- What Is Access Management?
- What Is Single Sign-On (SSO)?
- What Is CIAM (Customer Identity and Access Management)?
- What Is Passwordless Authentication?
-
Authentication and Authorization Explained
- Authentication and Authorization Explained
- Differentiating Authentication from Authorization
- Authorization Models: RBAC, ABAC, and Policy Enforcement
- Lateral Movement and Attacker Workflow
- Cloud Security Implications for Authorization
- Zero Trust Alignment with Access Control
- Authentication and Authorization FAQs
- What is BeyondCorp?
- What is the Evolution of Multifactor Authentication
- What Is the Principle of Least Privilege?
- What Is Cloud Infrastructure Entitlement Management (CIEM)?
- What is Multifactor Authentication (MFA) Implementation?
- What Is Identity and Access Management (IAM)?
What Is Access Control?
Access control is a comprehensive data security mechanism that determines who is permitted to access specific digital resources, such as data, applications, and systems. It relies on procedures like authentication, which verifies a user’s identity through credentials, and authorization, which grants or denies user access based on predefined criteria or policies.
These policies can be modeled in various ways, including discretionary (DAC), mandatory (MAC), role-based (RBAC), and attribute-based (ABAC) methods. The primary objective of access control is to protect sensitive data from unauthorized access, ensuring that only the right individuals or entities can access specific resources under the right circumstances.
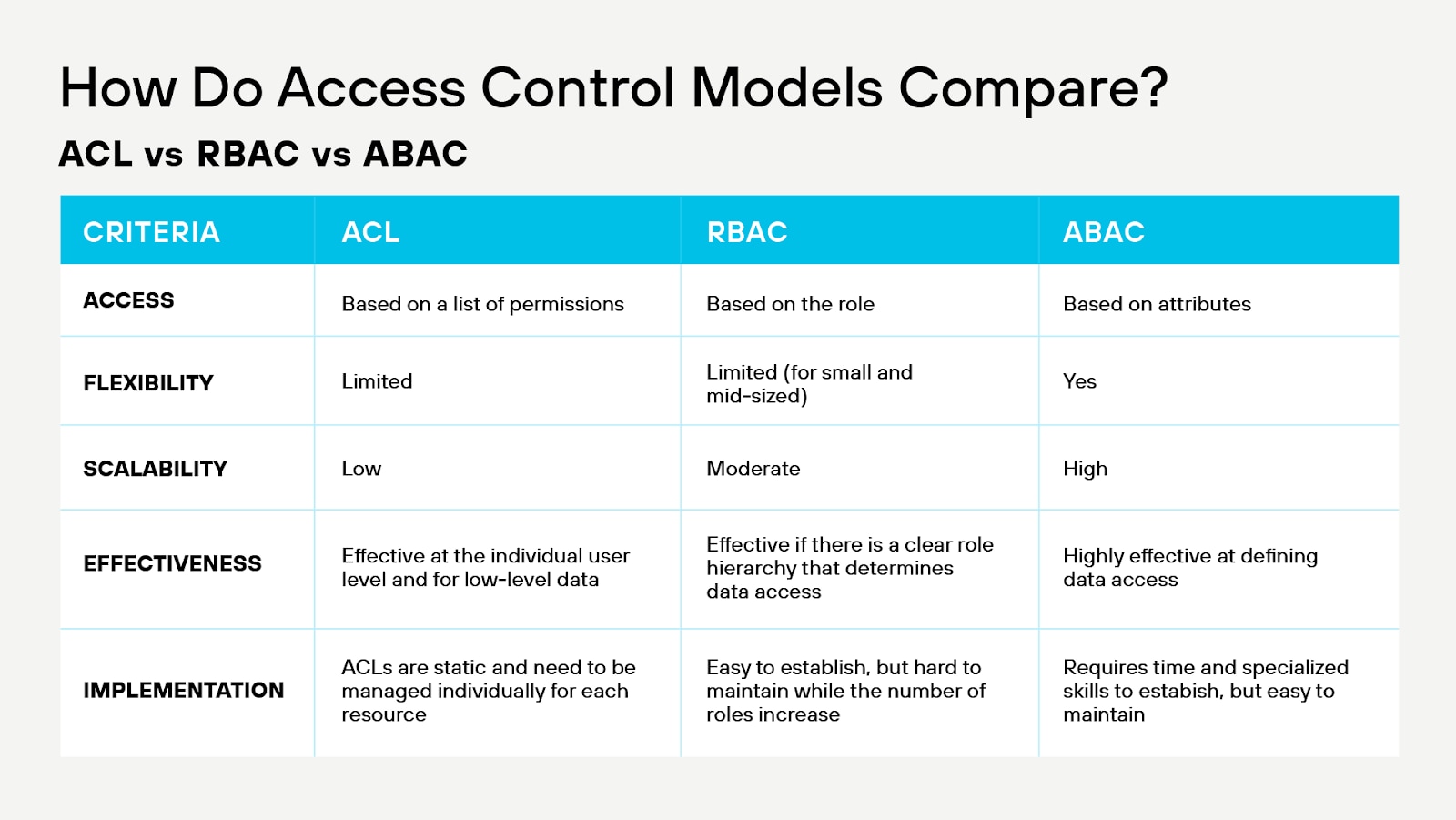
Figure 1: At-a-glance view of leading access control models
Access Control Explained
Access control is the gatekeeper. Think of it as a highly-organized bouncer at an exclusive event. The event represents your organization's data and resources, while the attendees represent users who may need access to various parts of the event.
