Infrastructure-as-Code, abbreviated IaC, refers to the practice of quickly, easily, and automatically provisioning cloud infrastructure using declarative templates during deployments. The use of IaC templates, the blueprints used to deploy and manage cloud infrastructure, is steadily on the rise. According to Gartner, “By 2023, 60% of organizations will use infrastructure automation tools as part of their DevOps toolchains, improving application deployment efficiency by 25%.”
At Palo Alto Networks, we see Prisma Cloud users regularly provisioning infrastructure with templates like Hashicorp Terraform, Amazon Web Services (AWS) CloudFormation, Microsoft Azure Resource Manager (ARM) or Kubernetes app manifests.
Because it is becoming an important part of cloud native development, our latest Prisma Cloud release further simplifies IaC visibility and policy management with our DevOps Asset Inventory dashboard.
Potential Risks with Infrastructure-as-Code
Whether you are provisioning infrastructure manually or via automation with IaC, you need to ensure that resources are configured securely and cloud infrastructure meets your internal security and compliance requirements.
The Palo Alto Networks Unit 42 Research Team has regularly shared findings in their bi-annual Cloud Threat Report. In 2020, Unit42 disclosed risks with IaC:
- Nearly 200K insecure IaC templates were in use
- 42% of CloudFormation templates (CFT) contain at least one insecure configuration
- 22% of all Terraform configuration files contained at least one insecure configuration.
In order to address these risks, Prisma Cloud allows DevOps and security teams to embed security across the application lifecycle with functionality sets that increase visibility and control over IaC templates – as well as hosts, container images or functions.
DevOps Asset Inventory to Centralize Control Over IaC
In our latest Prisma Cloud release, we’re centralizing visibility and policy management for IaC with our DevOps Asset Inventory UI. This new dashboard displays a comprehensive view of all IaC scans sourced from Prisma Cloud DevOps plugins, expanding existing shift-left security capabilities.
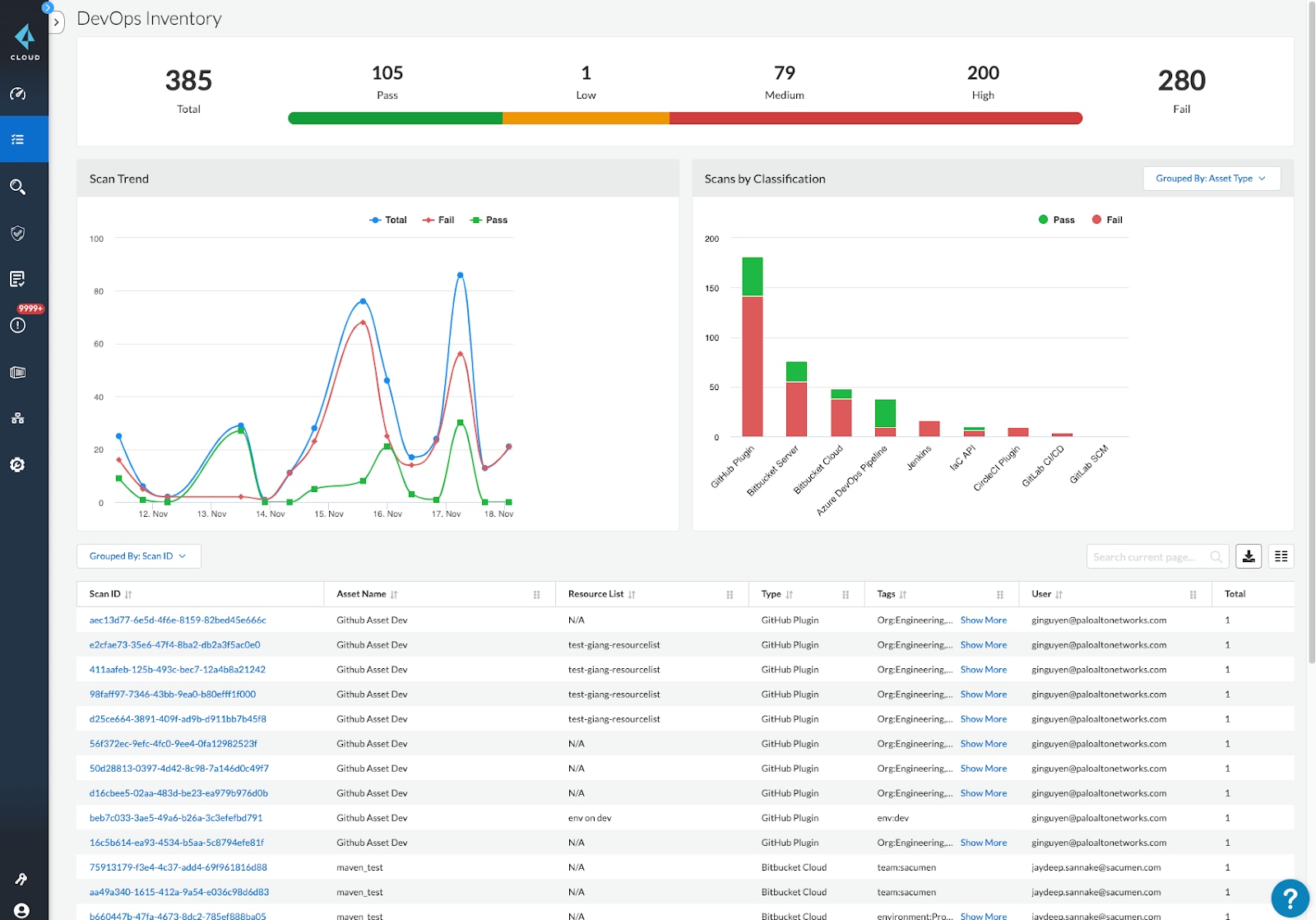
Prisma Cloud also surfaces all IaC scans and the corresponding results of each scan with a pass or fail status based on your desired policies. Additionally, any scan can be expanded to see specific details like severity, location and type of violation, as highlighted below. This helps security teams to quickly filter out IaC scans happening for production workloads or IaC scan results related with specific projects. And, Prisma Cloud roles can be configured to view specific IaC results in DevOps Asset Inventory based on cloud tags associated with projects, teams or other criteria.
