What Is Network Segmentation?
Network segmentation is an architectural approach that divides a network into multiple segments or subnets, each acting as its own small network. This allows network administrators to control the flow of network traffic between subnets based on granular policies. Organizations use segmentation to improve monitoring, boost performance, localize technical issues and – most importantly – enhance security.
With network segmentation, network security personnel have a powerful tool with which to prevent unauthorized users and protect static IP addresses, whether curious insiders or malicious attackers, from gaining access to valuable assets, such as customers’ personal information, corporate financial records and highly confidential intellectual property, the so-called “crown jewels” of the enterprise. As a result of the rise of software-defined networking (SDN), these assets are frequently found spread across hybrid and multicloud environments – public clouds, private clouds and software-defined networks (SDNs) – all of which need to be secured against attacks and data breaches. To understand the security usage of network segmentation, it’s first necessary to consider the concept of trust in network security.
The Trust Assumption
In the past, network architects targeted their security strategies at the internal network perimeter, the invisible line that separates the outside world from the data vital to an enterprise’s business. Individuals within the perimeter were assumed to be trustworthy and therefore not a threat. Thus, they were subject to few restrictions on their ability to access information.
However, legacy security infrastructures are generally flat network architectures that rely on a perimeter firewall as their only point of traffic inspection and control. Since network boundaries don’t exist as they used to, and most data center traffic is east-west, traditional port-based firewalls provide limited value in a cloud and mobile world.
Recent high-profile breaches have called the trust assumption into question. For one thing, insiders can indeed be the source of breaches, often inadvertently but sometimes deliberately. In addition, when threats penetrate the perimeter, they are free to move laterally in the network to access virtually any data, application, asset or services (DAAS). With virtually unhindered access, attackers can easily exfiltrate a full range of valuable assets, often before the breach has even been detected (see figure 1).
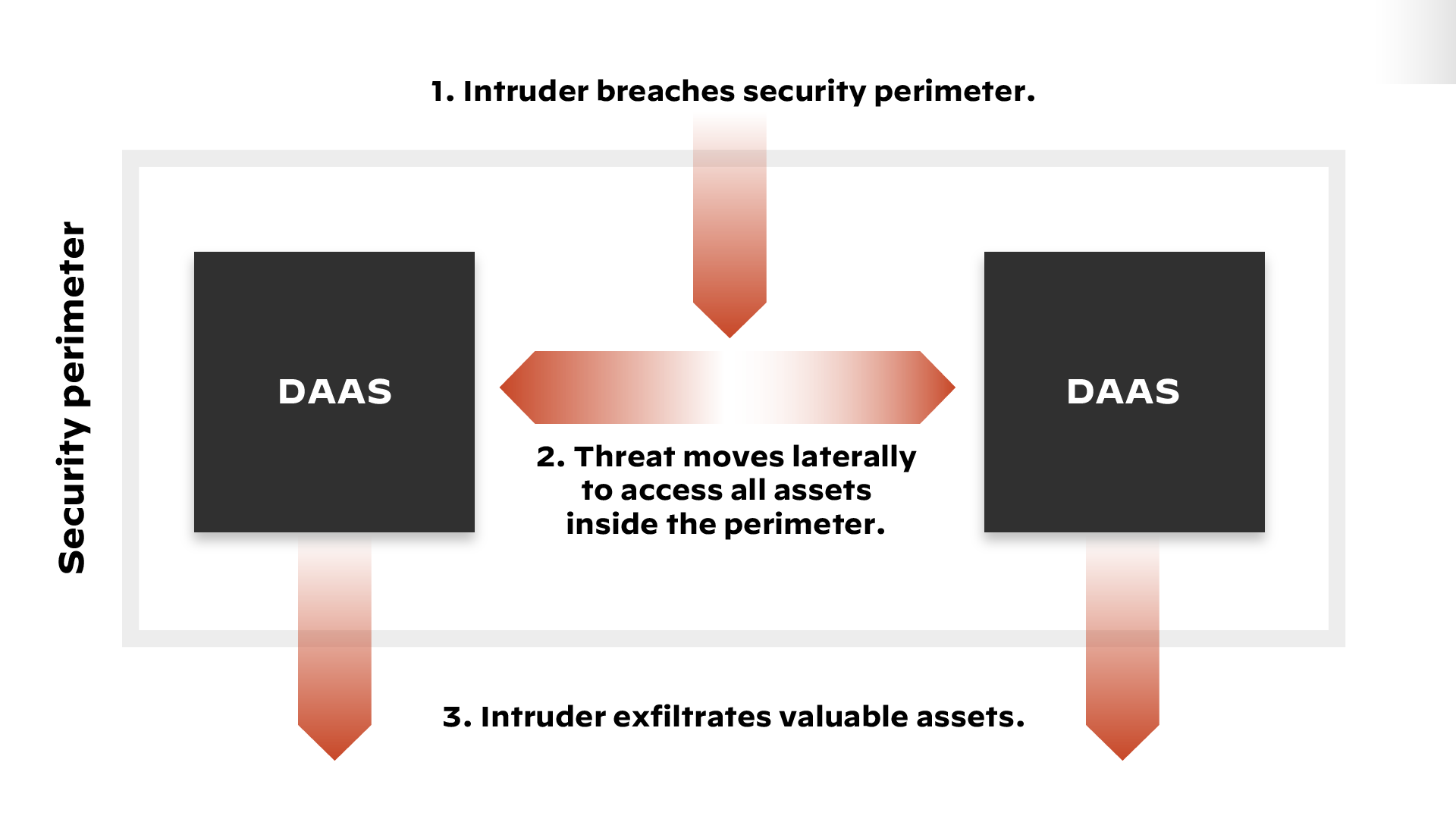
Figure 1: Lateral movement inside the perimeter under the trust assumption
The Zero Trust Response
