While we tend to talk about them as if they were a single entity, cloud environments are typically composed of multiple accounts across different global regions, with many users that have varying levels of privileged access. It's this complexity that heightens the risk of compromised credentials and insider threats.
User and Entity Behavior Analytics (UEBA) is one of the components that help reduce those risks. However, traditional UEBA tools fail to adapt to users' ever-changing behavioral patterns in multi-cloud environments. Prisma Cloud UEBA functionality addresses these issues with advanced machine learning (ML) techniques that help recognize unusual user activity, brute force anomalies and login anomalies.
To further strengthen these efforts, we are introducing compute provisioning anomaly detection, one of the top challenges facing cloud security teams.
The Challenges of Tracking Increased Compute Usage
Gartner predicts that cloud spending on Infrastructure-as-a-Service (IaaS) will reach $82 billion in 2021. Typically, about ⅔ of the public cloud bill is spent on compute (VMs), which equals about $54.7 billion.
With that level of spending, it is easy to miss abnormal usage. For example, if an organization is spending $10M a year on VMs, it is easy to overlook when an internal user, either accidentally or maliciously, is spinning up VMs that cost another $50K, since that would represent less than 1% of total spending. Similarly, an attacker could infiltrate an environment and spin up hundreds of VMs at a time without anyone noticing the suspicious activities.
Suspicious provisioning of compute resources is often a precursor to the creation of an unauthorized network of compute instances for cryptojacking purposes. Cryptojacking is the process of illegally mining cryptocurrencies using systems that are not owned or maintained by the mining operators. As cryptocurrencies such as Bitcoin and Ethereum reach all-time highs, criminal organizations are highly incentivized to cash in on this profitable global market using such means.
Unit 42 researchers have reported that cryptojacking operations are currently estimated to affect 23% of cloud environments, up from 8% in 2018. What’s more, anomalous compute provisioning activities could indicate the potential for further cloud account compromise.
Detecting Anomalous Compute Provisioning with Prisma Cloud
Prisma Cloud uses audit logs to perform UEBA to identify unusual user activity. Machine Learning algorithms profile user activities and usage of access keys based on the location and the type of cloud resources, which sets the baseline for "normal" user activity patterns. By tying chains of activities together and correlating additional resource visibility data, Prisma Cloud would categorize an activity as unusual or not.
