-
- How Cortex XSIAM 2.0 Revolutionizes Security Operations
- Cortex XSIAM Solutions and Advantages
- Addressing Critical Issues in Current SOC Solutions
- How Cortex XSIAM Transforms the SOC
- Distinctive Features of Cortex XSIAM
- Comprehensive SOC Solutions: Single Platform Delivery Highlights
- Integrated Capabilities: The XSIAM Solutions Delivery
- Ready to Transform Your Cybersecurity Landscape?
Table of contents
-
What Is Security Operations (SecOps)? Comprehensive Guide
- Security Operations (SecOps) Explained
- The Pillars of Modern SecOps: People, Process, and Technology
- Example Scenario: Incident Response to a Malware Alert
- Proactive Security Operations Examples
- Technology: Core Tools for the SOC
- Core Components and Functions of the SOC
- SecOps vs. DevOps vs. DevSecOps
- Security Operations FAQs
- What Is a Security Operations Center (SOC)?
-
How Do I Deploy SecOps Automation?
- Preparing for SecOps Automation
- Start Simple with High-Impact Tasks
- Automation Benefits for Organizations of All Sizes
- Peer Review and Approval
- Secure a Champion for Automation
- Defining Automation Use Cases
- Example Use Cases: Phishing and Malware
- Selecting the Right SOAR Platform
- SOAR Deployment and Use Cases FAQs
- Security Operations Center (SOC) Roles and Responsibilities
- What is SOC as a Service (SOCaaS)?
- How Do I Improve SOC Effectiveness?
How AI-Driven SOC Solutions Transform Cybersecurity: Cortex XSIAM
5 min. read
Table of contents
In today’s fast-evolving threat landscape, traditional SOCs struggle to keep up with the volume and complexity of security data. CISOs and cybersecurity practitioners need a more intelligent, automated approach. This article introduces Cortex XSIAM, an AI-driven platform that transforms SOC operations.
Learn how Cortex XSIAM addresses critical SOC challenges, integrates powerful capabilities into a single platform, and enhances threat detection and response. Discover how this next-gen solution can streamline operations, strengthen security posture, and prepare your organization for the future of cybersecurity.
How Cortex XSIAM 2.0 Revolutionizes Security Operations
Cortex XSIAM (Extended Security Intelligence and Automation Management) is the AI-Driven automation-first platform for the modern SOC, harnessing the power of machine intelligence to radically improve security outcomes and transform security operations.
XSIAM is designed to be the center of SOC activity, augmenting SIEM and specialty products by unifying broad functionality into a holistic solution. XSIAM capabilities include data centralization, intelligent stitching, analytics-based detection, incident management, threat intelligence, automation, attack surface management, and more–all delivered within an intuitive, automation-first user experience.
XSIAM consolidates multiple products into a single coherent platform, cutting costs and improving analyst experience and productivity, offering enterprise security significant advantages.
