Internet exposures, such as the Remote Desktop Protocol (RDP) open to the internet, are a ticking time bomb before they are exploited by threat actors as an initial attack vector for ransomware. Such exposures are often known issues for days or longer before an organization has the ability to act on them. Just knowing the exposure exists, and how bad it is, is only the first step of the process: remediation needs to be efficient and quick.
Understand where your network might be vulnerable with help from Cortex Xpanse. If you use Palo Alto Networks firewalls, you are not only able to discover the weak spots with Xpanse, but also can decide if the Active Response Module should automatically remediate exposures for you. This will ensure that these internet exposures don’t become large security incidents that disrupt your business.
Protect Your Firewall Management Interfaces
One challenge with a software as a service (SaaS) offering that needs API communication to your firewalls is you don’t want your Palo Alto Networks firewall and Panorama management interfaces openly available on the internet.
Instead of taking that risk of opening up firewalls management interfaces to the public internet, you can use what we call an engine– a small Linux server you set up on your network right alongside your firewalls that acts as a proxy. This engine will safely connect to Cortex Xpanse without exposing your systems. It requires a simple shell script to be installed and HTTPS connectivity to the internet as well as your firewalls.
Once you have that engine in place, you need to allow Xpanse to talk to your firewalls through secure API communication. It's a straightforward way to keep things running smoothly without opening up any additional gaps in your defenses.
Connecting to Firewalls via API
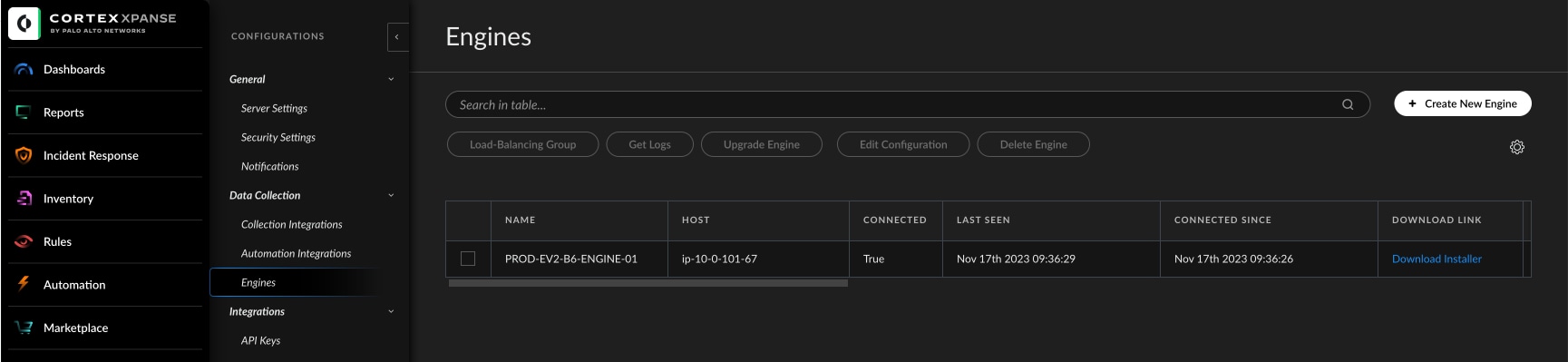
To connect your Palo Alto Networks firewalls and Panorama to Cortex Xpanse, there's an integration in the PAN-OS by Palo Alto Networks content pack. The content pack is only a couple of clicks away to install or upgrade via the Marketplace tab.
Before you get started, you'll also need the right administrative role on the firewall that allows configuration and commit permissions for the Extensible Markup Language (XML) API in order to take full advantage of enrichment and remediation of Xpanse alerts.
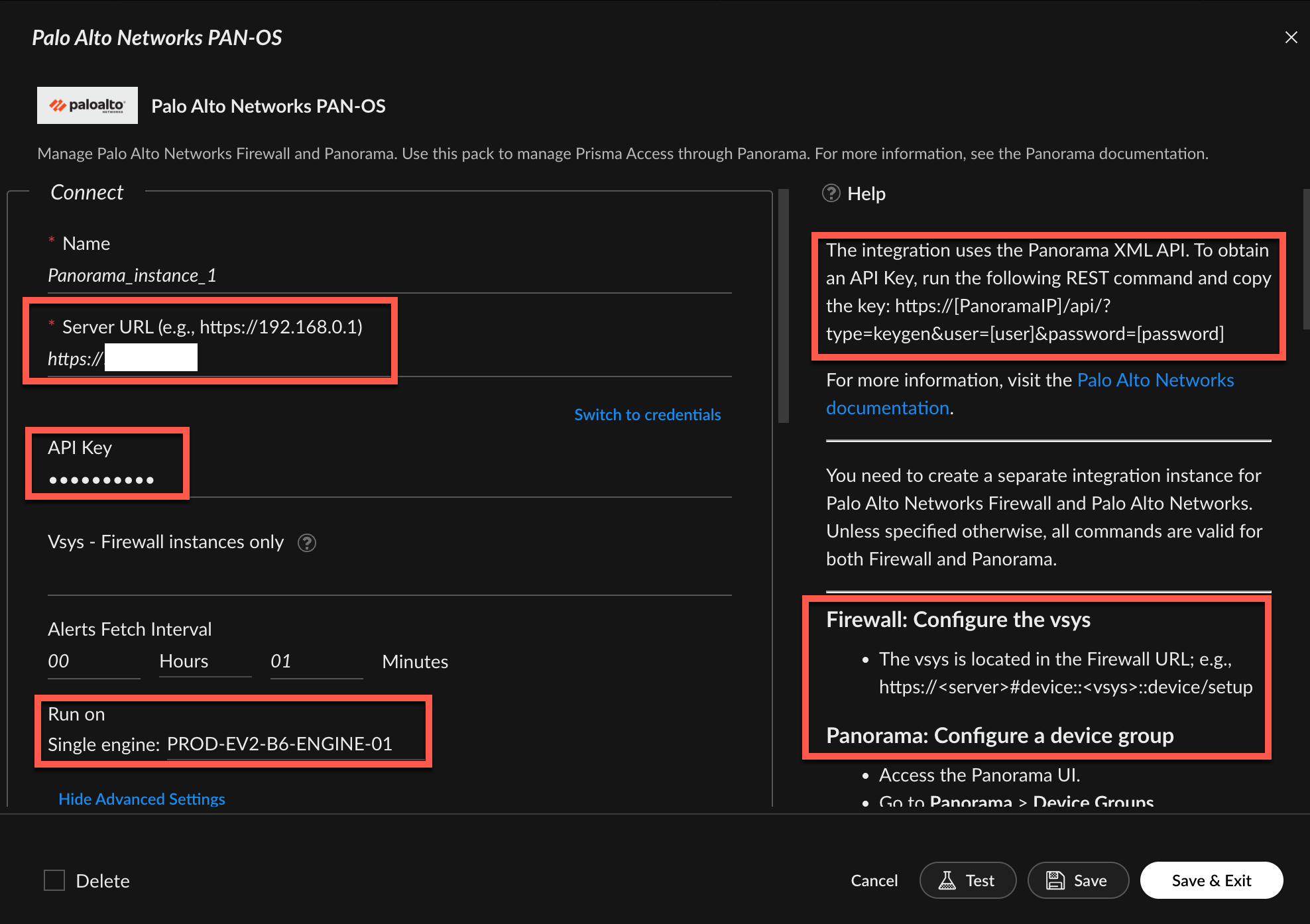
When configuring the integration, make sure to follow the directions that show up in the right of the window regarding creating the API key as well as specific configuration for firewall vs Panorama. You will need to enter the URL for your firewall, the API key, and choose the engine that you previously configured. Don't forget to hit "test" to make sure the connection works.
Once complete, you are ready to start pulling information on firewall rules that are over-permissive (enrichment) as well as starting to remediate these dangerous exposures.
Collecting Additional Information on Over-Permissive Firewall Rules
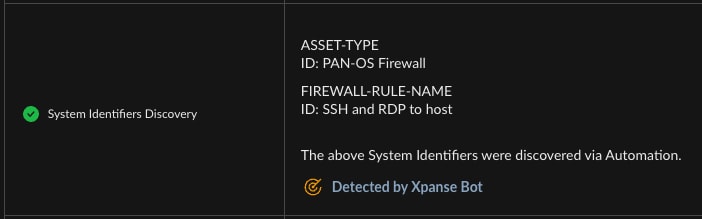