When a person (user) approaches the entrance to the venue (your data and resources), the bouncer (access control) first checks their invitation (authentication) to ensure they have the right to attend. The invitation might include a unique code, a name, or biometric information like a fingerprint.
Once the bouncer verifies the person's identity, they consult a guest list (authorization) to determine which areas of the event the person can access. This guest list takes into account the person's role or job function. A staff member may have access to more areas than a regular attendee, for example.
As the event progresses, the bouncer (access control) continuously monitors the attendees, ensuring they only visit authorized areas and don’t attempt to enter restricted ones. The bouncer also keeps a detailed log of who enters and exits each area, which helps track attendance and identify potential security issues.
The bouncer's diligence in verifying invitations, consulting the guest list, and monitoring attendees represents the various aspects of access control that serve to protect an organization's data and resources from unauthorized access.
What Are Different Types of Access Control?
Access control models define how permissions are determined and who gets access to specific resources. They offer frameworks to guide the development and implementation of access control policies within a system.
Discretionary Access Control (DAC)
- In DAC models, the object’s owner decides who can access it.
- Owners have discretion over granting access rights.
- Examples: File permissions set by users in a file system, database records ownership.
Mandatory Access Control (MAC)
- Access rights are regulated by a central authority.
- Entities (like users) are granted clearances, and objects (like files) have classifications.
- Based on clearances and classifications, access decisions are made.
- This model is prevalent in environments that require high security, like government or military settings.
Role-Based Access Control (RBAC)
- Access decisions are based on roles within an organization.
- Users are assigned roles, and roles have permissions associated with them.
- For example, a “nurse” role in a hospital might have access to patient records but not to financial systems.
Benefits of Effective Access Control Systems
Access control offers organizations many benefits, enhancing security and operational efficiency.
Enhanced Security
Access control implementation in cloud environments bolsters security by restricting access to sensitive resources, reducing the risk of data breaches and unauthorized access. Authentication and authorization mechanisms ensure only legitimate users can access specific resources, effectively protecting against potential threats and creating a more secure cloud infrastructure.
Regulatory Compliance
Adhering to access control best practices helps organizations meet industry regulations and standards, including GDPR, HIPAA, PCI DSS, SOC 2, and ISO 27001. Controlling access to sensitive information and following predefined policies allow organizations to demonstrate compliance during audits, avoid potential fines or penalties, and maintain trust among clients and partners.
Selective Restriction
In cloud environments, access control enables precise resource access management by granting differentiated access based on roles, responsibilities, or attributes. Selective restriction ensures users access only the resources necessary for their job functions, minimizing the risk of data leakage or unauthorized actions and promoting the principle of least privilege.
Audit and Monitoring
Access control systems in cloud environments provide logging capabilities, tracking user access to resources and recording activities. An audit trail proves invaluable for security reviews, investigations, and user behavior monitoring. Together, these enable organizations to detect anomalies, maintain a secure cloud infrastructure, and respond speedily to potential security incidents.
Operational Efficiency
Access control streamlines the management of user permissions in cloud environments, simplifying administrative tasks and reducing human error. By automating the assignment of roles and privileges, organizations can minimize manual intervention, improve productivity, and ensure the right users have access to the necessary resources.
Data Integrity and Confidentiality
Implementing access control helps maintain data integrity and confidentiality by preventing unauthorized access to sensitive information. By restricting access based on predefined policies, organizations can safeguard their critical data from tampering or unauthorized disclosure, protecting their intellectual property, and preserving their competitive advantage.
Reduced Risk of Insider Threats
Access control mitigates the risk of insider threats by enforcing the principle of least privilege, ensuring users only have access to the resources required for their job functions. By closely monitoring user activities and regularly reviewing permissions, organizations can identify and address potential vulnerabilities, minimizing the risk of unauthorized actions or data leaks.
Multilayered Security with MFA
Combining access control with multifactor authentication (MFA) adds an additional layer of security to cloud environments. MFA requires users to provide multiple forms of identification before gaining access to resources, making it more difficult for attackers to compromise accounts. This multilayered security approach strengthens overall protection and reduces the likelihood of unauthorized access.
Physical Security
Access control mechanisms contribute to the physical security of cloud infrastructure by limiting access to data centers and server rooms. By granting entry only to authorized personnel, organizations can protect their critical hardware and network equipment from unauthorized access, tampering, or theft, ensuring the integrity of their cloud infrastructure.
Flexibility and Scalability
Access control systems in cloud environments offer flexibility and scalability, allowing organizations to efficiently manage user access as their needs evolve. As new users join or roles change, access control policies can be easily updated to accommodate these changes, ensuring continued security without hindering growth or productivity.
