On Nov. 7, 2021, Unit 42 published a detailed report on a sophisticated, active, and difficult-to-detect campaign that has compromised at least nine organizations across the technology, defense, healthcare, energy, and education sectors.
Threat actors leveraged an authentication bypass vulnerability (CVE-2021-40539) in Zoho ManageEngine ADSelfService Plus, a self-service password management and single sign-on solution.
How Does CVE-2021-40539 Work?
With this vulnerability, an attacker could create a crafted Rest API URL to bypass a security filter due to an error in URL normalization, subsequently allowing them to execute arbitrary code. The vulnerability affected ADSelfService Plus builds up to 6113 and was rated as “Critical” with a CVSS v3 score of 9.8. Refer to ManageEngine’s Security Advisory for more information.
Cortex Xpanse Discovers Vulnerable Versions Affected by This CVE
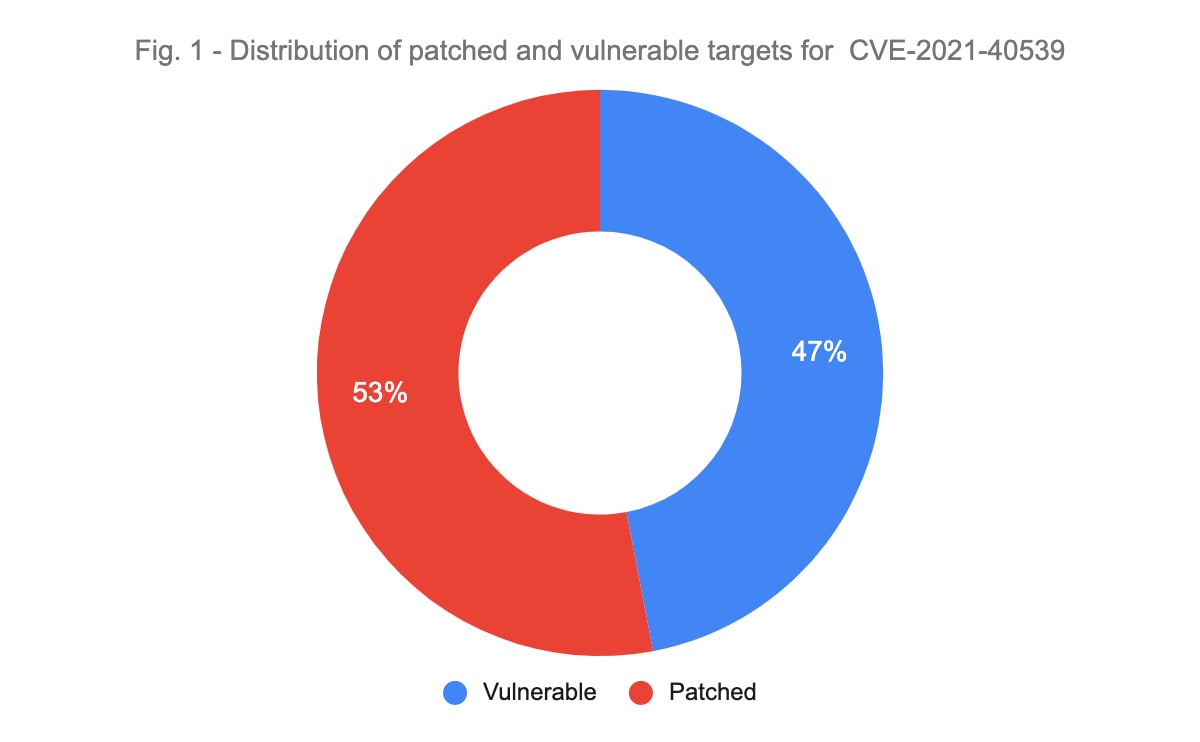
According to recent scans with the Palo Alto Networks Cortex Xpanse platform, there are several thousand internet-exposed systems around the world running the affected Zoho software. Globally there are ~4000 servers running Zoho ADSelfService Plus. Based on the publicly available device version information, 1,885 of those are running a build version affected by CVE-2021-40539 (i.e 47% of instances accessible via the public internet are vulnerable to this issue.)
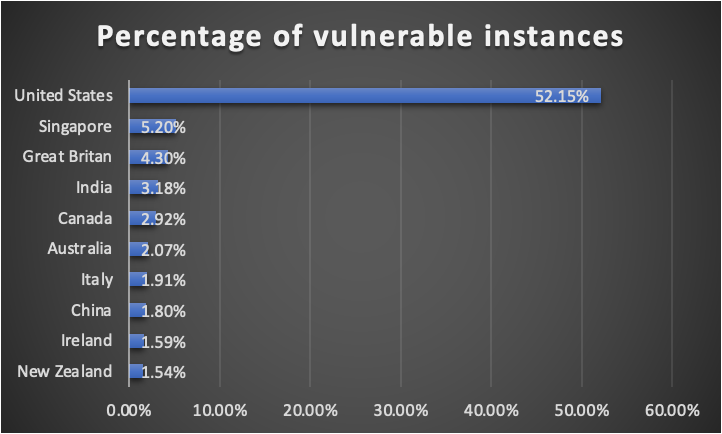
We also observed that the majority of global systems that are potentially vulnerable to this CVE are located in the United States. More than 52% of vulnerable Zoho ADSelfService Plus versions are found in the United States, followed by Singapore at 5% and Great Britain at 4%.
Fig. 2 - Distribution of vulnerable versions of Zoho ADSelfService Plus by geography (Top 10 countries)
Is Your Organization Also Running End-of-life Software?
