Through the annals of literature, music and scientific explorations, we have witnessed iconic dynamic duos who combined their unique strengths and talents to achieve great accomplishments. Sherlock Holmes and Dr Watson, Batman and Robin, Mario and Luigi, to name a few.
So with a bit of tongue in cheek, we offer you the “dynamic duo” XDR and XSOAR automation pack that leverages XDR’s extended endpoint threat detection and response, with the workflow automation and orchestration capabilities of XSOAR. Let’s talk a bit about why this combination is so compelling for the SOC, and especially so when combined with the recent addition of the XQL engine.
What’s the XQL engine?
On October 14th, 2021 we enhanced the Palo Alto Networks Cortex XDR - Investigation and Response pack with the ability to leverage the XQL search capability available within Cortex XDR. The XDR Query Language enables analysts to search vast amounts of data that XDR collects across your endpoints and cloud systems to support security investigations and security hunts. Combining the XDR Query engine with XSOAR enables organizations to automate these advanced investigations quickly confirm threats in their environment.
Example
An important step in a malware investigation is to understand if an unfamiliar piece of software exists elsewhere in the organization. This could confirm process rarity or if the software has already been confirmed as malicious or unwanted, what other endpoints in the organization have this software? This expands the scope of an incident beyond the original endpoint that reported it to addressing it for the entire organization.
Leveraging the XQL Engine integration, you could generate a hash of the file (SHA-256), search for it in the environment, and return a list of hosts that have the file. From this point you could decide how to address the issue: kill the process if it is running, isolate the hosts, get approval, or other response actions. When running the search command, you would pass the following search string to ‘xdr-xql-generic-query’ command
|
dataset = xdr_data | filter event_type = FILE and action_file_sha256 in(“7e282327c69f48368d6954b1821e7dd40354a4fce26e95dd696c1005f6”) | fields agent_hostname, agent_ip_addresses, agent_id, action_file_path, action_file_sha256, actor_process_file_create_time |
Sample XQL : Search for a specific file based on hash
So with all this build up, what exactly does the Palo Alto Networks Cortex XDR - Investigation and Response pack do?
With this pack, you can automate multiple scenarios such as: malware investigation, malware response, threat intelligence (IOC) synchronization, deal with threats performing network service discovery, handle out-of-policy endpoints with connected external storage devices or disconnected endpoints, and more.
-
Enhanced threat detection with IOC synchronization
The Cortex XDR IOC integration as provided in the Palo Alto Networks Cortex - Investigation and Response pack enables you to operationalize your threat intelligence feeds and also ensure your detection and response controls are leveraging the threat Intel feeds you’ve purchased. If you have multiple threat intel feeds, you can use XSOAR to push your IOCs to XDR to enable better threat detection to answer questions such as: Is there a known bad file? Is an endpoint sending traffic to known malicious infrastructure? This can be configured using the “Cortex XDR - IOC” integration.
-
Automate reconnaissance or lateral movement detection
Network Service scanning is a common tactic that adversaries use to discover what assets exist on a network, any potential vulnerabilities, and potentially exploitable infrastructures. Use the Cortex XDR - Port Scan automation to enrich the detections from XDR, compare against known whitelists and appropriately defend against the reconnaissance.
-
Key incident response actions exposed via integration
The primary integration included in the Palo Alto Networks Cortex - Investigation and Response pack, includes a host of commands and actions that can be performed by the analyst within XSOAR in real-time or embedded as a task in an playbook.
Core response actions
The XDR and XSOAR automation pack supports the typical actions you would likely take in response to a malware execution. These actions are included in subplaybooks and exposed directly as commands (for example ‘xdr-blacklist-files'):
-
-
-
- Block File
- Delete File
- Kill Process
- Isolate Host
- UnIsolate Host
- Quarantine File
-
-
Advanced investigation and response actions
For full control in investigating and responding to security threats, you can build playbooks that will initiate commands as if an analyst was actually performing actions on the target operating system. These commands could include modifying files, triggering applications, etc. Click here to see XDR documentation on Interactive Mode.
- Interactive Shell Execution
- Script Execution
-
Malware investigation & response (aka “Incident Handler”)
You can automate key malware investigation steps including threat intelligence enrichment, automatic fetching of potential malicious files and delivering said file to your sandbox platform for detonation. This playbook also includes steps to search for indicators across your Palo Alto Networks product stack. Your part as an analyst will just be to decide if the alert is a true positive and approve core playbooks response actions such as file blocking.
-
Proactive scanning for dormant malware
This is an interesting topic that is not often mentioned. Sometimes malware threats lay dormant within a company’s environment waiting for specific conditions to execute (a specific time or possibly for the infected endpoint to connect to the company’s internal VPN). Included in the Cortex XDR pack is the ability to initiate malware scans to identify these “ticking time bomb” threats. Here is supporting documentation on XDR scanning.
-
Endpoint hygiene for better device control
USBs and external storage devices pose multiple risks to an organization including exfiltration risk and as malware attack entry points. When these hygiene issues are detected, automate the response and exception process with the end-user. Monitor the endpoints in the state with the included dashboards in the content pack.