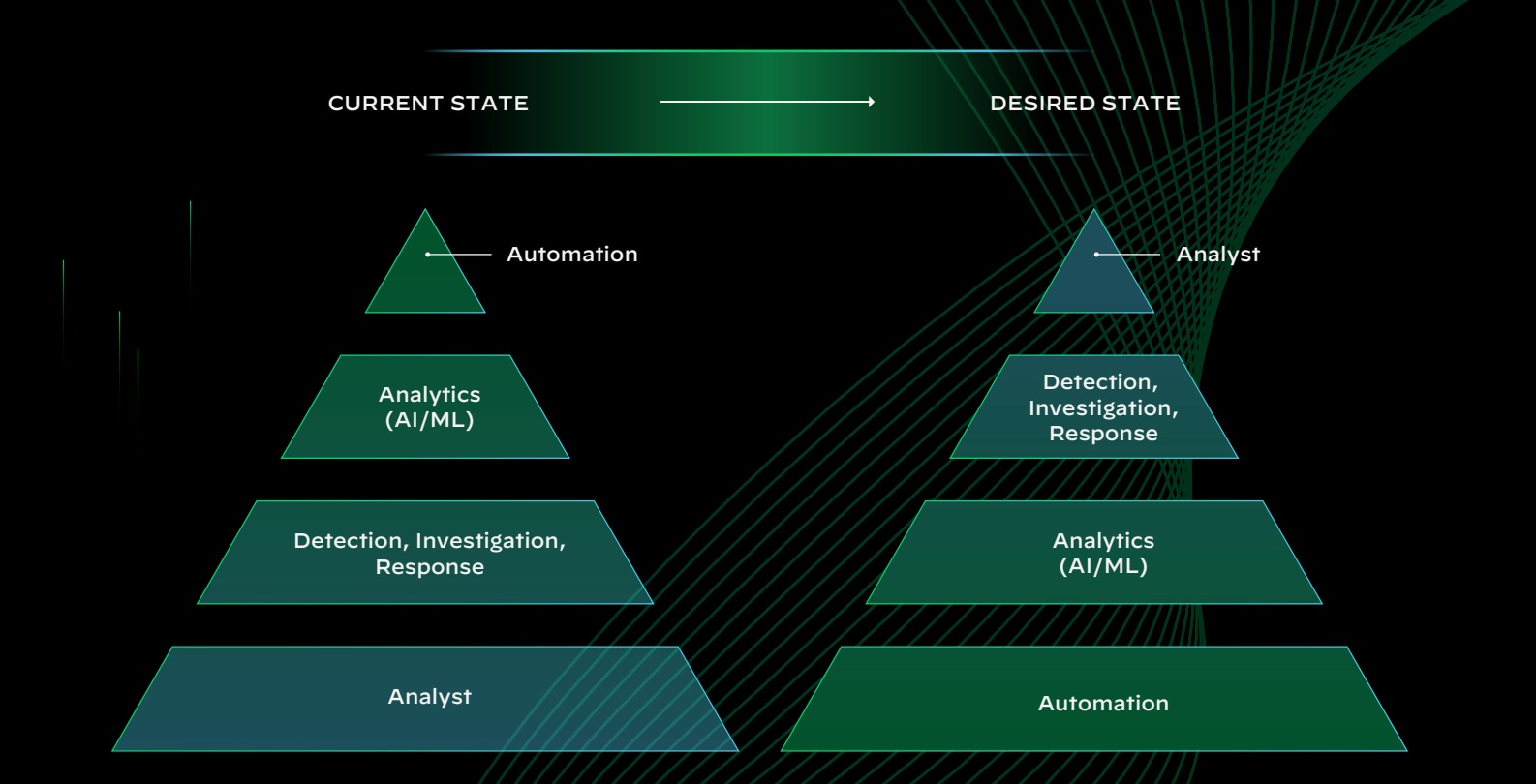
Transition to an Analyst-Assisted Security Operation
| Improve analyst experience and increase productivity by eliminating security silos. | The typical SOC relies on a mix of screens from multiple products. In contrast, XSIAM delivers all functionality in the same console with the same workflows, operating on fully-integrated data. |
| Uncover advanced attacks with behavioral analytics and industry-leading threat intelligence. | Palo Alto Networks experts collect indicators across customers, process, and update models to ensure up-to-date protection. |
| Easily onboard new data sources. | Unlike existing SIEMs, adding a new data source to XSIAM is fast and easy. Onboarding takes only a few clicks, and the new data is automatically integrated into the XSIAM data model, into models and correlations, and into playbooks and dashboards. The result is an ever-growing foundation for machine learning and analytics. |
| Connect tools and orchestrate response with 600+ product integrations. | The Cortex Marketplace includes hundreds of SOAR playbook integrations and automation packs for XSIAM that can be deployed out of the box. |
| Speed up investigations with intelligent alert grouping and SmartScore. | XSIAM automatically groups multiple alerts into a single incident, automating the scoping process and cutting investigation time. SmartScore incident scoring uses machine learning to identify high-risk incidents, helping analysts focus on the threats that matter most. |
| Lower risk with attack surface management and internal asset discovery. | XSIAM displays all known data about a given internal or internet-facing asset using various data sources, including Cortex agents, network traffic, attack surface analysis, Active Directory, and more. Embedded attack surface discovery and response proactively identifies and shuts down new vulnerabilities, while integrating vulnerability data into incidents and analytics. |
| Take the guesswork out of response with remediation suggestions | XSIAM will automatically suggest response actions to the analyst based on the information in a given incident. |
| Extend detection, monitoring, and investigation to the cloud | For many organizations, new cloud systems are not integrated into their SOC. XSIAM is designed to analyze multicloud data and operations, ensuring true enterprise-wide visibility and security operations. |
For many organizations, new cloud systems are not integrated into their SOC. XSIAM is designed to analyze multicloud data and operations, ensuring true enterprise-wide visibility and security operations.
Addressing Critical Issues in Current SOC Solutions
Today’s hybrid enterprise generates many times the security data of a few years ago. Yet the typical SOC still operates on data silos, limited cloud visibility, aging SIEM technology, and manual, human-driven processes that invite attackers to exploit their advantage.
