Modern applications are more interconnected than ever with the delineations between each cloud-native code component – infrastructure as code (IaC), Kubernetes manifests, open source packages and container images. But the way most organizations approach cloud-native security is still siloed. Stitching point solutions together requires extensive resources and inevitably leaves coverage gaps.
Gartner estimates that “by 2025, 70% of organizations will consolidate the number of vendors securing the life cycle of cloud-native applications to a maximum of three vendors.” And code security solutions combined with posture management and runtime security are necessary for that consolidation to occur.
To help teams get code security that is as interconnected as the applications they need to protect, Prisma Cloud has added Software Composition Analysis (SCA) to its Cloud-Native Application Protection Platform (CNAPP). This addition builds on our foundational industry-leading IaC security capabilities, creating the first context-aware SCA solution that is able to bring the context of the infrastructure into securing the application.
The Need for Open Source Security Is Greater Than Ever
For modern development teams, open source software (OSS) is essential to building applications modularly and shipping features fast. But with a 10% year-over-year increase of open source vulnerabilities reported as found by Forrester, it’s also the first place attackers start when they’re looking for a way in. The constant threat of vulnerabilities and persistence of OSS, coupled with the rising complexity of cloud-native applications, has made this a challenging problem to solve.
Last year we witnessed our customers scramble to determine if and how they were affected by Log4Shell, both across their stacks and at different phases of the development cycle. Unfortunately, because modern applications are so complex and open source software is so dependency-driven, this was much harder than it should have been. And it remains a problem to this day, with an estimated 30% of vulnerable Apache Log4j instances in the wild left unpatched.
Existing Approaches to Eliminate Open Source Risk Fall Short
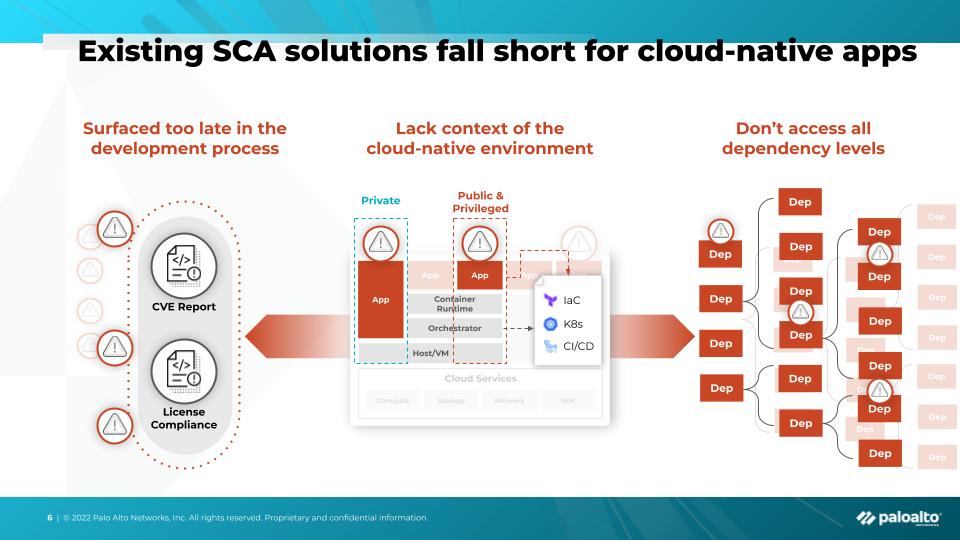
Open source risk is by no means a new challenge, but many SCA solutions still aren’t equipped to handle the interconnectedness and complexity of cloud-native applications. Many traditional solutions surface vulnerabilities and license compliance issues too late, resulting in resource-intensive remediation processes that can leave vulnerabilities exposed for too long.
Newer developer-friendly software composition analysis tools focus on shifting that process earlier in the application lifecycle. But with disparate application and infrastructure security point tools, it’s challenging to accurately prioritize risk based on the context of the broader cloud-native environment. And even if teams are able to sift through security findings and prioritize issues, they may still have an incomplete view of their open source risks because most SCA solutions lack the depth of scanning to completely uncover all open source risks at even the deepest dependency layer.
Prisma Cloud Software Composition Analysis
Prisma Cloud Software Composition Analysis leverages proprietary threat research and the most trusted vulnerability databases, supports the popular open source package managers and languages and provides granular version bump fixes to enable developers to implement changes safely. This depth of coverage, paired with Prisma Cloud’s existing breadth of developer and DevOps integrations, makes our SCA solution one of the most accurate and comprehensive on the market.
Infrastructure-Aware Approach
By bringing the worlds of IaC and open source security together in a Code-to-Cloud CNAPP, Prisma Cloud not only helps organizations consolidate solutions but also uniquely provides the context of vulnerabilities within the broader cloud-native environment. This connection allows organizations to identify vulnerabilities embedded in container dependencies and helps them prioritize and address vulnerabilities faster.