The key to detecting anomalous compute provisioning activity, then, is to define what constitutes an organization's normal boundaries. In the datacenter world, establishing this “normal compute resource usage” pattern was relatively straightforward – but it is exponentially more difficult in the cloud world. Thanks to things like cloud bursting, CI/CD, blue/green deploy or dark deploy, cloud compute resources constantly spun up and down.
Basic ML-based solutions are often tripped up by these usage patterns, generating lots of false positives and ultimately causing alert fatigue. To properly identify either accidental or malicious compute resource provisioning, a sophisticated ML-based solution would need to take multiple other factors into consideration: Did the user try to hide their identity behind the TOR anonymity network? Did the user provision the compute resources from multiple geographical locations in hope to evade detection?
Let’s take a look at some real-world examples.
The image below charts an actual attack on a Prisma Cloud customer. Though it only lasted four hours, the new compute provisioning anomaly detection was able to identify it. The attacker used a managed Kubernetes service to create over 2000 cloud instances (with an estimated cost of $55k per day) across 24 global regions, using 40 TOR exit nodes. Prisma Cloud was able to detect this anomaly after learning the normal behavior of the users in the organization.
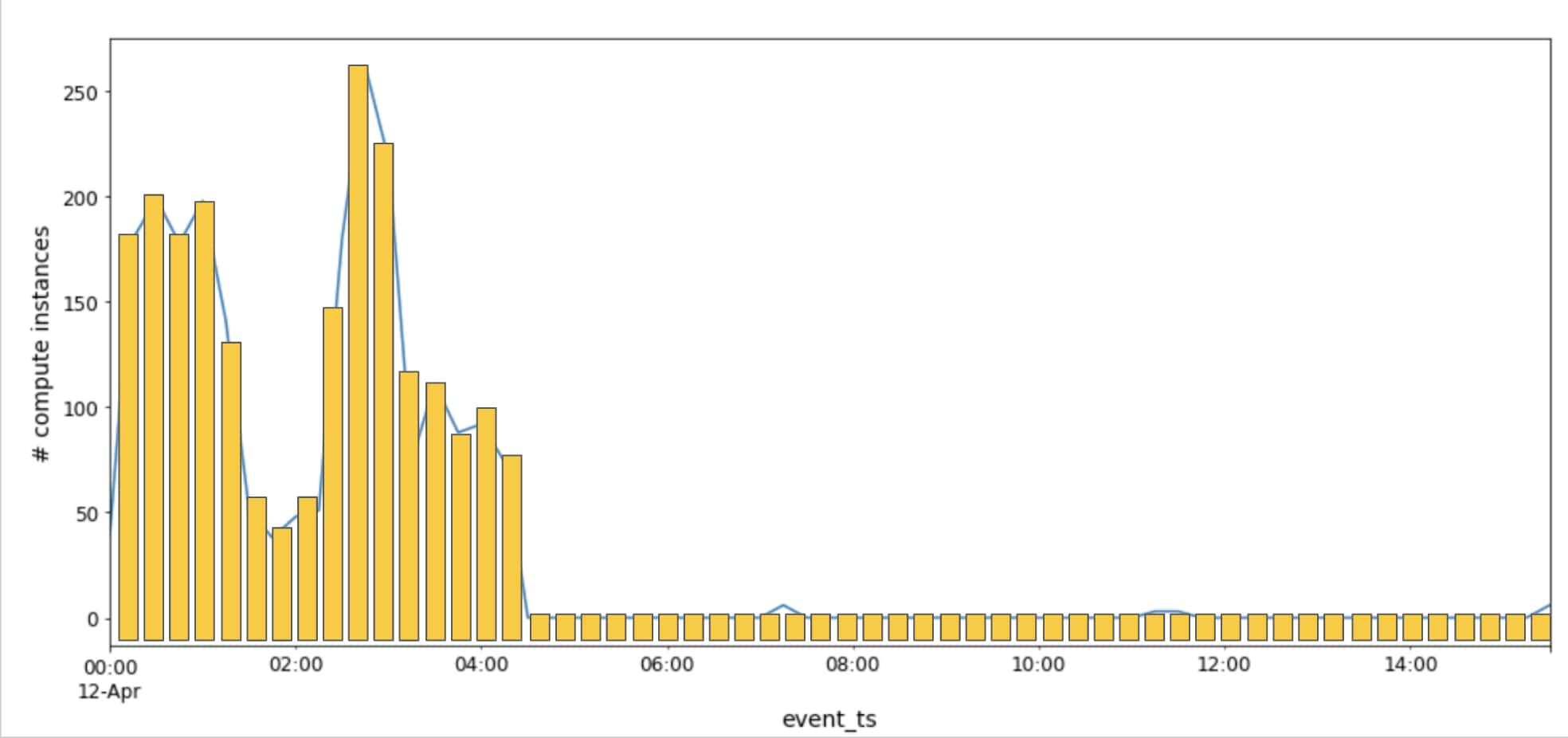
Another customer example involves a failed attack. An employee accidentally posted his private key on GitHub, and within minutes there were attempts from three TOR nodes to use the key to create 50 compute instances. Luckily, the malicious efforts were blocked by constraints the DevOps team had set on the Google Cloud account, but Prisma Cloud was able to detect the unusual activity and prompt the customer to delete the secret.
Customizing Prisma Cloud Threat Detection
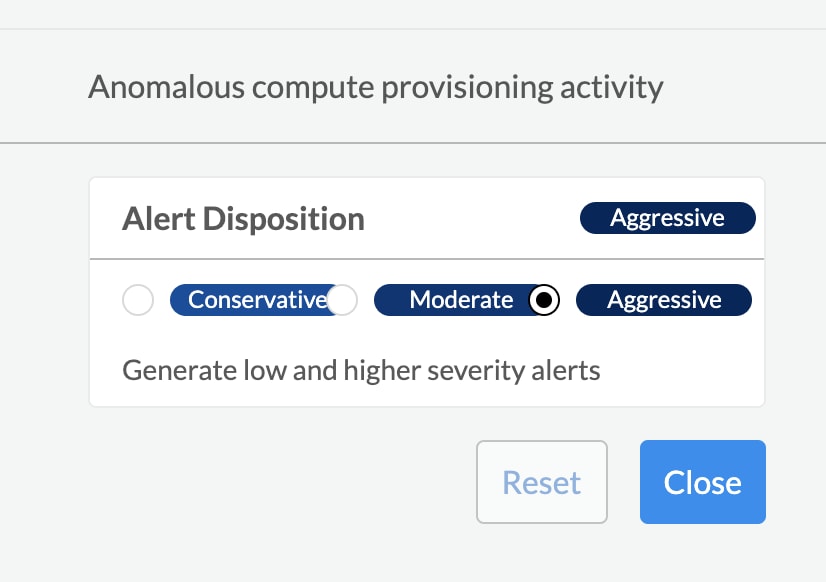
Prisma Cloud Threat Detection is powered by highly-customizable ML techniques and multiple threat intelligence sources. We understand that the threshold for suspicious activities varies across industries and organizations, so in addition to alert rules and trusted lists, customers can define the alert disposition for anomalous compute provisioning activity. The conservative setting only generates alerts for high severity incidents, moderate will alert for medium and higher severity alerts, and aggressive will generate them for low and high severity incidents.
Next Steps
Compute provisioning anomaly detection is available now and can be found in the Policies tab of the Prisma Cloud console.
With these enhanced threat detection capabilities, Prisma Cloud provides customers with some of the most comprehensive Cloud Security Posture Management (CSPM) capabilities in the industry. To learn more about operationalizing CSPM strategies, check out our white paper, Guide to CSPM Tools.