Because of the inherent weaknesses of assumed trust, many organizations have begun to adopt the Zero Trust strategy. Zero Trust assumes nobody is trustworthy by default, even those already inside the network perimeter. Zero Trust works on the principle of a “protect surface” built around the organization’s most critical and valuable DAAS. Because it contains only what’s most critical to business operations, the protect surface is orders of magnitude smaller than the attack surface of the full network perimeter.
This is where network segmentation comes in. Using segmentation, network architects can construct a microperimeter around the protect surface, essentially forming a second line of defense. In some instances, virtual firewalls can automate security provisioning to simplify segmenting tasks. However it is accomplished, authorized users can access assets within the protect surface while all others are barred by default.
Segmentation is bad news for attackers because, unlike in the days of assumed trust, simply penetrating the perimeter isn’t enough to gain access to sensitive information. Microperimeters, whether physical or virtual, prevent threats from moving laterally within the network, essentially negating much of the work that went into creating the initial breach (see figure 2).
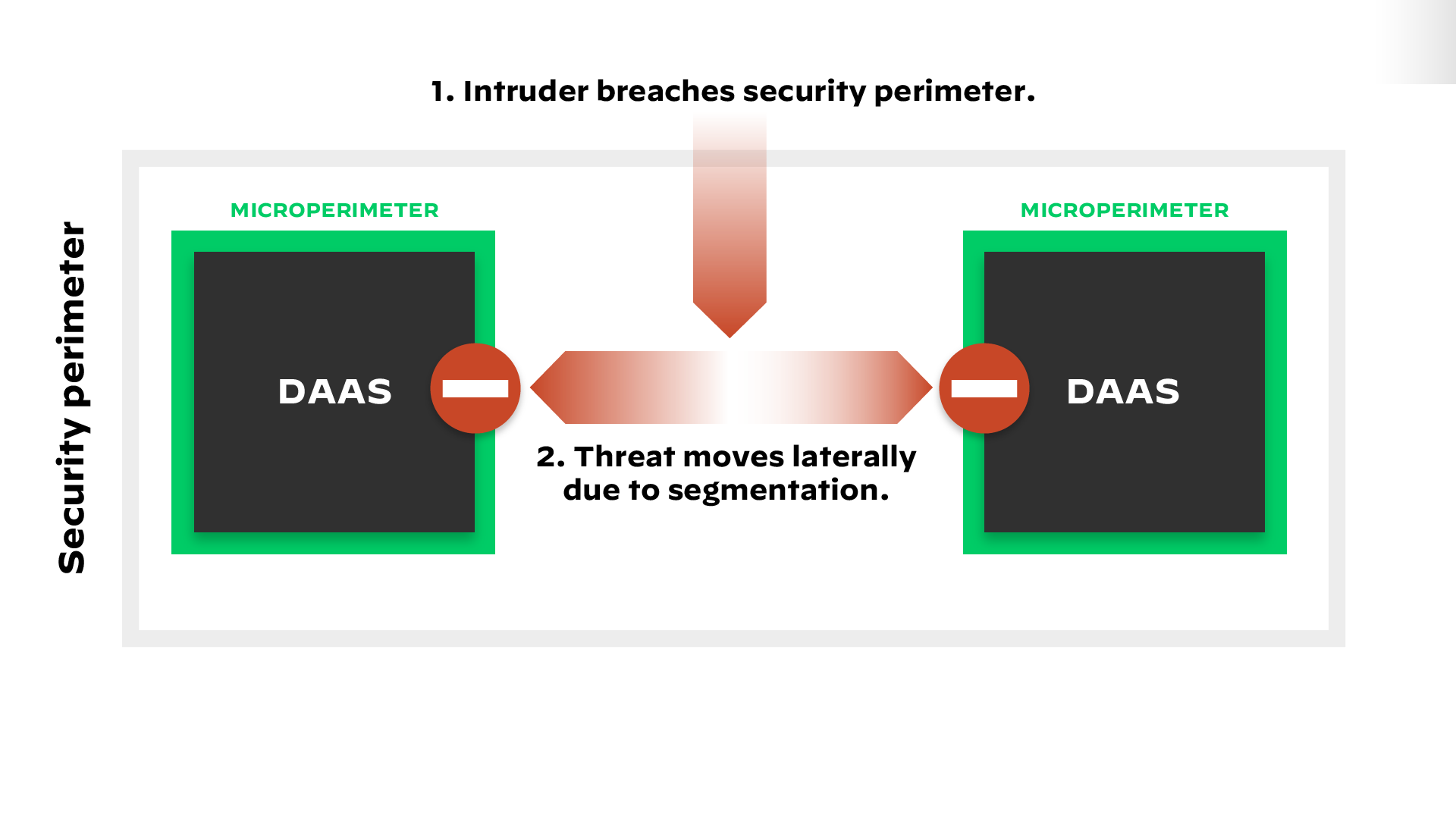
Figure 2: Limited movement inside the perimeter with Zero Trust and network segmentation
Use Cases
Organizations can use network segmentation for a variety of applications, including:
- Guest wireless network: Using network segmentation, a company can offer Wi-Fi service to visitors and contractors at relatively little risk. When someone logs in with guest credentials, they enter a microsegment that provides access to the internet and nothing else.
- User group access: To guard against insider breaches, many enterprises segment individual internal departments into separate subnets consisting of the authorized group members and the DAAS they need to do their jobs. Access between subnets is rigorously controlled. For example, someone in engineering attempting to access the human resources subnet would trigger an alert and an investigation.
- Public cloud security: Cloud service providers are typically responsible for security in the cloud infrastructure, but the customer is responsible for the security of the operating systems, platforms, access control, data, intellectual property, source code and customer-facing content that typically sit atop the infrastructure. Segmentation is an effective method for isolating applications in public and hybrid cloud environments.