We have also introduced new “build alert rules” in Prisma Cloud so that security teams can configure specific policies during IaC scans based on specific projects or compliance standards.
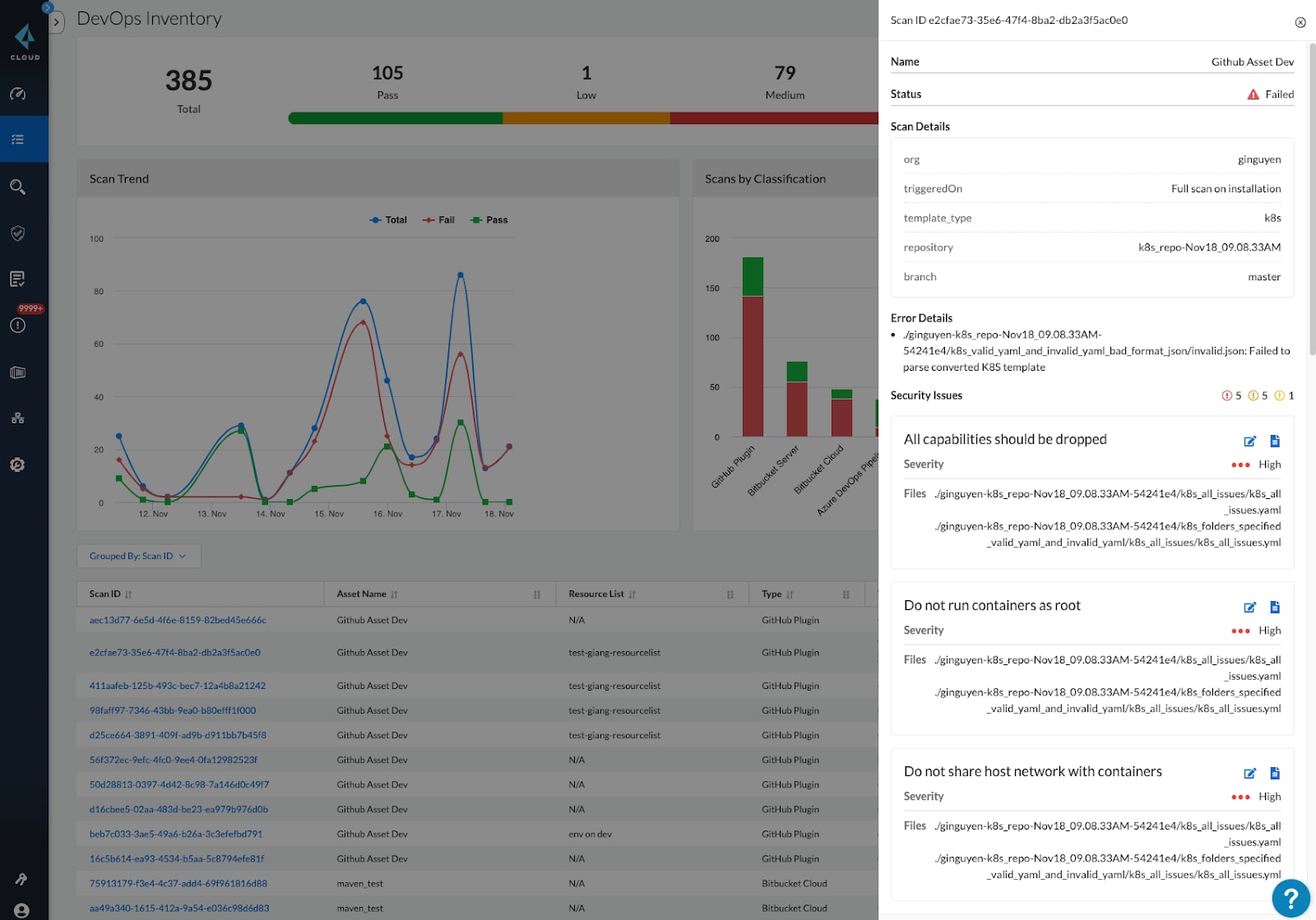
The screenshot above shows scan results for a Kubernetes YAML file sourced from GitHub. The scan returned five high-severity issues, as well as other medium and low-severity issues, such as containers running as root and containers that share the host network.
In order to address these issues, users can expand the details further to see the exact location and code snippet for remediation. Most importantly, all the scan results can also be shown directly within native development tooling, like GitHub, to help developers and DevOps teams quickly fix high-priority issues.
Shifting Security Left Across the Cloud Native Application Lifecycle
The latest enhancements to Prisma Cloud build on powerful capabilities for shift-left security, allowing organizations to identify and fix vulnerabilities or misconfigurations earlier in the development lifecycle. The net effect helps improve the overall level of security in production and reduces costs.
If you haven't taken advantage, get started with IaC scanning by installing and configuring the appropriate scan plugin or extension for your DevOps tool to start identifying issues in your IaC templates.
To learn more about other capabilities from Prisma Cloud, check out our other related blogs: