Last week, we announced our first Modern Malware Review, where Wade Williamson and other Palo Alto Networks experts had the opportunity to analyze 3 months of data from WildFire, including data from more than 1,000 real networks and more than 26,000 seemingly unique samples of malware collected in real enterprise networks (out of 60k+ that evaded AV solutions on customer networks). You can find the full report here.
We’ve gathered some interesting quotes from media coverage of the review below. Also, Wade speaks with Threatpost’s Dennis Fisher about the MMR and some of the particularly compelling (dare I say alarming) findings in this podcast – give it a listen here.
"If you talk to most enterprise IT guys, they're not spending much time worrying about FTP because it's seen as a dusty old protocol. Some of these older protocols that are flexible and still work are being used by attackers because nobody is going to blink if they see it." – Wade Williamson (CRN, March 25, 2013)
“Most network managers don’t give a second thought to FTP, but it’s pretty obvious that attackers are thinking about it…a lot,” – Wade Williamson (Security Bistro, March 27, 2013)
Can you sense the theme? FTP was observed to be exceptionally high-risk. FTP had the ignominious distinction of being both a common source of unknown malware as well as one of the sources that rarely received coverage. FTP was the most evasive application in terms of port evasion, and had one of the lowest detection rates in terms of malware.
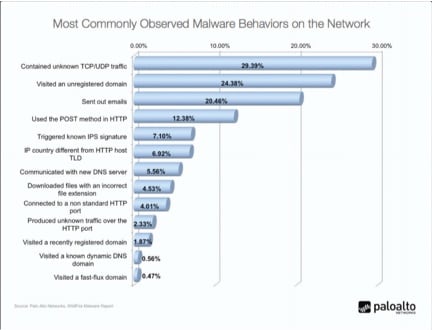
For more details on getting a handle on the scale of modern malware check out Wade’s guest post on Security Week here. Let us know what you think of the Modern Malware Review in the comments below.