This post is also available in: 日本語 (Japanese)
The pandemic has changed the way we work and conduct business for good. Poll after poll confirms that people “do not want to go back to the office full time, even once it’s safe to do so.” With hybrid work environments becoming the new norm, organizations are reconsidering their networking and security infrastructure to support this new reality.
Corporations need to ensure that their employees have optimal user experience wherever and whenever they work, while maintaining safe access to the right data and applications for the right users and devices. This is difficult to achieve in a hybrid cloud world where data, applications and user identity are spread across on-premises and cloud sources. Meanwhile, security teams are under pressure to secure the ever-increasing surface area of their organizations efficiently with finite people and limited resources.
Palo Alto Networks announced Complete Zero Trust Network Security to address these requirements and safeguard productivity in this new reality of a hybrid work environment. In addition to new services such as SaaS Security service, Advanced URL Filtering and expanded DNS security capabilities, we introduced innovations in the core operating system to continue to empower organizations to move toward Zero Trust.
The latest PAN-OS 10.1 innovations simplify identity-based security, simplify and consolidate decryption, enable you to manage firewalls efficiently by using open and programmable platforms, and deliver hyperscale security in physical and virtual environments. Let's look at some of the key innovations introduced in PAN-OS 10.1.
Simplify Zero Trust for Identity
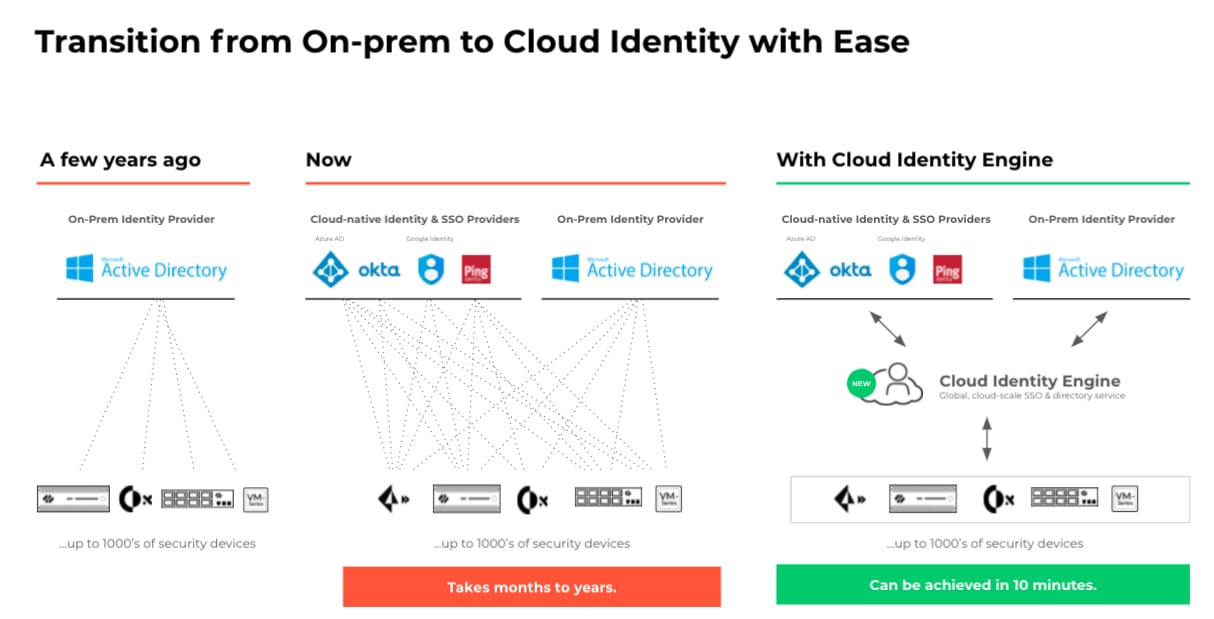
Enterprises today find it hard to consistently verify their users and enforce identity-based security as user information is fragmented between different identity stores, such as Active Directory (on-premises), Okta (cloud), Azure AD (cloud) and more. This has led to network security operators struggling to secure their workforce and enable safe and secure access to applications and data. Configuring, maintaining and synchronizing the network security ecosystem with the multiple identity providers is time-consuming and resource-intensive, resulting in significantly increased effort and delayed projects.