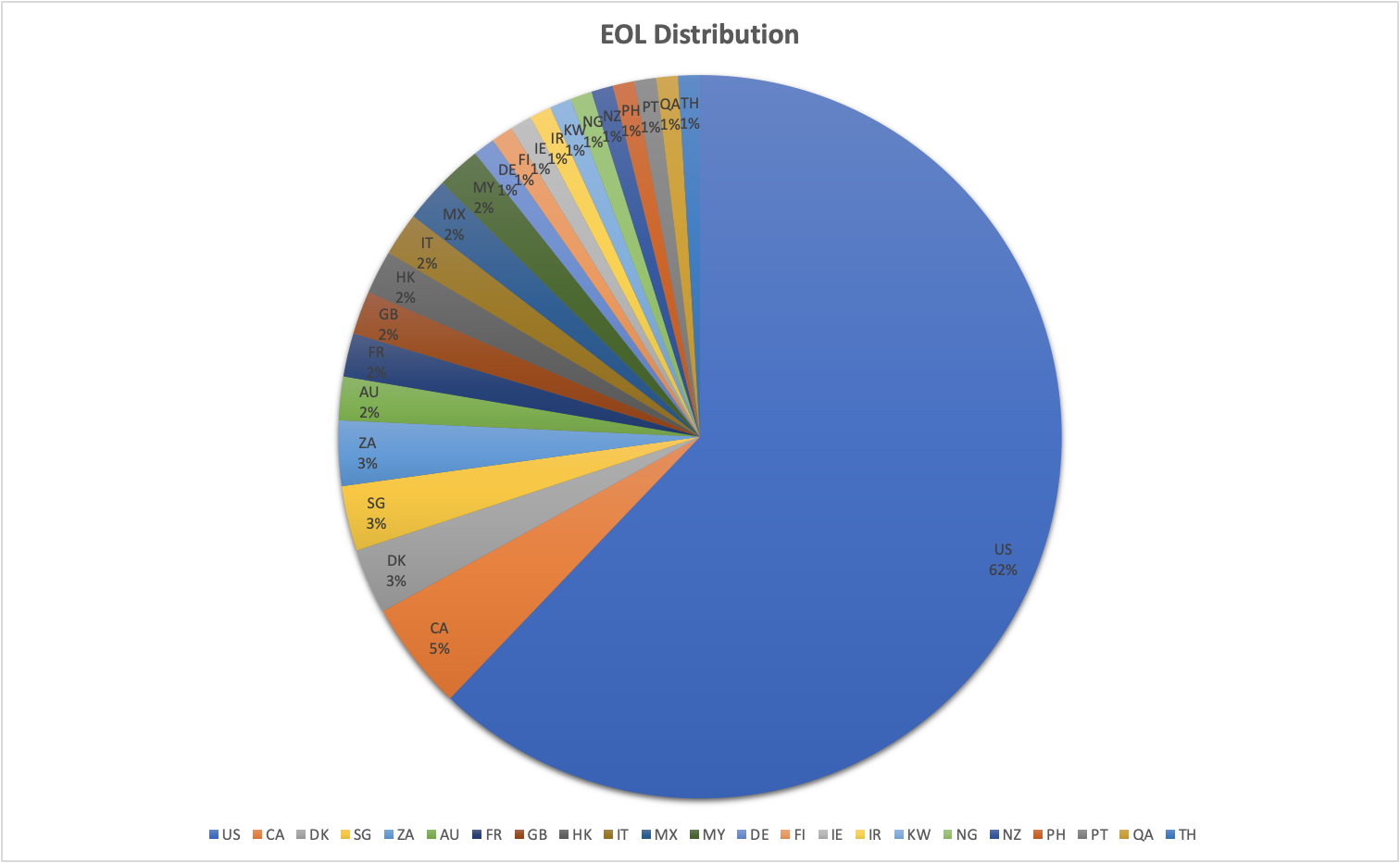
Several organizations are also running outdated end-of-life versions of Zoho ManageEngine. As per the vendor’s end of life policy, versions released in the last five years are supported, indicating that versions prior to those are considered end-of-life. As a result, we categorized builds 5318 and prior as end-of-life versions. Five percent of the total number of vulnerable instances are running end-of-life builds and have not been updated in more than five years. The greatest cluster of end-of-life builds was found to be in the United States at 62% followed by Canada at 5%.
Fig. 3 - Distribution of End of Life (EOL) versions by geography
What Can You Do?
A patch for CVE-2021-40539 was released on Sept. 7, 2021, and the vulnerability was the subject of a CISA alert on Sept. 16, 2021, which urged organizations to ensure that ADSelfService Plus is not directly accessible from the internet.
In the light of this information, we recommend organizations proactively review their internet-facing assets. Due to the network access provided by ADSelfService Plus, the application should not be exposed to the public internet. It is crucial to maintain an up-to-date inventory of assets directly visible on the internet to protect against the ever-changing threat landscape.
A continuous and updated view of your attack surface can help organizations in their rapid response to new CVEs. The 2021 Cortex Xpanse Attack Surface Threat Report found that malicious actors start scanning within 15 minutes following a new CVE disclosure. In contrast, on average, organizations take 12 hours to identify vulnerable systems, assuming the enterprise is tracking and monitoring all assets on its network.
With Cortex Xpanse, organizations gain a continuously updated and near-real-time view of their attack surface which drastically reduces both Mean Time to Detection (MTTD) and Mean Time to Response (MTTR).
If you want to learn whether your organization is running vulnerable versions of a software, please contact us.