DevSecOps has risen to buzzword status in the past few years, encompassing several shift left security use cases. And while the word DevSecOps gets thrown around a lot, there are still some misconceptions about what it actually entails and why it’s touted so frequently as the answer to all modern, cloud-native security woes. In this post, we’ll explore some common DevSecOps use cases and their benefits. But first, let’s start from the top.
DevSecOps Explained
Simply put, DevSecOps is a methodology that embeds security into every stage of the software development lifecycle. In response to more reactive and manual approaches to cybersecurity, DevSecOps evolved out of DevOps to take a more proactive and agile approach to security.
How Does DevSecOps Differ From DevOps?
DevOps is based on guiding principles like automation, collaboration and continuous testing. Developers use processes such as git, version control systems (VCS) and automated continuous integration and delivery (CI/CD) pipelines to efficiently control how software is built, managed and released. With DevOps, stages of the software development process are no longer siloed or executed independently, which improves team agility and velocity as well as software quality.
Although there is an emphasis on quality with DevOps, security concerns are not explicitly addressed. Traditionally, security—for both applications and infrastructure—happens at the end of the development lifecycle. And crucially, security is traditionally owned by InfoSec teams tasked with protecting applications rather than the engineering teams that built them. Similar to the friction that ensued between development and operations teams that led to the rise of DevOps, DevSecOps aims to break down silos between security and engineering teams.
To do that, DevSecOps builds upon the DevOps best practice of leveraging automation to embed security best practices into developers’ tools and workflows. This enables the right teams to more easily identify and address security issues early and throughout all stages of development.
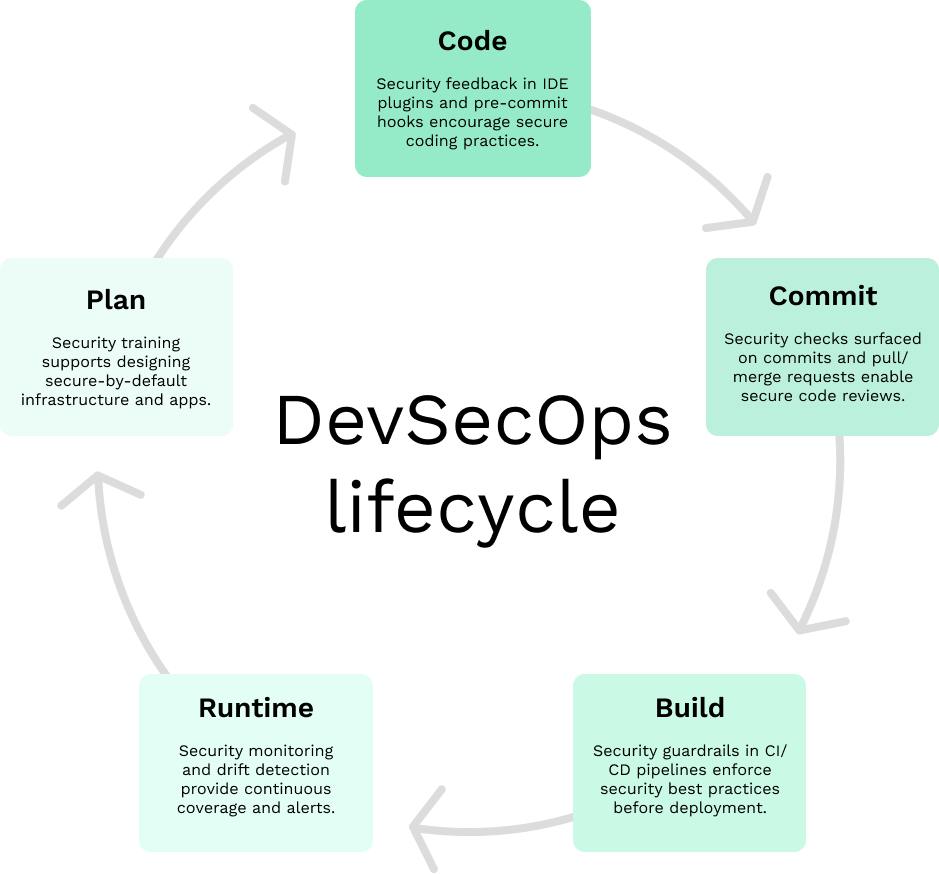
DevSecOps Use Cases
Three of the most common use cases for DevSecOps are application security, infrastructure as code (IaC) security and version control and CI/CD pipeline security. Regardless of the DevSecOps use case, it’s crucial to integrate security into the development process as early and often as possible via the tools already in use, such as IDEs, version control systems and build pipelines.
Application Security
Application security—commonly shortened to AppSec—focuses on identifying vulnerabilities in application code, third-party packages, container images and runtime application environments. Taking a more developer-friendly approach with DevSecOps requires focusing on identifying those vulnerabilities as early as possible.
Common AppSec testing methods include:
- Static Application Security Testing (SAST) is used to statically scan source code and related dependencies for known vulnerabilities through white-box testing.
- Dynamic Application Security Testing (DAST) is used to simulate a cyberattack through running web applications or APIs without directly accessing your source code through black-box testing.
- Software Composition Analysis (SCA) is used to scan open source packages for known vulnerabilities and identify open source license compliance issues.
- Interactive Application Security Testing (IAST) is used to gain real-time visibility into your application’s runtime security.
But without the right approach, these security measures become reactive and result in friction between security teams wanting to fix every single vulnerability and developers who have context into what is and isn’t a real risk.
