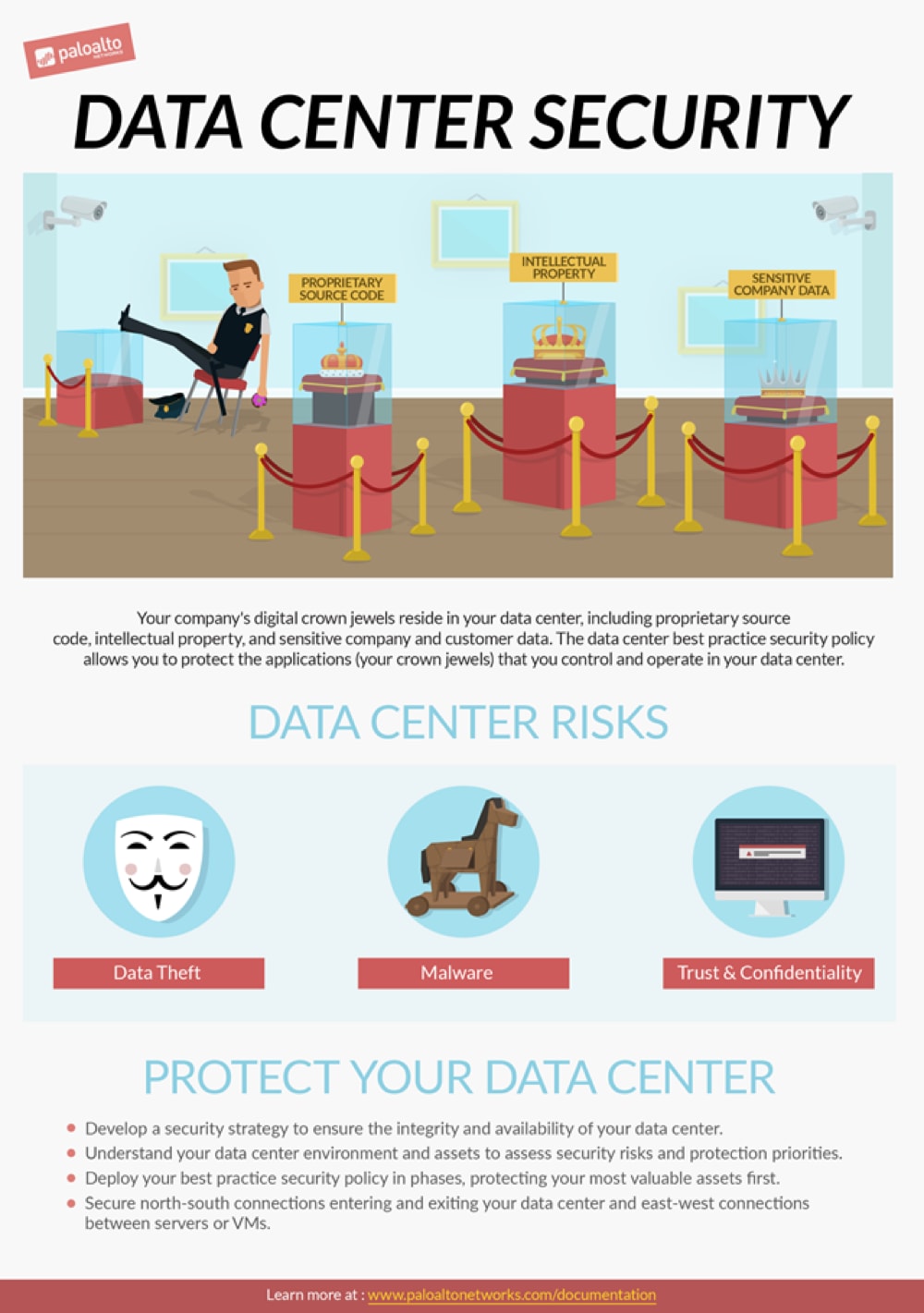
A data center houses an enterprise’s most critical data, such as source code, financial and personal information, or designs for pharmaceutical drugs – the enterprise’s digital crown jewels.
Designing and deploying a best practice security policy to protect your valuable data means protecting not only the perimeter of your enterprise network; it means protecting the connections into and out of the data center perimeter, as well as the connections between servers and VMs inside the data center.
But how do you transition to a data center best practice security policy?
In “Data Center Best Practice Security Policy Part 1: Concepts,” you’ll be presented with ways to think about a best practice security policy strategy and how to design it for your particular business, with the goal of achieving positive security enforcement that allows only the users, applications and content that you explicitly permit on the network, and denies all other traffic. It addresses questions such as:
- How do you create a transition strategy that aligns with your business goals?
- How do you decide which assets to protect first?
- What methods should you use to make the transition?
- How will you protect your data center during the transition?
Coming Soon!
If you enjoyed part 1, look for “Data Center Best Practice Security Policy Part 2: Implementation” to learn the specific best practices to apply to traffic at the perimeter and inside the data center.