Cost Savings
Implementing effective access control in cloud environments can lead to cost savings by reducing the risks associated with data breaches, unauthorized access, and noncompliance penalties. By minimizing these risks, organizations can avoid financial losses, protect their reputation, and maintain customer trust, ultimately resulting in a more cost-effective security strategy.
User Convenience
Features like single sign-on (SSO) allow users to access multiple applications or platforms with a single set of credentials, enhancing user experience without compromising security.
Access Control Use Cases
As seen in diverse use cases, access control across domains helps to protect information, resources, and systems from unauthorized access.
Data Protection
- Description: Safeguarding sensitive data such as customer information, financial data, intellectual property, and proprietary business information.
- Examples: Banks protecting customer financial details, hospitals securing patient medical records, and companies safeguarding their trade secrets.
Cloud Security
- Description: Protecting data and applications in cloud environments.
- Examples: Restricting who can access specific data in cloud storage, setting up permissions for users of a cloud-based application.
E-commerce and Online Transactions
- Description: Ensuring that online transactions are secure and can only be initiated and completed by authorized users.
- Examples: Password-protected accounts for online shopping platforms and secure payment gateways.
Physical Security
- Description: Limiting or controlling physical access to specific areas or buildings.
- Examples: Employees using badges to access office buildings, gated communities requiring PIN codes or cards for entry, and restricted zones within research labs.
Network Security
- Description: Preventing unauthorized users from accessing or harming the network.
- Examples: Firewalls that block unauthorized incoming or outgoing traffic, Virtual Private Networks (VPNs) that allow secure remote access.
Application and System Security
- Description: Ensuring only authorized users can access specific software applications or systems.
- Examples: A Content Management System (CMS) to which only authorized editors can publish articles to accounting software to which only the finance department has access.
Workflow and Task Management
- Description: Granting access based on tasks or stages in a workflow.
- Examples: A document review process where different tiers of reviewers have different access levels, manufacturing processes where workers have access only to their specific task areas.
Regulatory Compliance
- Description: Meeting requirements set by government or industry standards regarding data access and protection.
- Examples: HIPAA regulations for patient data in the healthcare industry and GDPR for data protection and privacy in the EU.
Device and Resource Management
- Description: Controlling who can use or modify specific devices or resources.
- Examples: Admin controls on corporate laptops, machine operators needing special access to operate specific machines.
These use cases highlight the importance of access control in maintaining security, ensuring efficient operations, and meeting regulatory demands across different industries and contexts.
DSPM and Access Control
Data security posture management (DSPM) with data detection and response (DDR) allows organizations to scan, analyze, and categorize structured and unstructured data in the cloud. By identifying sensitive information and categorizing it appropriately, teams can refine access control to improve data protection.
DSPM with DDR increases visibility into an organization's data security infrastructure, equipping organizations to identify potential access control vulnerabilities. Through the process of discovering, classifying, and categorizing data, organizations can understand the sensitivity of their information. In addition to enabling teams to implement granular access control policies, DDR's real-time monitoring of data access and usage patterns detects anomalies and suspicious activities that could indicate unauthorized access. DDR then allows organizations to quickly respond to potential access control violations, minimizing the risk of data breaches.
Access Control FAQs
Access control management refers to the process of creating, implementing, and maintaining access control policies to protect digital resources, such as data, applications, and systems. It involves defining user roles, assigning permissions, setting up authentication mechanisms, and monitoring access to resources.
Effective access control management ensures that only authorized individuals can access specific resources under appropriate circumstances, safeguarding sensitive information from unauthorized access and enhancing overall security. Additionally, access control management helps organizations streamline administrative tasks, which go far in reducing the risk of data breaches and security incidents.
A data inventory is a comprehensive list of all the data assets that an organization has and where they're located. It helps organizations understand and track:
- Types of data they collect, store, and process;
- Sources, purposes, and recipients of that data.
Data inventories can be managed manually or automatically. The reasons for maintaining a data inventory vary — and could include data governance, data management, data protection, data security, and data compliance.
For example, having a data inventory can help organizations identify and classify sensitive data, assess the risks associated with different types of data, and implement appropriate controls to protect that data. It can also help organizations understand which data they have available to support business objectives, or to generate specific types of analytics reports.
The data lifecycle describes the stages involved in a data project, often including data generation, collection, processing, storage, management, analysis, visualization, and interpretation.
Understanding how data is processed, stored, and accessed is foundational to data security and disaster recovery. Similarly, managing data governance, classification, and retention policies play pivotal roles in data lifecycle management effort.
Data in use refers to data actively stored in computer memory, such as RAM, CPU caches, or CPU registers. Because it’s not passively stored in a stable destination but moving through various systems, data in use could be vulnerable to and target for exfiltration attempts, as it may potentially contain sensitive information such as PCI or PII data.
To protect data in use, organizations can use encryption techniques such as end-to-end encryption (E2EE) and hardware-based approaches such as confidential computing. On the policy level, organizations should implement user authentication and authorization controls, review user permissions, and monitor file events.
Data leak prevention (DLP) software can identify and alert security teams that data in use is being attacked. In public cloud deployments, DLP is best achieved through the use of a data detection and response solution.