Taking a DevSecOps approach to AppSec means surfacing application vulnerabilities early and directly to the developers who understand the context in which they may exist. You can do this by embedding SCA and SAST tools into your version control system to flag vulnerabilities in IDEs and VCSs, where it’s easiest for developers to fix issues. Even if you’re continuously scanning your code in build-time, you’ll want to ensure security coverage across the development lifecycle by employing IAST and DAST tooling. If you embed these tools into your CI/CD pipeline, your DevOps team can gain visibility into the application runtime environment and make any fixes as needed. To fully embrace DevSecOps for AppSec, you also need to encourage collaboration between your security and DevOps teams so they can identify relevant sources of security risk and prioritize critical vulnerabilities.
Infrastructure as Code (IaC) Security
IaC enables you to configure cloud infrastructure via code and use those files to automatically spin up cloud infrastructure at scale. IaC frameworks such as Terraform, CloudFormation, Kubernetes and Azure Resource Manager (ARM) vastly simplify the process of provisioning and managing cloud infrastructure, but they can also add complexity when it comes to security. Cloud misconfigurations are easy to miss in IaC without the right security awareness or tools.
That risk of misconfiguration is exacerbated by the use of open source templates, which, similar to third-party packages, make it easier to spin up infrastructure without reinventing the wheel. Also, similar to open source libraries and licenses, open source IaC can contain security flaws. Research from Unit 42’s Cloud Threat Report showed that about half of open source Terraform templates contain misconfigurations.
If not detected early, those misconfigurations can cause noisy alerts and introduce misconfigurations into your runtime environment. Because the risk of misconfigured cloud resources is so great, it’s important to embed IaC security tools such as Checkov into your workflows.
IaC security scanning tools allow teams to shift cloud security left by identifying misconfigurations—like missing encryption and weak security group roles—in build-time rather than runtime. As you implement DevSecOps best practices across your infrastructure stack, you’ll want to focus not only on identifying issues early but also on enabling developers with the context they need to swiftly understand and fix issues. More advanced cloud DevSecOps initiatives may also include code to cloud visibility through IaC resource tagging to enable drift detection and transforming runtime misconfigurations into code fixes.
Version Control and CI/CD Pipeline Security
In addition to securing your code, it’s important to remember that the underlying pipelines such as your VCS and CI/CD can contain weaknesses that bad actors can use as entry points to access sensitive data or inject malicious code. With the right security approach and tools, however, you can automatically scan your VCS organizations, repo configurations and CI/CD workflow configurations to ensure they’re following security best practices.
For secure VCS and repo configurations, this includes scanning to ensure best practices such as multifactor authentication, single sign-on (SSO), signed commits and branch protection rules are in place. And for your CI/CD workflow configurations, you’ll also want to scan for overly permissive roles and automatically enforce stricter permissions that follow the principle of least privilege. Locking down repos and delivery pipelines requires tight collaboration between security and DevOps teams to ensure developers aren’t hindered from shipping code but that all security gaps are covered.
Following those security best practices is a must, but because these systems are typically hosted by third parties or are built on top of third-party components, new risks may also arise. For that reason, it’s crucial that security and DevOps teams work together to stay on top of new vulnerabilities and exploits to prevent software supply chain attacks. A good first step to maintaining software supply chain security is getting visibility into how software components and their pipelines are connected.
Key Benefits of Using DevSecOps
DevSecOps is buzzworthy for a reason. Teams that successfully embrace it have the potential to revolutionize their approach to security, breaking silos between teams, reducing manual effort, and ultimately, improving release velocity.
Reduced Time Spent on Repetitive Security Tasks
The DevSecOps methodology’s obsession with automation reduces the time spent on repetitive security tasks. Instead of spending their time on fixing security issues, developers can now focus their time on more high-value ventures like implementing new features, fixing functionality bugs and working on innovative R&D projects. And with DevSecOps, there is less rework because issues are flagged and addressed by the right people at the right time. This approach to security reduces the amount of context switching and back and forths between developers and security teams when addressing security issues in code.
Improved Security Response Times
DevSecOps also makes the software development process more efficient by reducing the MTTR (mean time to remediate) security issues. By empowering developers to address issues at the right time and place, fewer issues make their way into becoming runtime alerts. With fewer alerts to triage and better context and collaboration between developers, security teams and operation teams, remediating issues is much faster.
Reduced Security Risks
By combining the previous two benefits of addressing issues at their source and having fewer alerts distracting security and engineering teams, DevSecOps provides more cohesive coverage. This risk reduction makes it more challenging for bad actors to gain access to your system, inject malicious code into your files, or steal valuable data.
Enables You to Level up Your Team’s Culture of Security
When done right, a culture of DevSecOps can empower developers to get curious about security. This encourages developers to improve their security knowledge and take ownership of building secure software, starting with their code. Developers learn to apply the basic principles of application security, like using appropriate tooling, which automates and streamlines security review processes and introduces more advanced security techniques into team workflows.
While using the appropriate tooling is important to get started with DevSecOps, to truly shift left, you’ll need to create a culture of DevSecOps within your team. To become a solid DevSecOps team, ensure you:
- Prioritize short and frequent code releases with embedded automated security scans to make security checks quicker and more efficient.
- Conduct periodic scans, code reviews and other security tests across each stage of the development cycle to discover, investigate and fix any emerging security weaknesses in code.
- Empower developers with security training, invest in individuals who want to become security champions and encourage developers to regularly attend security conferences.
DevSecOps is revolutionizing the way we develop software and proactively address cloud security issues. By expanding upon the DevOps tenet of automation to embed security best practices, DevSecOps enables you to automate your cloud-native security from code to cloud.
Interested in implementing DevSecOps, but not sure how to get your team on board? Check out this blog for help as you build a business case for DevSecOps.