Enrichment in Xpanse alerts is all about collecting additional information for your vulnerability analyst to look over before they make their decision on next steps to take. For example, if a firewall rule is too liberal and causes a potential risk, the enrichment can tell you exactly which rule it is. For Panorama users, it can also identify the affected device group.
This detail is really helpful when you're figuring out where the problem is to fix. It also makes it easier for you to explain the issue to the team in charge of that part of the network, so they can take the right steps to tighten security.
Automation to Fix the Exposure Efficiently
It's crucial to address exposures quickly, because they can escalate into major security incidents if left unchecked. This is where the power of automated remediation comes into play. With Cortex Xpanse, for vulnerabilities that can be fixed by blocking a specific firewall port, the process is simple.
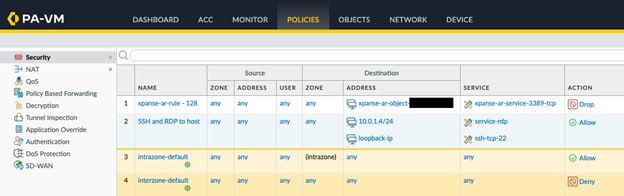
Here's how it works: the details gathered during the enrichment phase are used to automatically guide the remediation steps. The automation system uses the prefix "xpanse-ar" to create new firewall elements (services, addresses, and rules) which are then strategically placed in your firewall rulebase to block the problematic traffic.
Additionally, the solution is traceable by including the alert ID in the name of the new block rule. This way, you can easily identify and reference the change later. The ultimate aim here is to close off the vulnerability promptly and accurately without interrupting the flow of other network traffic.
Increasing Coverage
Cyberthreats are always advancing and you need automation systems that defend against them to evolve as well. That is why Palo Alto Networks always looks into making improvements that simplify security operations while increasing protections.
One example of improvement could be to simplify the configuration on the firewall side by unifying all firewall rules created by Cortex Xpanse into a single rule or external dynamic list (EDL). Furthermore, the addition of App-ID support is a possibility, promising to enhance your ability to identify application traffic.
The diversity of firewall configurations, particularly the use of network address translation (NAT) before the firewalls, which is very common for cloud service provider (CSP) deployments, is an understood challenge. Therefore, there’s a focus on increasing interoperability for all the varied and advanced setups of firewalls you might encounter.
The most important part of the software development process is receiving and integrating feedback to improve the overall product. We're eager to hear your thoughts on what we are doing with remediation of internet exposures with Cortex Xpanse as well as integration with Palo Alto Networks firewalls. Are these solutions meeting your needs, or do you see room for improvement? Your feedback is crucial to us. Please reach out to your Customer Success Architect to give us some input.
To learn more about Cortex Xpanse Active Response module
Article Reference Links