EDR Security Evolves
An evolution is happening in the cybersecurity industry. Even as our workforce is becoming more and more distributed, our security architecture is unifying into a single security analytics capability for endpoint threat detection and response. Extended detection and response (XDR) is at the center of this shift, providing centralized visibility across your various security data sources. Security teams who are investing in managed detection and response tools must consider XDR in their evaluations, as XDR delivers all the capabilities of traditional endpoint detection and response (EDR) security, but with superior extensibility and analytics to meet the needs of the future.
XDR is an Extension of EDR Capabilities
To tell the story of XDR, we must begin with traditional EDR solutions because it is the foundation from which we are extending. EDR capabilities are a critical precursor to an XDR solution because there is no better way to detect an intrusion than by monitoring the actual target environment being attacked, and the telemetry collected by EDR forms the basis of triage and investigation. You simply cannot have a marketable XDR solution if you don’t have best-in-class EDR capabilities. That said, 10-20% of any organization’s laptops and workstations are not under management, so as great as EDR is, it’s only situationally useful. Let’s take a look at how XDR improves upon this situation.
Cloud Workloads Require a Different Type of Endpoint Monitoring
An endpoint is traditionally understood to be end user computing devices such as a laptop or workstation. Unfortunately, this ignores another important endpoint if we’re to view network communication using the middle-school definition of a line segment, connecting two endpoints. As cloud technologies such as containers and serverless become more prevalent, it’s essential that we be able to monitor these endpoints with the same confidence we have in our end user computing environment. This critical next step toward a full-fledged XDR product enables a unified view across the endpoints within your environment, regardless of system function.
Network Telemetry Connects the XDR Environment
Network telemetry serves three critical functions in an XDR environment:
- Detecting compromise of unmanaged assets.
- Providing application-layer anomaly detection where some attacks may never compromise the system itself.
- Correlating events across systems to enable triage of alerts as a single incident across your environment.
While the first two objectives are advantages of having a network detection and response (NDR) solution, only by leveraging XDR can you accomplish the third to greatly reduce not only the frequency of alerts but the time to triage and investigate them.
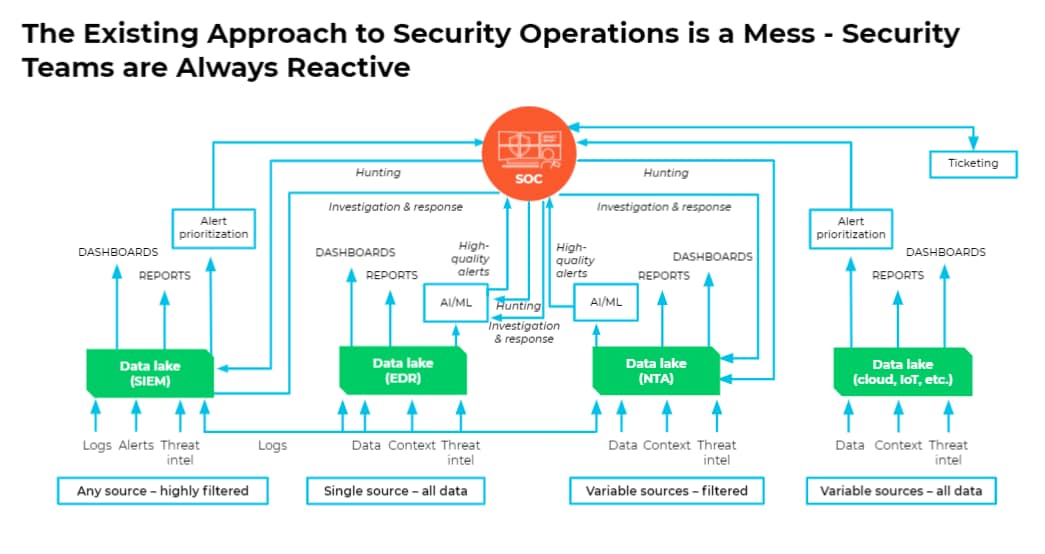
Update Your Endpoint Detection and Response Solution
XDR security extends all the benefits you expect from a traditional endpoint solutions product by further stitching together telemetry from non-endpoint sources to provide better detection and a bigger picture of what’s going on in your environment for your security operations team.
Organizations without XDR invest tons of time and money sending traditional EDR data into their SIEM in an attempt to achieve the same benefits an XDR solution will give you out of the box. Don’t invest in the last generation of endpoint security products with traditional EDR, extend your team by unifying your threat detection capabilities with XDR.
The evolution of endpoint security has progressed from antivirus software to endpoint protection (with endpoint security policies and modules), then EDR (next-gen endpoint which detects and contains security incidents and restores hosts to pre-attack condition), and now XDR which provides cross-data analytics and insights.
With a strong focus on prevention, Cortex XDR provides an integrated platform for cross-data prevention, detection and response:
- Prevent all you can, including sophisticated, zero-day threats.
- Detect with cross-data analytics running on the industry’s most comprehensive
security data asset. - Deliver lightning-fast investigations through cross-data visibility and insights.
- Respond to the entire security infrastructure.
Learn More About EDR Security and How It Is Evolving
Download our on-demand webinar featuring a candid discussion with Palo Alto Networks field CTO and former Forrester analyst Josh Zelonis as he presents the case for moving to XDR today:
Watch On-Demand Now: “Moving Beyond Traditional EDR-How XDR is reshaping SOC Operations”