As organizations’ attack surfaces continue to grow, we’ve seen that traditional vulnerability testing is insufficient to secure an organization’s externally-facing assets. Conventional vulnerability management (VM) tools lack a comprehensive inventory of known and unknown external assets. This means that external vulnerability testing is incomplete as well as manual and infrequent.
Introducing Cortex Xpanse Attack Surfacing Testing
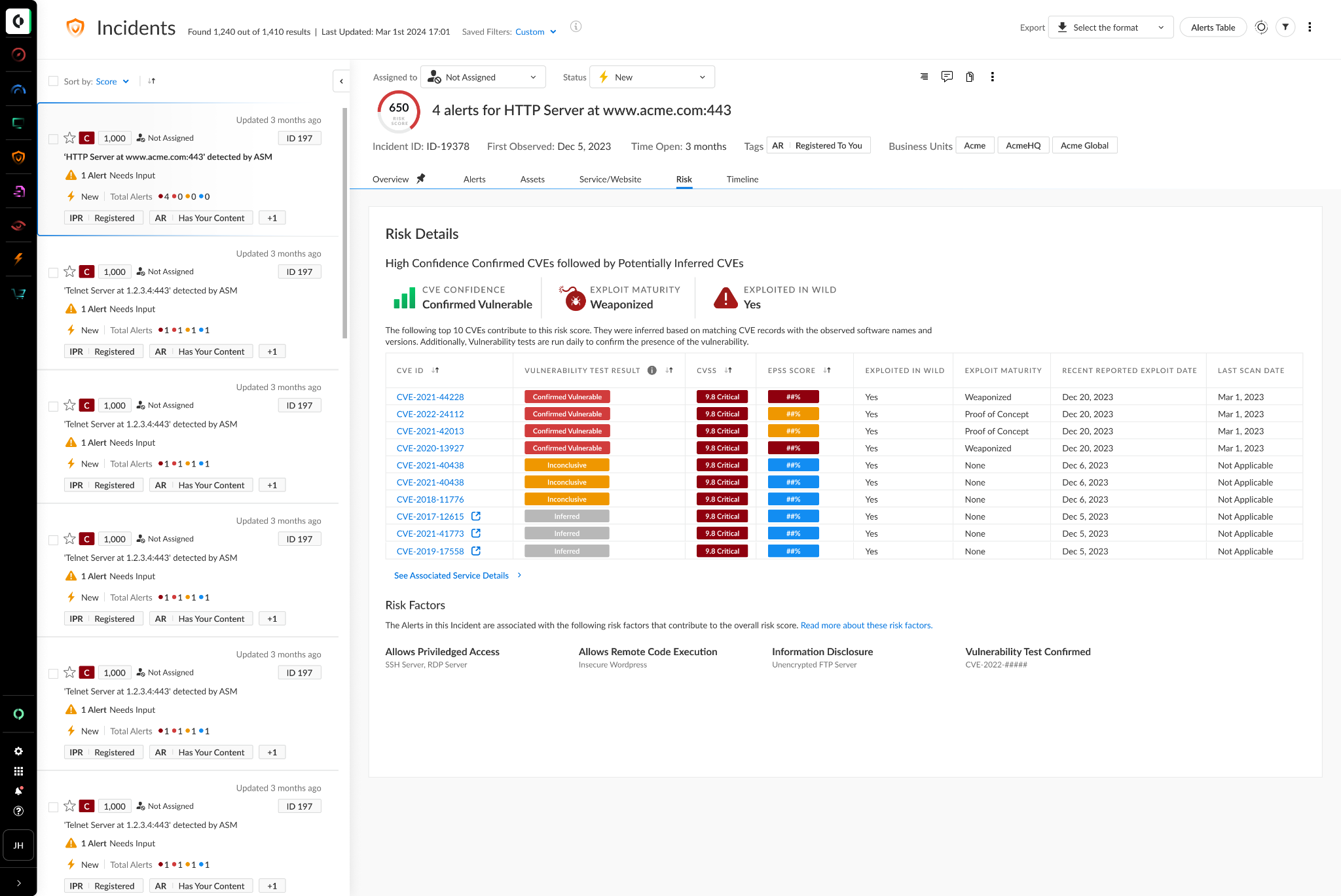
To address this challenge, Cortex Xpanse has introduced Attack Surface Testing (AST), which runs unintrusive, benign exploits with explicit user authorization to confirm vulnerabilities in an organization's services.
Unlike traditional vulnerability management tools, AST performs daily scans against an automatically updated list of external organization-owned assets for comprehensive coverage. Its sophisticated scanning methods prevent network congestion, and its targeted testing approach enables organizations to prioritize vulnerabilities more effectively.
How Does It Work?
Cortex Xpanse Attack Surface Testing can be configured to run on all Xpanse-discovered assets or customer-defined subsets. It conducts targeted tests based on service type, reducing the likelihood of service degradation due to testing and significantly improving scanning cadence and coverage. It can be easily configured from your Xpanse instance, without the need for any devices or agents. confirmed vulnerabilities do not open new alerts or incidents, and results are integrated with Xpanse’s best-in-class incident prioritization workflows to aid in efficient remediation using our Active Response Module.
Benefits of Attack Surface Testing
- Enhanced scan frequency and coverage: AST can be configured to scan newly discovered customer-owned assets as they appear. Xpanse AST's daily scans considerably improve an organization's attack surface scanning cadence.
- Service-specific testing: AST conducts targeted tests based on service type, reducing service disruptions and network issues caused by spray-and-pray testing methods.
- Confident prioritization: Xpanse prioritizes actively tested vulnerabilities and provides users with a 14-day history of evidence payloads so that your team can pursue remediation with confidence.
Attack Surface Testing is a part of the Xpanse 2.5 release, which will become generally available to all customers starting April 14th, 2024. This release also includes additional features and capabilities to help you manage your attack surface more efficiently.
What's New in Xpanse 2.5?
- Respond flexibly to risks with Active Response Enhancement: Cortex Xpanse now supports endpoint-based mitigation playbooks on several ASM alert types, giving you more flexibility in addressing internet-exposed risks.
- Investigate incidents faster with comprehensive information in redesigned Service Details: The revamped service details page offers a single point of access to all incidents, alerts, websites, and assets related to a service, as well as attack surface test results or inferred CVE intelligence.
- Improve your SOC workflow with our new integrations: Seamlessly connect your attack surface data with Rapid7 InsightVM, ServiceNow CMDB, and QRadar for correlation, alerting, and additional scanning.
For a complete list of the new capabilities and features, please see the Cortex Xpanse 2.5 Release Notes.
Organizations can respond to threats at machine speed with comprehensive discovery, dynamic assessment, and automation-first remediation capabilities provided by Xpanse. Xpanse has helped several organizations to shrink and secure their constantly growing attack surface.
To learn more about attack surface management, please read Expander from Cortex Xpanse.
1 Go SSH Scanner,” GreyNoise, last accessed March 13, 2024.,