Respond Quickly to Phishing Campaign Targeting Diplomats
Unit 42 recently reported that a Russian threat actor they had been tracking was engaged in phishing campaigns targeting diplomats. The Fighting Ursa phishing campaign used a car for sale as a lure to distribute the HeadLace backdoor malware. The campaign likely began as early as March 2024, and the threat actor has been associated with Russian military intelligence.
Unit 42 has observed other threat groups using similar tactics, posing as car sellers. In addition, the group Fighting Ursa has been conducting campaigns leveraging a zero-day exploit in Microsoft Outlook (now known as CVE-2023-23397) targeting nation-states.
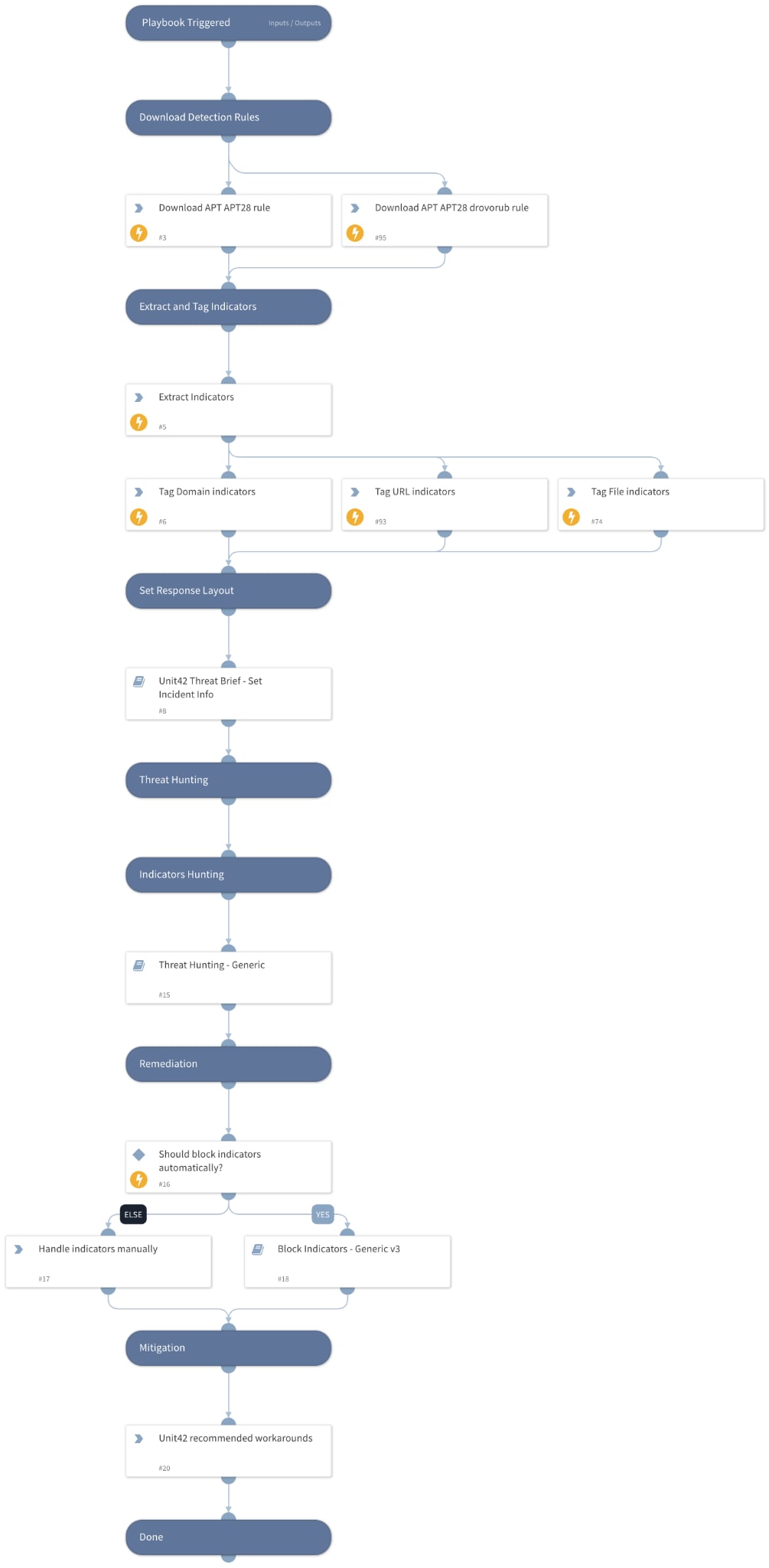
To help your team facilitate response, we are providing the Unit 42 Threat Brief - Fighting URSA content pack to help you automate the following:
- Collection, extraction, and enrichment of indicators
- Fetching threat actor-related detection rules
- Indicator-based threat hunting across your PANW products and SIEM solutions
- Mitigation actions where identified indicators can be blocked automatically or handled manually by the analyst
- Unit 42 recommendations for additional mitigation measures an analyst can take to reduce the likelihood of an impact
Sub-playbooks in this pack include:
- Threat hunting - generic playbook
- Block indicators - generic playbook
- Rapid Breach Response - set incident info
You can download this pack in our Cortex Marketplace. Cortex XSOAR or XSIAM is required for this automation.
To learn more about how you can automate security operations with Cortex XSOAR, check out our virtual self-guided XSOAR Product Tour.