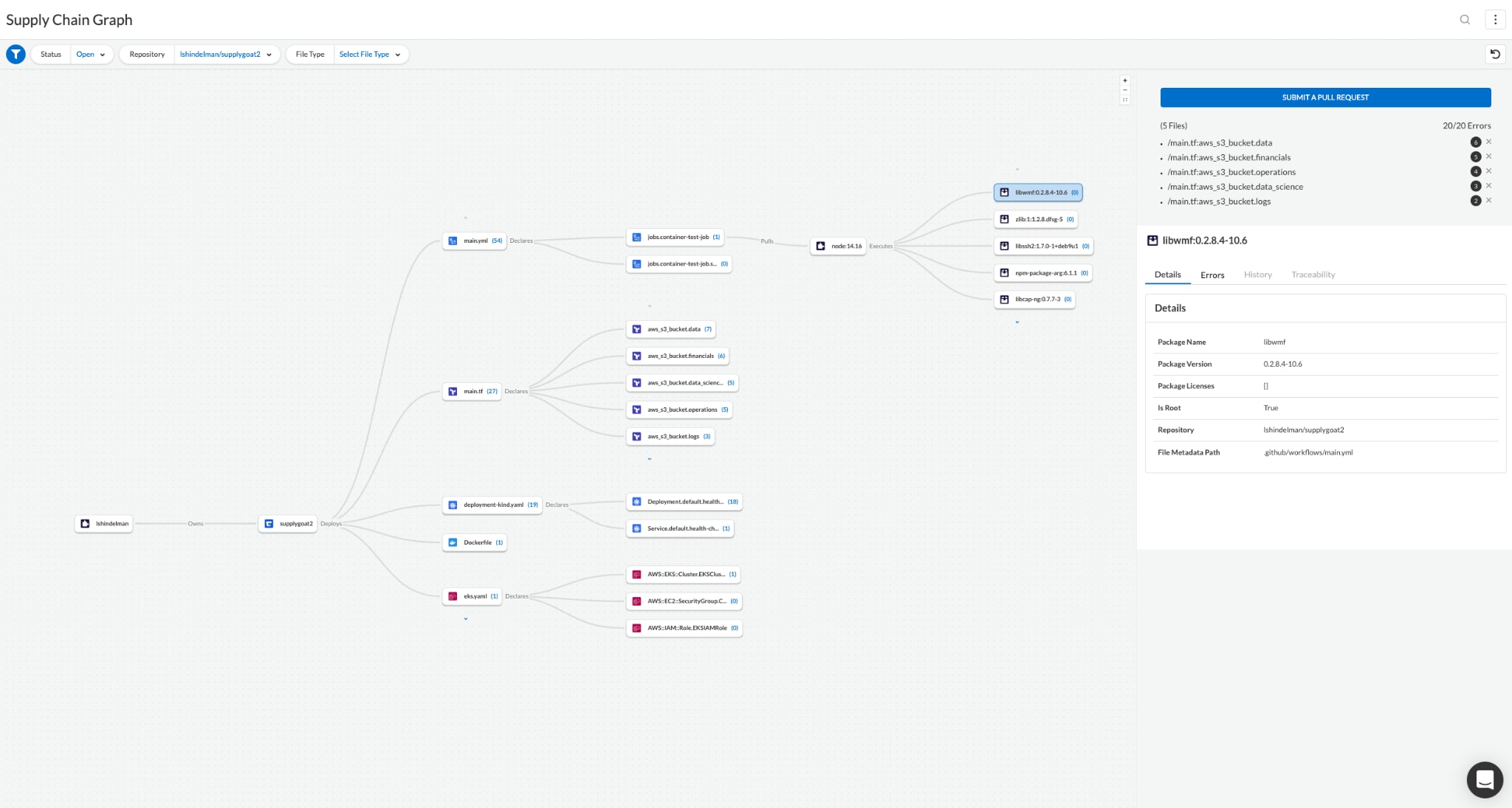
In addition to SCA, Prisma Cloud now also supports consolidated software bill of materials (SBOM) generation, which includes both IaC resources and open source packages, along with their associated misconfigurations, vulnerabilities and licenses.
Developer-First Integrations
Prisma Cloud Software Composition Analysis leverages existing integrations and experience to surface feedback as early as possible, providing vital intel to developers directly within the tools and workflows they depend on.