The core challenge with today’s SOC is the length of time it takes to detect security incidents (MTTD) and, when they are detected, it takes too long to remediate (MTTR). Combine this with recent regulatory requirements and threats actors carrying out end-to-end attacks in a matter of hours, this introduces significant risk to organizations.
Incremental analyst headcount cannot stem the tide, and additional tooling only worsens today’s complex SOC architecture and engineering maintenance burdens. The modern SOC must turn to an intelligent, machine-driven model that can block attacks from endpoint to cloud, at scale, with minimal analyst involvement and SOC engineering overhead.
Siloed and Disjointed Data
Organizations have vast amounts of security data stored in different places. Because of this, they are unable to perform AI-based analytics. In addition, alerts are disconnected data points that need to be manually correlated by the SOC. Finally, visibility into the relationship between alerts and events across the environment is limited.
Disparate and Disconnected Tools (Operational Complexity)
Today’s SOCs are built on disparate tools for very specific security functions. This means that SOC analysts need to constantly switch between tools, all with different consoles, terminology, and datasets. Some SOCs attempt to connect these tools, but this means managing fragile integrations between vendors and it introduces overhead, inefficiencies and a high likelihood of missing critical information.
Heavy Reliance on Manual Work (Slow Incident Remediation)
Vast amounts of disconnected data and disparate tools result in an overwhelming number of alerts for SOCs to investigate and resolve. SOC analysts struggle to prioritize which alerts to handle first, and many important alerts are ignored. Events correlation across various data sources and tools is performed manually, or through fragile rules. Typical incident response is a highly manual process, with minimal automation.
Using a security-specific data model and applying machine learning, XSIAM automates data integration, analysis, and triage to respond to most alerts. This enables you to focus on the incidents that require human intervention.
Cortex XSIAM is designed to address the needs of the modern SOC by harnessing the power of machine intelligence and automation to dramatically improve security outcomes and transform the manual SecOps model. This model enables the SOC to be proactive instead of reactive by delivering on the promise of machine-triaged data so the analysts can focus on unusual behavior and anomalies.
Streamlined Data Onboarding Process
XSIAM is the central operations platform for the modern SOC, providing the best-in-class capabilities of EDR, XDR, SOAR, attack surface management (ASM), threat intelligence management (TIM), Identity Threat Detection and Response (ITDR) UEBA, SIEM, and more. But XSIAM is not a collection of disparate tools. Instead, XSIAM weaves together functions and intelligence in a task-oriented user experience and a rich incident management flow that minimizes activities and context switching to power rapid and accurate attack response.
A streamlined data onboarding process lets SecOps teams easily add new data sources while an extended data model normalizes and correlates data for schema on-read data access. Cortex XSIAM also automatically stitches together endpoint, network, cloud, and identity data, so it can detect advanced threats with precision and simplify investigations with cross-data insights.
Cortex XSIAM lets analysts swiftly investigate incidents by providing a complete picture of every attack, including intelligent alert grouping and collected information about the root cause. Embedded automation can enrich alerts, respond to malicious activity, and close low-risk alerts before they reach the queue—enabling analysts to focus on the few threats that require human intervention.
Unlike legacy SOC solutions, where operationalizing and optimizing the product is an exercise left to the customer, XSIAM benefits from continuous updates from Palo Alto Networks Unit 42® research team. Palo Alto Networks experts collect threat intel from more than 70,000 customers, update machine learning (ML) detection models, and automatically distribute the latest protections to XSIAM deployments to safeguard customers from advanced and fast-moving threats.
SOC Controls for Cloud and the Hybrid Enterprise
XSIAM builds an intelligent data foundation across all enterprise security sources, from endpoints to specialized cloud feeds from providers, dynamic workloads, and cloud security products.
The system continually collects deep telemetry alerts and events from these sources, automatically prepares and enriches the data, and uniquely stitches it into security intelligence tuned to support rich machine learning analytics specialized for both specific sources and kill chain-wide behavioral detection. By fusing leading technology with shared intelligence and research, Palo Alto Networks shares the responsibility of protecting our customers’ ongoing operations.
Distinctive Features of Cortex XSIAM
Cortex XSIAM is a true SOC platform and a game-changer for the traditional, multitool, human-driven SOC operating model. Overwhelmingly, organizations using a legacy SOC model all have similar pain about their existing security architecture and management.
Cortex XSIAM was built by security practitioners who have lived through these pains. Its development was influenced by Palo Alto Networks clients seeking a way to solve their security outcome challenges.