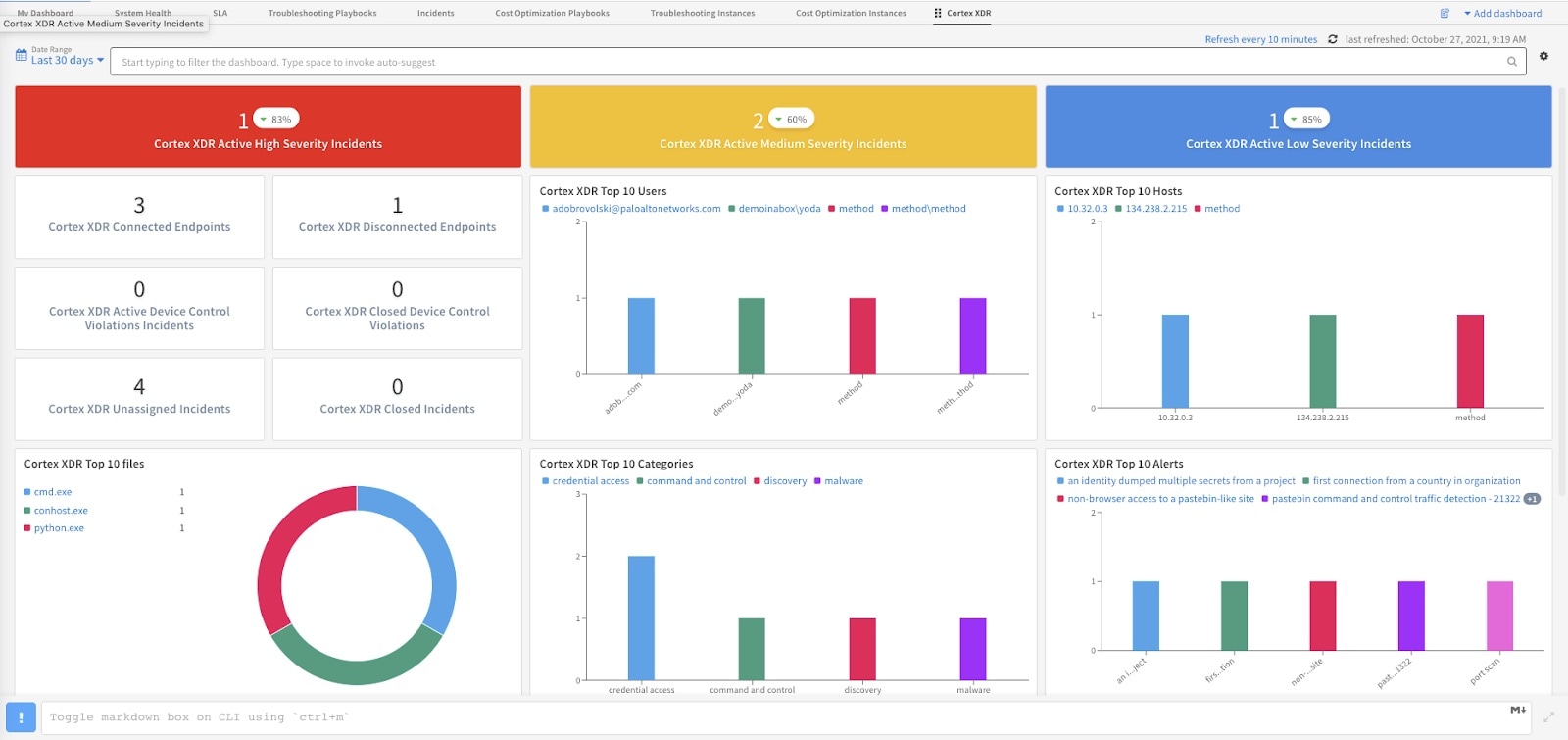
Included Cortex Dashboard
-
Monitor & automate the process for disconnected endpoints
Periodically, end users take their endpoints offline for extended periods of time. This poses a risk to the organization since the endpoint agent may not be up to date with the latest threat detections and this becomes a blind spot for the security team. Our out-of-the-box dashboards make it easy to monitor these endpoints and the playbooks can automatically engage end-users to reconnect the endpoint.
-
Deep linking to XDR alerts for improved usability
Sometimes you cannot fully investigate or respond to an alert from the XSOAR platform. Included in the pack as a pre-built incident layout, is the ability to click an alert from within XSOAR and jump to the alert you are investigating.
-
Incident mirroring for real-time updates
As incidents are investigated, enriched, confirmed, and ultimately closed, incident mirroring ensures that everything stays in-sync.
-
XDR alert aggregation & rollup
XDR produces multiple alerts and separate events that breakout the various aspects of a specific threat. The Cortex XDR pack will automatically group these separate alerts into a single incident within XSOAR and enable the analyst to see the individual items within the incident. This step is often needed for automations that work with SIEM or Data Lake platforms.
-
Investigation & response for targeted risks
Out-of-the-box playbooks are included to address specific vulnerabilities such as [CVE-2021-1675 LPE] and [CVE-2021-34527 RCE]: PrintNightmare.
-
Mitre ATT&CK mapping
Map your XDR alerts to Mitre ATT&CK to inform your prioritization and workflow. Dashboard widgets will display alerts & activities based on Mitre mapping.
Intrigued? Want to know more about the XDR and XSOAR automation pack? Go check it out for yourself! Download our free 30-day trial of Cortex XSOAR and you can find the Palo Alto Networks Cortex XDR - Investigation and Response pack in the XSOAR Marketplace.