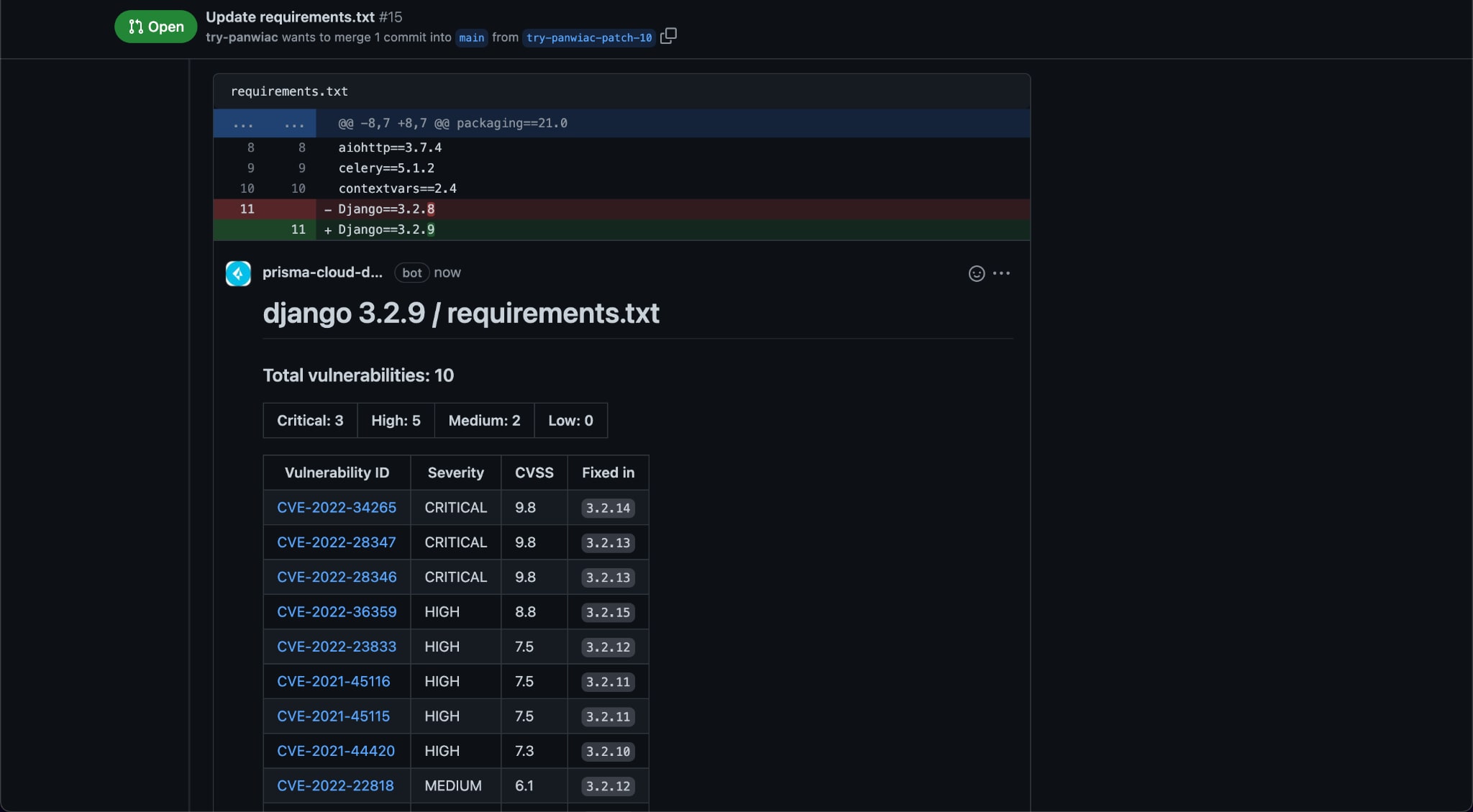
By leveraging Checkov, Prisma Cloud’s open source CLI tool, or integrated development environment (IDE) plugins, developers get notified of vulnerabilities as they bring OSS into their codebase. Additionally, as open source code makes its way into the build phase, Prisma Cloud surfaces feedback in version control systems (VCS) in the form of pull/merge request guardrails and comments, as well as build steps within CI/CD pipelines.
