Let our Unit 42 hunters work for you
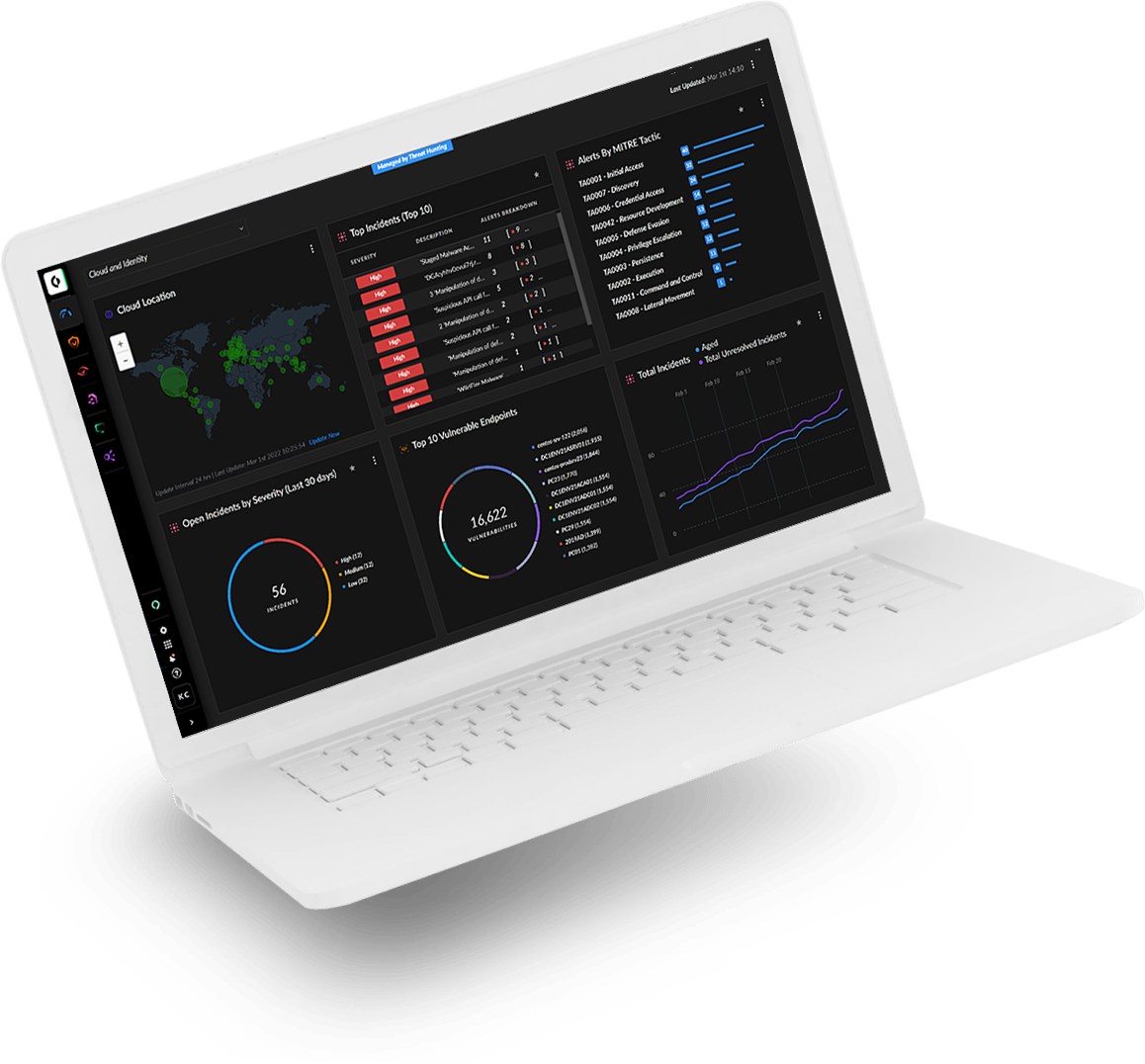
Augment your team with security experts who relentlessly search your environment for attacker tactics and techniques. Our hunters have years of experience hunting and identifying unknown threats as well as reverse-engineering malware.
