The FedRAMP Joint Advisory Board (JAB) has announced that Prisma Cloud has achieved FedRAMP High Impact Level Ready status.
Over the last few years, we’ve observed tremendous progress in cloud-native transformations across U.S. government agencies. As the demand for cloud computing accelerates, the cyber threat landscape becomes increasingly complex.
In 2021, Prisma Cloud became the industry’s first cloud-native application protection platform (CNAPP) to achieve Federal Risk and Authorization Management Program (FedRAMP) Moderate Authority to Operate (ATO). This achievement required Prisma Cloud to undergo rigorous auditing to prove it was fit to protect federal agencies.
Today, we are proud to announce that Prisma Cloud has been accepted by the Joint Advisory Board (JAB) and reached Ready status for FedRAMP High.
The JAB selects a limited number of cloud services offerings (CSOs) to sponsor each year, with each sponsorship acknowledging the CSO’s ability to deliver best-of-breed, consolidated security for the most critical cloud deployments.
The Need for Security Consolidation
Cloud has become the dominant compute model for organizations, including U.S. Federal Government agencies. According to The State of Cloud-Native Security 2023 Report, respondents reported that 53% of their workloads are hosted in the cloud.
In a second survey, Palo Alto Networks found that organizations rely on 30+ tools for overall security. Trying to secure rapidly changing cloud environments with myriad point tools creates complexity, elevated costs, and technical debt for security teams. Typical challenges faced by organizations working with siloed security tools include:
- Blind spots: Understanding risk in the cloud requires an automated correlation of broad data points — misconfigurations, excessive permissions, data risk, network exposure, vulnerabilities, and more. Point tools provide visibility into fragments of application risk and do not integrate for effective risk correlation.
- Alert fatigue: While security teams may receive thousands of alerts daily, only a handful require urgent action. Without context, though, security teams aren’t equipped to prioritize risks and must manually comb through each alert.
- Overburdened staff: Because disparate tools don’t talk to each other, security teams spend many cycles manually integrating products, which cuts into time needed to monitor threats.
Given that these challenges oppose security outcomes, organizations are moving towards consolidation. According to Gartner, “By 2026, 80% of enterprises will have consolidated security tooling for the life cycle protection of cloud-native applications.
U.S. Federal Government Agencies Are Taking Mission Critical Systems to the Cloud
The ubiquity of cloud-based IT systems across the federal government puts a spotlight on how critical government data with the highest national impact is stored, accessed, and analyzed. In view of the outsized impact of a breach, law enforcement and emergency services systems, financial systems, and health systems require stringent controls.
But government agencies face inefficiencies from independent capacity planning, as well as unused compute resources. Protecting cloud applications and elastic environments that aren't under their physical control presents agencies with new challenges — and new challenges demand new security processes and tools to learn, integrate, and operate.
In response to evolving threats and the imperative of national and economic security, the White House issued the Executive Order on Improving the Nation’s Cybersecurity (Executive Order 14028) in May of 2021 to establish standardized policies for the prevention, detection, assessment, and remediation of cyber incidents.
The Importance of FedRAMP
By establishing a common security framework, FedRAMP has enabled the government to accelerate the adoption of cloud computing, as agencies no longer need to conduct individual technology audits and can rely on transparent standards and processes for security authorizations.
Authorization Process
Achieving FedRAMP authorization involves three milestones: Ready, In Process, and Authorized. Organizations can pursue a FedRAMP authorization through one of two approaches — via the JAB or agency sponsorship. The JAB is the primary governing body for FedRAMP and includes representations from the Department of Defense (DoD), Department of Homeland Security (DHS), and General Services Administration (GSA).
