Introduction
SAP NetWeaver Visual Composer has recently come under fire due to a critical zero-day vulnerability - CVE-2025-31324. This flaw, actively exploited in the wild, allows unauthenticated attackers to upload malicious files via the /developmentserver/metadatauploader endpoint, potentially achieving full remote code execution (RCE) on exposed SAP systems. The CVSS score of 10.0 underscores its severity, making rapid detection and remediation essential.
To help organizations mitigate this threat, the Cortex XSIAM Response and Remediation pack introduces a dedicated playbook: CVE-2025-31324 – SAP NetWeaver Visual Composer. This playbook identifies vulnerable systems, hunts for potential webshells and indicators of compromise (IOCs), and executes and guides containment and remediation steps.
This playbook can be triggered by:
- Adopting “CVE-2025-31324 – SAP NetWeaver Visual Composer” trigger rule in your XSIAM product.
- Running this playbook manually.
Learn more in the full Unit42 threat brief: Unit42 Threat Brief – SAP NetWeaver CVE-2025-31324
Threat Overview
CVE-2025-31324 is a remote code execution (RCE) vulnerability affecting the Metadata Uploader component in SAP NetWeaver Visual Composer. Due to missing authorization checks, unauthenticated attackers can upload malicious files (e.g., JSP web shells) to vulnerable systems. The flaw has received a CVSS score of 10.0, reflecting its severity.
- Component Affected: SAP NetWeaver Visual Composer Metadata Uploader
- Endpoint: /developmentserver/metadatauploader
- CVE ID: CVE-2025-31324
- Exploitability: Remote, unauthenticated
If exploited, attackers can execute arbitrary code with privileges of the SAP server process, compromising system integrity and confidentiality.
Stages of the Playbook
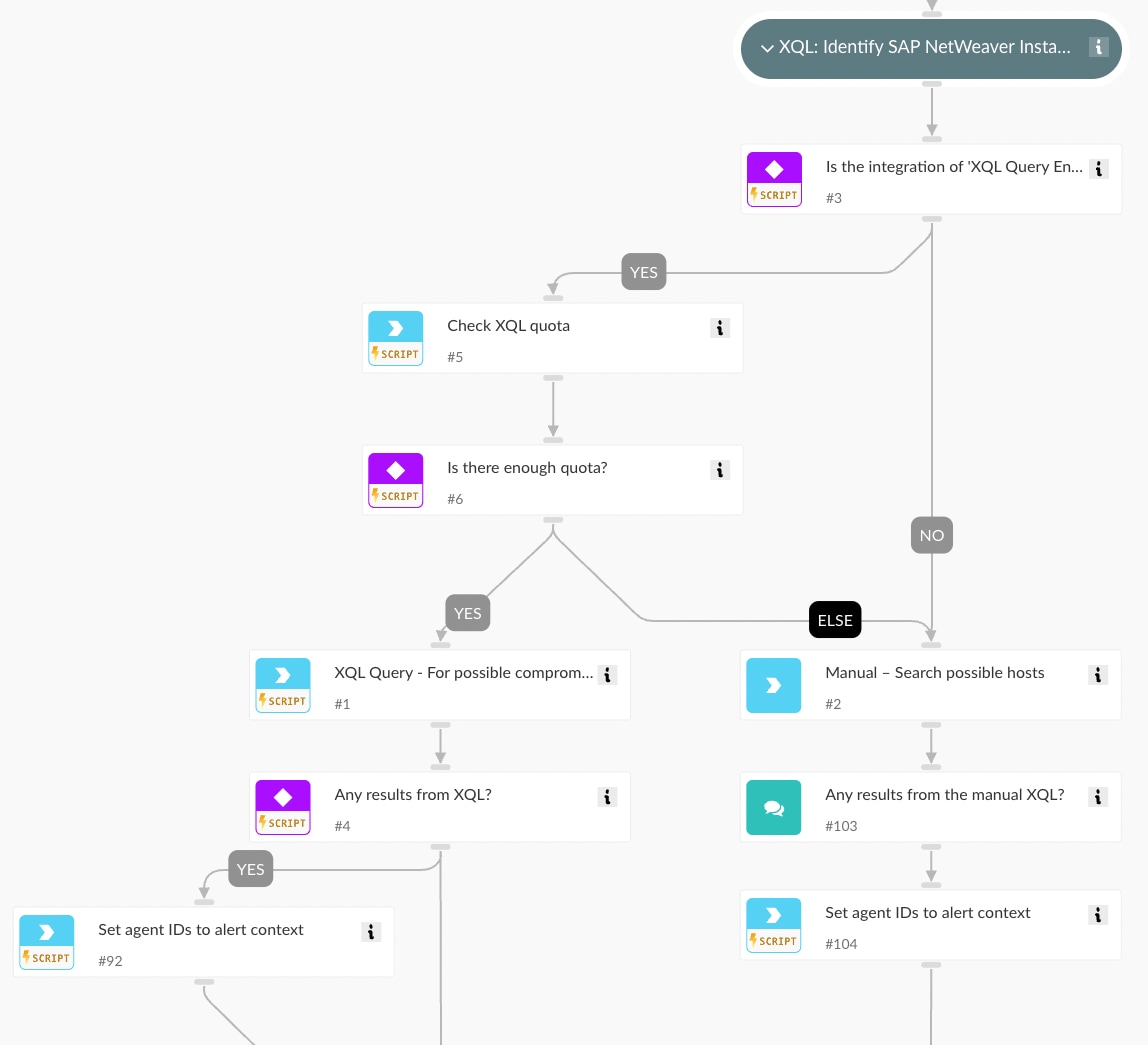
- Asset Discovery (XQL)
Identify endpoints running SAP NetWeaver Visual Composer by querying for jstart.exe activity in paths containing visualcomposer.