- PCI DSS compliance: Network administrators can use segmentation to isolate all credit card information into a security zone – essentially a protect surface – and create rules to allow only the absolute minimum, legitimate traffic in the zone while automatically denying everything else. These isolated zones are frequently virtualized SDNs in which PCI DSS compliance and segmentation can be achieved via virtual firewalls.
Physical vs. Logical Segmentation
Network segmentation can be implemented as either physical or logical segmentation.
As the name implies, physical segmentation involves breaking down a larger computer network into a collection of smaller subnets. A physical or virtual firewall acts as the subnet gateway, controlling which traffic comes in and goes out. Physical segmentation is relatively straightforward to administer because the topology is fixed in the architecture.
Logical segmentation creates subnets using one of two primary methods: virtual local area networks (VLANs) or network addressing schemes. VLAN-based approaches are fairly straightforward to implement because the VLAN tags automatically route traffic to the appropriate subnet. Network addressing schemes are equally effective but require more detailed understanding of networking theory. Logical segmentation is more flexible than physical segmentation because it requires no wiring or physical movement of components to accomplish. Automated provisioning can greatly simplify the configuration of subnets.
Moving to a segmentation architecture provides an opportunity to simplify the management of firewall policies. An emerging best practice is to use a single consolidated policy for subnet access control as well as threat detection and mitigation, rather than performing these functions in different parts of the network. This approach reduces the attack surface and strengthens the organization’s security posture.
Benefits of Network Segmentation
- Stronger network security
Because segmentation splits the network into smaller subnetworks, isolating network traffic lessens the attack surface, obstructing lateral movement. Segmentation also isolates attacks before they spread. For instance, a malware infection in one subnetwork would not impact systems in another. - Less congestion, better performance
Network segmentation reduces congestion. When a network has too many network hosts, congestion ensues because too many packets are transmitted. In some cases, performance can suffer to a degree wherein no packet is delivered. Subnetting, or breaking the network into small segments, relieves congestion significantly. - Decreased scope of compliance
Regulatory compliance costs can be reduced using network segmentation, as it limits the amount of in-scope systems.