What Is a Cloud Secure Web Gateway?
A cloud secure web gateway (SWG) is a cloud-delivered network security technology that filters internet traffic and enforces corporate and regulatory policy compliance.
A cloud SWG secures internet access for diverse environments, from remote users to IoT devices, by offloading traffic from on premises to the cloud. It enhances visibility and control over web traffic and threats, applying robust controls and data protection while facilitating direct-to-cloud connections to improve network performance.
Limitations of Legacy On-Premises Web Proxy Appliances
When security vendors first introduced SWGs into the marketplace, they primarily consisted of proxy vendor solutions. However, proxies and SWGs serve different purposes: a proxy primarily provides a networking role, while an SWG offers a comprehensive security solution.
A proxy, acting as an intermediary device or program, facilitates a user's request to access a destination like a website or cloud application. The proxy conceals the user's IP address, which adds a level of privacy. Proxies function by accepting a client's web request, disconnecting the initial connection, connecting anew to the requested destination, and relaying the client's data.
Traditional on premises web proxy appliances come with limitations, including:
Inadequate Security
Proxy vendors didn’t originally design these appliances, along with other legacy multivendor solutions, with the cloud in mind. They don't provide consistent security for all users and devices, which can leave gaps in an organization's defenses.
Restricted Visibility
Traditional proxies cannot detect over half the threats remote workers face from non-web applications, making it impossible to secure against unseen risks.
Degraded User Experience
Routing internet traffic through centralized data center proxies causes performance issues. Remote workers might use VPNs instead of SWGs to access private apps, leading to potential confusion and increased support demands.
Vendor Appliance Issues
Employing multiple vendors for security appliances can lead to disjointed management, uneven security policies, and reduced network threat visibility. This often results in higher maintenance costs and hampers teamwork between networking and security teams.
What Is a Secure Web Gateway (SWG)?
Cloud SWG Benefits
Cloud-based secure web gateways are pivotal for organizations seeking robust internet security across various locations, including remote offices, branches, and even large headquarters. By transitioning from on-premises systems to cloud-based solutions, organizations can effectively meet high bandwidth demands. Cloud web security gateways also provide real-time comprehensive visibility into user activities and internet threats, along with robust controls for access, functions, SaaS, and sensitive data protection.
Cloud-based web security gateways can substantially enhance end-user experiences. By circumventing the need to route all traffic through a corporate data center—a process that often results in latency—direct cloud connections can significantly boost network performance. This approach streamlines access and security procedures and aligns with modern, decentralized work environments.
Cloud SWGs that support proxy architectures offer a forward-leaning posture in network security that complements, rather than replaces, the foundational security provided by firewalls.
How Cloud SWG and SASE Work Together
Deploying SWGs as standalone systems can create challenges, including disjointed workflows and a lack of integration with other security services within an organization. Fragmentation can lead to increased complexity and inefficiency in security operations, particularly as organizations grow and security needs become more complex.
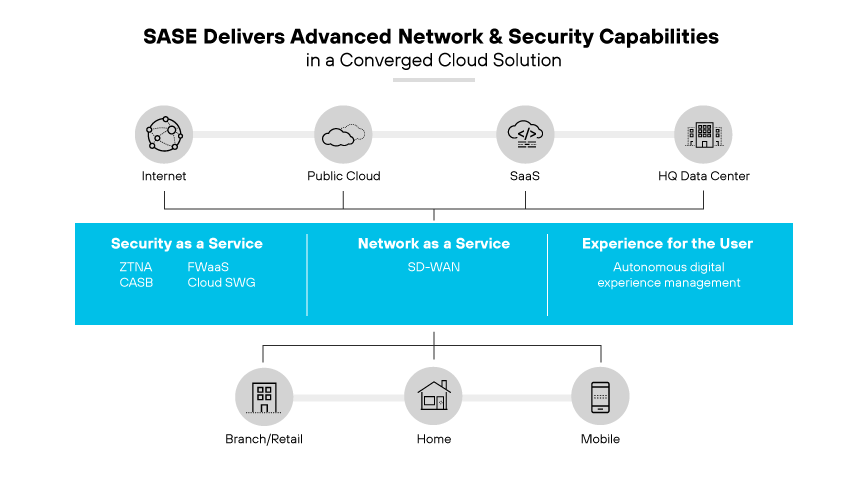
The secure access service edge (SASE) model presents a solution by merging networking and security into a singular cloud-based service. This integrated approach simplifies the delivery of comprehensive network and security functions, encompassing SD-WAN, VPNs, cloud SWG, CASB, FWaaS, DLP, and threat prevention.
In a SASE framework, the cloud SWG component plays a crucial role. It extends web access control and applies security policies to protect against a variety of threats, including malware and phishing attacks. The cloud-native nature of SASE enables it to secure a geographically dispersed workforce and the use of SaaS applications efficiently.
A SASE solution centralizes the deployment of SWG in the cloud, offering organizations visibility and control over their entire network. This unified platform is particularly beneficial for managing the security of remote users and disparate enterprise applications. It ensures consistent security enforcement, regardless of user location or device, streamlining the security experience and bolstering an organization's defense posture.