This post is also available in: 日本語 (Japanese)
A Zero Trust approach of “never trust, always verify” is most effective when it spans all the locations and environments where workloads power and run your applications and data. That’s why our firewall platform significantly bolsters a Zero Trust architecture by moving network security as close to workloads as possible – and there are six primary reasons it does so effectively.
These six reasons address today’s reality of enterprises relying upon workloads hosted in more than one environment.
Application interconnectivity has led to an explosion of traffic between workloads found across data centers and public, private and hybrid clouds – as well as containerized workloads, which are rapidly spun up and destroyed to meet immediate needs in fast-paced environments.
Add third-party applications and services and all these growing interconnections between workloads become complex and difficult to manage, to say nothing of ensuring that access is not overprovisioned and only the right users and systems are able to communicate with each other.
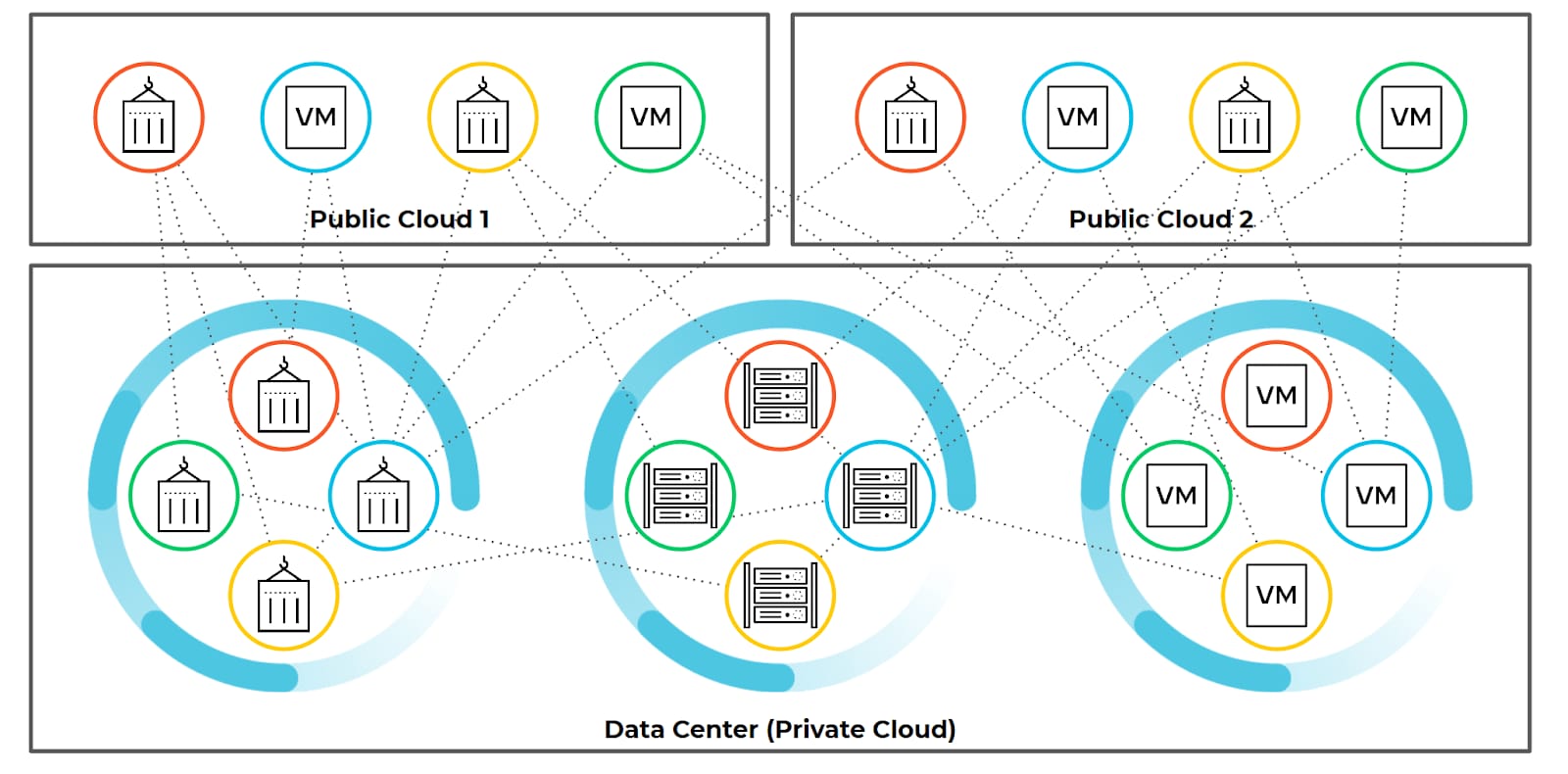
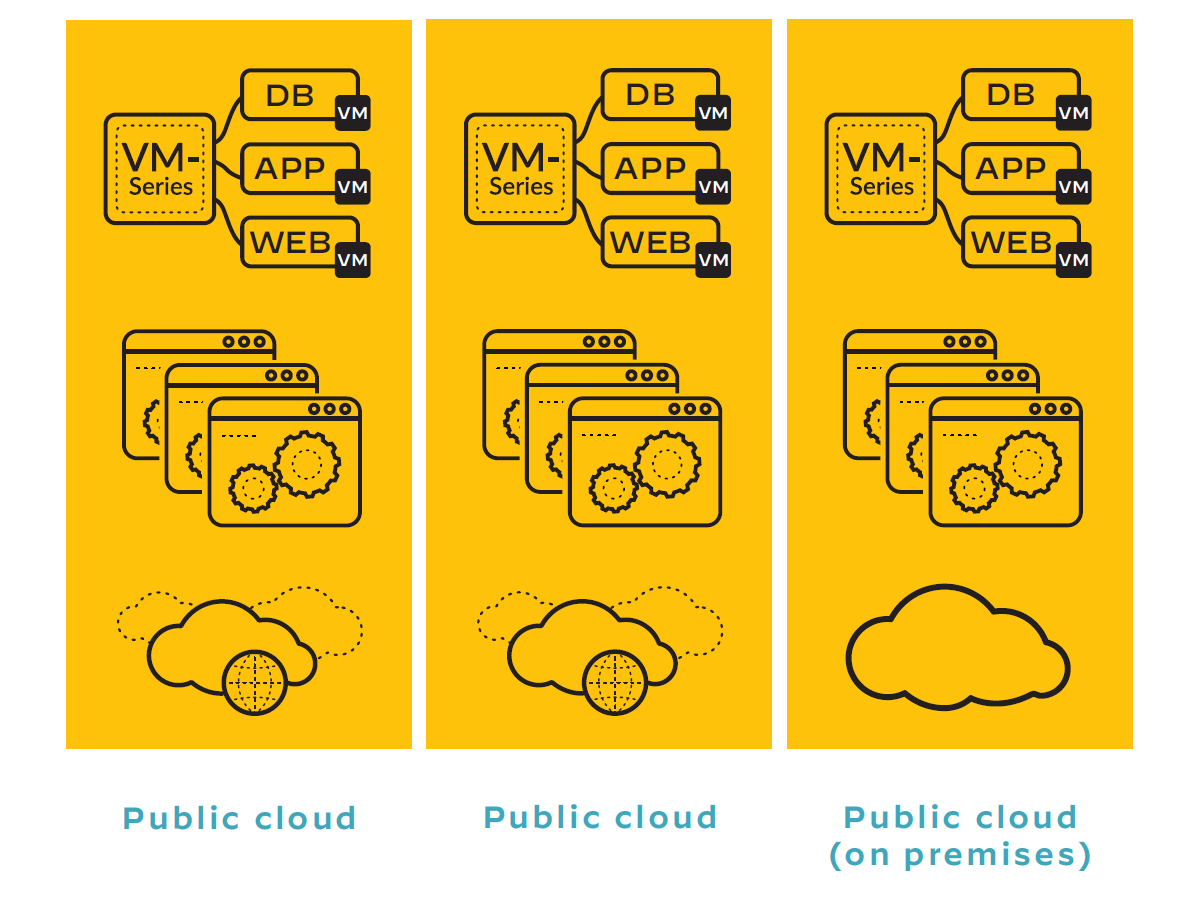
Take a look at the diagram above and you can easily imagine a scenario in which a containerized application hosted in a public cloud environment is, say, connected to a shared service hosted on a bare metal server in an on-prem data center. Take it a step further and you can also easily see how attackers might move between the two environments, taking advantage of a policy gap resulting from a lack of visibility and control into one part of the environment, and then start looking for other workloads to compromise.
