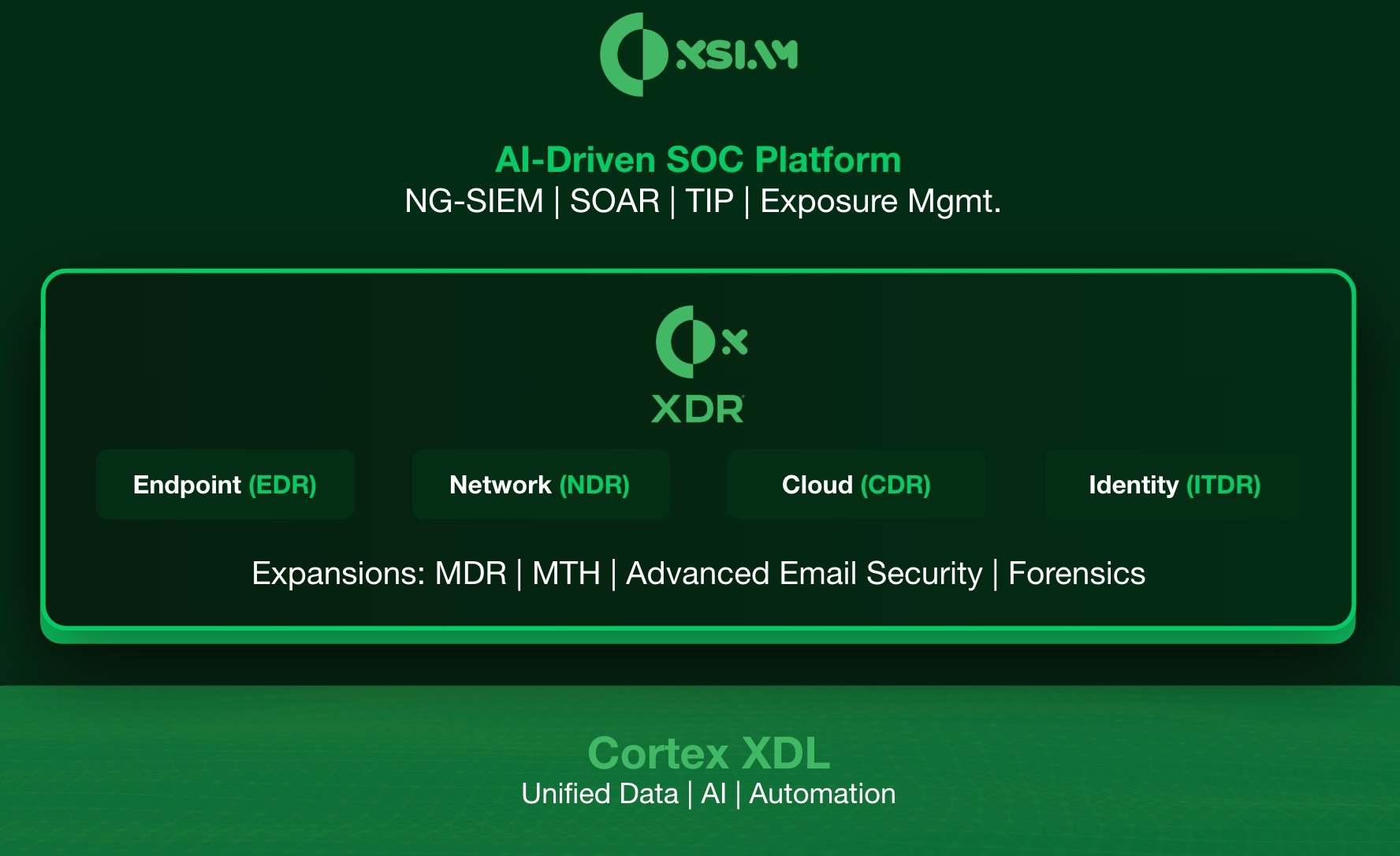
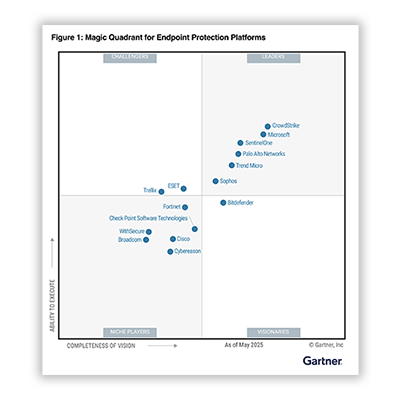
Detect More Attacks in Real Time with AI
Endpoints are the #1 target, but 84% of attacks span multiple vectors. Cortex XDR® connects data from endpoint, cloud, network and identity sources and applies AI to detect and prioritize cyberattacks, no matter where they come from.