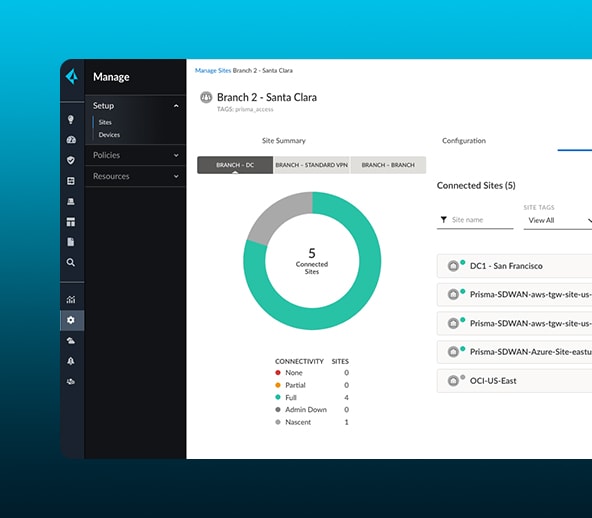
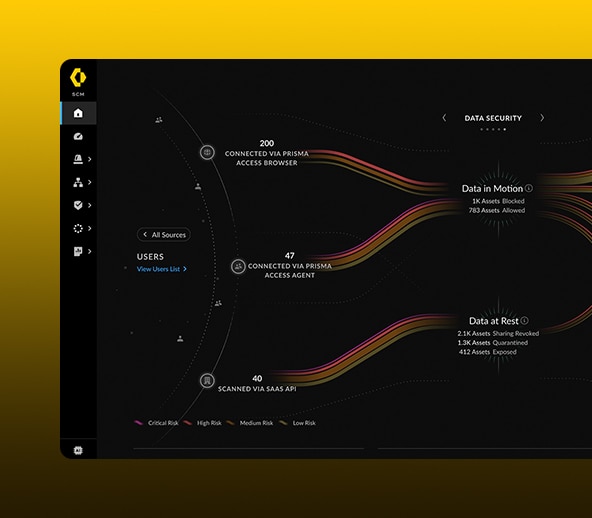
Achieve True Zero Trust Security for Your Entire Network
Ensure secure, least-privileged access to all applications, eliminate implicit trust and reduce your attacks surface without the complexity of traditional VPNs.
Prevention starts with blocking inline attacks every day.
Avoid outages with the industry’s most resilient backbone.
Faster app performance than direct-to-web with native app acceleration.
Ensure data and apps are protected from all threats and risks.
New Zero-Day threats prevented everyday
security processing SLA
SaaS performance SLA
people secured
days
downtime
users enabled to work remotely
reduction in number of vendors
increase in visibility into security blind spots
reduction in disparate tools
High-priority incidents
for generation of compliance reports reduced
Eliminate complexity with the industry’s first Zero Trust management and operations solution.