Getting the Most Out of Your Threat Feeds
How confident are you in tracking and assessing the threat actors that stalk your enterprise? Despite the millions of threat indicators that come in daily, SecOps rarely get the most visibility out of their enterprise's threat intelligence investments. Furthermore, the variance in quality and manual processing of these threat intelligence feeds inhibits the rapid identification of malicious indicators impacting your organization.
Integrating these feeds with your incident response workflow allows you to map external threat data to what's happening within your enterprise's network. By automating responses to the hundreds of thousands of threat indicators, Cortex XSOAR helps your analysts stay a step ahead of the game in today's threat detection.
SecOps should consider a few crucial questions when ingesting each threat indicator:
- How bad is it?
- Who is using this IP Address?
- Who is behind it?
- Which policy is blocking this IP address?
The XSOAR Marketplace supplies content packs on threat intelligence management (TIM) that help make threat indicators actionable via automated playbooks. The TIM - Indicator Auto-Processing Content Pack includes playbooks that operationalize the processing of indicators for many use cases, such as tagging, checking for existence in various exclusion or other lists of interest, running enrichment for specific indicators, and preparing indicators for a manual review in case additional approval is required.
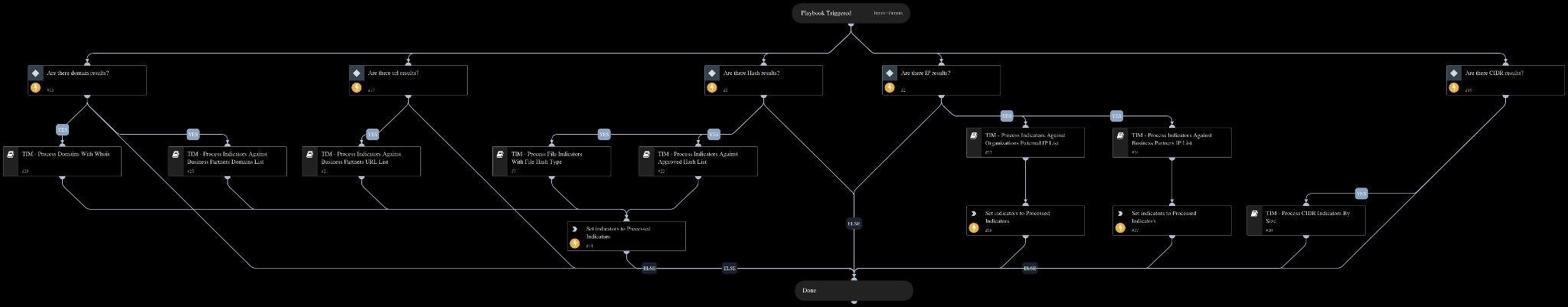
For example, there are playbooks to automate searching for enterprise-relevant IOCs by processing indicators to check if they exist in a Cortex XSOAR list, which contains the business partner domains or IP addresses. These playbooks help you quickly separate indicators relevant to your organization from irrelevant ones. Furthermore, the TIM - Process Indicators - Manual Review playbook automatically selects IOCs ingested by feeds that require manual approval. It optionally concludes by creating a new incident that includes all indicators needed for analyst review.
What does the TIM - Indicator Auto-Processing pack do?
With this content pack, you can significantly reduce the time your threat intelligence analysts spend on reviewing hundreds of thousands of indicators by performing many pre-defined logics and processing tasks automatically. The TIM - Indicator Auto-Processing Pack is one of many solutions available for download on the Cortex XSOAR Marketplace to help you automate repetitive tasks associated with the handling of indicators and threat intelligence management, including:
- Checking if indicators are related to internal exclusion lists such as business partners or other approved origin.
- Validating CIDR indicator size in order not to approve or deny large CIDR ranges.
- Creating incidents for indicators that require additional analyst review and chain of approval.
- Running additional enrichment for indicators ingested by specific feeds.
- Checking Whois to validate domains registrant and time of creation.
- Checking if an indicator with a tag of organizational_external_ip has been updated and keeps or removes the tag according to the results.
- Processing indicators against IP and CIDR lists.
For more information on the TIM - Indicator Auto-Processing Pack and other XSOAR packs and playbooks, visit our Cortex XSOAR Developer Docs reference page.
To learn more about how you can automate security operations with Cortex XSOAR, check out our virtual self-guided XSOAR Product Tour
We also host virtual and in-person events, so check here for upcoming ones.