Limitless Dependency Scanning
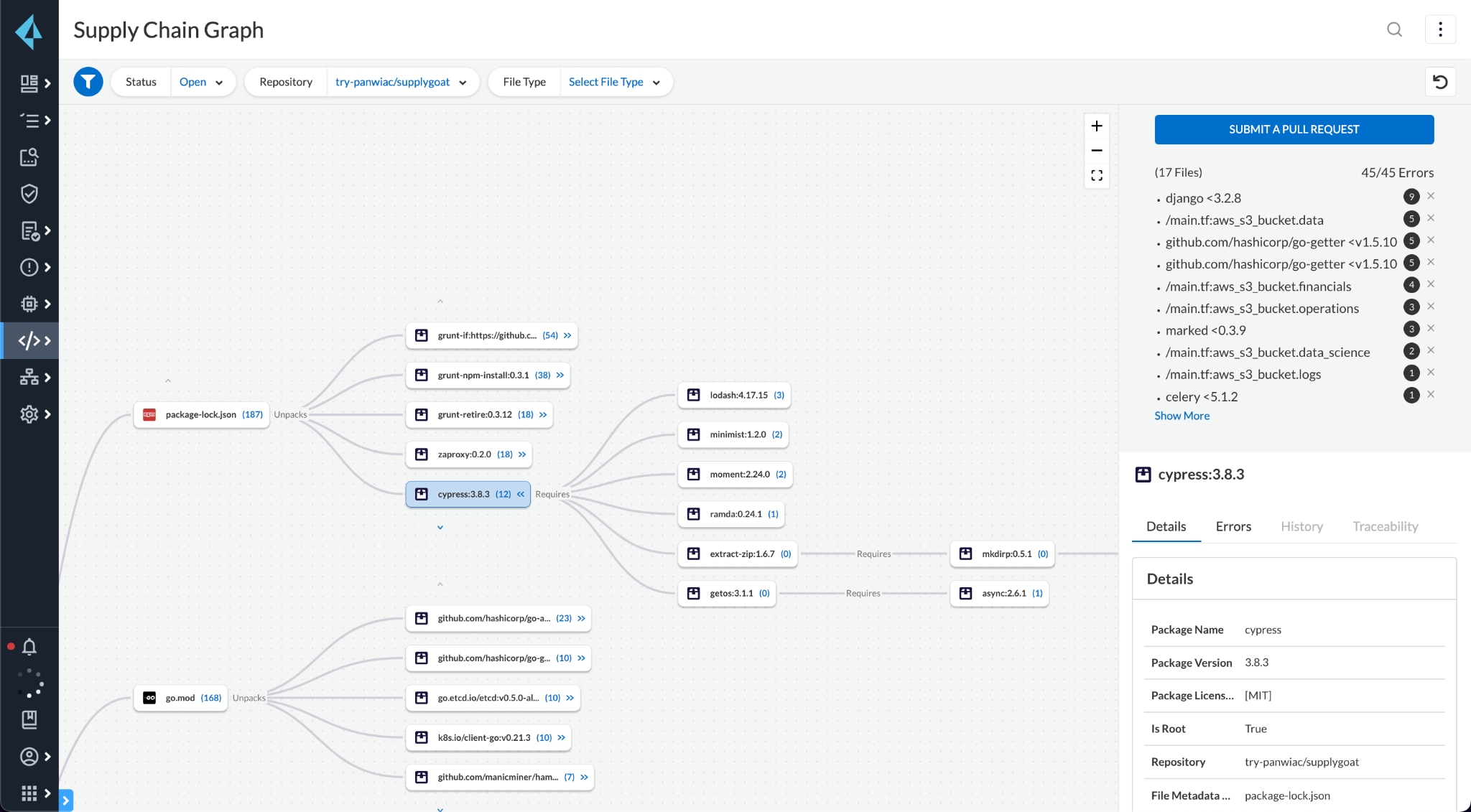
OSS is incredibly dependency-driven and each package version may change critical functionality, so without complete visibility or guidance throughout dependency trees, vulnerabilities go undetected or unfixed. By fully extrapolating dependency trees and providing granular version bump fix suggestions at all layers, Prisma Cloud provides deep open source coverage.
Code-to-Cloud CNAPP
The only way to ensure complete coverage when securing cloud-native applications is to scan for vulnerabilities at each step of the development lifecycle. SCA is just one component of the Prisma Cloud CNAPP solution, which secures applications and infrastructure from code to cloud. With Prisma Cloud, the same intelligence stream used to identify vulnerabilities in repositories continuously identifies vulnerabilities in registries and at runtime, providing consistent and accurate visibility into the vulnerabilities in your environment.
While Prisma Cloud provides actionable guidance directly to developers to improve remediation rates, unpatched and zero-day vulnerabilities are inevitable. To address this challenge and provide complete coverage, Prisma Cloud includes web application and API security (WAAS) and agents, both of which identify and protect applications from exploit attempts. By leveraging these integrated capabilities, Prisma Cloud customers can track and secure vulnerabilities from code to cloud.
Conclusion
With its proactive and integrated approach to addressing open source vulnerabilities and license compliance issues, Prisma Cloud SCA gives developers the actionable insight they need to leverage only secure and compliant packages and gives security teams the guardrails they need to consistently enforce policies.
To learn more about Prisma Cloud’s approach to SCA and see it in action, register for our upcoming Meet the Experts live session.