With this constantly growing interconnectivity in mind, let’s look at the six reasons why our firewalls help ensure a Zero Trust approach at the workload level.
Reason #1: The Right Form Factor Provides the Layer 7 Visibility and Threat Prevention Everywhere
A guiding principle in the design of our ML-Powered Next-Generation Firewalls (NGFWs) is to move security as close as possible to the workload. This approach takes advantage of software constructs such as virtual machines, containers and Kubernetes®, and helps provide additional context for creating and managing security policies. It also ensures critical Layer 7 visibility and threat prevention vital to a Zero Trust approach for workloads, regardless of their hosting environments.
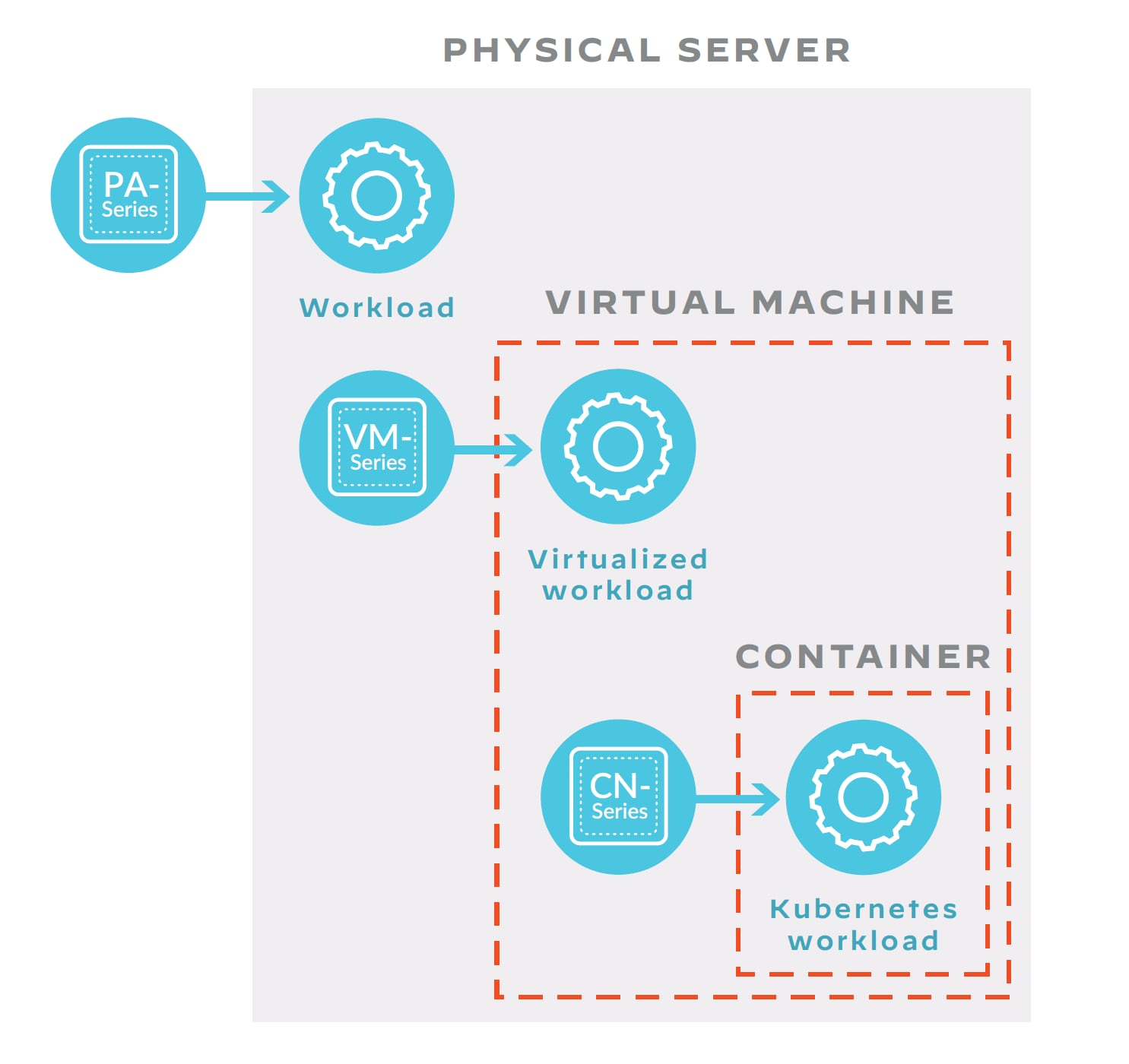
- PA-Series hardware NGFWs are ideal for workloads on physical machines in on-prem data center and multi-data center architectures.
- VM-Series virtual firewalls are designed for workloads in virtualized environments – public clouds, virtualized data centers and software-defined networking (SDN) environments.
- CN-Series container firewalls secure Kubernetes environments and protect traffic traversing Kubernetes namespace boundaries.
All three firewall form factors offer the same rich set of NGFW features and deep Layer 7 visibility and threat prevention into every part of a network infrastructure. This secures traffic between users, applications and services regardless of where workloads and users are located.
Reason #2: They Boost Real-World Network Segmentation and Microsegmentation
While network segmentation and microsegmentation certainly reduce the attack surface, they don’t guarantee security in complex environments. For one thing, communication across different workload types residing in different trust zones is increasingly common, as are trust zones themselves being located on physical, virtual and public cloud networks.
That’s why leveraging – and augmenting – network segmentation and microsegmentation is both a pillar of Zero Trust and an essential component of our firewall design. Our firewalls can automate security provisioning to simplify segmenting tasks. And, in internal networks, our customers can enforce trust zones using our software firewall form factors to segment their networks, which prevents the lateral spread of threats.
Microsegmentation goes a step further than segmentation to isolate workloads from one another and secure them individually. But what happens when you have workloads in microsegmented environments that must communicate with each other?
Our firewalls provide visibility and protection for the necessary allowed traffic between apps and services in microsegmented environments. And to make sure attackers can’t take advantage of these allowed connections to move laterally in an environment, advanced threat prevention, such as intrusion prevention, is built into each firewall to secure workload traffic that moves between trust zones, especially zones with different levels of trust.
