Accelerate time-to-market securely with Azure Linux for AKS
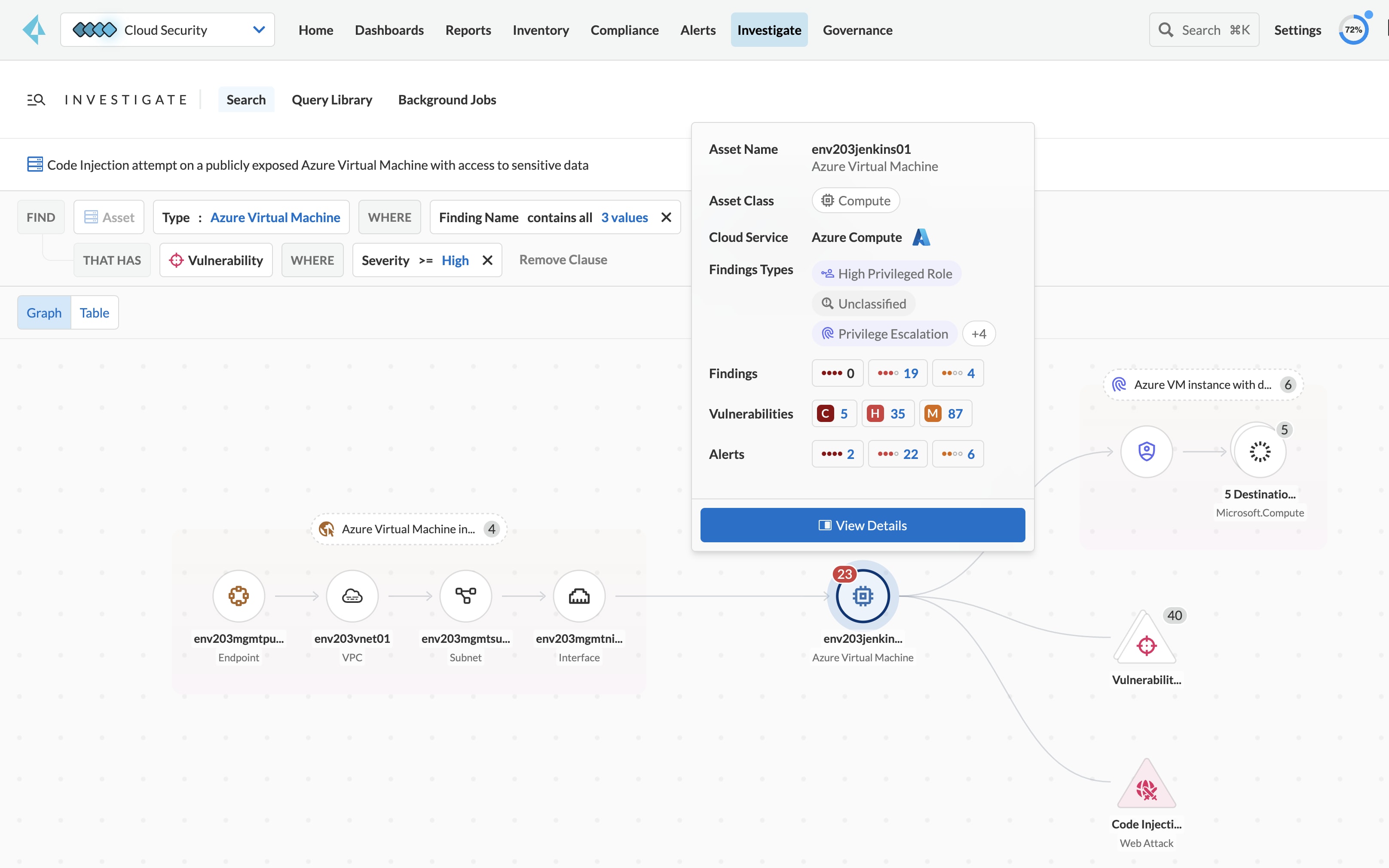
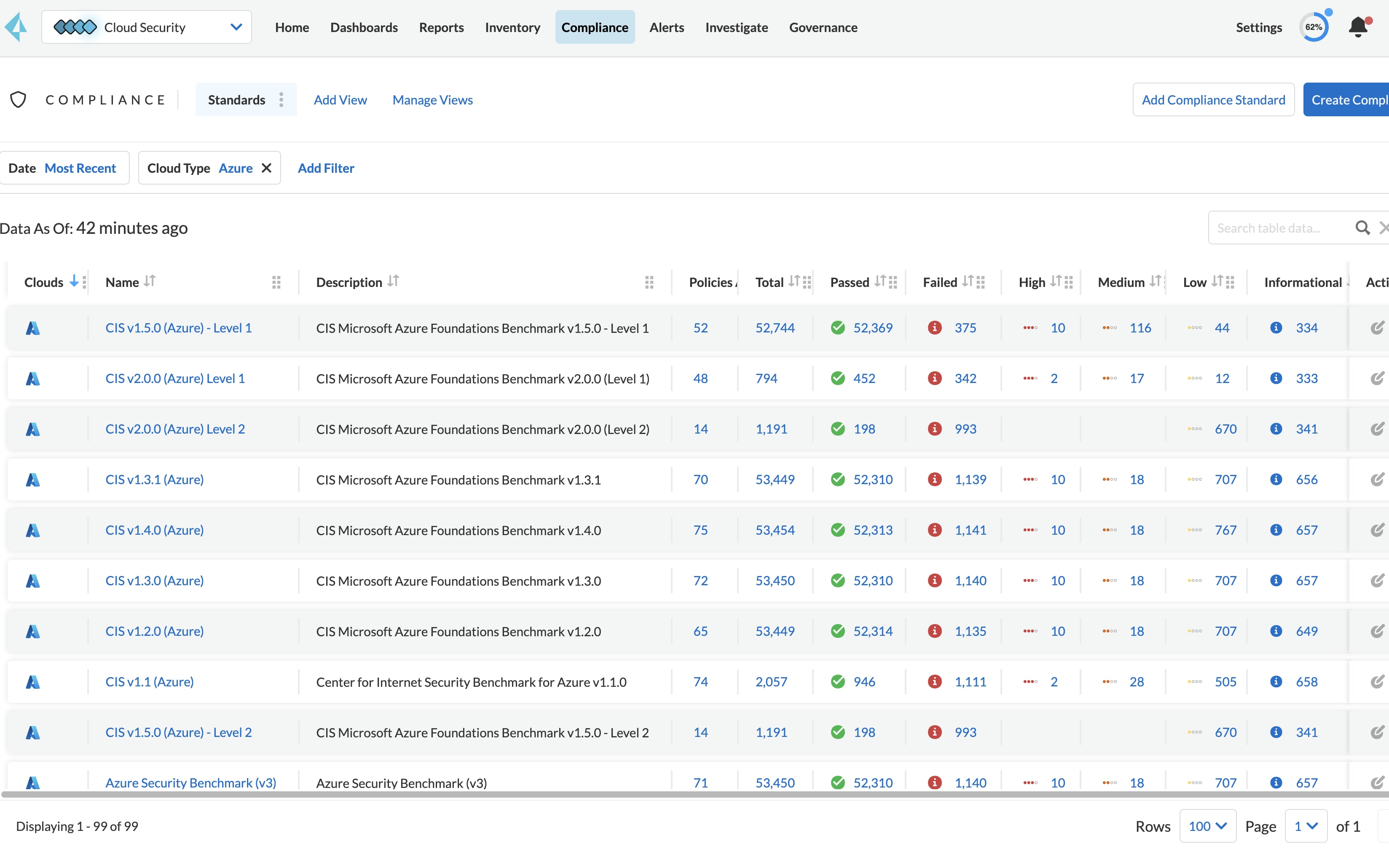
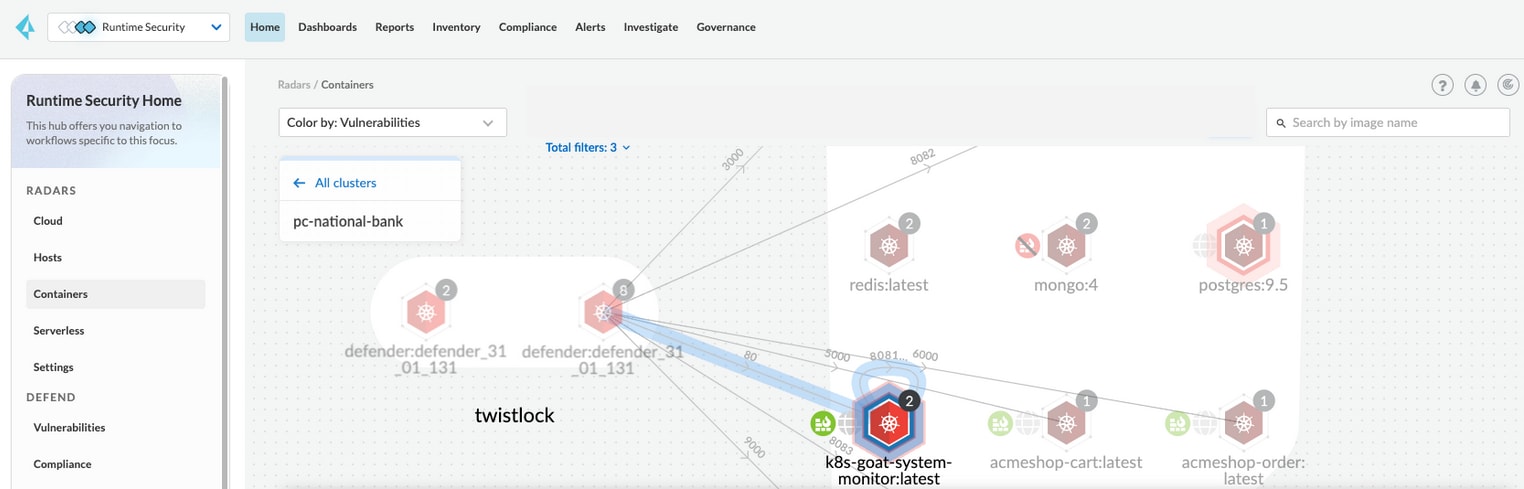
Prisma Cloud supports simplified and enhanced Kubernetes container security with the Azure Linux container-optimized host operating system for Azure Kubernetes Service (AKS). Simplify and accelerate your container workload security on Microsoft Azure with Prisma Cloud.