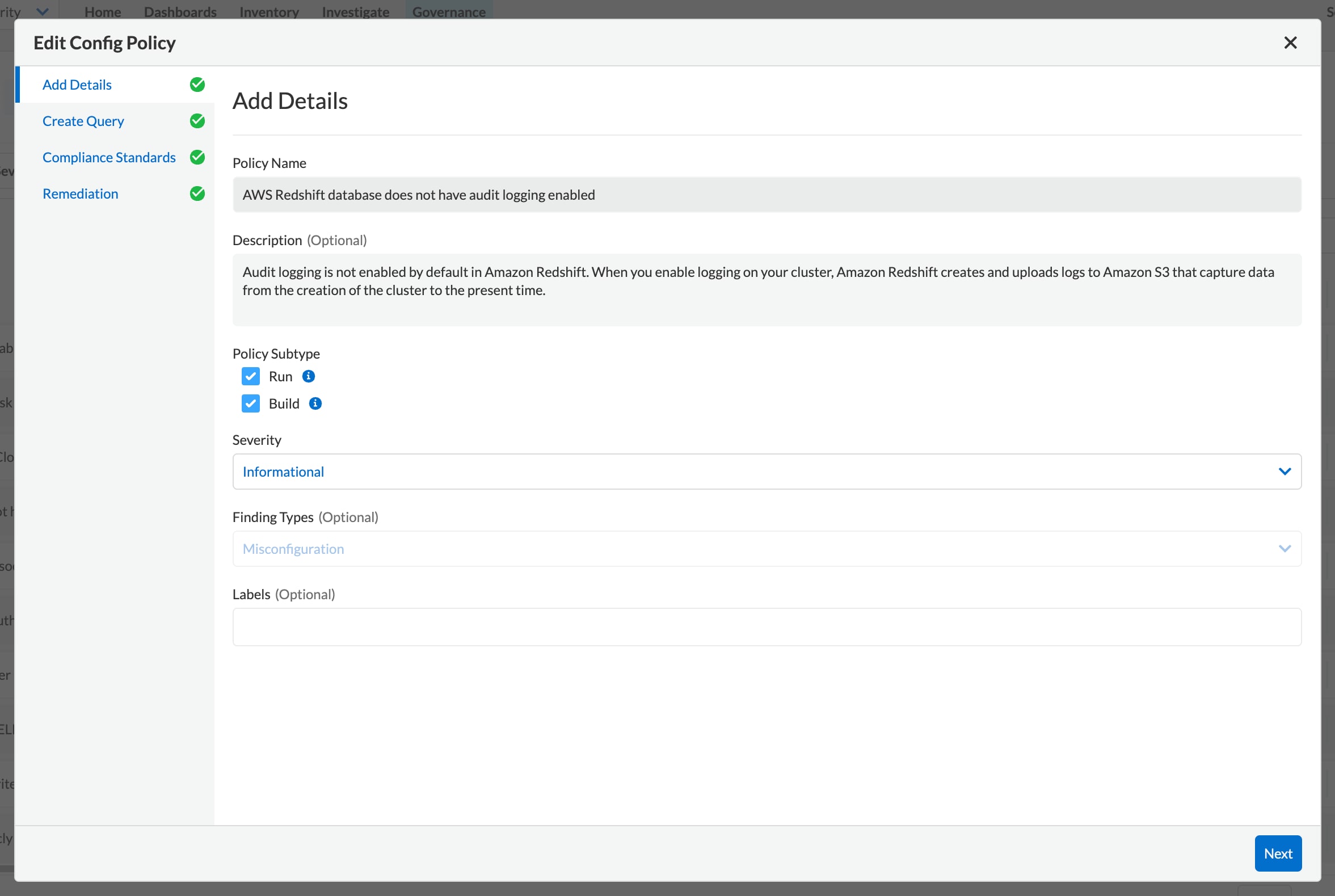
Provide automated feedback and fixes in code
Automate pull request comments for misconfigurations along with automated pull requests and commit fixes and Smart Fixes for identified misconfigurations.