What Our Cyvera and Morta Acquisitions Mean For Palo Alto Networks and You
Thanks to the technologies we are acquiring with Cyvera and already acquired with Morta Security, the Palo Alto Networks platform will become the first commercial system to provide network defenders the ability to set policy for detection and blocking all the way down the Kill Chain, including the host, and laterally across the network using one simple interface.
What’s more, we’re doing this at a fraction of the cost to deploy equivalent point products from a conga line of security vendors that is the norm for today’s cyber security solutions.
Let me share some details of what this means to you.
Introduction
When I began interviewing for the Palo Alto Networks Chief Security Officer position last fall, I made my way around to all the senior leaders in the company. The question I got that was consistent amongst all leaders was whether Palo Alto Networks should be on the desktop. They had been thinking about the proposition for a long time and were ready to make a decision one way or the other. I could not believe my good fortune to get involved with a company like ours at this unique time in cybersecurity history.
Disruptive Change Is Coming
For the past few years I have been advocating the need for the cybersecurity community to change its paradigm regarding how to defend the enterprise. The old perimeter defense concept is a dead idea and the model of tactical signatures deployed on point-based products across multiple vendors has never worked as advertised.
Advanced organizations like the Defense Industrial Base (DIB) and the Financial Sector Information Sharing and Analysis Center (FS-ISAC) have moved away from that model with great success and moved toward a Kill Chain Model of defense by developing sets of Indicators of Compromise for the various adversaries that attack their member companies.
These organizations have learned that the tactical discovery and potential blocking of an adversary’s actions without any context regarding the ultimate objective and the campaign plan designed to achieve that objective is at best, inefficient, and at worst, an utter failure. Therefore, they are learning a more strategic approach. They have figured out how to determine an adversary’s campaign plan by developing sets of Indicators of Compromise across the Kill Chain down-to and including the host, sharing them with its member organizations and looking for multiple signs of activity across the attack surface.
One of the reasons the DIB and the FS-ISAC have been successful is that many of the member organizations have dedicated significant resources to this effort. They have thrown money and people at the problem and have been able to harness the massive amounts of raw information generated by dozens of different technologies built by, as my Senior Vice President of Worldwide Field Operations, Mark Anderson, likes to say, a conga line of vendors deployed across their enterprises. That is the good news. The bad news is that despite their expertise and success, the overall process is still too hard, still relies on the well-resourced organization to put all of the pieces together, and still has nothing to say for those organizations that do not have the kind of budget or advanced expertise.
A Shift In Thinking
Our cybersecurity community has passively accepted the notion that using multiple point products that may or may not integrate with each other is the solution that everyone needs to defend the enterprise. As we see it, that could not be further from the truth. The best way to understand the Kill Chain model is that it is a system. Therefore, the defense of it needs to be managed like a system.
One of the reasons that I wanted to come to work for Palo Alto Networks is that, out of all the vendors in the cybersecurity community space, we are the only one that offers a true system solution at a reasonable price. Our next-generation enterprise security platform provides visibility at all layers of the Kill Chain, does it with one in-line box designed from the ground up to make defensive decisions with one pass of the data, and does it at a fraction of the cost that it would take to deploy and manage an equivalent set of point products.
In my previous job as the CISO to a DIB company, I had lots of point products deployed. It was expensive and complex and I always had the feeling in the back of my brain that such complexity was harming us, not least because it gave the adversary lots of places to hide. The Palo Alto Networks solution reduces that complexity. I was ecstatic that I could work for an organization that “got it.”
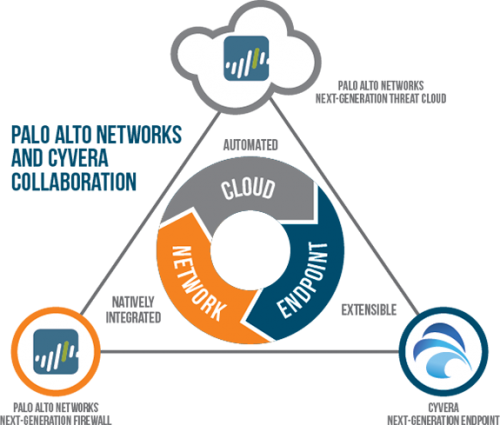
Now comes our next step, and I invite you to learn more about what we’ve acquired with Cyvera and Morta. Up until now, we've had to infer host adversary activity. In other words, we had no direct contact with the host. With our WildFire service -- the copying of all documents coming through the Palo Alto Networks platform to a sandbox in the cloud or on the customer’s premise to discover stage-1 and stage-2 delivery of malicious and executable code – our platform could infer what the malicious code would do once installed on the host. But it could not watch directly what the malicious code actually did on the host.
The Cyvera acquisition changes that equation. As we integrate the Cyvera technology into the Palo Alto Networks platform, we will no longer just infer malicious host activity -- we will be watching it directly. Combine that with technology we acquired through Morta -- simply put, the ability to detect lateral movement in a compromised network – and the Palo Alto Networks platform becomes the most innovative and disruptive commercial cybersecurity solution designed specifically for threat prevention, not just detection, since the idea of a firewall started to emerge back in the early 1990s.
Conclusion
It is an exciting time in our cybersecurity community, in our industry, and especially at Palo Alto Networks. I can’t tell you how good it feels to belong to an organization that is on the leading edge of deploying these disruptive ideas to the marketplace -- ideas that have been percolating around our best advanced thinkers (organizations like DIB and the FS-ISAC) for the past 10 years.
Good things are coming and I can hardly wait to share more. Leave a comment or send me a note at rhoward@paloaltonetworks.com to let me know what you think. And for more on today's Cyvera acquisition announcement, please head to our resource page.
Related Blogs
Subscribe to the Blog!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.