Manual and semi-automated hunting:
Rest easy knowing world-recognized hunters are scouring your environment for the latest threats.
Expert assistance:
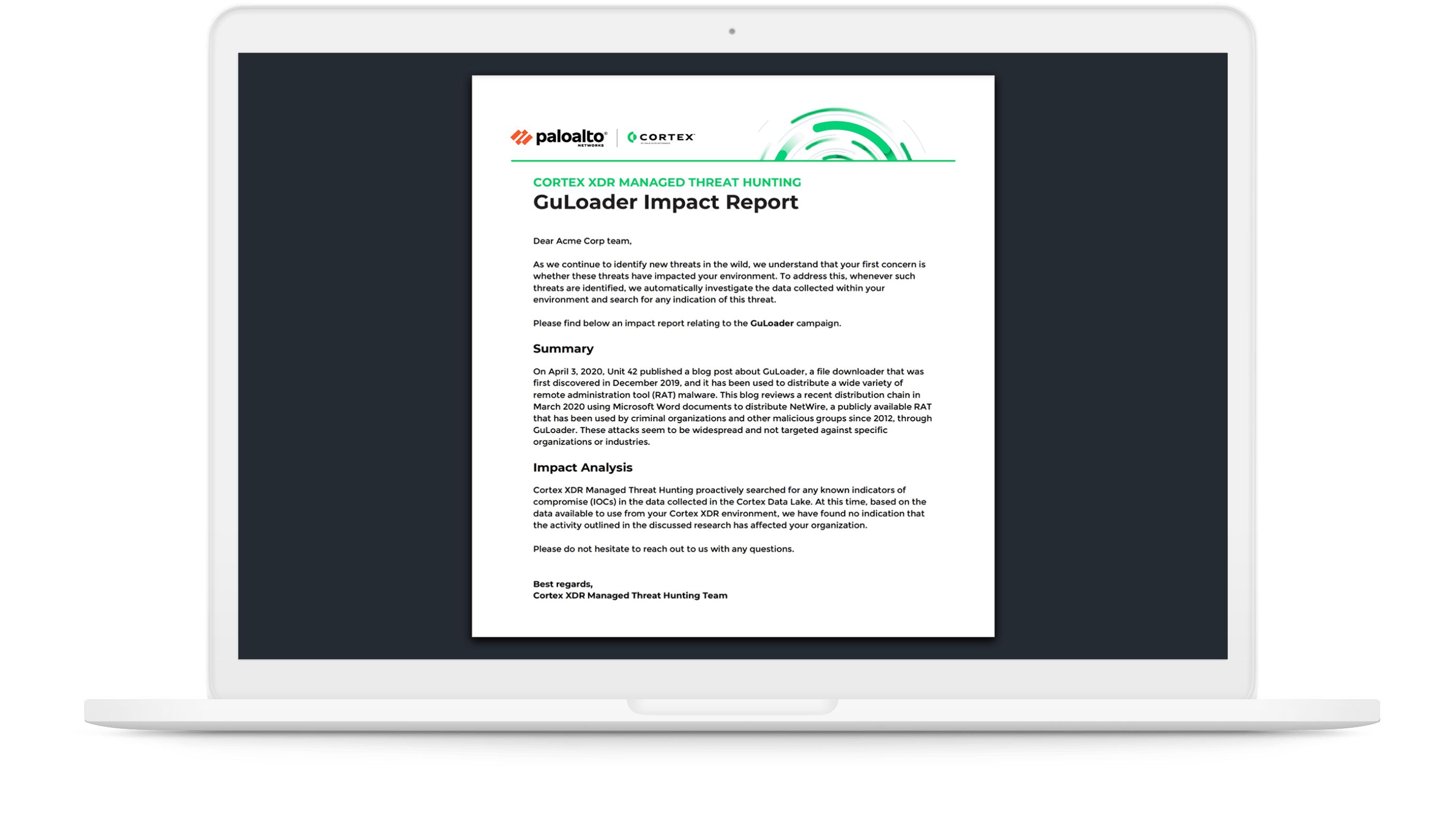
Get answers to questions and receive guidance about findings revealed in Threat, Inquiry, and Impact Reports.