How Palo Alto Networks can help you securely power your remote workforce
A VPN is a necessity for keeping your data safe and secure when doing work online or on any public network.
Palo
Alto Networks offers multiple solutions that can help you power and secure your remote workforce – Prisma
Access
and GlobalProtect.
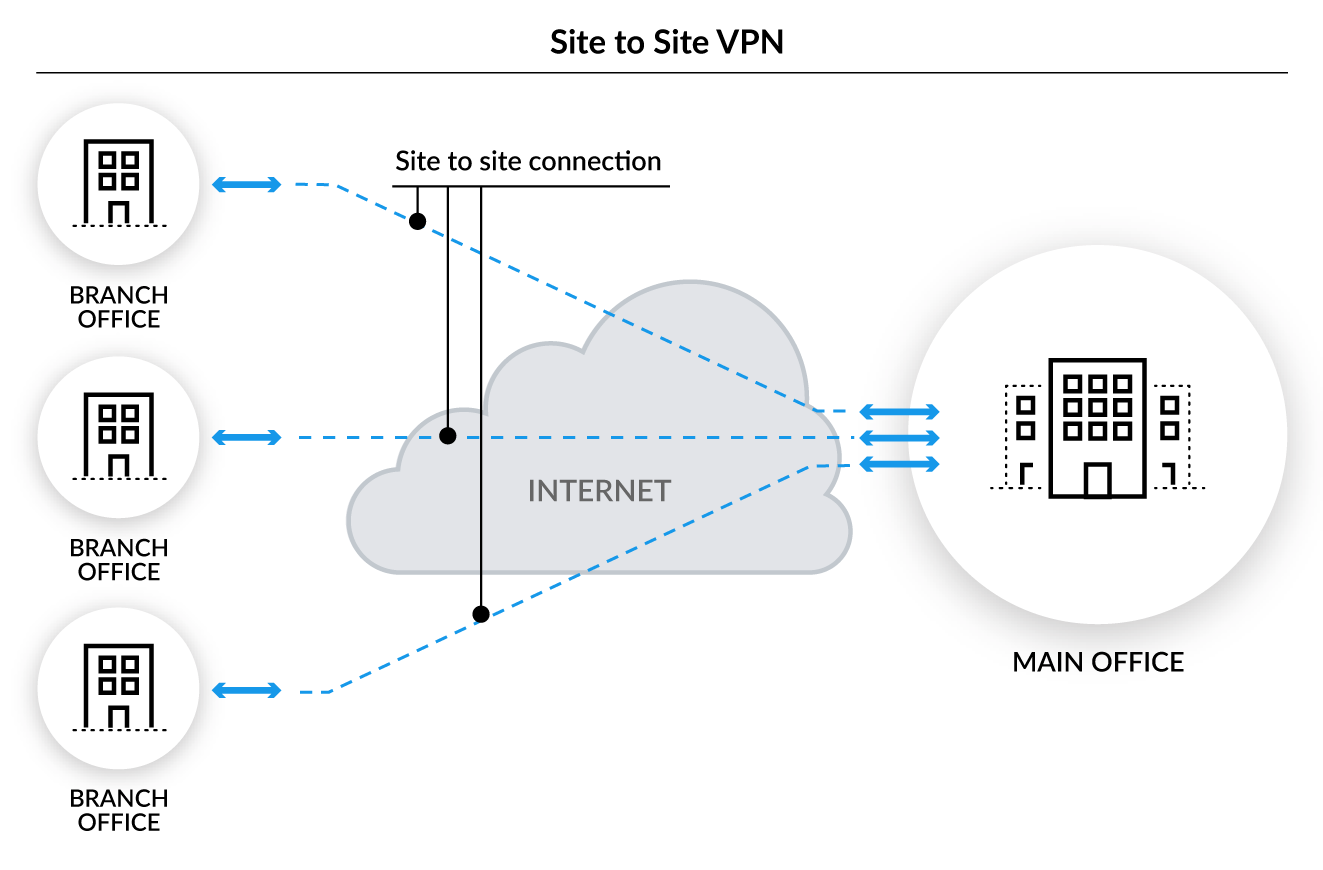
Prisma Access
Prisma Access™ delivers the networking and security that organizations need to
secure the cloud-enabled remote workforce. Prisma Access is the ideal option when you require the ability to
scale your remote workforce quickly.
Mobile users and remote branches connect to our service in the cloud, forming a VPN tunnel between the cloud and
the mobile user or branch, enabling seamless and secure access to cloud, data center and SaaS apps or resources.
Think of it as a cloud
network between users and the corporate network that delivers all the functionality of hardware, managed by
Palo
Alto Networks in the cloud.
For example, if you had the need to scale to 10,000 users working from home, the process is easy. You simply
need to install the same software client onto your mobile devices and connect into Prisma Access, bringing all
the security capabilities of Palo Alto Networks Next-Generation firewalls, but without the need to deploy
additional
infrastructure. In essence, Prisma Access helps organizations secure remote workforces rapidly, no matter where
they are in the world.
Additional use cases
-
Firewall as a Service
- DNS security
- Threat prevention
- Cloud secure web gateway
- Data loss prevention
- Cloud access security broker
Further resources
GlobalProtect
GlobalProtect™ network security for endpoints is the on-premises, built-in VPN solution for the Palo Alto
Networks Strata network security suite. Every Palo Alto Networks Next- Generation Firewall is designed to
support always-on, secure access with GlobalProtect as your mobile workforce grows.
GlobalProtect extends the prevention capabilities of the Security Operating Platform® to mobile workers, regardless of their location. By leveraging Next-Generation Firewall capabilities, GlobalProtect provides greater visibility into all traffic, users, devices, and applications. You can extend consistent security policies to all users while eliminating remote access blind spots and strengthening your security.
For instance, if you already operate the necessary firewall appliance and originally planned to enable 20% of
your workforce to work remotely but had the need to scale to 100%, the process would simply require users to
run the coinciding software client on their laptops, connect to that same next generation hardware appliance
and they’re good to go.
Additional use cases
-
Protect your growing mobile workforce
- Implement a zero-trust architecture
- Enable and secure bring-your-own-device
Further resources
VM-Series Virtual Firewalls
VM-Series Virtual Next-Generation Firewalls provide all the capabilities of the Palo Alto Networks Next-Generation hardware firewall in a virtual machine form factor. This allows you to secure your
environments using a single tool, automate network security and boost your cloud investments.
If you’re struggling to provide remote access with limited hardware, it’s possible to add more capacity by
using a virtual machine-based firewall.
Additional use cases
-
Infuse segments and microsegments with threat protection
- Leverage a single security tool with consistent control across multi-cloud environments
- Get dynamic security provisioning and scalability for dynamic environments
Further resources
Palo Alto Networks is here to help you protect your mobile workforce.
We hope this guide has been beneficial to you in your search for trustworthy information on securing your
remote employees by using a VPN. Palo Alto Networks is here to help with your rapid deployment needs to power
and secure your remote workforce.