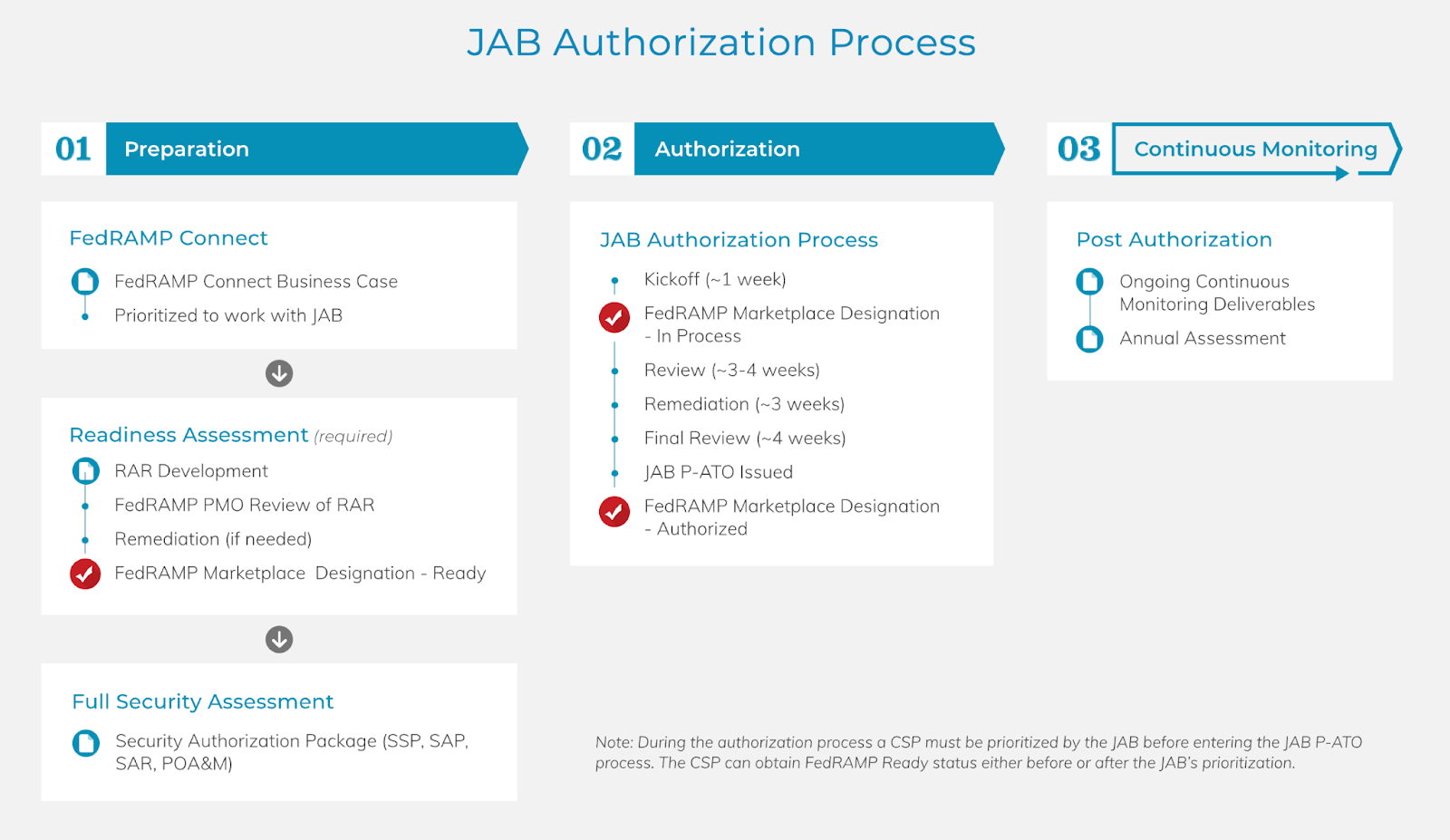
Levels of FedRAMP Authorizations
FedRAMP security categories are determined by the potential impact that adverse events could have on an organization’s ability to protect individuals, protect its assets, fulfill its legal obligations, and maintain its day-to-day functions.
Based on this impact potential, FedRAMP authorizations are graded low, moderate, and high, These levels align with NIST FIPS-199 Standards for Security Categorization of Federal Information and Information Systems, which provides the standards for categorizing information and information systems to ensure cloud service offerings (CSOs), or services, meet security requirements for the data processed, stored, and transmitted on public clouds.
Actualizing the Shared Responsibility Model
The shared responsibility model specifies that cloud service providers share responsibility with their customers when it comes to securing workloads hosted on their clouds. CSPs, for example, don’t have full control over everything users do on their clouds and can’t force customers to configure IAM policies in a secure way or make sure that they patch their applications against the latest vulnerabilities.