Here are the key bullets on how XSIAM is differentiated:
- Truly A Single Product - One UI, One Backend
- Automated Blast-Radius And Recommendations
- Ease of Onboarding And Integration
- Machine-Centric for Human Augmentation
- Lighten the SOC Burden - We Have an Opinion
- Elevate Security Maturity With Each Passing Day
Reduce MTTR with OOTB Orchestration
Some SIEMs have embedded automation; however, the power we have from using the best SOAR and the amount of integrations and content is an advantage. There are also other players that offer automation but it’s not integrated. Finally, few other SIEMs recommend playbooks in a curated, specific way.
XSIAM will include XSOAR, with everything it can do, and more. Automation runs at the incident level and we will also offer OOTB playbook recommendations to analysts.
Reduce Operational Complexity with Tech Consolidation
Typical enterprise SOC landscape today is littered with many tools and point-products - making maintenance and rationalization a chronic challenge. With XSIAM we provide EPP/EDR/XDR/SIEM/NTA/SOAR/UEBA/ASM/TIM/Ticketing in the same console. No one else is doing that. This is a huge deal in terms of cost reduction and operational efficacy.
Onboard with Ease
Some SIEMs are a never ending loop of onboarding systems, and there are many cases where it’s just too complex to connect to a source and customers just give up. Our onboarding wizard is designed to not only connect to source, but also offer rules, dashboards, playbooks and even suggest next steps and which sources should follow after a given one is completed.
Automatically Scope Incidents
SIEMs mostly work at the alert level, or incidents that focus around a single entity (machine, user, IP, etc). They do not offer complex, cyber-related logic that helps group alerts into incidents. This is critical since scoping an incident is mandatory when doing triage and without it investigations cannot be done. This is often a manual process that takes hours and requires skill.
Data Digestion
Any SIEM or even basic log management tool can ingest data, but how many of them can digest it? XSIAM normalizes data and stitches different POVs of the same event into a single, augmented log line that tell the story of the activity, and then uses this data in the analytics engine and makes it available for querying via XQL.
Make Sense of the Cloud
Cloud security is highly segmented and full of niche vendors. XSIAM is being built to address cloud security as a whole (CSPM/CWP/CIEM/etc) using data from all leading CSPs and cloud security vendors, and run analytics on top of that data to identify can help respond to the things that matter within the cloud realm, and in plain english. No need to be a devops expert to understand what’s going on.
Make Sense of Your Network
All SIEMs take in network data, but 90%+ of customers don’t send all of it. They typically choose from which FWs to collect data, and even then they filter heavily. They miss out on the full visibility of east-west/north-south traffic, or some areas of the company, etc. We can take in all data from all FWs, and of course leverage EAL to provide rich context that doesn’t exist in syslog. Once data is in we run powerful analytics on it, build dashboards, etc.
Embedded Threat Intelligence
Threat intel is well incorporated into most SIEMs/EDRs/UEBAs, but few have the amount of in insights and context we do. The U42 name is well known, and Wildfire is used by so many global customers, that the sheer scale of information we can provide about threats and/or threat actors is unmatched. The fact that it’s embedded for free in the solution is a big deal.
Own Your Attack Surface
XSIAM includes Xpanse for EASM, and also consumes data from agents, FWs, AD, and will provide visibility from the inside-out and outside-in. It will also include vulnerability information about assets from Xpanse and active discovery via Xpanse/broker/agents.
Using a security-specific data model and applying machine learning, XSIAM automates data integration, analysis, and triage to respond to most alerts. This enables you to focus on the incidents that require human intervention.
The data model is updated continuously with Palo Alto Networks threat intelligence gathered globally across tens of thousands of customers. XSIAM uses an ML-led design to integrate massive amounts of security data, aggregate alerts into incidents for automated analysis and triage, and respond to most incidents automatically.
Comprehensive SOC Solutions: Single Platform Delivery Highlights
- Simplifies Security Operations with a Converged Platform
- An Intelligent Data Foundation
- Stop Threats at Scale with AI-Driven Outcomes
- Outpaces Threats
- Accelerate Incident Remediation with an Automation-First Approach
- Accelerates Response
- Converges SOC capabilities including XDR, SOAR and SIEM into a single platform, eliminating console switching and streamlining security operations.
- Broad integration support and simplified data onboarding reduces engineering and infrastructure complexities and allows SOCS to easily ingest more data sources.
- Continuous collection, stitching, and normalization of raw data, not just alerts, enabling superior security analytics.