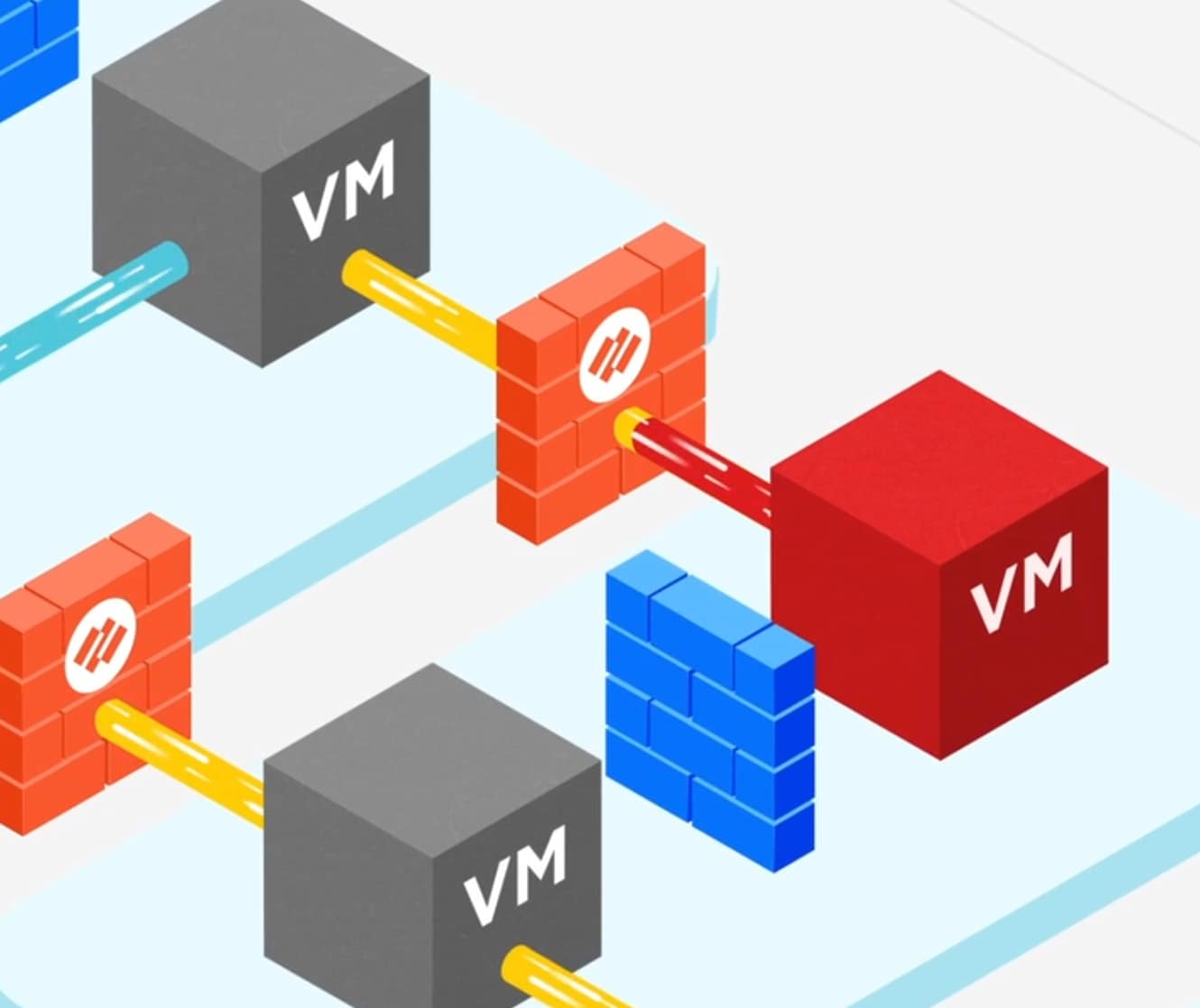
Reason #3: They Dramatically Limit Lateral Movement Between Disparate Workloads
That Palo Alto Networks firewall enforcement of workload trust boundaries around sensitive data and applications goes a long way in preventing threats from moving at will laterally within the infrastructure. It’s critical for Zero Trust at the workload level, because once attackers breach the security perimeter, they’re likely to propagate internally from compromised physical machines, virtual machines and containers. This kind of “east-west” movement is difficult to detect in real time with logs and other traditional security tools – or with disconnected tools that cannot easily oversee and protect disparate and interconnected workloads.