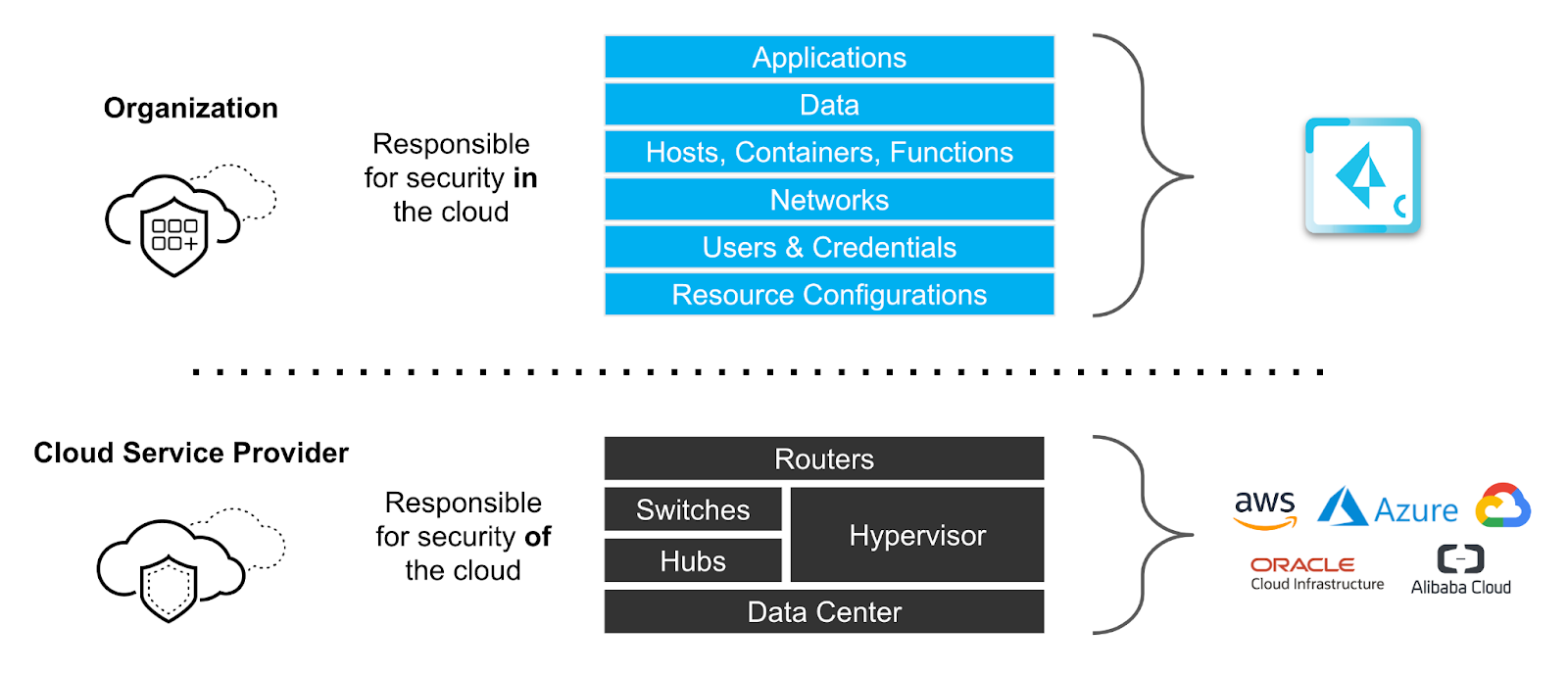
Likewise, organizations that use public clouds have limited control over their cloud infrastructure. They can’t monitor for vulnerabilities in a CSP’s servers or detect intrusions inside its network. Therefore, CSPs and their customers must share responsibility for security, with each party taking the lead in securing the resources it controls.
With recent U.S. executive orders and the impetus compelling agencies to enhance cybersecurity and software supply chain integrity, it has become paramount that government agencies adopt cloud-native security tools to protect their environments.
Prisma Cloud and FedRAMP
Prisma Cloud secures applications from code to cloud across multicloud environments, delivering comprehensive security with continuous visibility and proactive threat prevention, enabling security and DevOps teams to effectively collaborate to accelerate secure cloud-native application development and deployment.