- Simplified connection and collection for any data source
- Automatic data normalization and enrichment
- Stitches data for rich analytics and investigation context
- Built on a cost-effective, scalable cloud architecture
- Out-of-the-box AI models that provide the “full story” of incidents in one place, enabling better detection, analysis and response.
- Alert grouping and AI-based incident scoring connects low confidence events into high confidence incidents that are prioritized based on overall risk.
- Generative AI Copilot to simplify how analysts gather information and take security actions in XSIAM
- Cloud and attack surface visibility and threat detection
- Specialty endpoint, network, cloud, and UEBA analytics
- Real-time behavioral analysis and methods across all data
- Continuous intel and learning from 70,000 customers
- Hundreds of Cortex Marketplace content packs automate previously manual tasks, with the ability to add or customize or automations as needed.
- Alert-specific playbooks that trigger automatically to execute security tasks before an analyst even looks at an incident.
- XSIAM learns from manual analyst actions and recommends future automations to continuously improve automatic resolution of future incidents.
- Alert grouping, incident enrichment, and prioritization
- Automatic execution of common activities
- Intelligent inline playbook functions and rich library
- Unifies and automates broad SOC functions
- Platform Convergence Centralized security made simple
- Stop Threats at Scale with AI-Driven Outcomes
- Dramatically better attack protection
- Accelerate Incident Remediation with an Automation-First Approach
- Analyst actions minimized and optimized
Integrated Capabilities: The XSIAM Solutions Delivery
| SIEM Includes all common SIEM functions, including log management, correlation and alerting, and compliance reporting*. |
TIP* Provides full TIP capabilities to manage Palo Alto Networks and third-party feeds, and to automatically map them to alerts and incidents. |
| XDR Integrates endpoint, cloud, and network telemetry for automated detection and response. |
EDR Includes a complete endpoint agent and cloud analytics backend to provide endpoint threat prevention, automated response, and in-depth telemetry useful for any threat investigation. |
| ASM* Includes embedded ASM capabilities that provide a holistic view of the asset inventory, including internal endpoints and vulnerability alerting for discovered internet-facing assets. |
User and Entity Behavior Analytics Includes specialized identity analytics that use machine learning and behavioral analysis to profile users, machines, and entities to identify and alert on behavior that may indicate a compromised account or malicious insider. |
| SOAR Includes a robust SOAR module and marketplace to create and orchestrate playbooks for use with XSIAM. |
Cloud Detection and Response (CDR) The XSIAM analytics array includes specialty analytics designed to detect and alert on anomalies in cloud data such as cloud service provider logs and cloud security product alerts. |
| Management, Reporting, and Compliance Centralized management functions simplify operations. Powerful graphical reporting capabilities support reporting for compliance, data ingestion, incident trends, SOC performance metrics, and more. |
|
* Available through additional licensing and modules.
Palo Alto Networks’ Cortex XSIAM stands out as a paradigm shift in the realm of cybersecurity, offering an unparalleled suite of features designed to centralize, streamline, and fortify security operations.
By harnessing the power of AI-driven intelligence, comprehensive data integration, and extensive tool connectivity, it empowers security analysts to detect threats with greater accuracy, manage incidents more efficiently, and enhance overall productivity.
The platform's commitment to automation and intelligent decision-making ensures that organizations are not just responding to threats, but proactively managing their security posture. From enhanced threat detection to streamlined incident response, Cortex XSIAM delivers a holistic and agile security solution, tailored to meet the demands of today’s ever-evolving digital landscape.
Embracing Cortex XSIAM is not just an upgrade to an organization’s security infrastructure—it is a strategic investment in building a resilient, future-proofed cybersecurity ecosystem. As we navigate through a world where cyber threats are becoming more sophisticated and pervasive, adopting advanced solutions like Cortex XSIAM is no longer just an option; it’s an imperative for ensuring the integrity, confidentiality, and availability of critical digital assets.
Ready to Transform Your Cybersecurity Landscape?
Dive into the future of advanced threat detection and seamless incident response with Cortex XSIAM. Don’t just stay ahead of threats—outsmart and preempt them. Take the first step towards unparalleled security intelligence and operational efficiency. Request a Demo today.
Experience firsthand how Cortex XSIAM can revolutionize your security operations. Contact a representative today to see the power of AI-driven security in action. Transform your cybersecurity strategy and fortify your defenses with Cortex XSIAM.
Discover more insights from Cortex reports, webinars, data sheets, solution briefs and more when you browse our resource center.