In case XQL is unavailable, you can manually add the Cortex XDR Agent IDs of affected machines.
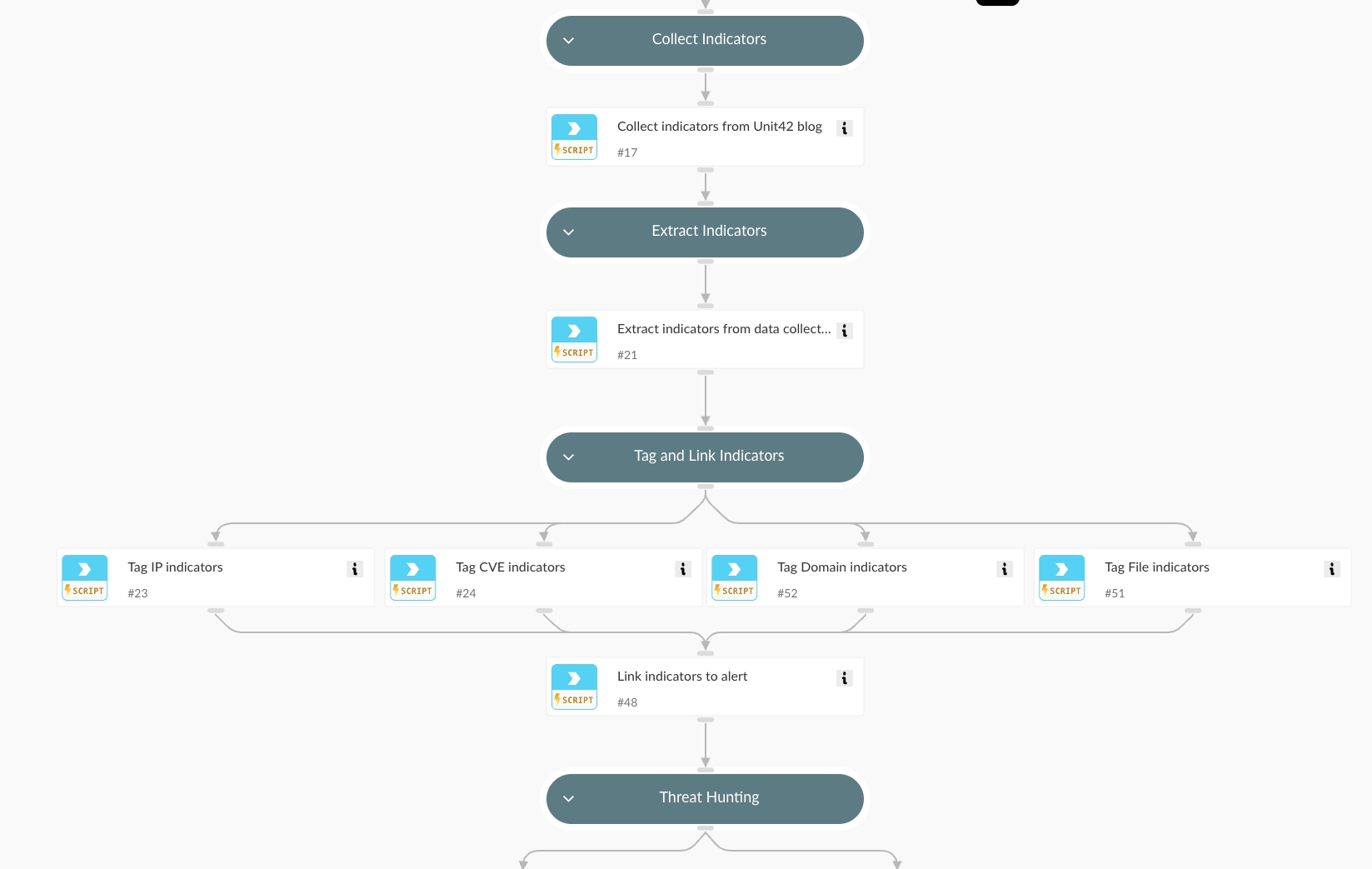
2. IOCs Collection and Tagging
-
- Extracts Indicators of Compromise (IOCs) from the Unit42 Threat Brief
- Tags indicators (File, Domain, IP, CVE)
- Links indicators back to the triggering alert
3. Threat Hunting
Uses the Threat Hunting - Generic playbook to search for IOCs across integrated platforms (Cortex, Splunk, QRadar, etc)
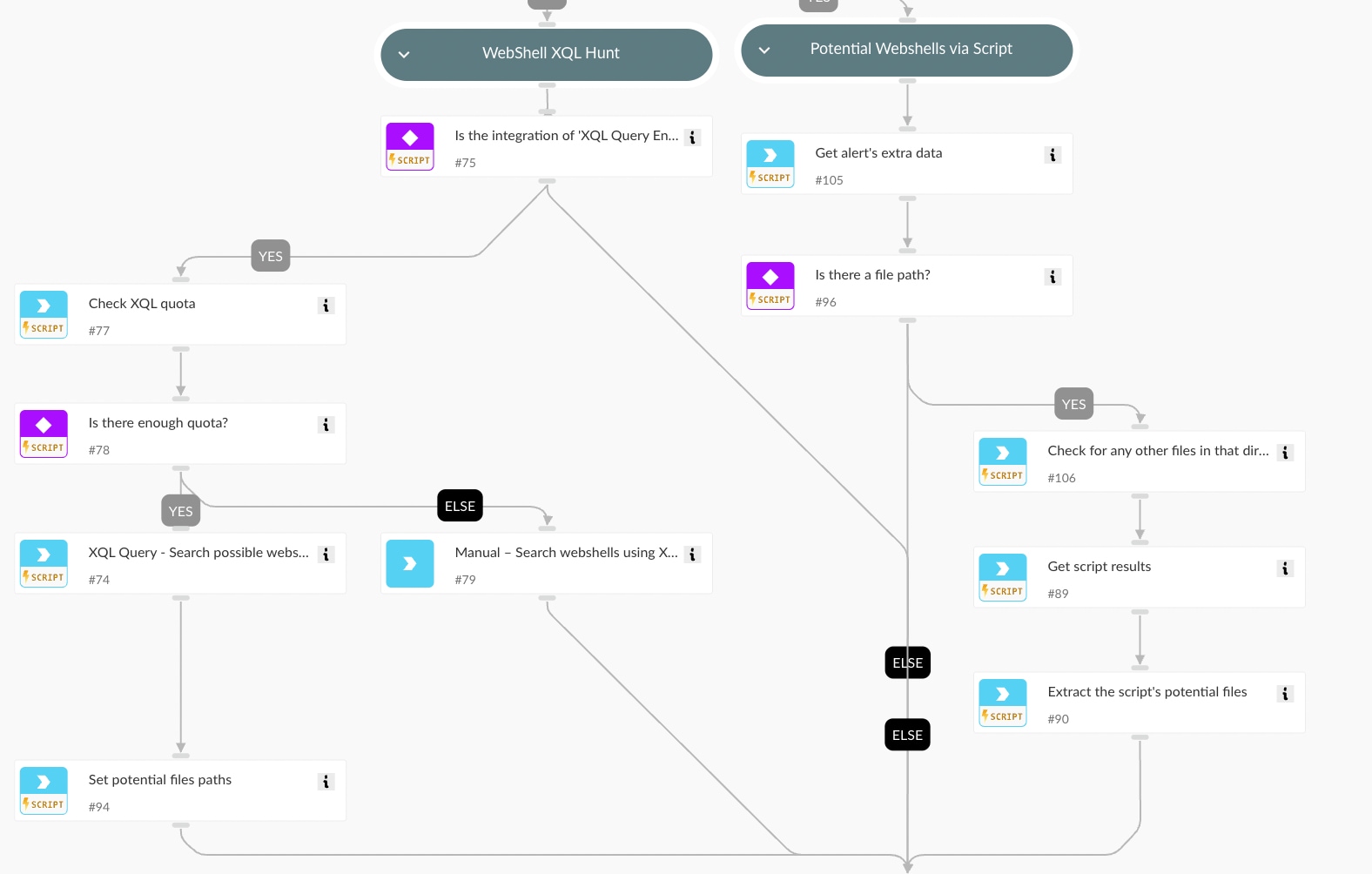
4. WebShell Detection
Performs inspection of /servlet_jsp/irj/ directories to detect suspicious files indicative of webshells.
This step leverages two key Cortex XSIAM capabilities:
- XQL Queries to detect file operations in the target directory using suspicious extensions (e.g. .jsp,.jspx,.class)
- Cortex XDR Agent Live Terminal actions to remotely enumerate the directory and identify known or suspicious webshell files
5. Containment and Blocking
Invokes the Containment Plan - Block Indicators sub-playbook to block all identified malicious domains, IPs, and hashes
6. Playbook Provides Mitigation Guidance
Provides detailed remediation steps, including:
-
- Patching via SAP Note #3594142
- Applying YARA rules for webshell detection
- Implementing Sigma rules (from public PR)
- Manual quarantine suggestions for suspicious files
7. Investigation Resolution
Analysts are prompted to determine whether to escalate or close the case based on investigation findings and patch level. Additionally, the playbook shares information about open-source tools for compromise assessment, intended for cases where the Cortex Agent is not deployed on affected systems.
Conclusion
With CVE-2025-31324 actively exploited in the wild, rapid response is critical. This playbook provides an automated and guided workflow to identify vulnerable systems, hunt for exploitation signs, and block threats before they escalate. It embodies the Autonomous SOC vision by minimizing analyst overhead and maximizing detection and response speed.