“The Dark Arts,” said Snape, “are many, varied, ever-changing, and eternal. Fighting them is like fighting a many-headed monster, which, each time a neck is severed, sprouts a head even fiercer and cleverer than before. You are fighting that which is unfixed, mutating, indestructible.” – J.K Rowling, Harry Potter and the Half Blood Prince
It’s ironic that these words written in 2005 accurately describe our cyberthreat landscape today. Typically, the change initiators are threat actors that use new attack patterns to target weak spots that the defenders are not yet aware of. While the defenders gradually become aware and learn to respond to the newly introduced pattern, attackers have already moved on to find new ways to attack.
What defenders need is a security platform that goes deeper than the surface of the latest attack vector. While individual attacks appear to be different from each other, they originate from and rely on certain core foundations. By discovering and targeting these foundations, a security platform can counter advanced threats in general, not just specific attacks. In this post we will illustrate how Traps, as part of Palo Alto Networks next-generation security platform, can protect from the recently disclosed 'BadWinmail' vulnerability, CVE-2015-6172.
Interaction Not Needed
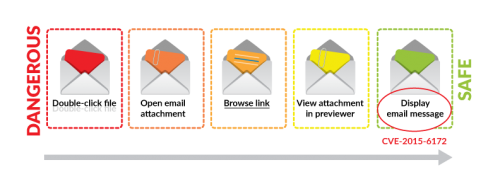
CVE-2015-6172 is a vulnerability in Microsoft Outlook that was recently disclosed by security researcher Haifei Li and patched by Microsoft on December 8, 2015. This vulnerability enables an attacker to run exploits on a user who merely displays a received email. It isn’t even necessary for the user to double-click on attachments, open links, or preview a document to become vulnerable. A user’s machine can be fully compromised just by displaying an Outlook email message. To fully recognize the significance of CVE-2015-6172 from the attackers’ perspective, we need to first understand the underlying attacker-defender dynamics.
Perception Is Everything
This vulnerability is an important breakthrough from the threat actors' perspective because it targets an action that users currently perceive as safe.
Threat actors develop their attacks to align with and leverage users' perceptions of risk in their daily activities. From the attackers’ perspective, the safer a user perceives an activity to be, the better that activity can serve as an attack vector. Therefore, exploiting a vulnerability in Adobe Reader is better than embedding a malicious executable in an email because a typical user will be more likely to open an attached PDF than to double-click an unknown executable.
Software vendors implement security mitigations in software based on what they perceive as vulnerable. In the case of Outlook, if an email contains direct code execution, then it will automatically be blocked; if the message contains a link or an attachment, then a warning dialog box will open to notify the user of the potential risk.
In addition, all Microsoft Office documents, whether previewed or double-clicked, are directed to the Office sandbox, which provides users with relatively high levels of protection from Office-based threats delivered through Outlook. This security measure is implemented because attackers might exploit vulnerabilities either in the Office document itself or in embedded objects an Office document might contain, such as an Adobe Flash object. Since Flash is considered a top exploitation target, we will use it to explain the implications of CVE-2015-6172.
A Flash-y Example
Software vendors acknowledge Flash's exploitability and respond by making sure it can only run in a sandbox environment, as is the case with Google Chrome, IE11 and Microsoft Edge.
Flash can also be embedded in Office documents. Therefore, Office documents carrying Flash objects are opened in the Office sandbox. This ensures that, even if a document contains an exploit of a Flash vulnerability, the exploitation will be contained in the sandbox and not compromise the endpoint on which it is opened.
This illustrates the importance of threat perception. Microsoft perceives Flash as an exploitable application and Office as an exploitable carrier. Therefore, Microsoft implements a security mechanism to mitigate the potential risk of malicious Flash objects carried by an Office document.
But in this case, the potential risk is the Outlook application itself. BadWinmail embeds the exploitable Flash objects in the actual email message, not the attached Office document! Outlook will open such an object directly, and Microsoft does not redirect Outlook to the sandbox since it does not perceive Outlook as a potential carrier of exploitable objects.
So in the example of an embedded Flash object, the exploit that is otherwise mitigated by the sandbox when the object is embedded in an Office document is now fully deployed when embedded in the email message itself, resulting in a full compromise of the Outlook application and, consequently, the endpoint it runs on.
The Compromise-Respond Cycle
CVE-2015-6172 is a fair illustration of the pattern that we described above. First, attackers target an action that users perceive as safe. Software vendors respond by addressing the specific implementations of the attack. Then, attackers shift to target a new component that is not subject to the software vendor's mitigation efforts because it is perceived to be secure. As the illustration below shows, compromised targets are an inseparable part of this cycle.
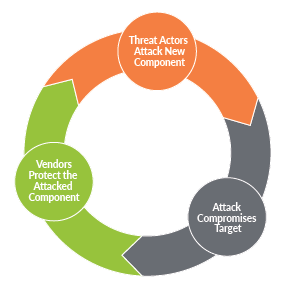
What makes CVE-2015-6172 unique is that it enables an attacker to successfully exploit vulnerabilities that are otherwise un-exploitable due to Microsoft Office mitigation provisions.
Breaking Out of the Cycle
Palo Alto Networks Traps enables the defender to break out of the Compromise-Respond Cycle. Traps mitigations are generalized and not application-specific. Through its knowledge of exploitation techniques, Traps protects applications from being exploited, regardless of the delivery vectors associated with the exploit.
In our example, Traps protects Adobe Flash by default. When an attacker attempts to exploit a Flash vulnerability, Traps will thwart the exploitation attempt. The protection Traps applies is the same whether the Flash object is embedded in an Office document or in Outlook.
By blocking the exploitation technique that all exploits must utilize to successfully compromise an application, Traps turns the table on the attackers. It is no longer a case of an attacker choosing an exposed attack surface but of a defender who has control over all paths attackers must take.
As we have stated earlier, Microsoft has issued a patch for this vulnerability. History teaches us that attackers reverse-engineer high-impact, patched vulnerabilities. Outlook is the most widely used email application in enterprise environments, which makes CVE 02015-6172 a low-hanging fruit for exploit writers. Even when a patch is available, applying it to the entire 400 million Outlook customer base will be a long process. While most organizations remain vulnerable until the patch is distributed in their environments, Traps can protect all Windows servers and endpoints from CVE-2015-6172 right now with its built-in, default policy.
When encountering threats that are “many, varied and ever-changing,” it is important to gain an advantage through what is fixed and unchanged. Traps realizes this concept on the endpoint, rendering full, automated prevention of security breaches and advanced threats.
To learn more about how Traps prevents security breaches, visit our Advanced Endpoint Protection web portal.