On December 7, 2023, Apache released an advisory regarding CVE-2023-50164, a critical vulnerability with a severity of 9.8 that affects Apache Struts 2. The affected versions are Struts 2.0.0 - Struts 2.3.37, Struts 2.5.0 - Struts 2.5.32, Struts 6.0.0 - Struts 6.3.0.
The vulnerability allows an attacker to manipulate file upload parameters to enable path traversal and upload a malicious file the attacker can then use to perform remote code execution (RCE), gaining full system control.
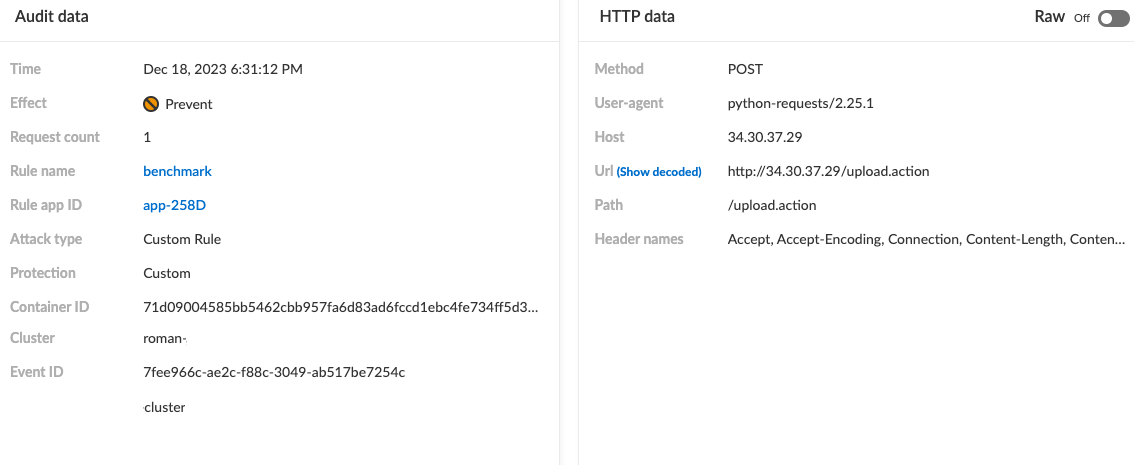
Users of Prisma Cloud’s WAAS utilizing custom rules are safeguarded from related threats by the recently released custom rule designed to detect exploitation attempts of the vulnerability.
A Closer Look at CVE-2023-50164
CVE-2023-50164 represents a critical vulnerability discovered within Apache Struts 2, an open-source framework for developing and building Java EE web applications. Apache Struts 2 is widely used in commercial and open-source projects, making this critical vulnerability a concern across industries — particularly in government, healthcare, and financial sectors.
Due to a path traversal flaw, CVE-2023-50164 could lead to an RCE if exploited. The flaw involves how Apache Struts 2 handles their file uploads to the endpoint upload.action.
By manipulating a file upload parameter, an attacker can effectively traverse the web server's directory structure without authorization and upload a malicious file, typically a Java Server Page (JSP) based shell, to unauthorized directories within the system.
Afterwards, the attacker can access the newly uploaded shell, triggering the execution of the malicious code, resulting in full control over the vulnerable server.
CVE-2023-50164’s Attack Vector
To carry out a successful attack, attackers need to find a web application that uses a vulnerable version of Apache Struts, in addition to finding the exact vulnerable file upload path.
An attacker would then send a malicious request to the file upload path, including a JSP-based webshell, while adding the path traversal payload to upload the malicious webshell into an unauthorized location in the system.
After the server receives and accepts the request, it will store the malicious webshell in an accessible directory that the attacker specified, enabling them to access the recently uploaded malicious webshell. From here, the attacker can utilize the webshell to execute any desirable code, effectively gaining complete control over the system.
CVE-2023-50164’s Potential Impact
Remote code execution is regarded as one of the most serious and critical threats an organization can encounter. A server susceptible to CVE-2023-50164 could grant the attacker full control of it, enabling the attacker to perform any action they desire, from stealing sensitive data to using the compromised server as a launchpad to infiltrate other machines within the network.
Mitigations
Apache has issued a security patch for this vulnerability, specifically in versions 6.3.0.2 and 2.5.33. We strongly recommend that our users promptly update their deployments to effectively secure their environments.
Learn More
If you haven’t tried Prisma Cloud, now’s the time. Experience the advantage with a free 30-day trial.