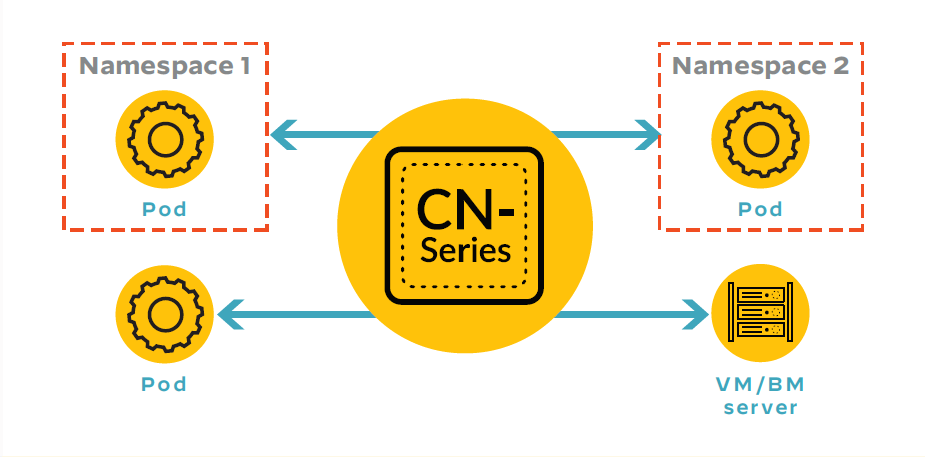
As an example of this protection in action, the CN-Series container firewall behaves like our other firewalls when it inserts Layer 7 traffic protection and advanced threat protection into Kubernetes environments – such as securing the allowed connections between two containerized applications of different trust levels. But to protect against lateral movement by securing traffic between pods and other workload types (such as virtual machines or even bare metal servers), the CN-Series limits lateral movement within Kubernetes as well as the rest of the infrastructure.
Reason #4: Centralized Management Simplifies Granular User-Access Control
To simplify management of all of your firewalls and security policies, Panorama can manage all of our firewall form factors from a single console. So rather than duplicate policies across environments, security teams can deliver the same best-in-class security to each environment and their workloads – extending a uniform policy model across the entire ecosystem to ensure consistent user verification and access.
VM-Series virtual firewalls deployed in public and private clouds, for example, can all be managed from the same Panorama console. This lets security teams deliver the same best-in-class, Zero Trust security capabilities to each environment and their workloads.
Reason #5: Automation Ensures Granular Control – Even in Dynamic Environments
Automation and scalability further reduce time, effort, expense and error. When new workloads are spun up, they can be automatically be protected with their security policies based on their native infrastructure tags and label. And when traffic spikes, additional firewalls can be provisioned in minutes to handle the increased traffic and protect applications and workloads.
Additionally, virtual firewalls can automatically trigger responses to detected threats. In SDN environments, the VM-Series automates threat response by notifying VMware NSX or Nutanix Flow of the existence of an infected workload, which NSX then tags. The VM-Series uses the NSX tag to enforce a quarantine policy, cutting off the workload’s ability to communicate. By leveraging a tag-based policy model, you can detach your security rules from static attributes such as IP addresses and ensure that whenever a new workload is created and tagged appropriately, it will automatically inherit the correct security policy.
Reason #6: Workloads Get the Zero Trust Attention They Need
Regardless of where your workloads reside, our firewall platform is fully aligned with Zero Trust so workloads, applications and data are continuously assessed through the lens of constant verification – which blocks data exfiltration, hijacking, ransomware and the myriad ongoing threats hybrid workloads face.
These reasons help show how to lay a solid foundation for implementing Zero Trust throughout your infrastructure, but they represent only some aspects of an enterprise Zero Trust strategy. Watch as Palo Alto Networks Founder and CTO Nir Zuk explains how it all fits together. And be sure to check out the rest of the blogs in our Zero Trust series.