Logins From Unusual Locations
In the global age of today’s business, it’s tough to spot a malicious VPN access attempt from a genuine case of employee travel and access from another country. Moreover, with increased cloud adoption, there are multiple sources of geographical presence to verify, heaping more work on security teams and presenting a window of opportunity to attackers.
How Orchestration Helps
Some security orchestration platforms enable playbooks as not just reactive measures, but also as proactive scheduled workflows. In this case, a VPN check playbook can be scheduled to run at timely intervals and identify any VPN anomalies before escalating to security teams for further investigation.
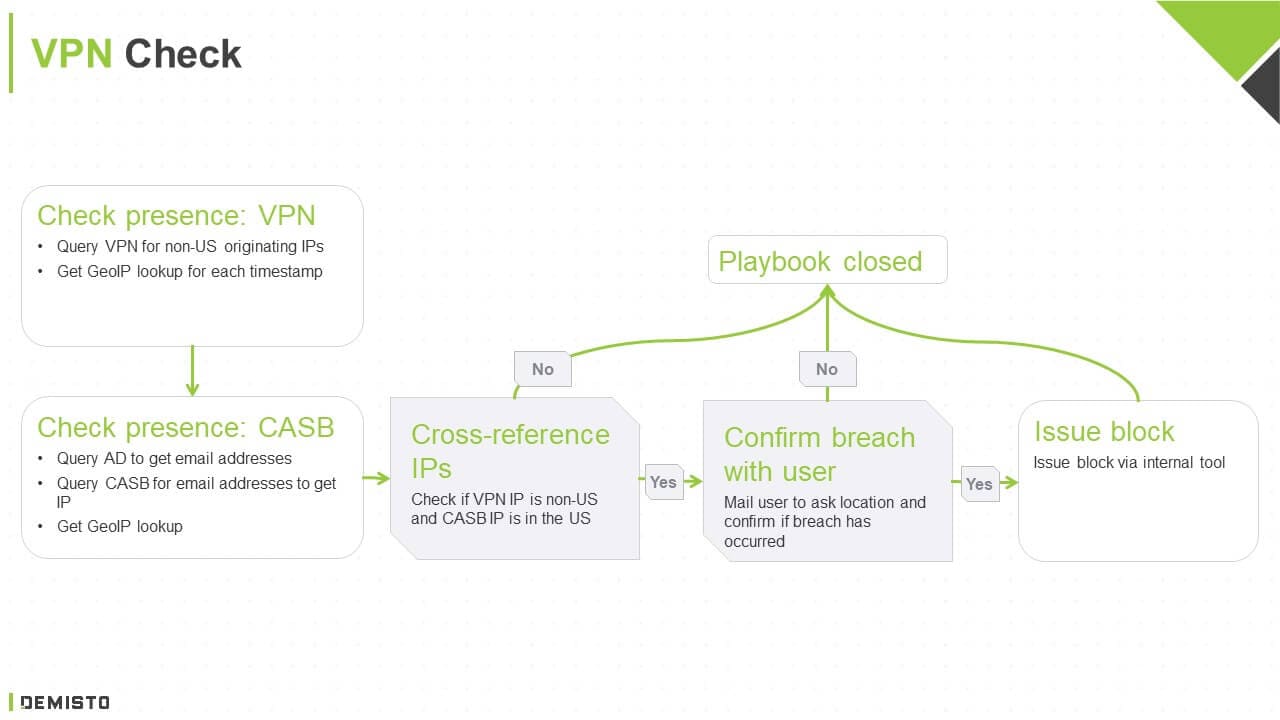
1. Check VPN Presence
The playbook queries the VPN service for non-US originating IPs and gets the GeoIP lookup for each timestamp on those IPs.
2. Check CASB Presence
To reconcile the VPN data, the playbook queries Active Directory for all email addresses and checks them against a CASB to retrieve IPs. The playbook then gets GeoIP lookups for each timestamp on these IPs.
3. Cross-reference IPs
The playbook cross-references IPs gathered from the VPN service with IPs gathered from the CASB. Whenever it spots a non-US VPN IP with a US-based CASB IP, it sends an automated email to the affected user to confirm their location.
4. Respond to Breach
If the user responds confirming the breach, the playbook blocks the concerned IP using internal tools and brings in the relevant security analyst for further investigation.
To access Cortex XSOAR's playbooks and orchestration use cases, visit our GitHub playbook repository and see what's possible
Benefits
Unify security functions: By coordinating among VPN, CASB, and email platforms, this playbook can enable security teams to have improved, centralized visibility over security data. It obviates the need for security teams to have multiple consoles open and perform these correlations manually.
Reactive and Proactive: This VPN check playbook can be reactive - triggering every time there's a VPN anomaly detected - or can be scheduled to run at regular intervals as a 'health check' scenario. Since security teams are busy fighting daily fires, they don't have time to conduct these proactive checks that usually act as early warning signs for attacks.
Improve investigation quality: Security orchestration platforms usually correlate intelligence from multiple tools so that security teams can quickly identify whether any attacks are isolated or persistent within their environments. In this example, if security teams schedule the playbook and it finds 10 VPN anomalies across employee laptops, it's a strong indicator of a coordinated breach attempt.
A Good Playbook Should Be...
Simple and intuitive: The playbook should ideally be represented as a task/process flow through a simple drag-and-drop graphical interface. Coding expertise shouldn't be a 'must-have' to make even the most complex playbooks, although each playbook’s code should also be available for analysts to tweak if required.
Primed for automation: Analysts should be able to automate the entire playbook in response to a phishing attack, greatly reducing response time, effort, and the possibility of human error for large-volume attacks. However, analysts should also be able to include manual steps in playbooks and require human intervention for sophisticated attacks.
Customizable: Analysts should be able to make copies of the standard playbook, modify it, or embed it in other playbooks as needed.
We hope you found this use case walk-through helpful. This is only a skeletal workflow - your own 'playbook' can be as simple or complex as your needs merit.
To see Cortex XSOAR in action, sign up for the free Community Edition.