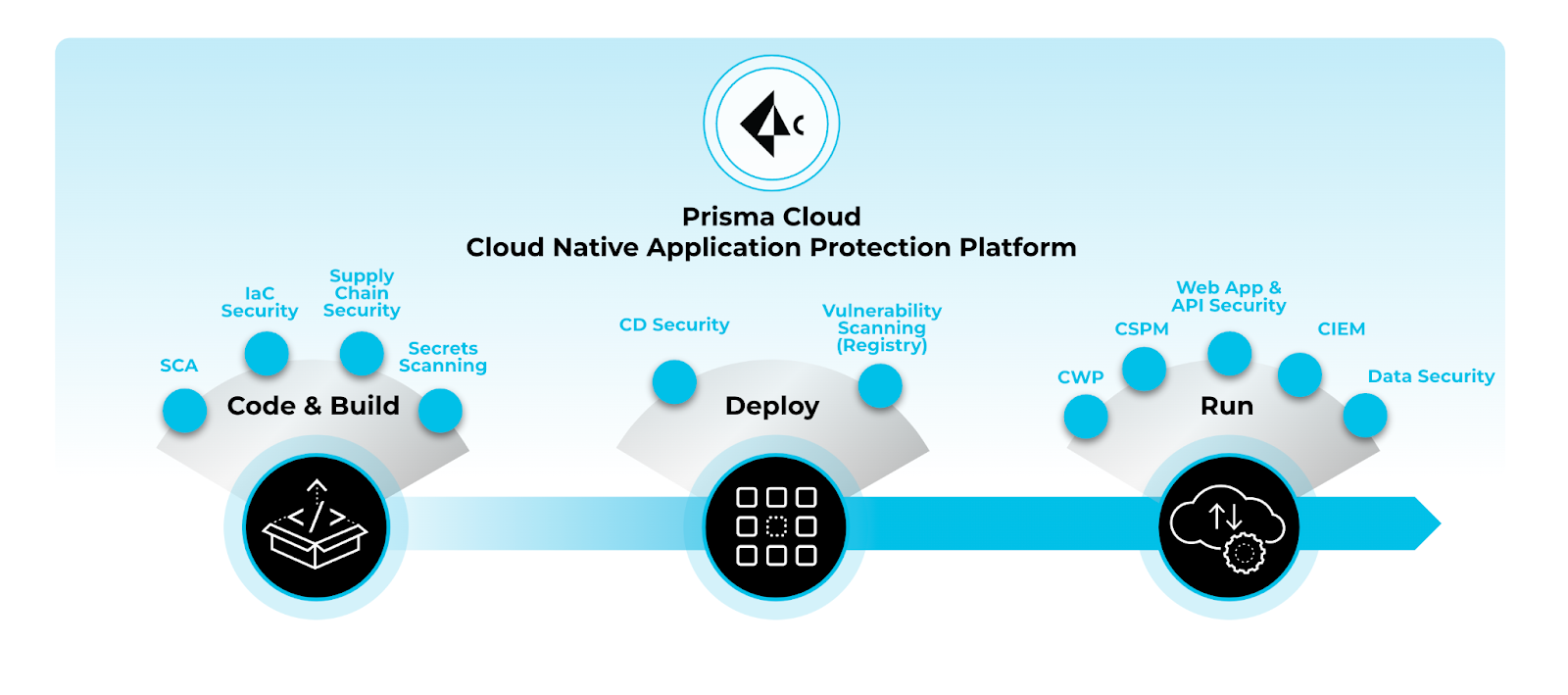
As illustrated below, Palo Alto Networks is actively working on raising the FedRAMP impact level for Prisma Cloud services from Moderate to High.
| Prisma Cloud Capability | ||
|---|---|---|
| Moderate Impact Level: Authorized |
High Impact Level: Ready |
|
| Cloud Security Posture Management | ✔ | ✔ |
| Cloud Infrastructure Entitlement Management | ✔ | ✔ |
| Cloud Workload Protection | ✔ | |
| Web Application & API Security | ✔ | |
| Code Security | ✔ | |
| Cloud Network Security | ✔ |
Table 1: Current FedRAMP status by capability
These CNAPP capabilities provide the public sector with the security foundations and workforce enablement, as outlined in the Federal CIOs Council’s Federal Cloud Computing Cloud Smart strategy.
The Cloud Smart strategy encourages agencies to take a risk-based approach to securing cloud environments. Agencies should ensure protections at the data layer — in addition to the network and physical infrastructure layers — transitioning to a multilayer defense strategy, otherwise known as defense-in-depth.
Prisma Cloud’s ability to secure applications from code to cloud, coupled with the assurance of FedRAMP, helps agencies apply security practices through the entire application lifecycle. By providing multicloud visibility and control through a common platform for your many stakeholders, Prisma Cloud fosters the enablement of your workforce’s capabilities.
Learn More
Palo Alto Networks looks forward to helping U.S. Government agencies secure their application from code to cloud. If you’d like to learn more, read the Prisma Cloud for Federal Datasheet.