With Cloud Identity Engine, security teams can now consistently authenticate and authorize their users, regardless of location or where user identity stores live. As a result, security teams can effortlessly allow access to applications and data everywhere – cloud, on-prem or hybrid – to quickly move toward a Zero Trust security posture. The Cloud Identity Engine offers a cloud-based architecture and assures synchronization of all identity-related data in the cloud to apply controls everywhere in the enterprise: data center, campus, public cloud, branches and remote users. New identity sources can be configured in about 10 minutes, versus days or months, saving time in deployment and management of identity-based controls on your network security infrastructure.
Consolidate and Simplify Decryption
Deploying decryption is crucial before securing all content, however, deploying and maintaining decryption has been a challenge for the industry. Organizations that deploy third-party security controls as part of their overall security suite need to decrypt traffic multiple times to realize the benefits of their entire security stack. Doing so introduces operational complexity, increases network latency and negatively impacts the end-user experience. Although firewall vendors offer decryption, they seldom send all the traffic to third-party security tools, which creates blind spots. As a result, enterprises buy additional appliances such as SSL decryption and dedicated packet broker appliances to decrypt, filter and forward traffic to security tools, increasing cost and operational complexity.
Palo Alto Networks makes it easy to deploy and maintain decryption with comprehensive visibility, support for modern protocols, easy troubleshooting and new hardware Next-Generation Firewalls (NGFW) and Data Processing Cards with heavily accelerated performance. With Network Packet Broker in PAN-OS 10.1, NGFWs by Palo Alto Networks can intelligently broker all types of traffic (Decrypted TLS, encrypted TLS and non-TLS) to a suite of third-party security tools from a single device. This allows customers to simplify their network and reduce capital and operating expenses with built-in decryption and broker on the NGFWs. In addition, network security teams can now optimize their network performance and maximize their existing security tools' efficacy by selectively sending only the necessary traffic to a given third-party security tool. For more information, download our “Decryption: Why, Where and How” whitepaper.
Simplify Management of Zero Trust Network Security Infrastructure
Network operators face a challenge while trying to enforce Zero Trust across their network. In PAN-OS 10.1 we have introduced two new capabilities to simplify management to better enable your Zero Trust strategy across network security infrastructure.
OpenConfig (OC)
Programmatically managing network services that span multiple network elements in their multi-vendor infrastructure can be difficult due to a lack of common schema/model interfaces.
With the support for OC vendor-neutral data models, Palo Alto Networks brings additional automation capabilities to the NGFWs. Customers can now manage NGFWs with OC to automate network service configuration across their infrastructure and stream telemetry to quickly resolve NGFW health and performance issues for their entire deployment.
Scheduled Push
When it comes to managing configuration changes in the management tools, administrators accumulate all the changes and have to wait for the next change management window to push the changes to the firewalls. Change management windows are typically off hours to avoid outages and admins’ need to be present to push the changes interactively during that time.
With PAN-OS 10.1, we are making it simple for admins to automate configuration changes for all firewalls with Scheduled Push with Panorama – a network security management solution. Schedule Push reduces human involvement during off hours. Admins can now schedule a one-time or recurring push to firewalls of their choice within Panorama, without having to be present. Admins can also efficiently push changes across their entire deployment in one single push. This also works for multi-virtual system (VSYS) firewalls, so if multiple device groups are mapped to different VSYS on a firewall, a single scheduled push can update the multi-VSYS firewalls. Panorama also gives you the ability to track all the changes. The execution of the scheduled push happens unsupervised, but all details are captured in system logs and configuration logs, including any errors.
Hyperscale Virtualized Network Security
In hyperscale data centers, the need to leverage compute resources as efficiently as possible is paramount. Service providers and enterprises alike strive to maximize efficiency to drive operating expenses down. This is one of the core reasons that organizations adopt virtualization, but it raises a question about how to effectively enforce Zero Trust Network Security in a virtual environment.
With the new Intelligent Traffic Offload feature, the VM-Series virtual NGFWs eliminate the tradeoff between security and cost in service provider and hyperscale data center environments. Organizations can extend Zero Trust Network Security posture to a virtualized infrastructure without breaking the bank or compromising network performance.

Find out how we’re securing the new flexible workplace. For a complete list of new PAN-OS 10.1 innovations, please see our PAN-OS Release Notes. Watch our virtual launch event on-demand: Complete Zero Trust Network Security. And get ready to secure productivity wherever it takes place.